Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

The AFL-CIO's Transportation Trades Division, which represents 32 unions in the US, has successfully lobbied for the removal of 10,000-lb. and heavier commercial trucks from provisions in bills expected to pass that could allow for millions of driverless vehicles on public roads and streets, Bloomberg News reported.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.

Augmented reality headset maker DAQRI has collaborated with the US Navy to outfit the company's Smart Helmet device for use on battleships.

Waymo revealed more clues about its future business model after it said yesterday it plans to kill its Firefly pod-like car project and focus more closely on offering driverless systems for commercially available car and truck models.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

Intel launched their Advanced Vehicle Lab in Silicon Valley this week, and the tech giant is now on the hunt for potential partners.

Viral infections have been the focus of attention in the development of autoimmune diseases—diseases where the body's immune system reacts to the body's own cells—because they trigger the immune system into action.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

Remember back in 2011–2012 when "Little Talks" by Of Monsters and Men was the bumping new single being played everywhere? Well, thanks to this robot created from a LEGO Mindstorm EV3 kit, and an acoustic guitar, you get to get the iconic "hey!" stuck in your head for the rest of 2017. You're welcome.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the carriers themselves have technical difficulties that can result in your phone's clock being minutes or even hours out of sync.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Now that Android Auto and Apple CarPlay have finally arrived, the days of clunky in-dash infotainment systems are coming to an end. Instead of using software created by an automotive company to get directions, stream music, or take calls, we can now get the best user experience Silicon Valley has to offer—all while sitting comfortably in the driver's seat.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Unless you have a newer iPhone 6S or 6S Plus, the front-facing "FaceTime" camera on your iPhone has a pretty weak, low-res sensor, which means unflattering selfies. You could use the rear "iSight" camera to take a high-res selfie, but framing your mug properly and hitting the shutter is difficult, takes many failed attempts, and usually results in a lackluster photo.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or right-click, but it usually requires special hardware to detect the amount of pressure you've applied.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

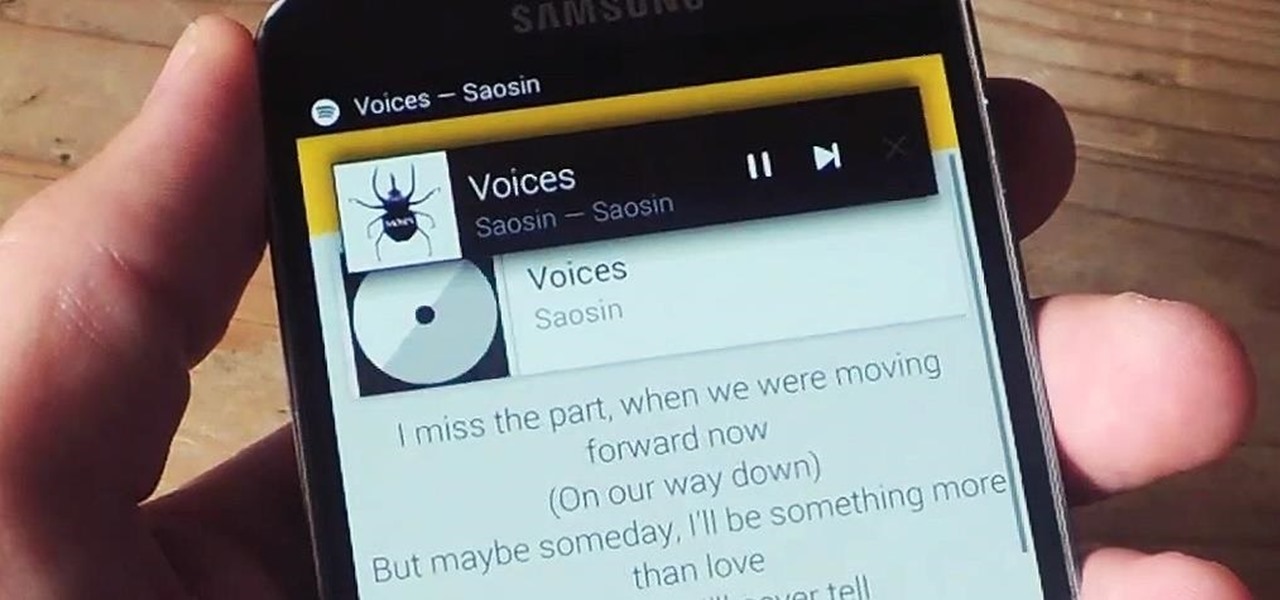
With floating song lyrics displayed over the screen, apps like musiXmatch and Floating Lyrics are perfect for people who want to go beyond just the tunes and delve into a song's message and meaning. And while these floating windows can be convenient, they're not always necessary.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Mac keyboards are great when listening to music or watching a movie, since you can control what's playing without going back into iTunes or QuickTime Player. However, when you're using an app like Photoshop that uses the F7, F8, and F9 as shortcuts, it gets pretty annoying to have to hold down the Fn key. Why can't you just hit the back, play/pause, and skip buttons alone?

Those of us with girlfriends understand that in order for the relationship to run smoothly, you have to keep your woman happy and let her know that you're thinking of her—even when you're not.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

It's time to enjoy one of America's longest lasting favorite pastimes. No, not baseball—pranking our friends! With the internet currently overrun with countless pictures and memes of cats, there's no way for your feline-hating friends to surf the web without coming across a kitten or two. But things can get worse for them. Way worse...

Clash of Clans is one of the most successful games ever to come out for Android and iOS. It has been downloaded over 50 million times from Google Play alone, and shows no signs of decline.

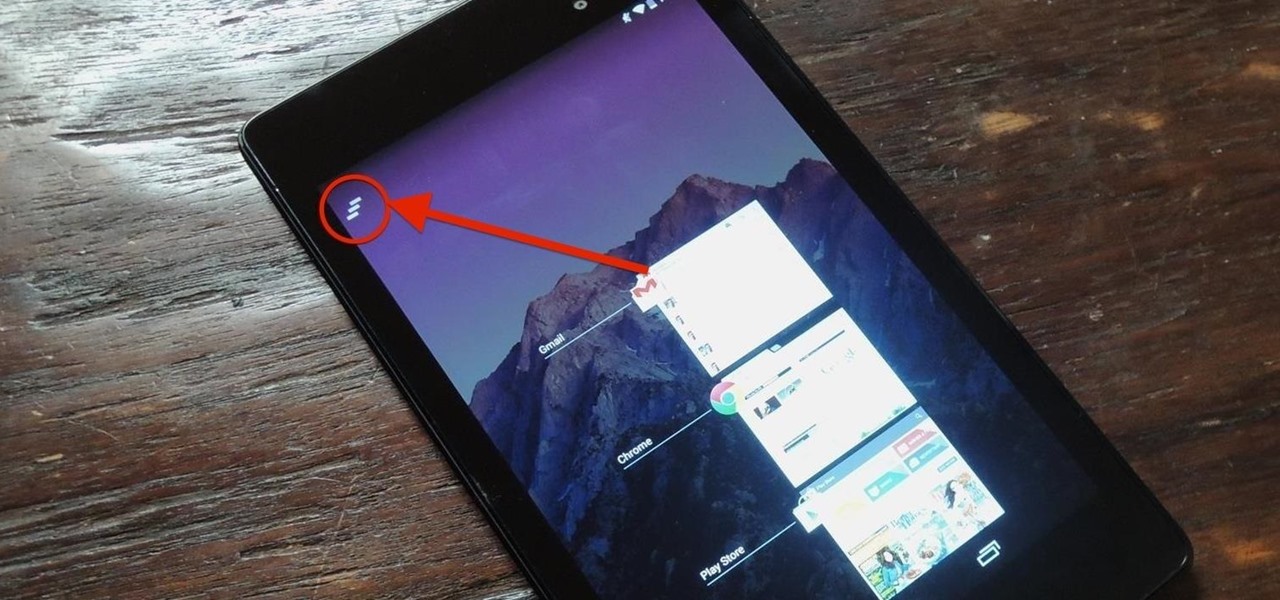
Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).

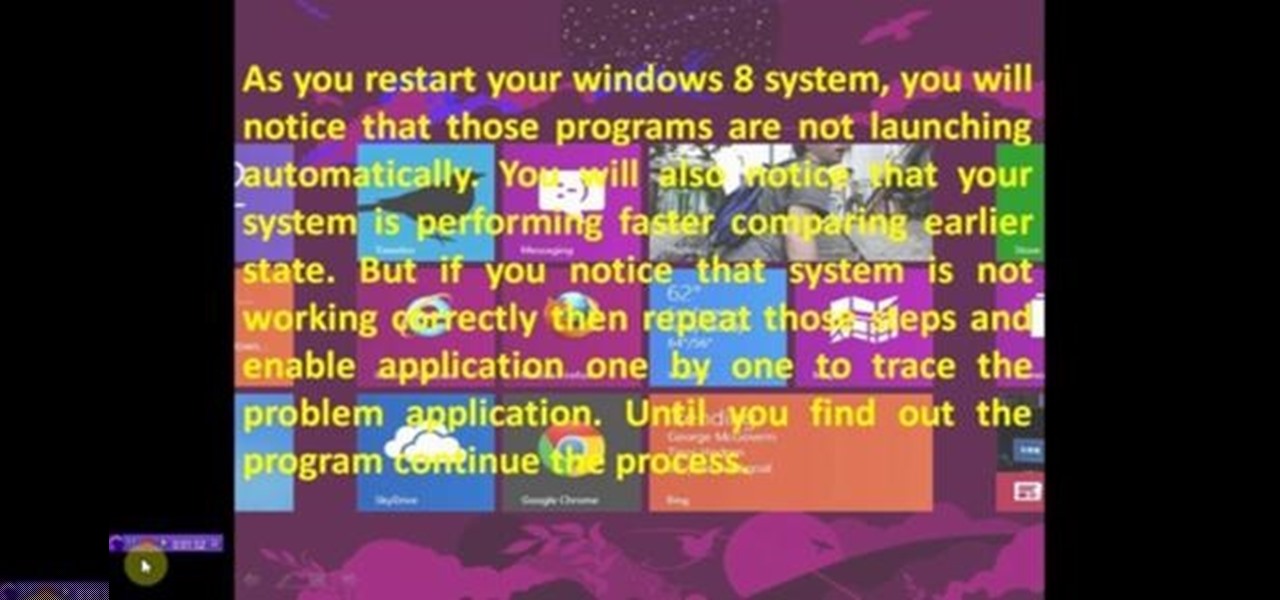
This video will show you how to Speed up Windows 8 System by Disabling Startup Program. This is mostly done by disabling few programs to launch at startup time. Be careful before disabling programs otherwise you may disable few important programs which will affect normal functioning of PC. Watch the video and follow all the steps.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

In a flurry of moves today, Microsoft has not only released their suite of Office apps for the iPad, but they also updated their Android and iOS Office Mobile apps to allow for creating and editing documents without requiring an Office 365 account (so long as it's for "home" use). Microsoft Office Mobile for Android & iOS

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.