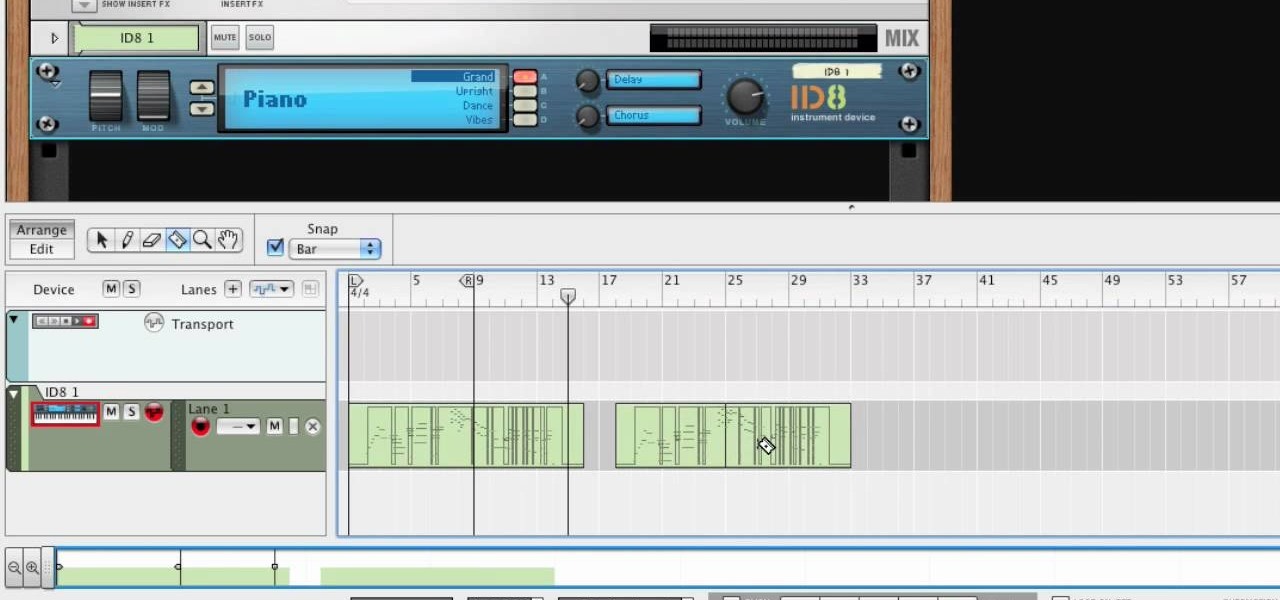
In this tutorial, we learn how to use MIDI in Record. First, automatically find your controller keyboard and set it up in your software. With this set up, create an ID8 instrument by clicking on the icon. Settle for a grand piano and record something to test it out. All clips are recorded and save mini notes, data, automation, and more. Clips can be moved, resized, duplicated, split, and joined through Record. These make up the arrangement and make the music. You can automate anything you wan...
Wish there were an easy way to have your Apple computer automatically check what you type for proper spelling? There is! And it's quite easy to enable. So easy, in fact, that this Apple accessibility guide can present a complete walkthrough of the process in just a minute and a half. For details, as well as to get started using this useful auto spellcheck feature yourself, watch this helpful how-to.
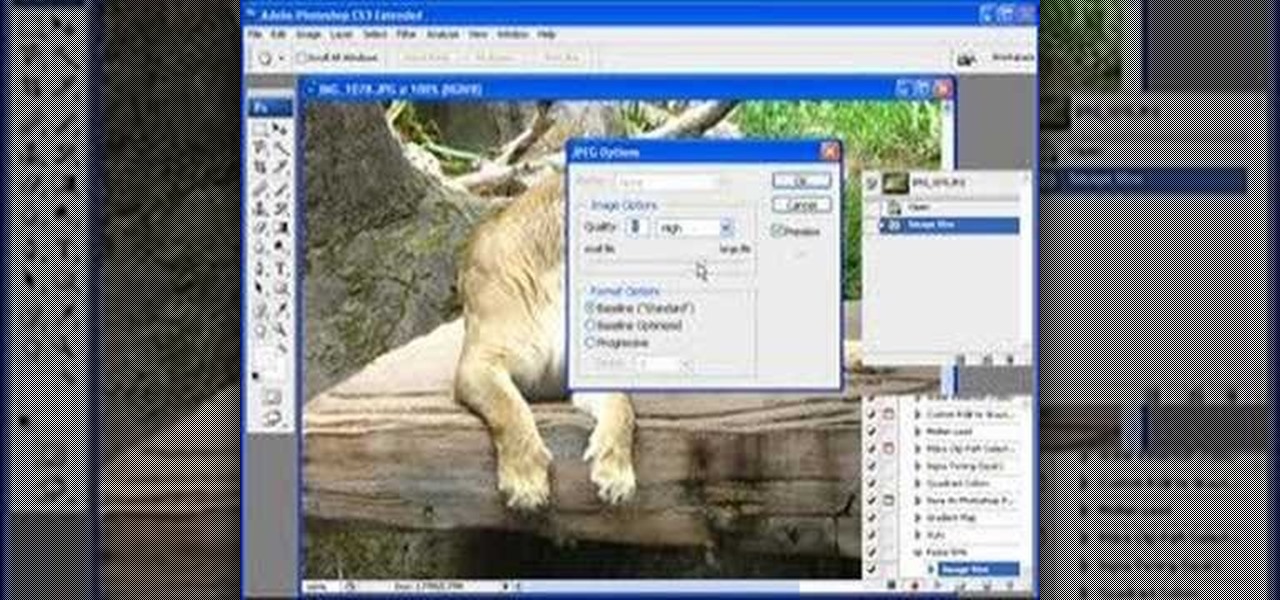
Here is a simple technique to resize multiple pictures in Photoshop by creating an action, to adjust the image size. The only requirement is for the pictures to more or less the same size. First we go to windows and select action then we open up an image to determine the appropriate size that we require. Then click on the create new action and, give it a name then hit record now go to image the image size resize the image and then save and hit ok .You can see that its still recording your act...

This tutorial will focus on how to use the fit image function within Adobe Photoshop. You will utilize this function when you want the pixel width to match between different sized photos in portrait and landscape. First you will select all the photos (you must create a batch action in Photoshop). Next select the fit image option in the file menu under automate. You will need to put the same number into length and width to constrain the proportions of your landscape and portrait photos have th...

This video in the Software category will show you how to create simple panoramic images in Photoshop. This video uses only five images for this effect. Select the five images and put them in a folder. Go to File -> Automate -> Photomerge. On the Photomerge page select ‘Folder’ and browse. Find and ‘choose’ the folder you created. Under the layout panel on left hand side of the page, select ‘cylindrical ‘option and click OK. Now the panoramic image will appear that will have some blank areas. ...
Follow along with this video and learn how to retweet a post on Twitter. -A Tweet is simply a message posted on Twitter.

Learn how to edit form fields in Adobe Acrobat 9 Pro. Start by looking at a automated form that has some errors in the field of gender and marital status. To correct click on forms add or edit fields. Click on the field that needs correcting and figure out the error. Rename the fields to reset them and correct the field. Double check that the name an tool tips have been fixed. Create a cross hairs that you can type over with the correct values you want. You can also shift over boxes. A specia...

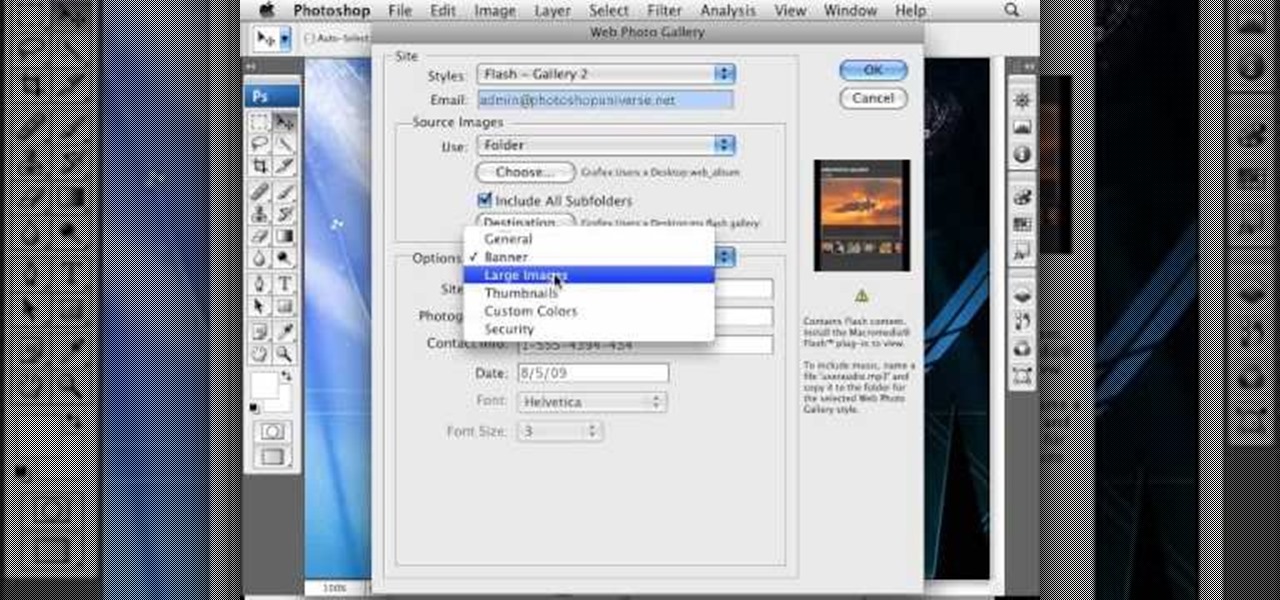
To create a web photo gallery on Photoshop, first go to file show all menu items if you have then automate go to Web photo gallery then to changes the styles click on the style to see them the description on thee right then set up email address after Source images on (use) choose a folder, click all sub folders if you do not have any sub folders in Your folder. Go to options select one that you choose then click OK then in Photoshop it resizes all photos quickly after open up a web browser an...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Windows from a USB flash key.

Studying to be a nurse? Then here is a nursing how-to video that teaches you how to measure blood pressure with a manual cuff. Every nurse should know the basics of this technique, follow along and see how easy it is to take a patient's blood pressure with a manual cuff. It is important to know how to take a manual cuff reading in case that the automated blood pressure machine isn't working. These medical tips are sure to help you pass your nursing exam with flying colors.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Ask anyone that works on the development of driverless vehicle technology and there is a very good chance that AutonomouStuff will have supplied something to their project.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

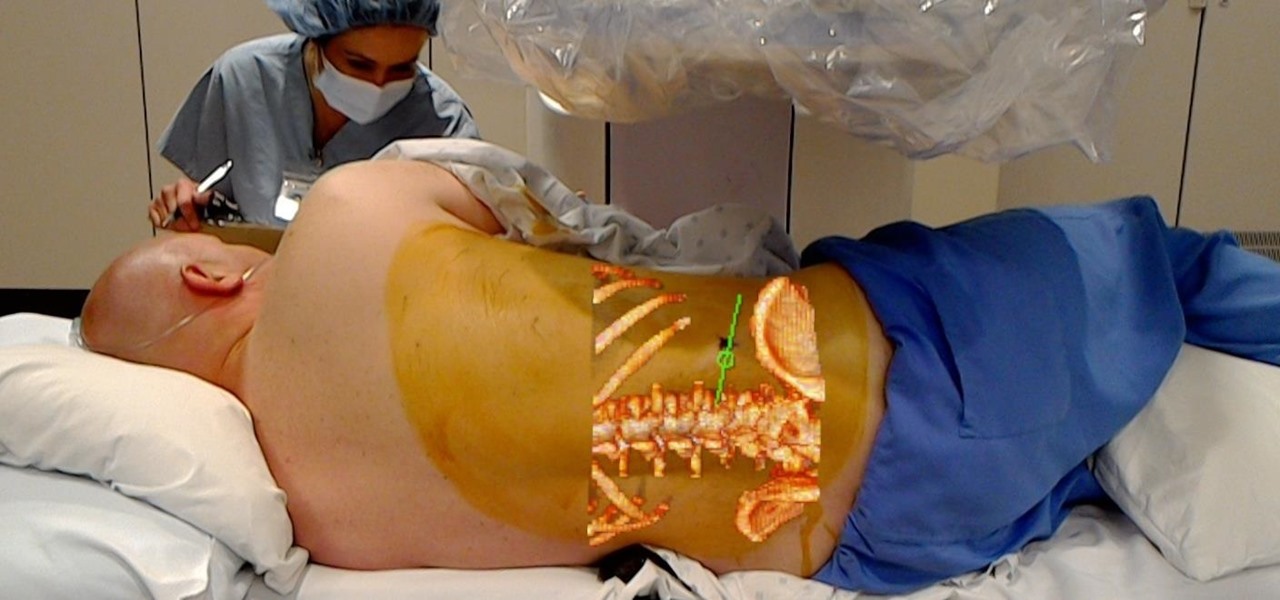
Numerous examples exist of doctors and surgeons using HoloLens to plan surgeries. The device has even been used to view reference images during a procedure and stream it to a remote audience. Until recently, it has not been used to augment the surgeon's view of the patient during a live surgery.

When Yosemite was released, a more detailed boot screen came to your Mac. So now, just like on Apple's mobile devices, you will see a loading bar telling you how far into the startup process you are. Apple also decided to add a black version of this boot screen to newer Macs, leaving those of us who purchased a computer before 2011 out of the loop.

This is an automated video on how you can win your ex girlfriend back. It tells you what you should do in this situation. This video also tells you how to be thoughtful during this time and how you can possibly go to far. It also tells you how you may be able to get her back while she has a current boyfriend. You should have a plan ready to get your ex back but you may also have to deal with rejection.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

We've all seen the classic tornado-in-a-bottle science experiment, which uses 2 two-liter bottles to create a whirlpool effect. This version requires you to get the tornado started yourself by spinning the bottles, but what if you want to make it fully automated?

When the new iOS 6 came out a few months ago, I was pumped because I finally would get Siri on my iPhone 4. Having the automated voice assistant readily available on my phone would be cool, even if I probably wouldn't use it all that much.

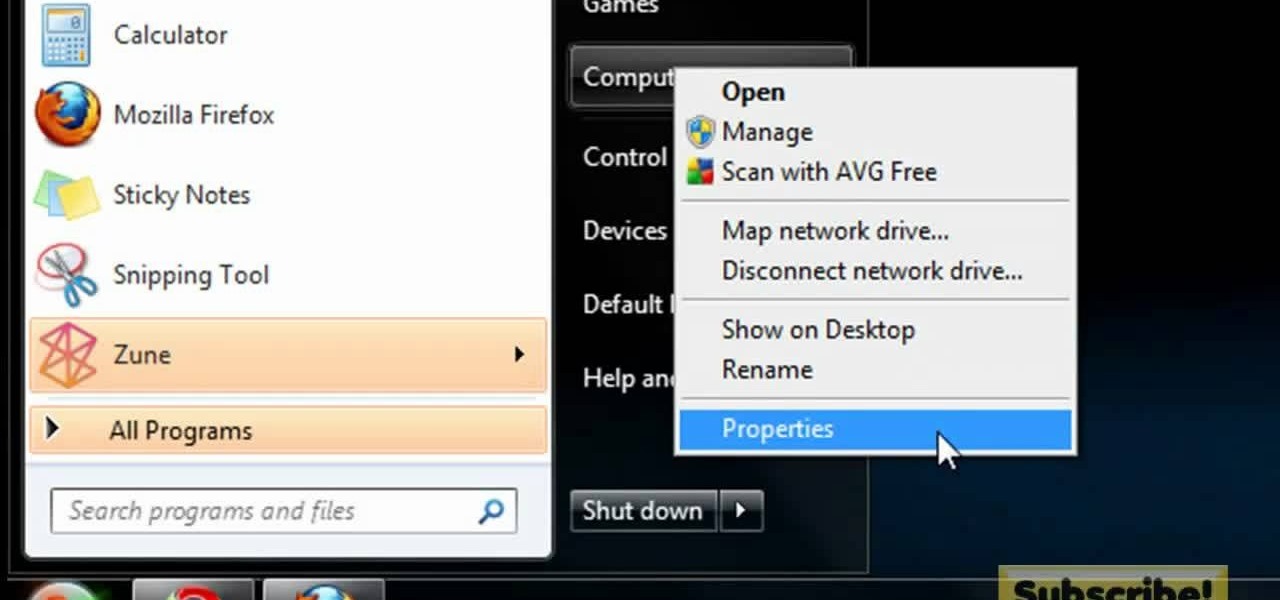
In this video tutorial, viewers learn how to make the System Restore feature use less space in Windows 7. Begin by clicking on the Start menu. Right-click on Computer and select Properties. Under Tasks, click on System protection. In the System Properties window, select the hard drive and click Configure. Under Disk Space Usage, drag the slider to the left for a lower amount. Then click on Apply and OK to confirm. This video will benefit those viewers who have a Windows 7 computer and would l...

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Delphi Automotive PLC has announced it is partnering with Transdev Group to develop on-demand driverless transportation systems, a deal that shows promise for autonomous development on a global scale.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Hello again, ***UPDATE: Adding links to the other Two articles****

Today we are pleased to announce the end to the Apple vs. Android war. About a year ago, our Gadget Hacks team started working on a top-secret project to dual-boot both Android and iOS on the same phone—and we couldn't be more proud to announce that we've finally succeeded! Your phone can now run both iOS and Android—whenever you want. Right now.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Verizon could be getting in on the autonomous vehicle party, judging by its recent investment in driverless software company Renovo Motors.

An expert in the driverless market has earmarked Porsche as the company to watch in the automated car race.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

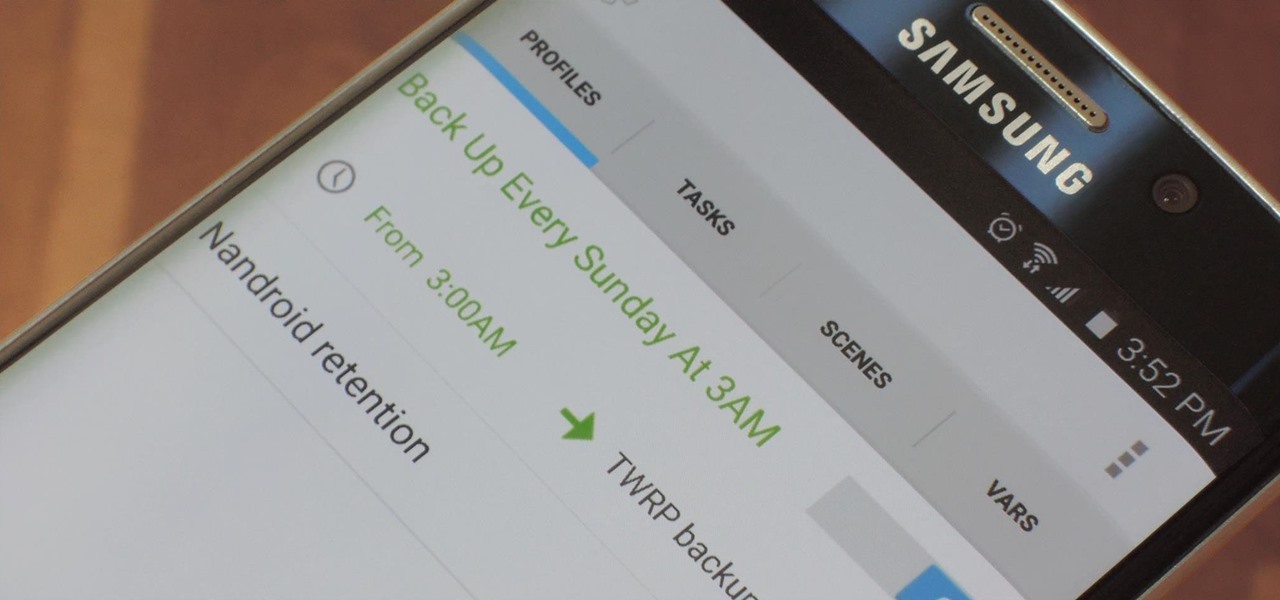
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

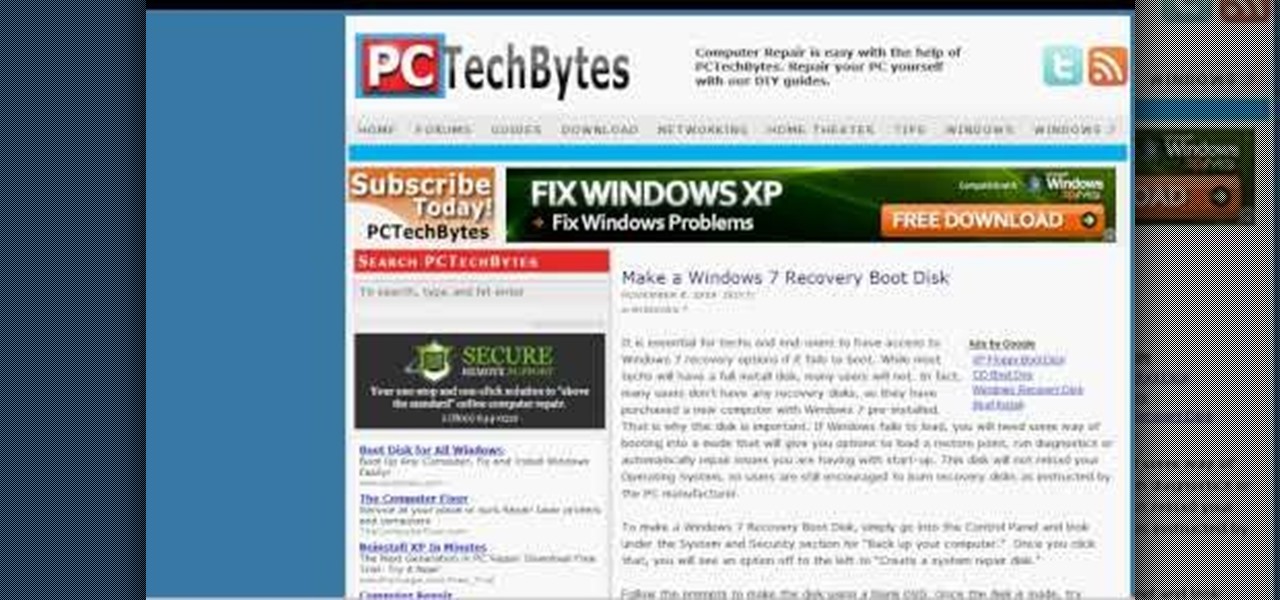
In this how-to video, you will learn how to quickly make a Windows 7 boot disk. This is essential for making backups or booting from something other than the operating system on your hard drive. First, go to the control panel and click the back up your computer option under system and security. Next, go to the left and click create a system repair disk. Put a blank DVD in to the optical drive. Select your drive and press create disk. This video shows just how quick and easy it is to make a bo...

A Tutorial: Ubuntu Linux is a completely free open-source operating system that has many useful features and abilities, and this guide will show you how to try this new OS without harming your Windows system, and it only takes five minutes to learn! This guide will show you how to: -Download and burn the Ubuntu image to CD -Shrink the Windows installation to make room for Ubuntu -Boot to the Ubuntu live CD and begin the installation process -A step-by-step description of what options to choos...

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.