A highly useful, yet unrecognized and under-appreciated feature in Apple's iOS 8 is the ability to seamlessly convert incoming texts regarding future dates into calendar events. Messages like "Let's chill tomorrow" can be tapped on and quickly added to the calendar. It's convenient and easy, but unfortunately, not available on most Android devices. However, it's pretty easy to get using Inviter (SMS to Calendar) from developer Sergey Beliy.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

There are those who hold their phone or set it down when they're not using it, and others, like myself, who pocket it. If you're like me and are rocking the pants pocket fade, then you'll love the new Android app I found.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.
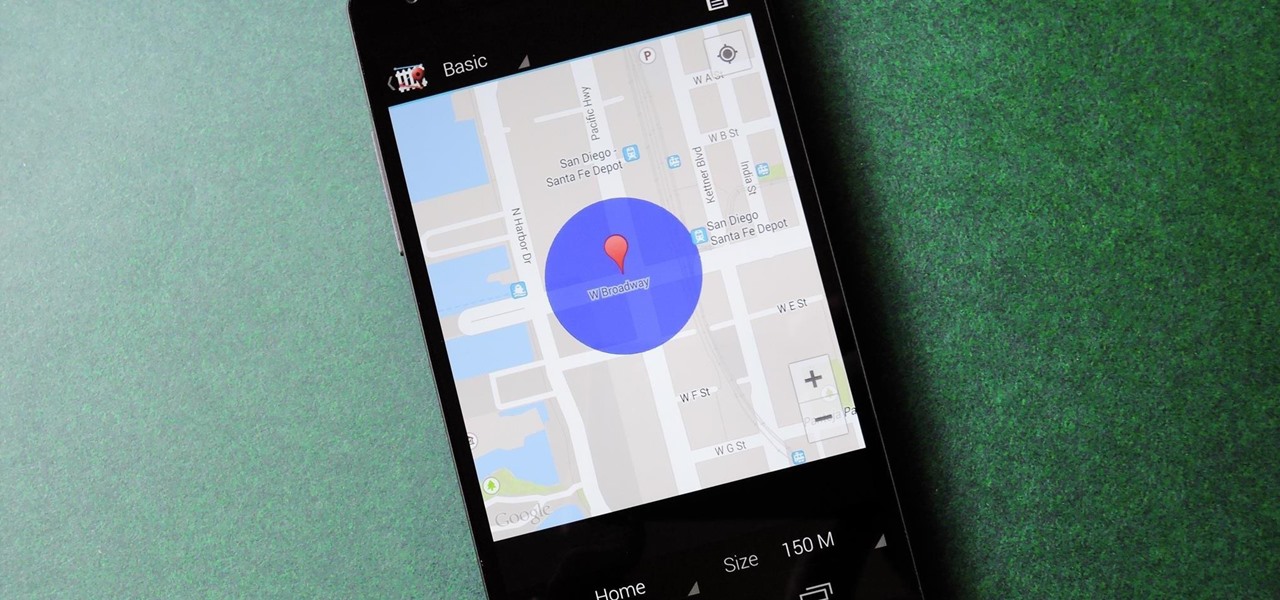
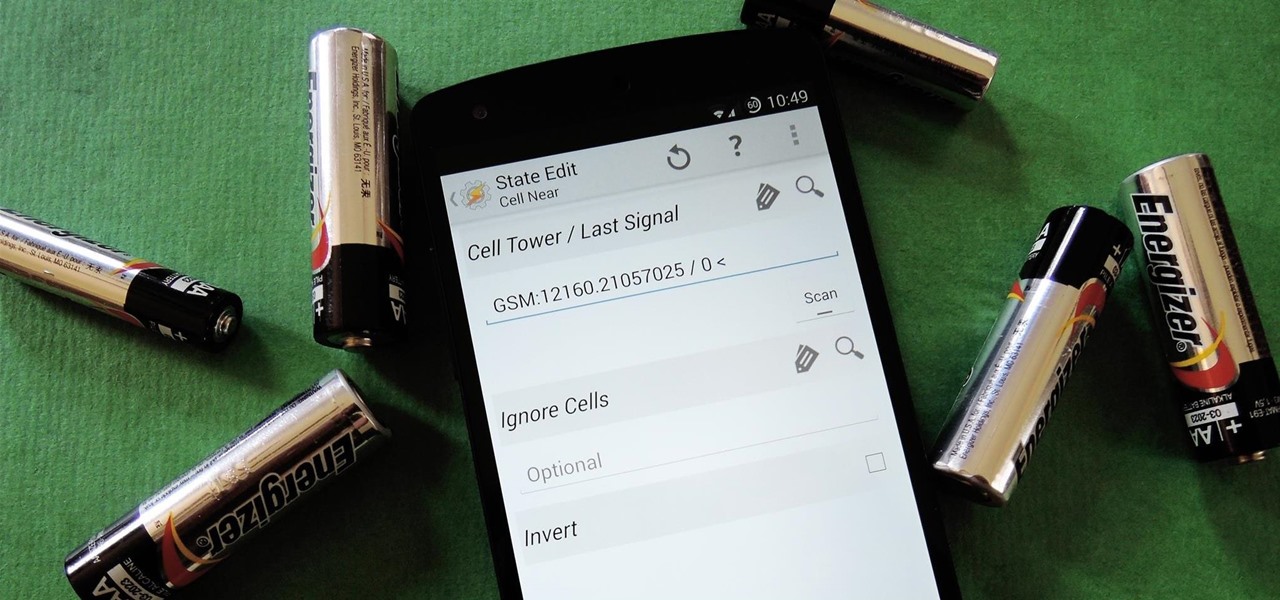
We live, work, and play in drastically different environments, so it only makes sense that we'd want our Nexus 5 smartphones to automatically adapt to our needs when in certain locales at certain times.

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

If you've ever used the automation app Tasker, then you know exactly how powerful the tool can be. If you haven't, suffice it to say that there's virtually nothing on your Android phone that Tasker can't automatically do for you.

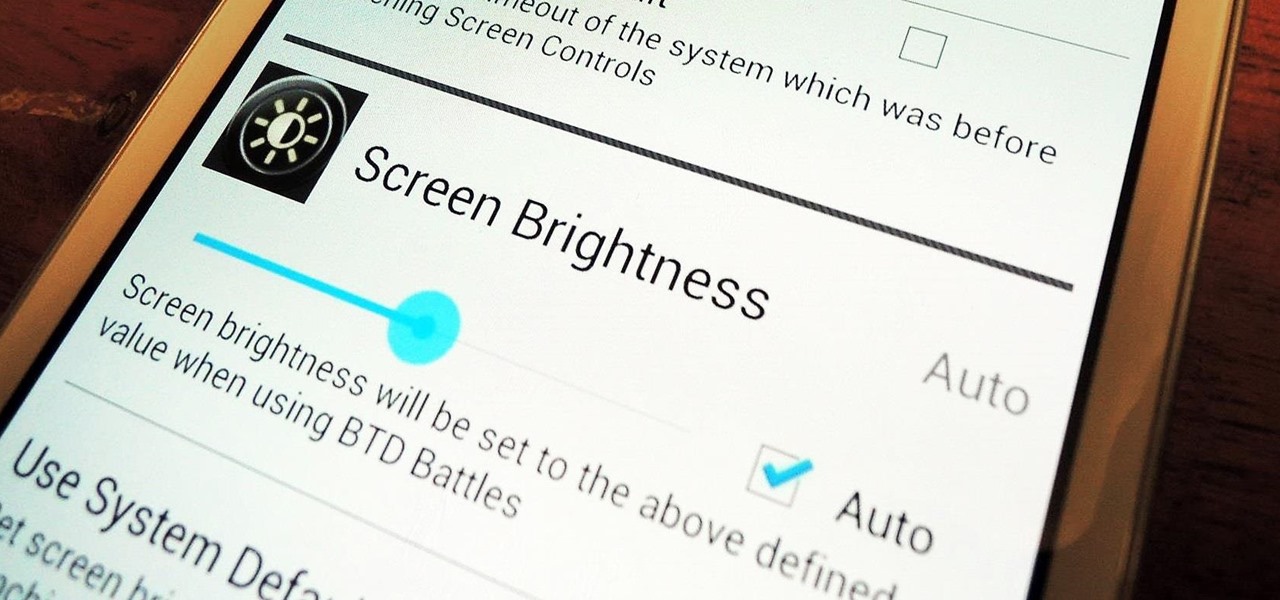
Adjusting the brightness on your Samsung Galaxy S3 can be a real pain sometimes. Each app you open may need a different amount of light to better optimize its use of the screen, and then you have to worry about it potentially eating up your battery life if it's too bright.

There's absolutely no shortage of flashlight apps on Google Play, so when one comes around that sports uniquely different features than the rest—it should definitely be noted. That's why I bring to you Ambient LED Flashlight, a new app for your Samsung Galaxy Note 2 by Android developer Jie Huang.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

There are plenty of useful shortcuts in Mac OS X, but not all of them are necessarily simple. You can use one of built-in shortcuts to take many different kinds of screenshots, but the shortcuts can be rather annoying to use because they require at least three different keys, which can be a little awkward to perform.

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

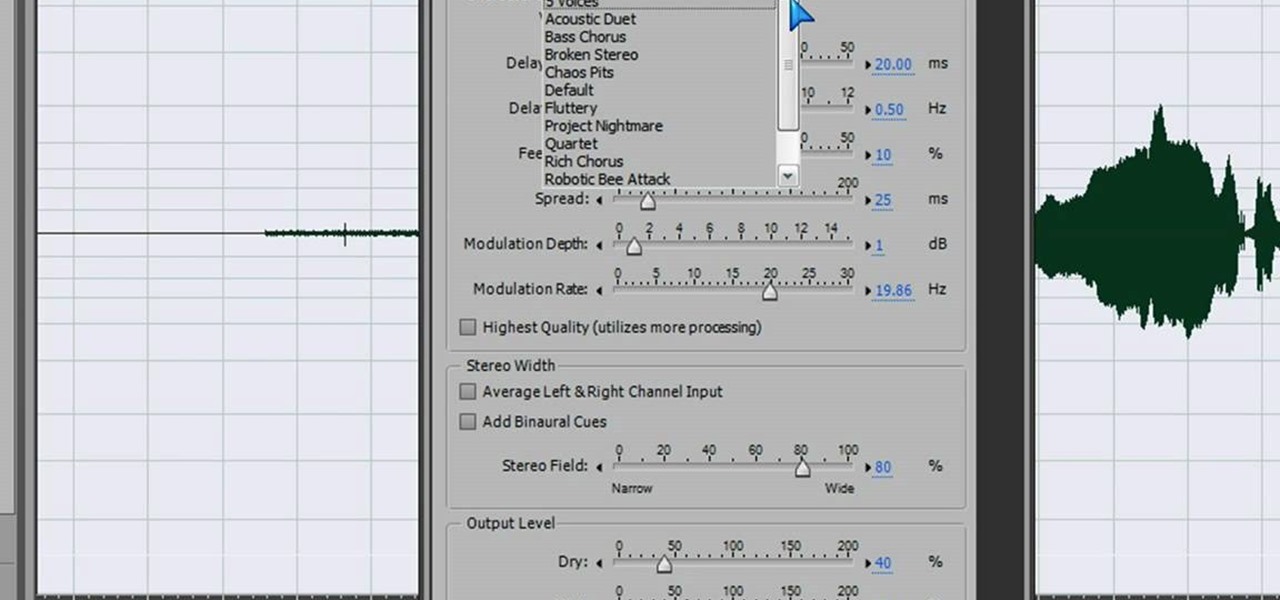
In this video we learn how to make a scary voice effect on Adobe Audition. First, record an audio that you made and open up Adobe Audition. From here, open up any other audio that you want to hear for the beat. Then, go to "generate" and then "silence. Put this to 1.5 seconds, then go to the end of your sound and do the same thing. This will make a good effect when you are editing and adding in echo. First, reverse the audio by going to "effects" and then "reverse". This will make it a lot ea...

Looking for a quick guide on how to generate 3D header and logo text in Photoshop CS5? This clip will teach you what you need to know. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

Wouldn't it be nice to know how many people actually visited your site each day, and how long they stayed there? Google Analytics is a great, free utility from Google that will tell you just that and so much more. In this clip, the Web Guru will show you how to use this program, generate and install an HTML code onto your site so that you can keep track of your visitors and demographics. This is a fantastic tool for advertising purposes and so you can see which content is working best for you...

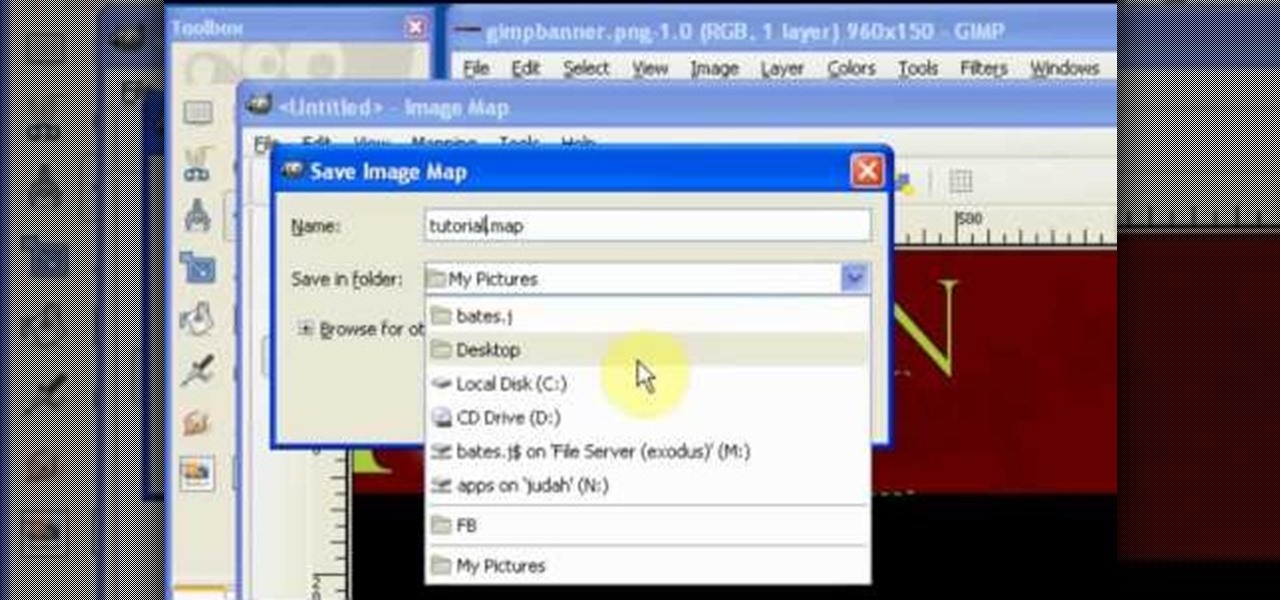
See how to use GIMP to generate a HTML image map in minutes. This mimics the slice function from Photoshop. Whether you're new to the GNU Image Manipulation Program, GNU's popular free graphics editor, or a seasoned designer just looking to pick up a few new tips and tricks, you're certain to enjoy this free video software tutorial. For more information, including detailed, step-by-step instructions, and to get started chopping up digital images yourself, take a look.

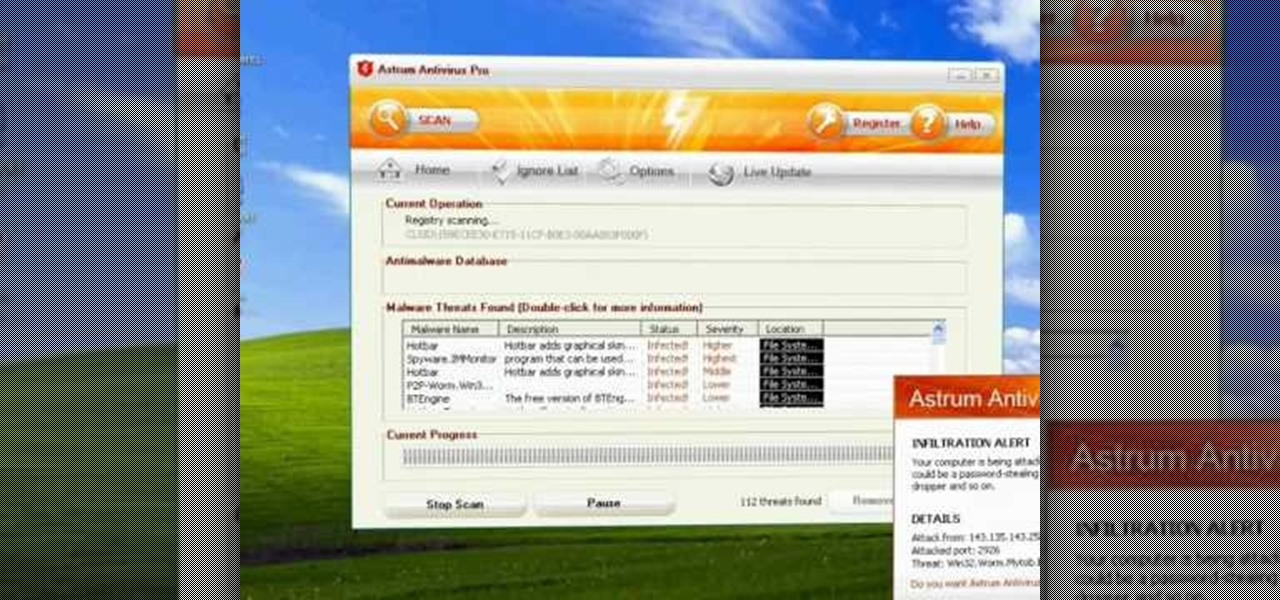
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...

Place the card in the center tip of your middle finger. The card should balance on your finger and you can test this by wobbling the card on your finger left and right without it falling off of your finger. Try to spin the card with your other hand. If it falls off your finger it may have been off center. Next, use your thumb, placed on top of the card to stabilize the card. Raise your thumb above the card. With your index finger, lightly pull the card toward your palm and generate a spinning...

This video shows the basics of multiplying integers. The main point that people can struggle with is the variation of signs. When multiplying integers you must always be aware of the positive and negative numbers. When you multiply two numbers that have the same signs, both positive or both negative numbers, this will always generate a positive answer. If there is one positive and one negative number this will always lead to a negative answer. This video shows very basic problems of multiplyi...

In this video the tutor shows how to make an ISO image file on a Mac. He shows what the requirements are to get started. He points to the disk utility program from where he points to the option where we can open a disk image from a folder. Now he selects the folder to which he wants to save the image. Now he guides us through the rest of the settings on how to prepare the image. Now we end up with an image file which is in the .cdr format. Now he shows some commands on the terminal through wh...

In this flash tutorial the instructor shows how to make a black and white mask animation. To do this, first start by importing your image into the flash tool and bring it on to the scene. The image should be wider than the scene. Now select and distribute the layers. Now convert those images into movie clips. Now go to frame 80 and add all frames. Get back to the first layer and create a shape that is the your mask. Now go to frame 40, select key layer and add free transform tool. Now, mask t...

In this tutorial the instructor shows how to convert a improper fraction to mixed number. In the example the instructor takes the denominator of the mixed fraction and writes it beside and keeps adding it self to the latest number and he keeps on doing that way generating a series until he reaches the value of the numerator. Now he counts the number of occurrences of the numbers in the series before the value of the numerator which gives the value of the whole number in the mixed fraction. No...

In this video the instructor talks about compound and continuous interest formula calculations. You need to understand the concepts of simple and compound interest. Only then you can understand what the bank is doing to your money which are in your bank account. Simple interest is a method where when returning a borrowed sum to some one you pay additional price for using the money all this time. Compound interest is a similar concept where you pay interest on the original sum borrowed, and al...

Check out this masterclass on Houdini 9.5 and how to rebuild the fire simulator. Houdini's Fluid Tools offer a powerful simulation environment for visual effects artists. Senior Mathematician Jeff Lait introduces you to the basic building blocks for generating fluids and low level tools that make it easier to control the simulations.

Most people don't use their cameras to make movies (really bad quality and a sort of user-generated content feel are probably the culprits) but cameras with a record function are great for those impromptu memory-making moments when your dog tries to do a handstand or your grandma unloads the biggest belch ever.

Get moving! Learn how to walk, run and jump your way through LittleBigPlanet. LittleBigPlanet exclusively for the PLAYSTATION 3. It lets you PLAY alone, or with friends, in a world of infinite possibilities. Run, jump, grab and swing your way thru imaginative levels and mini-games. If you're feeling creative, you can CREATE your own levels, enemies, obstacles and even storyline. Once done, SHARE them with our online community of thousands of User Generated Levels from around the world for

Stick it to them! Learn how to resize, rotate, and stamp your sticker collection in LittleBigPlanet.

Get some clothes on! Dress up or Dress down, learn how to express your own SackFashion for Little Big Planet on PS3.

This Houdini n9 software tutorial covers a very simple lighting and rendering scene to show the basic workflow for generating a PBR render. We use a digital asset to quickly establish a group of geometry to light. In the lesson we also add an area map so that we can extract the lighting information from it. There are two .rat files to experiment with, the seashadow.rat file simply provides a pattern. The st.peters_cross.rat is an HDRI image from the Debevec site. Watch and learn how to set up...

In this video tutorial you will learn about a very powerful feature in Houdini called Copy Stamping.

Continuing on with budget lighting, we explore using Fluorescent and LED lights, along with using available light, bouncing it with a reflector. These setups will work great for interviews, video casting, vlogging, and the likes. These lights use less power and also generate much less heat then big halogen work lights, and the price can't be beat. We also show the benefits of adjusting white balance on your camera, with lots of before and after shots. If you are shooting independent movies, s...

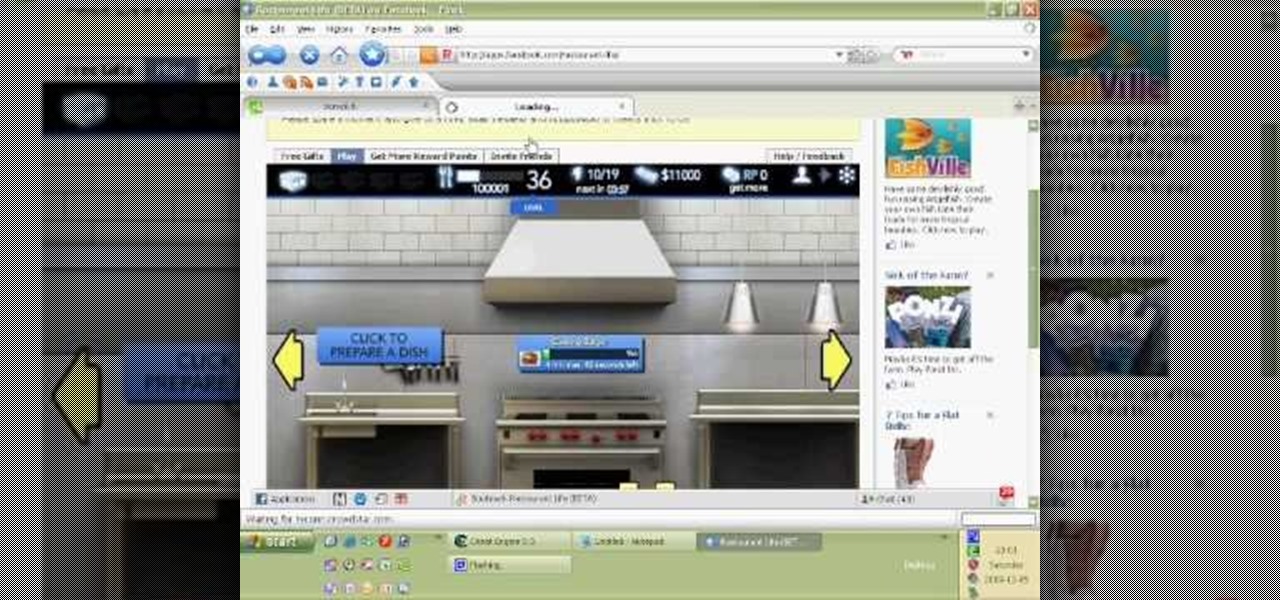
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

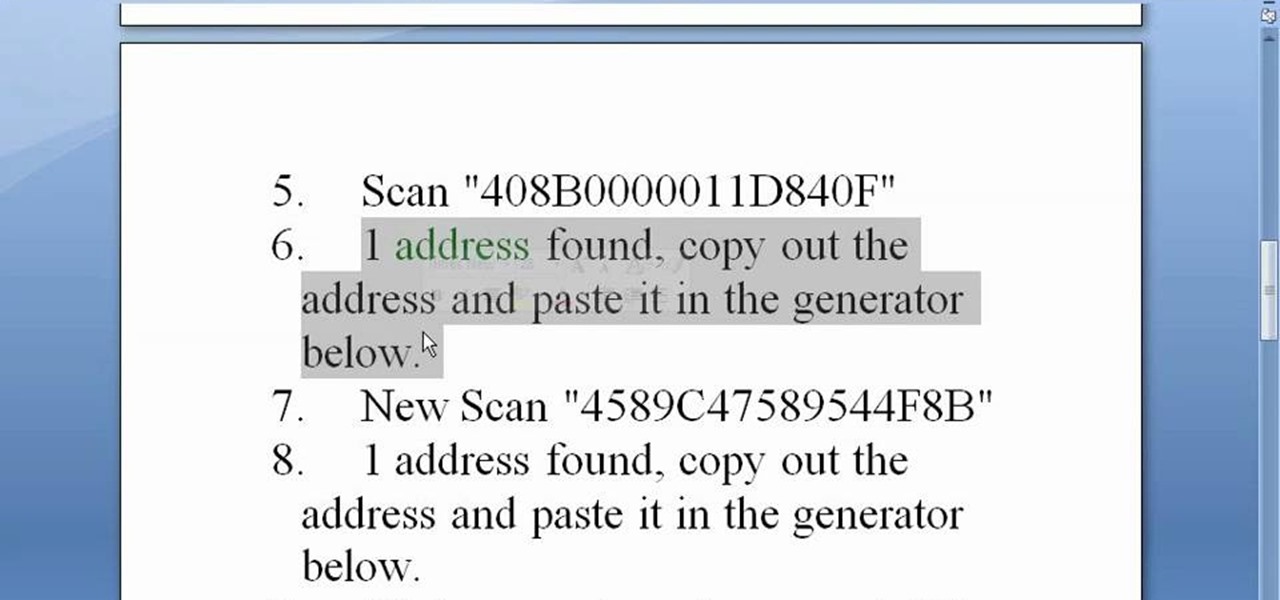
This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.

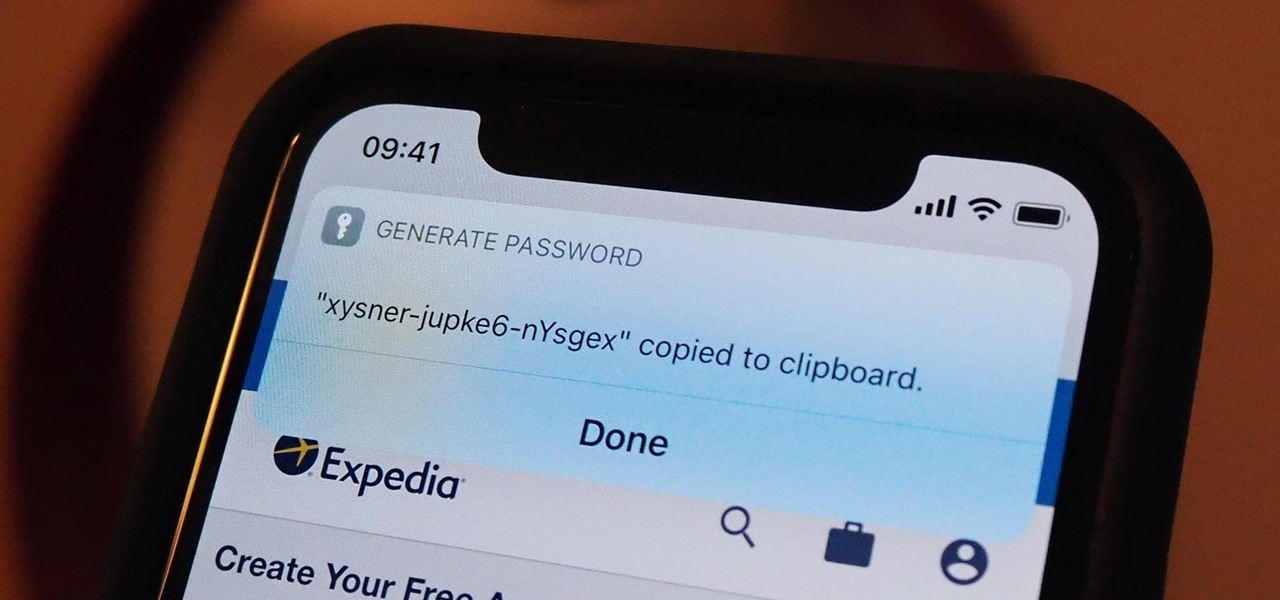
Apple's password manager, iCloud Keychain, lets you securely save important login credentials for apps, websites, and services that sync up across all of your Apple devices — iPhone, iPad, iPod touch, and Mac. One of its biggest highlights is that it can create strong passwords for you. Unfortunately, it doesn't always work, and in those cases, there are other ways to generate random, strong passwords.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

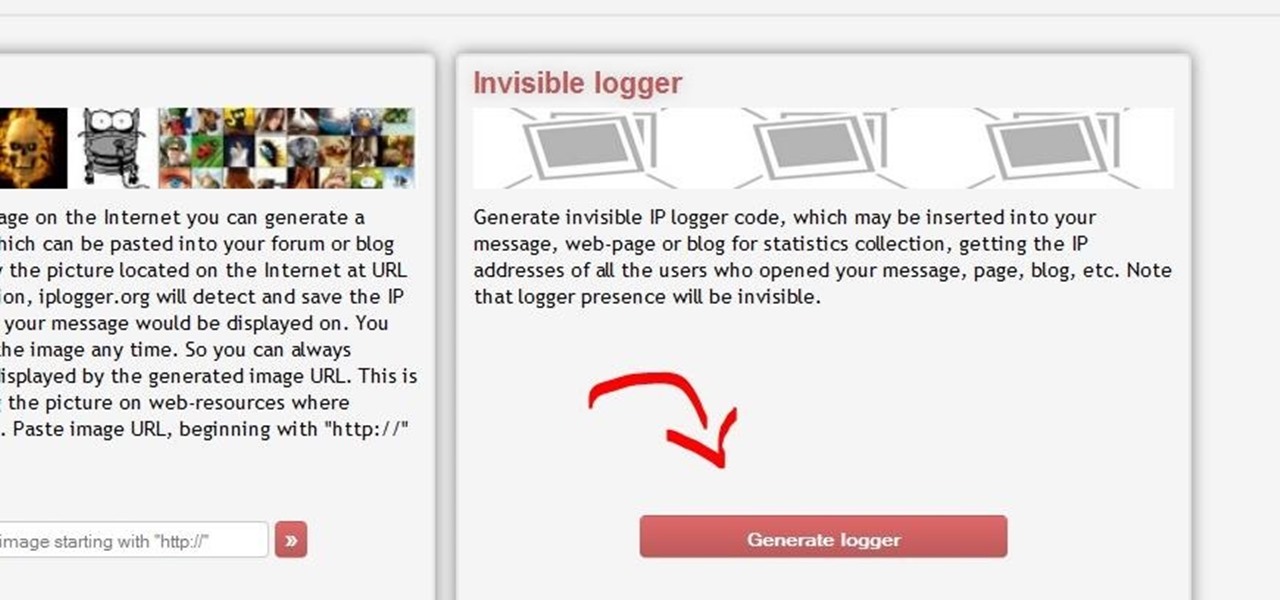
This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).