IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.
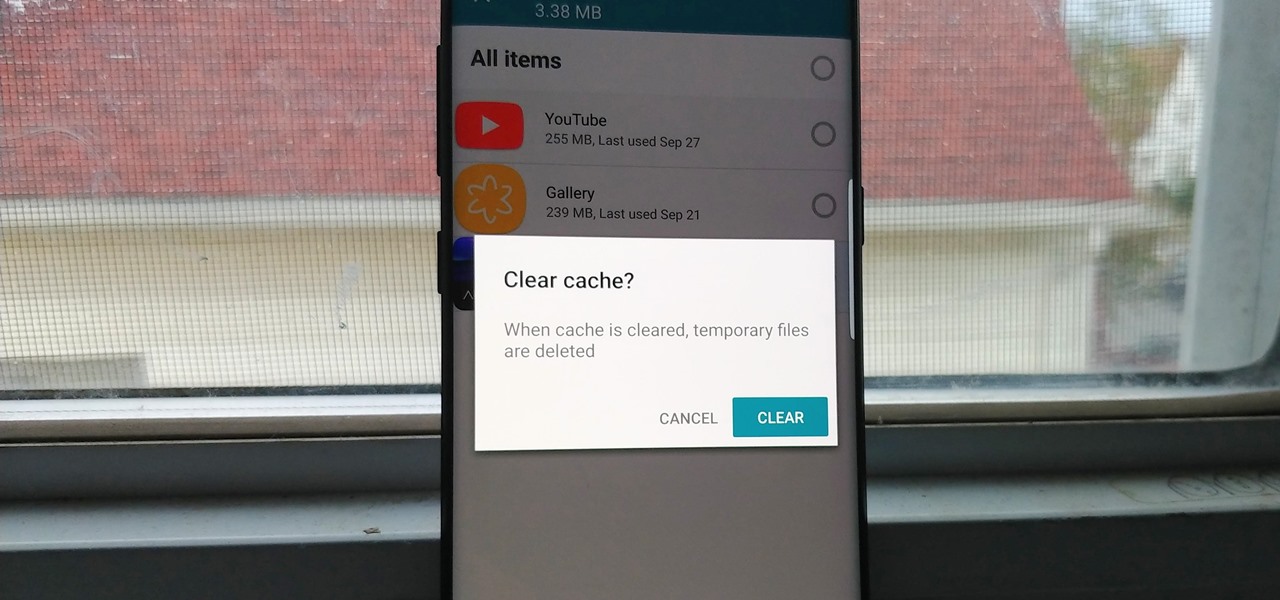
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.
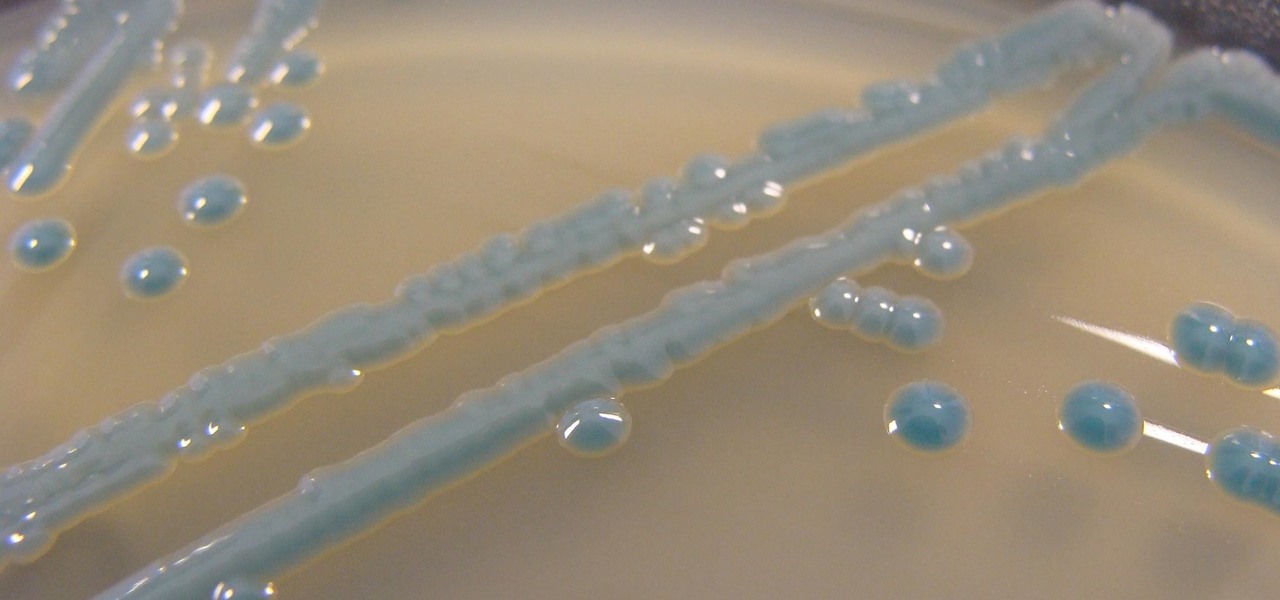
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

Apple likes to make their products simple. However, sometimes that simplicity leads to a confusing user-experience. Take the Apple TV, for example. How do you turn it off? Just press the power button, right? Sorry, there is no power button. Okay, so it's like an iPhone and has a nondescript button designated as a power button, right? Nope.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.

While you may not notice them at first, iOS 11 included some pretty significant improvements to the Photos app on your iPhone. These upgrades will help you make your Live Photos livelier, surprise you with photos you totally forgot about, keep your photos and videos organized, and more.

We're all looking to meet someone, and in this day and age the easiest way to do that is through one of the various dating apps out there. But we can all admit it can get disheartening swiping through all of those people for the frustration of someone not answering your messages after matching. The fact is, we could be missing out on great people just because they don't have time in their busy lives to answer their dating apps every day. Not to mention the fact that we as a society are becomi...

We know that healthcare-related facilities can be fertile ground for antibiotic-resistant bacteria, but recent research suggests your produce aisle might be too.

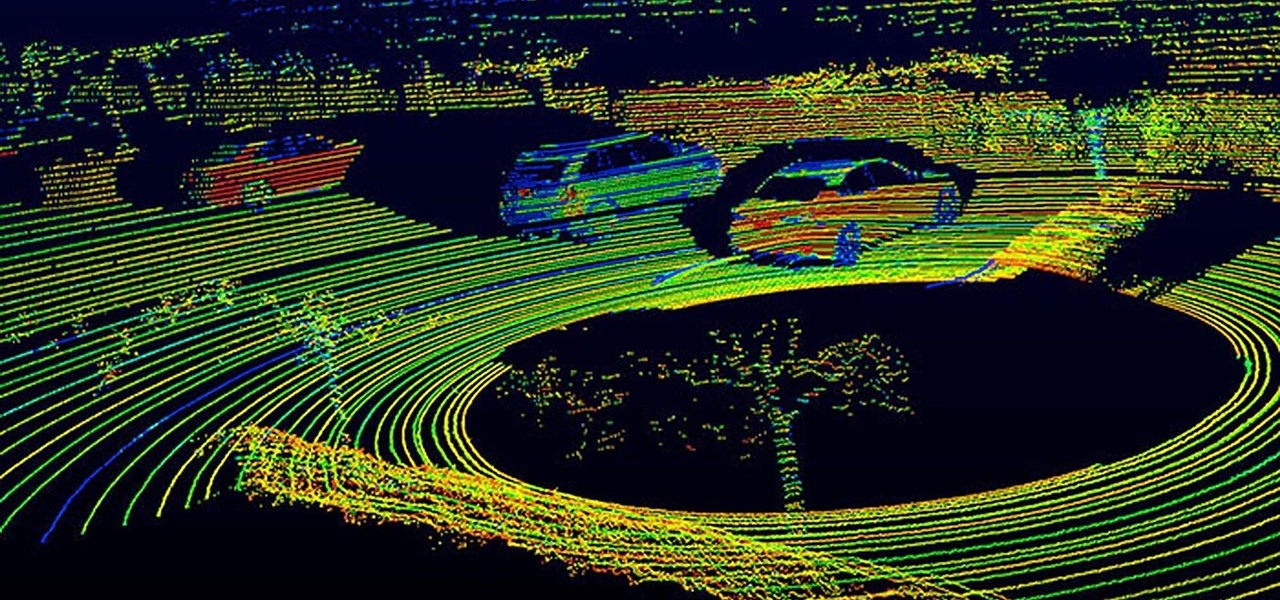
Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

Cholera is rapidly spreading in Mozambique, with over 1,200 people infected. Since the outset of 2017, cholera has spread from the capital city of Maputo (pictured above) to three of its ten provinces. Health officials report other areas in the country are seeing case counts rise, and two deaths have been logged so far.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

Over 6,500 waterfowl—mostly ducks—have died in Canyon County, Idaho, stricken by avian cholera. The outbreak started in February, and before it's over, it may not only be Idaho's largest outbreak, but one of the largest in the country.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

A rose by any other name may smell as sweet, but one annoying invasive weed may hold the answer to treating the superbug MRSA. Researchers from Emory University have found that the red berries of the Brazilian peppertree contain a compound that turns off a gene vital to the drug-resistance process.

Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

A stack of light-as-air pancakes can make a weekend morning truly golden. While fluffy pancakes may not seem like rocket science, the reality is that there are many little details that can contribute to a pancake fail that's either too dense or too crumbly.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

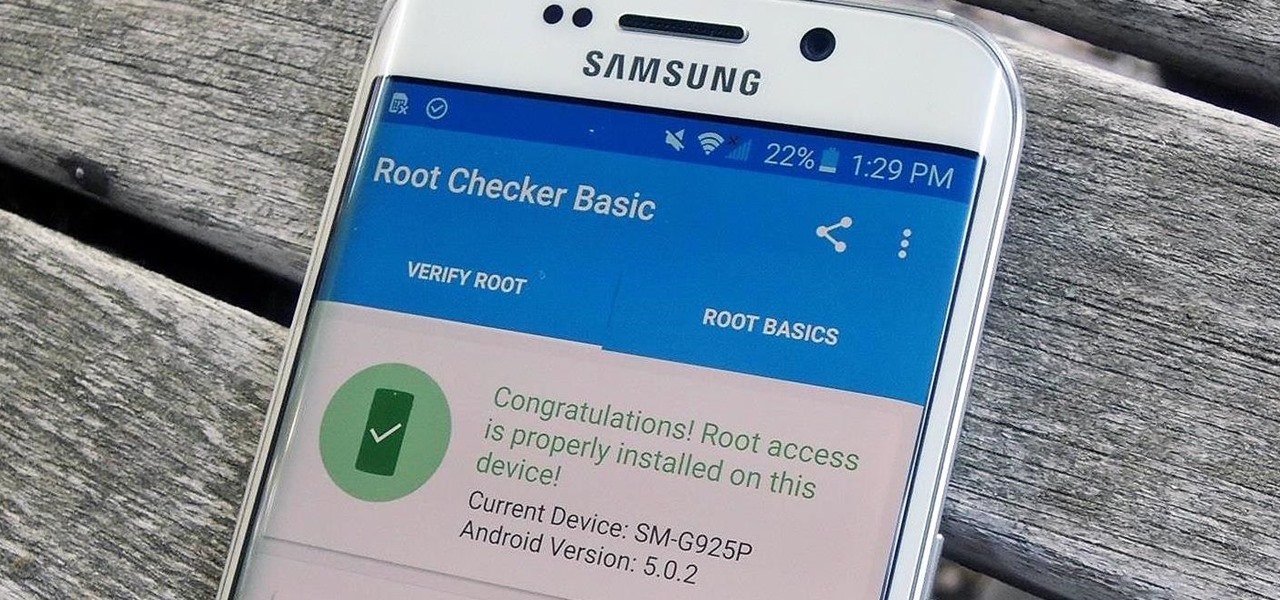
Thanks to leaks and hard working developers, rooting tools for brand new Android devices are usually available right around the time of the smartphone's release, if not earlier. The Samsung Galaxy S6 and S6 Edge are no exception.