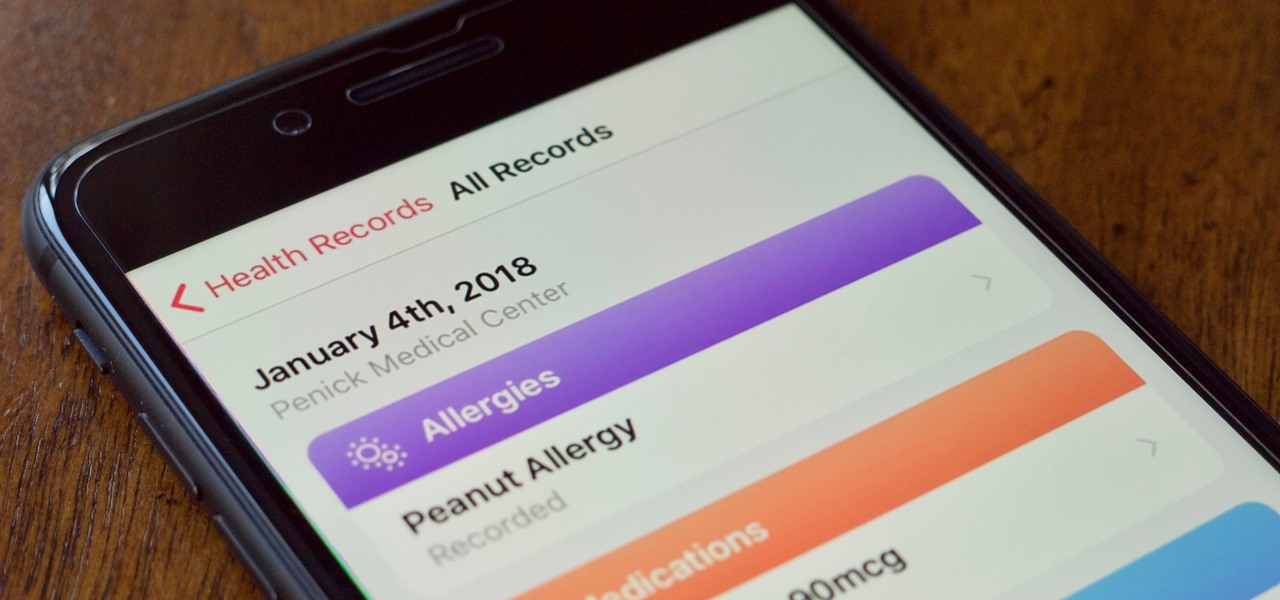
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

Pot, weed, bud, herb – whatever you want to call it, the green earthy treat makes everything way more fun. Now that marijuana is legal to some extent in more than half of all US states, we thought it was high time to showcase some apps that enhance your experience with the controversial pastime known as rolling up.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Whatever you want to call it for now—Android Nutella, Android Nougat, or Android 7.0—the upcoming "N" release of Android will surely bring in tons of new features and functionality. We know it will be named after a dessert, and we know that Google uses an alphabetical naming system, so something starting with "N" is next in line after Android 6.0 Marshmallow.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

iCloud is a very convenient service that allows you to share windows between two computers. To learn how to use iCloud, watch this video. With iCloud on your PC you can share information simply and efficiently between multiple workstations, or friends.

C-SPAN is one of the best ways to get your news on the web. Watching their videos from their website will get you up-to-date on all of the new headlines, and it will always give you a history lesson with all of the past headlines. See something interesting while watching a C-SPAN video and want others to see it, too? C-SPAN makes it easy to clip the exact portion you want, and share it with friends or embed it on a website or blog. Just follow these instructions.

David Hall of Professional Coin Grading Service presents this tutorial on coin grading and authentication. How are coins graded and what kind of care goes into coin grading. This is an overview of the numismatic science and process.

MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.

Is your BFF getting married? Looks like you have a bridal shower to plan! Organize a bridal bash that people will actually want to attend using these innovative ideas.

Testing products for a living is a bit more complicated than it sounds. You Will Need

Learn one of the world's most popular games. It's actually good exercise, too! Step 1: Decide who goes first

For anyone who's ever wondered why people are swatting an odd-looking object back and forth across a net, here's the lowdown. Watch this video to learn how to play badminton.

Low battery – two words you never want to hear. Banish them with these tips. You Will Need

Turn your possessions into cash and become an online selling machine. You will need: Something to sell, a computer with internet access, an eBay account, a digital camera, shipping supplies, something to sell,a computer with internet access, an eBay account, a digital camera, & shipping supplies.

Notaries can make $75-125 an hour for their services. All it takes is one course and a small fee to get a license and you will be on your way to raking in the extra cash. Being a notary is a great boost to your resume and your pocketbook, so why not give it a try?

Have access to a Battistella T220P ironing table and, however improbably, wondering how to use it? Well, you're in luck: With this video demonstration, you'll learn how to operate the Battistella T220P ironing table in the service of ironing a shirt. For more, or to get started using your own Battistella T220P ironing table, watch this video tutorial.

If you want to do some easy XML editing, then this markup language video is the one to watch, for XMLSpy. The graphical WSDL editor allows developers to design the interface for Web Services in an intuitive manner.

You no longer have to worry about repair technicians accessing the personal information on your iPhone when you send it in for repairs. With Apple's new security feature, you'll no longer have to erase your iPhone to ensure your photos, messages, accounts, and other private data remain for your eyes only.

While you can use Google Assistant on your Android phone to identify songs playing around you, you may still prefer Shazam's music recognition service, which has been available on Android since 2008 — a full nine years before Google Assistant's audio-fingerprinting technology. If that's the case, it's even easier now to Shazam songs in seconds, no matter what screen you're on.

If you're tired of the default yellow link colors in your Notes app, which I find hard to look at in light mode, there's a way to change them to another color on your iPhone, iPad, and/or Mac running iOS 17, iPadOS 17, and/or macOS Sonoma 14 and earlier.

Music goes well with almost every Instagram story, but adding a particular song or soundtrack isn't the most obvious task if you've never tried before or haven't done so in a long time.

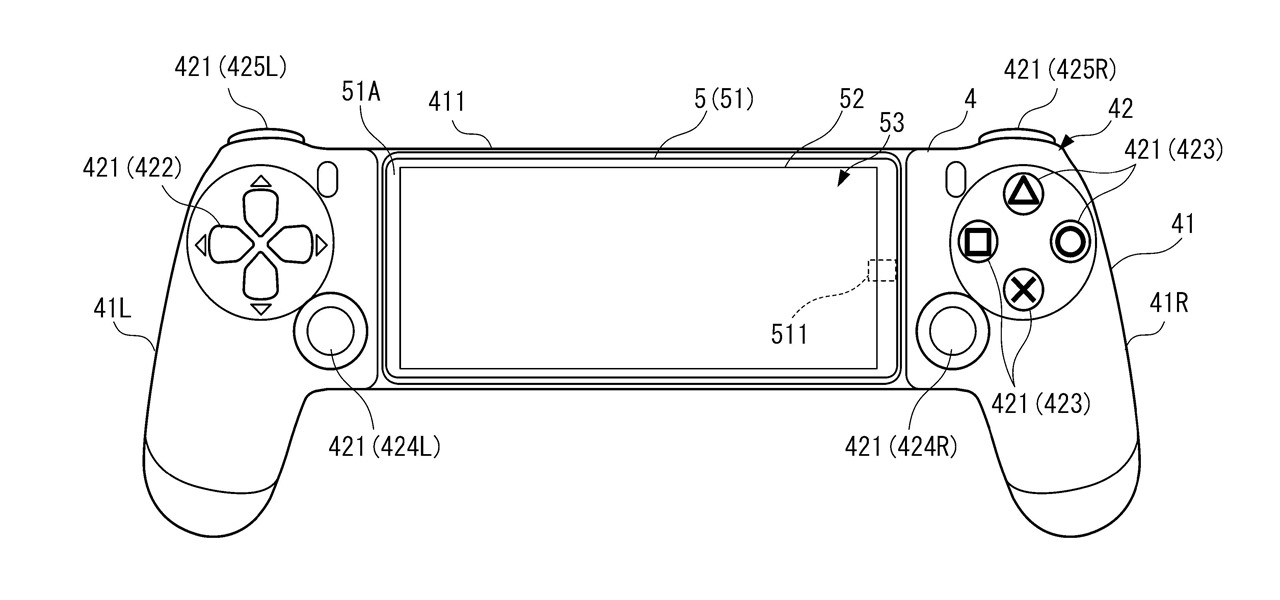
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.

Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.