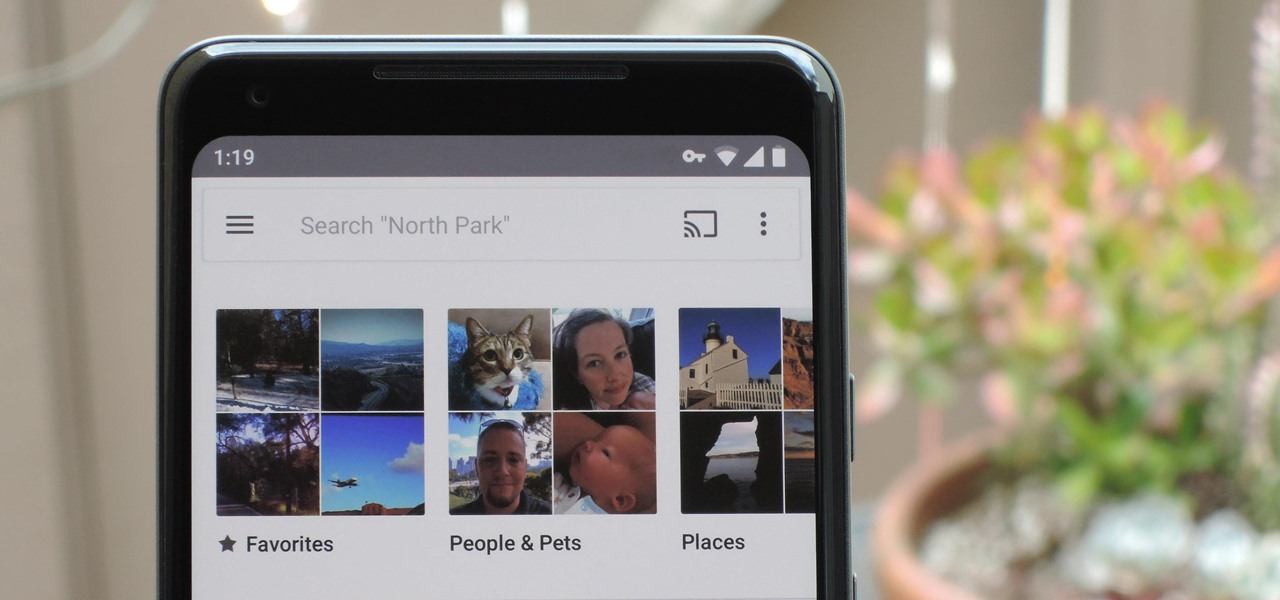
Google Photos is a fantastic service, giving you unlimited storage on either your Android or iPhone. With all this free space, some pictures can get lost in the shuffle. Fortunately, Google will now let users "Favorite" pictures — whereupon they're automatically put in their own standalone album.
Auto rotation is generally useful, but it gets annoying when you trigger it accidentally. In past Android versions, you could lock rotation into portrait mode as a workaround, but you'd have to disable this every time you wanted to put your phone in landscape mode. Luckily, Android Pie has a great fix for this.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.
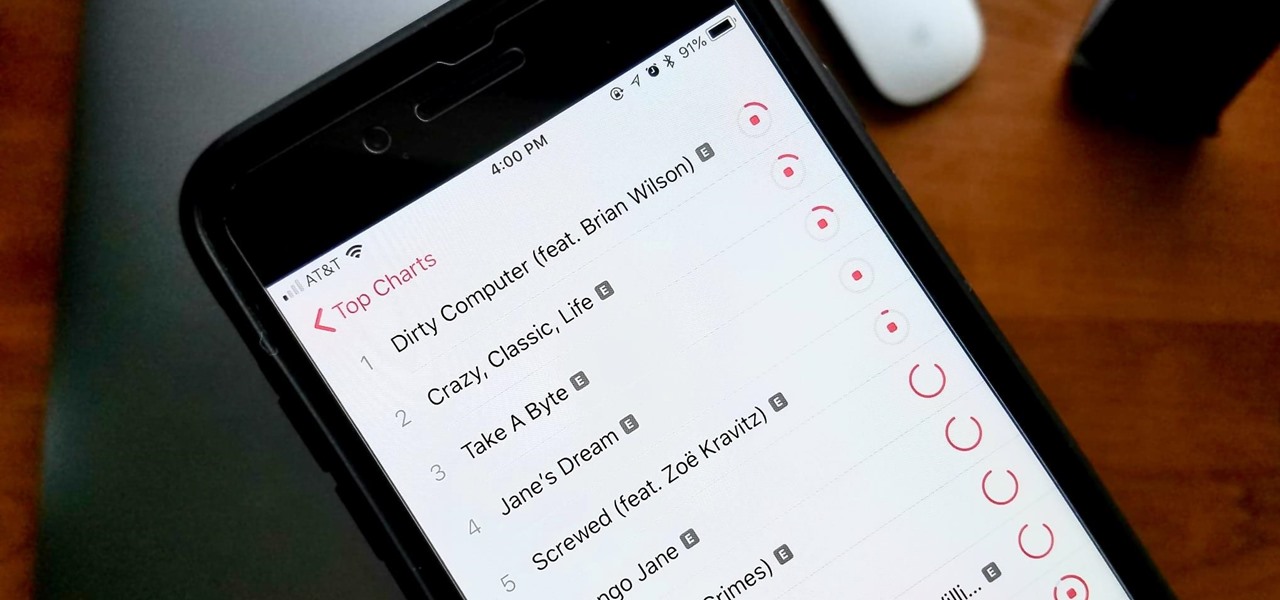
When you've exhausted your data plan, streaming isn't an option unless you want overcharges. While Apple Music makes it easy to download songs for offline listening, you need to add the music to your library first. This creates an extra step in downloading music, but it doesn't have to — Apple Music lets you automatically download any song, album, or playlist that you add to your library.

HTC is entering the augmented reality market through the back door by giving developers access to the stereo front-facing cameras on the Vive and Vive Pro VR headsets.

On Thursday, Osterhout Design Group (ODG) revealed a new, specially-crafted oxygen mask that uses the same augmented reality technology from its smartglasses to assist FedEx Express pilots navigating dangerous conditions.

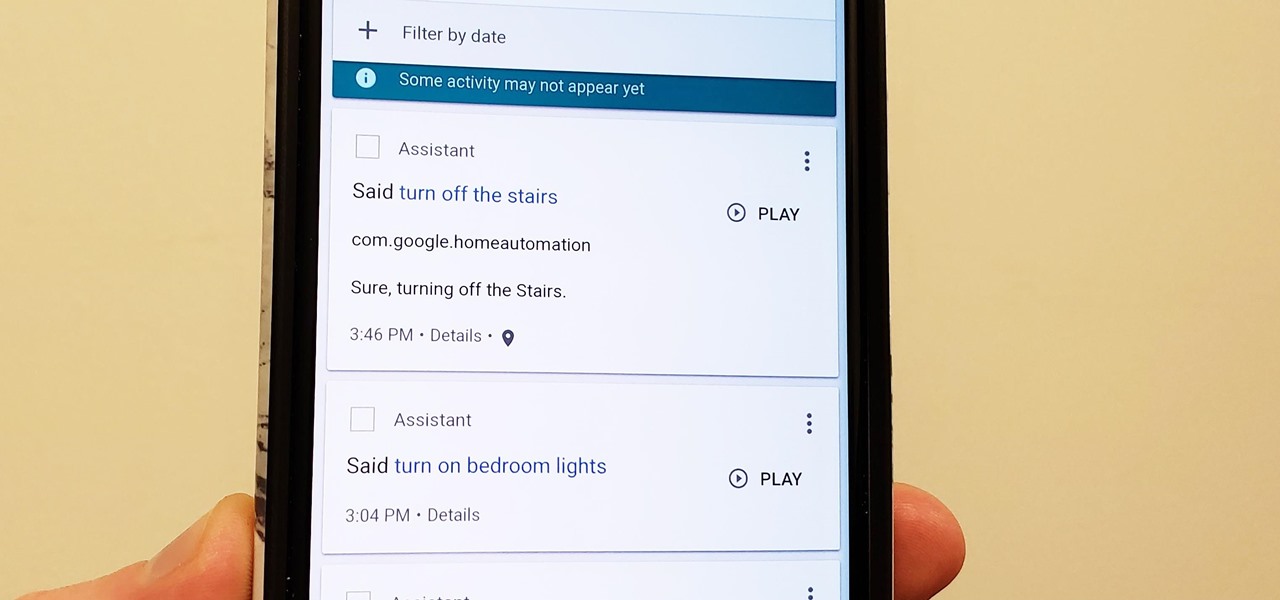
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Continuing with its new paradigm of using augmented reality to cover the news, The New York Times has published a feature story that takes a peek into the late David Bowie's eclectic wardrobe of on-stage outfits.

Augmented reality hardware maker Avegant has reportedly laid off between 20 and 30 employees, with founder Edward Tang returning to the CEO role at the company.

Samsung has had a rich screenshot editor in TouchWiz for years, and Apple even added a similar feature to iOS 11. Until now, stock Android has lagged behind in this area, but that's finally fixed in Android 9.0 Pie.

This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

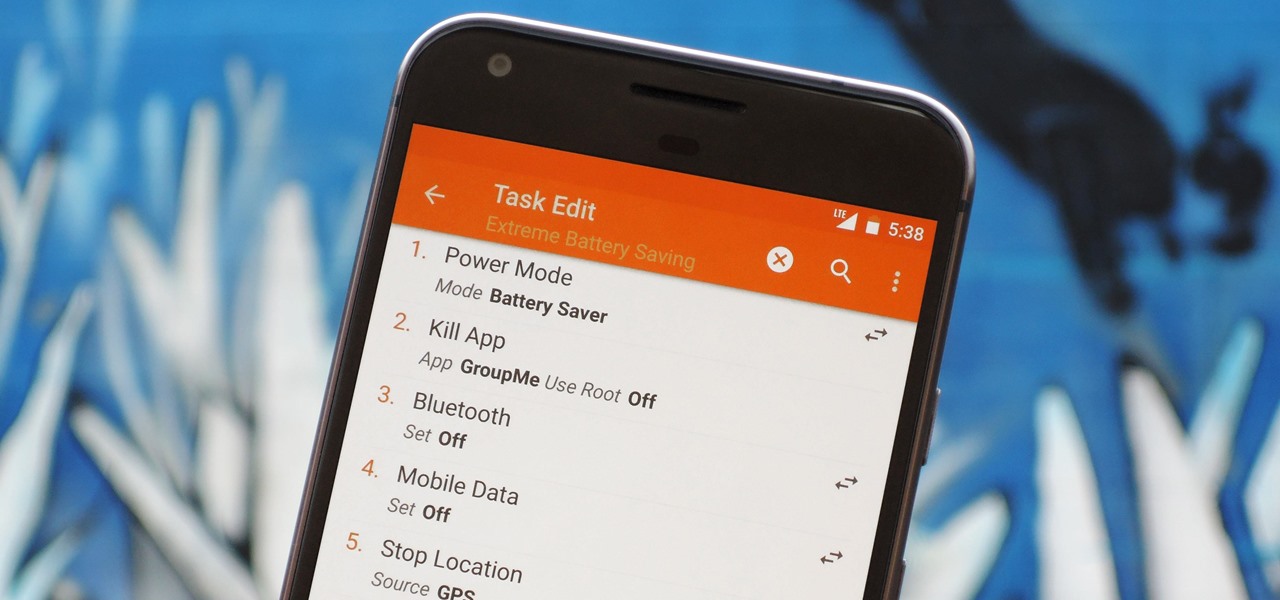
Preserving battery life has become one of the biggest problems for the average user. Whether you're on Android or iPhone, your battery is probably a massive concern. While there are a ton of battery-saving tips out there, they mainly rely on you manually performing actions yourself. This isn't the case if you use IFTTT to take care of your battery automatically.

Accompanying Snapchat's core features, like editing snaps and applying filters to them, is Bitmojis. These are small avatars that you create in your own likeness and use all throughout Snapchat. Formerly, there were two "styles" that you could pick from to make your Bitmoji: Bitstrips style and Bitmoji style. But Snapchat has a third style now that will redefine the way you use Bitmojis.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Update 1/17: Tim Cook chimed in about the upcoming iOS upgrade with expanded battery health data. We'll expand on that below.

T-Mobile has just pushed out a new update to the Samsung Galaxy Note 8, bringing the build number to N950USQU2BQLA. Here's what to expect.

Just nine days after the official release of iOS 11.2, Apple has released iOS 11.2.1. The update initially seems to have been seeded to only a handful of users and is intended to fix bugs in 11.2.

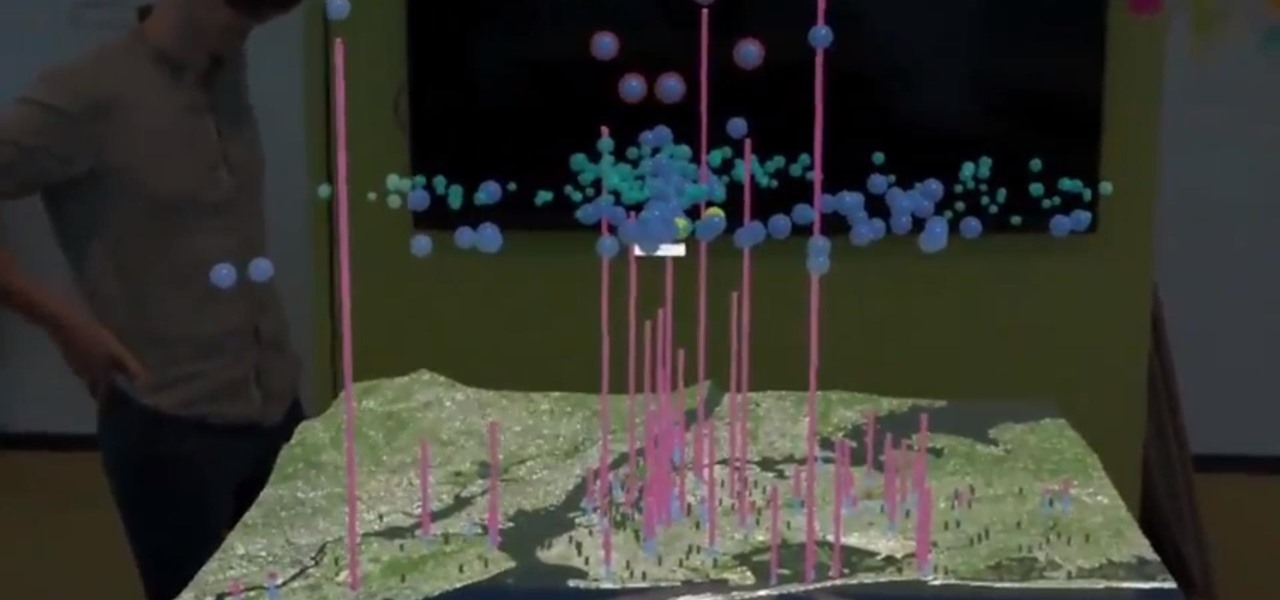
The same approach to augmented reality that some companies use to improve workforce productivity could also make it easier for car owners to operate and maintain their vehicles.

If you've ever made an Instagram story, you probably know you can add stickers to your stories. These stickers are interactive but, like real stickers, they don't move ... until now. In a Jan. 23 update to the app, more action can be added to your stories with animated GIF stickers.

One of the best parts of being an Android user is the countless awesome features. Many of these features are well-known and user-facing, like custom icon packs and launchers, but some get lost in the shuffle. Back at Google I/O 2016, Android Instant Apps were introduced to developers and enthusiasts. Since then, the feature has seen a wider rollout, but few users are aware of it.

On all other iPhone models, you go to "Battery" in the Settings app and toggle on "Battery Percentage" in order to see the exact amount of power left in the status bar. On the iPhone X, XS, XS Max, and XR, however, that option no longer exists since there's not enough room up there to show the percentage indicator because of the notch for the TrueDepth camera system. But that doesn't mean it's gone entirely.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Playlists are a vital feature for any music streaming service. For many, the ability to add and organize songs into the perfect order is a deciding factor in which streaming service to choose. The folks at Tidal (including owner Jay-Z) certainly recognize this, as they've provided users with the tools to not only create perfect playlists, but edit them as well.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

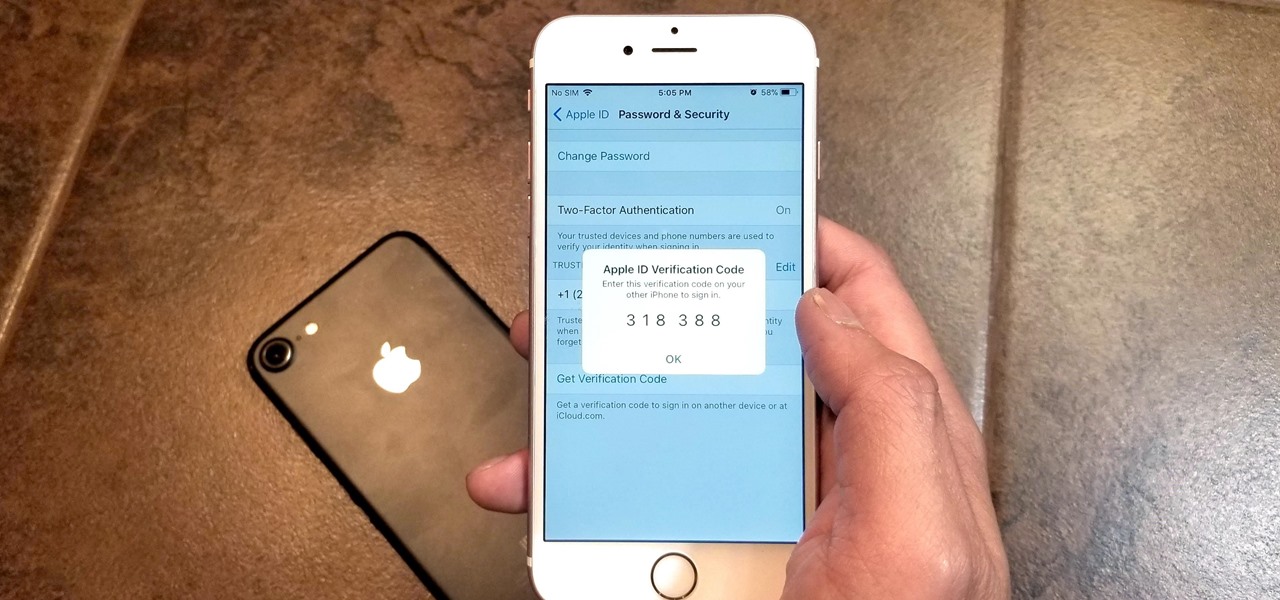
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

If you're a regular reader of this site, there's a good chance friends and family turn to you as their volunteer technical support staff.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

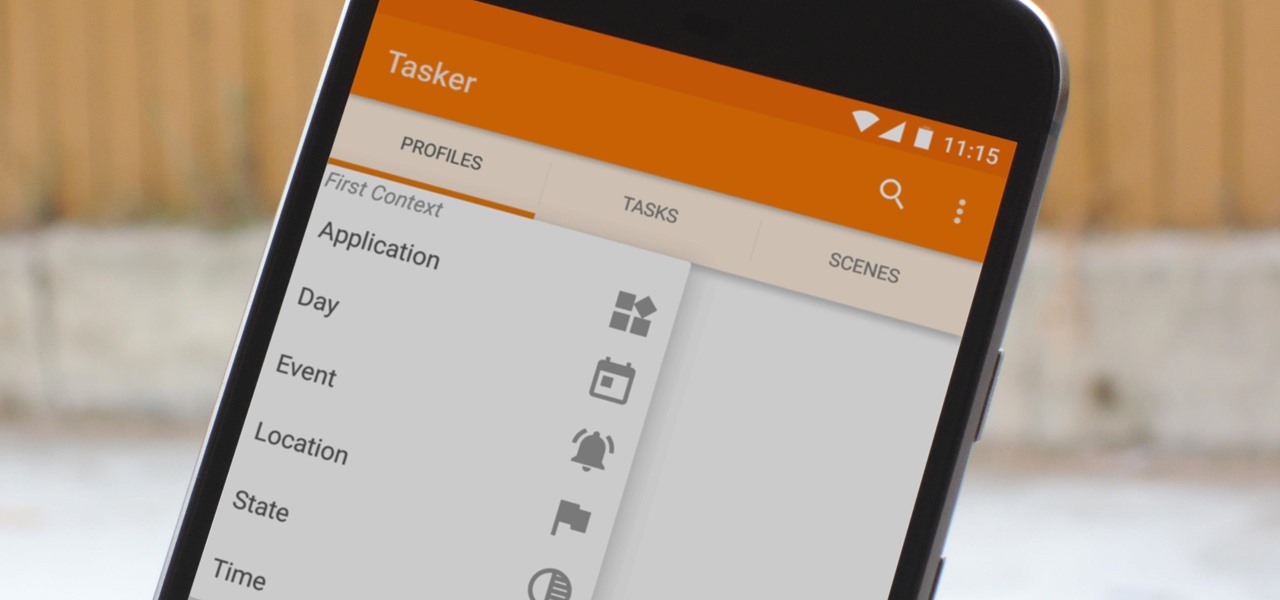
When you hear people say that Android is more flexible than iOS, it's because of things like Tasker. You can do virtually anything with the venerable automation tool, from saving battery life to controlling your smart home with your fingerprint. But before you get to that, you'll need a good understanding of all the basics.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

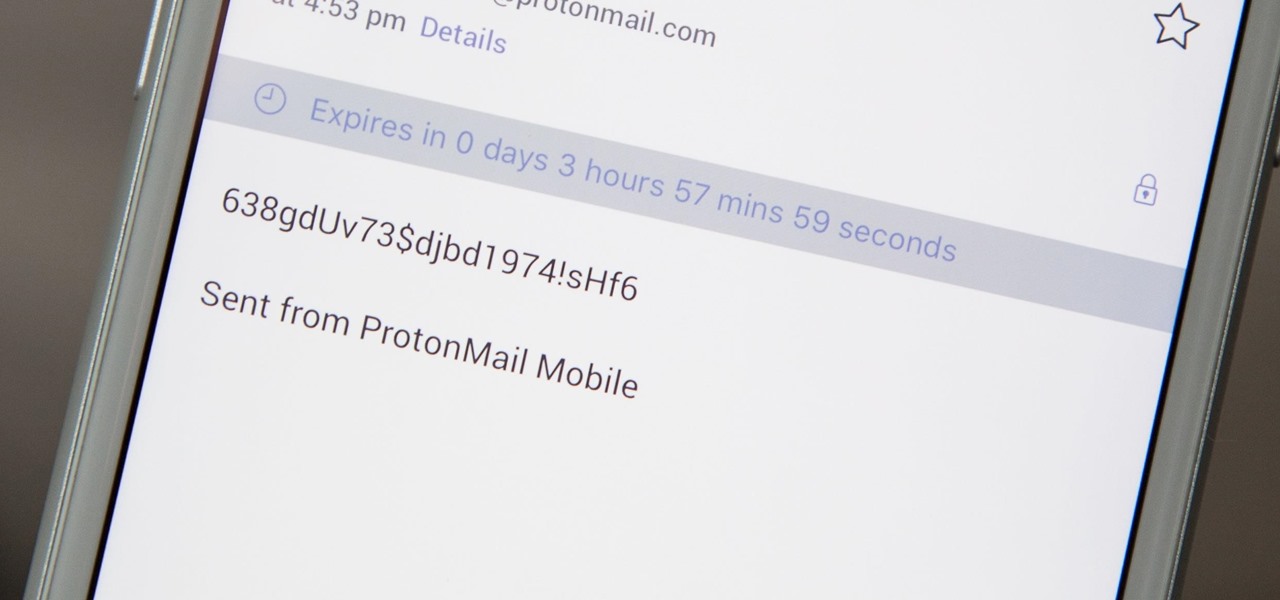
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind.

There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. Think of them like triggers and actions, respectively. Or a cause and an effect.

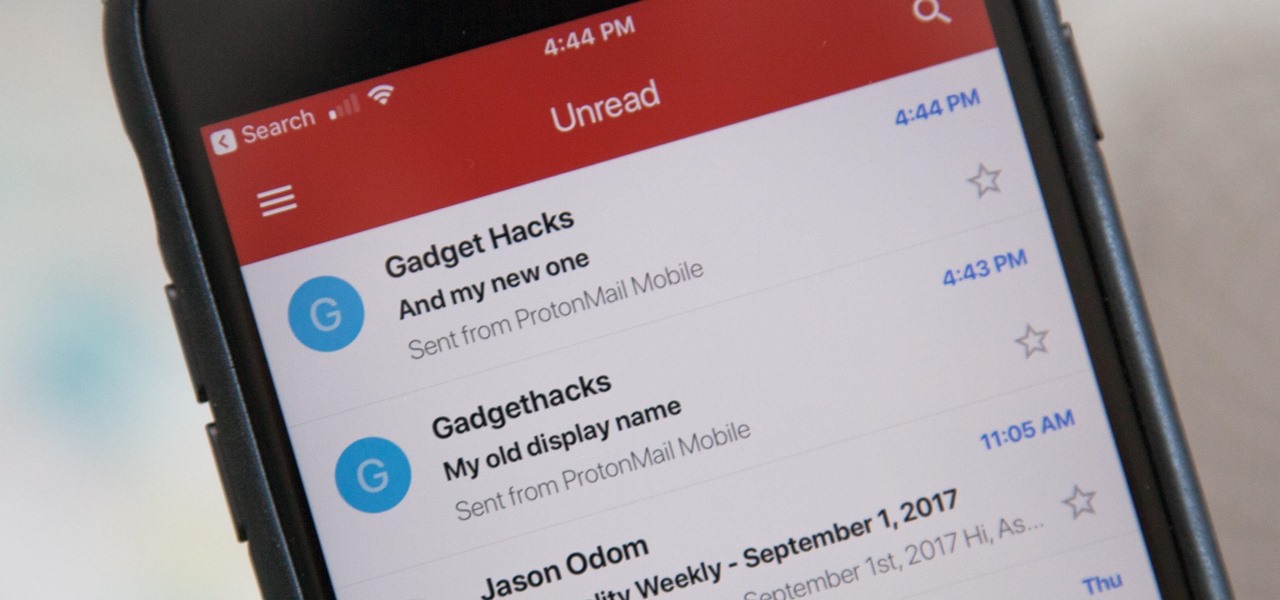
Your display name in ProtonMail is what email recipients will see when they first receive your message in ProtonMail, Gmail, or another email provider. You can choose this name when you first set up your ProtonMail account, but it can also be set up after the fact if you skipped that step.