When it comes to Android automation apps, Tasker has never had much competition. But considering how difficult it can be for a novice user to get the hang of things, and factoring in Tasker's drab and complicated interface, there's definitely room for another developer to step in with a Tasker alternative.

Those of us with girlfriends understand that in order for the relationship to run smoothly, you have to keep your woman happy and let her know that you're thinking of her—even when you're not.

When you're not using your phone, it doesn't make much sense that it would be wasting power by maintaining an internet connection for the inside of your pocket or purse. Well, perhaps you need a little bit of intermittent data here and there so that apps can update themselves in the background and still post notifications, but it doesn't need to be constant.
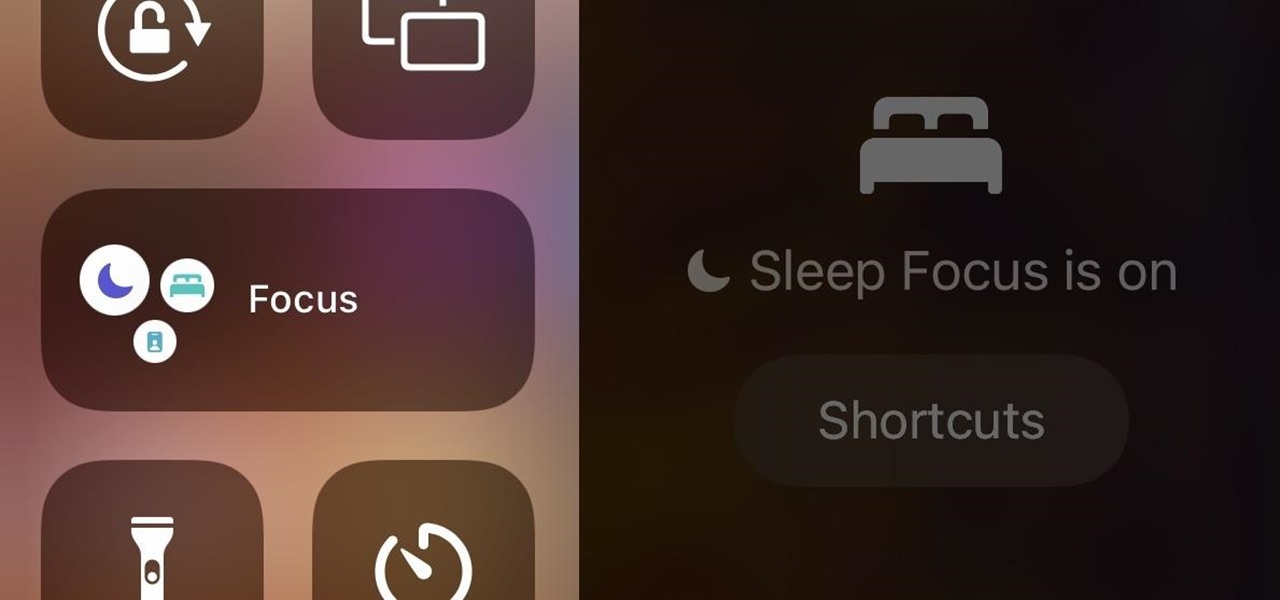
In iOS 15, Apple unveiled a new feature called Focus, an extension of Do Not Disturb that lets you focus on the one thing that's important at any particular moment. It does so by minimizing distractions from your iPhone and other Apple devices, but there's a lot you should know about setting up and using Focus on your iPhone or iPad before you dig in.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.
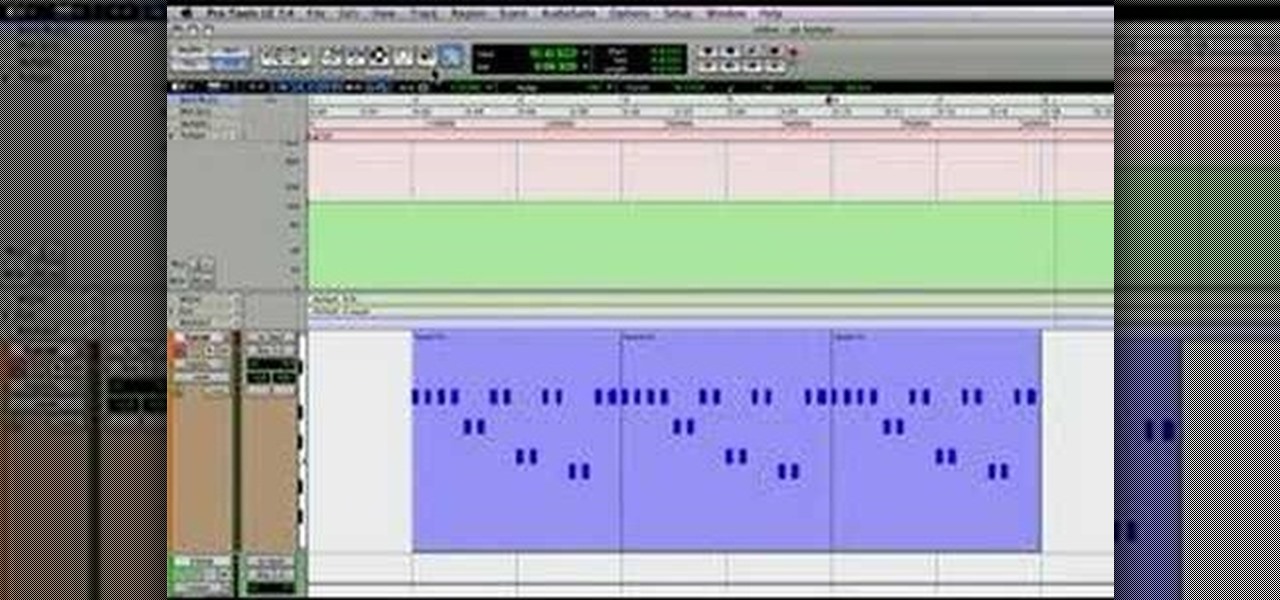
Connor shows you how to automate the tempo map in Pro Tools LE. This sounds simple, but sometimes in Pro Tools the simple tasks aren't so easy to see. Let Connor show you the way and you'll be automating tempos in Pro Tools in no time.

Photoshop offers lots of tools for automating selections, but two stand out from the pack: The first, Refine Edge, lets you modify your selection using five different parameters and preview the results in five different ways. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, i...

This clip demonstrates quick and simple QuicKeys workflow that automatically hides other Mac OS X applications when a specified application is opened. This quick clip presents a general introduction to creating macros and automating processes within Mac OS X using QuicKeys 4. Whether you're new to Startly Software's popular macro and automation application or are merely looking to pick up a few new tips and tricks, you're certain to be well served by this free video software tutorial. For mor...

This how-to video produced by Photoshop Universe gives step-by-step instructions on how to batch automate a process in Adobe Photoshop. With this tutorial you'll be able to learn to correct white balance, enhance colors, resize, and save for the web whole folders' worth of images in one go. The first step to doing this is to open up one of the images in your folder and correct the white balance, enhance the colors, resize the photo and save. The next thing you want to do is to record all of t...

This quick clip presents a general introduction to creating macros and automating processes within Mac OS X using QuicKeys 4. Whether you're new to Startly Software's popular macro and automation application or are merely looking to pick up a few new tips and tricks, you're certain to be well served by this free video software tutorial. For more information, including detailed, step-by-step instructions, watch this video guide.

HowToMakeAnything describes how to make Script work in Sony Vegas. Script is a way of automating a normally cumbersome process. Select events from Cursor, add regions to add, fade effects etc to the clip. That may also be selected from Tools Menu, then Scripting. Drag the desired two or three scripts to the folder of Script menu in Sony Vega Pro 8 available in C drive and rescan script menu folder. It is to be noted that adding hundreds of clips can also be done to the folder if one so desire...

There are many reasons to use Filmic Pro if you're a mobile videographer. Chief among them is its automated controls, called "pull-to-point" sliders. These pull-to-point controls not only allow you to manually adjust focus, zoom, exposure, ISO, and shutter speed before and during the action, they also let you set start and end points to automate each function, leaving you free to focus on filming.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're not home.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Though not as flashy as Face ID and other features, Low Power Mode has become one of the unsung heroes of iOS. When you're away from a charger, enabling this feature will dial back performance and networking to help you eke out up to three extra hours of battery life. If your device is jailbroken, you can even automate Low Power Mode to ensure your battery never dips to critical levels while out and about.

Automating tasks on your Samsung Galaxy Note 2 is nothing new. Everything from adjusting screen brightness, to turning on the flashlight, to saving Snapchat pictures can be done automatically with the help of a few function-specific apps. The only problem with task-specific apps is that you have to download a handful of them to get everything you want, which can quickly add up. Now, thanks to AutomateIt, you can clean up your app drawer on your Note 2 and create loads of custom tasks using ju...

When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

Jamie Zawinski uses a command line to control his curtains.. ..How cool is that?

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. There are few things more tedious in Minecraft than collecting items from your chicken, cow, and sheep farms. No one wants to take the time dealing with animal mobs even in the smallest of Minecraft farms. The answer? Automated Minecraft animal harvesters.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Harvesting items from animals no longer requires wasting precious time chasing after them. During last Saturday's Weekly Workshop, we built a few different kinds of animal harvesters that worked in different ways, but for this guide we will be building the most compact and easy to use harvesters we made over the weekend.

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

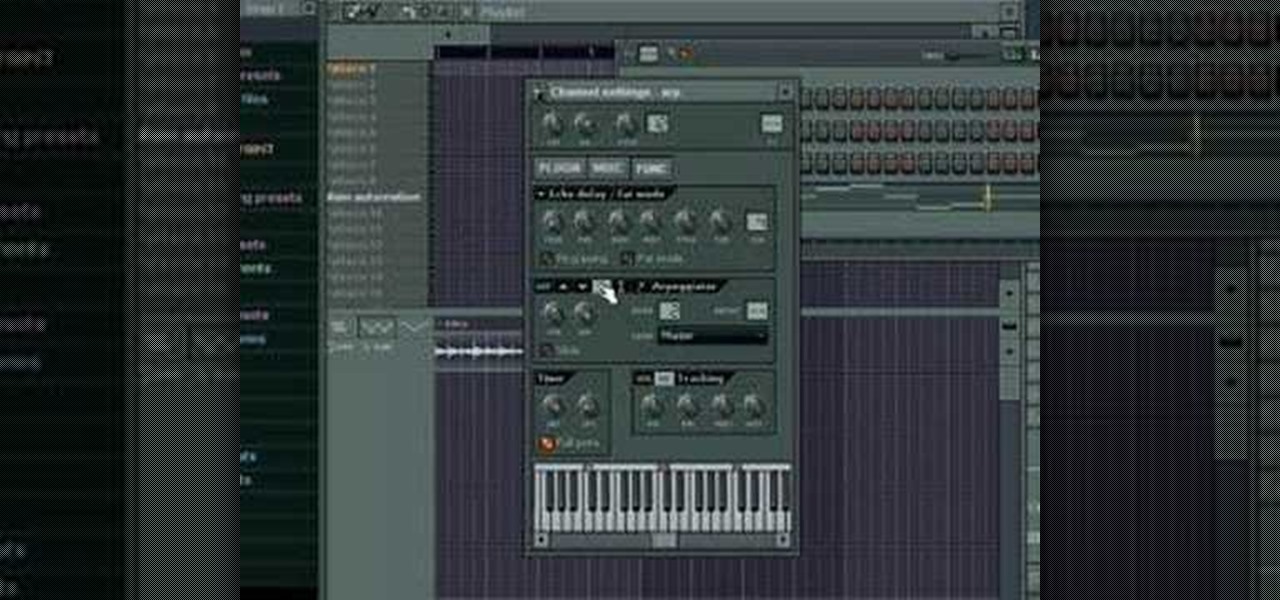
This music production software tutorial shows some ideas and inspirations in using, automating, and humanizing the arpeggiator to make believable-sounding patterns in FL Studio (fruity loops). See how to rock the arpeggiator!

In this clip, you'll learn how to go about automating basic parameters within Autodesk Maya 2010. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the Maya 3D 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using this trick yourself, watch this free video guide.

QuicKeys 4.0 includes a nifty feature for quickly automating a task. This quick video tutorial will show you how to use the program's instant recording and replaying feature. Whether you're new to Startly Software's popular macro and automation application or are merely looking to pick up a few new tips and tricks, you're certain to be well served by this free video software tutorial. For more information, including detailed, step-by-step instructions, watch this video guide.

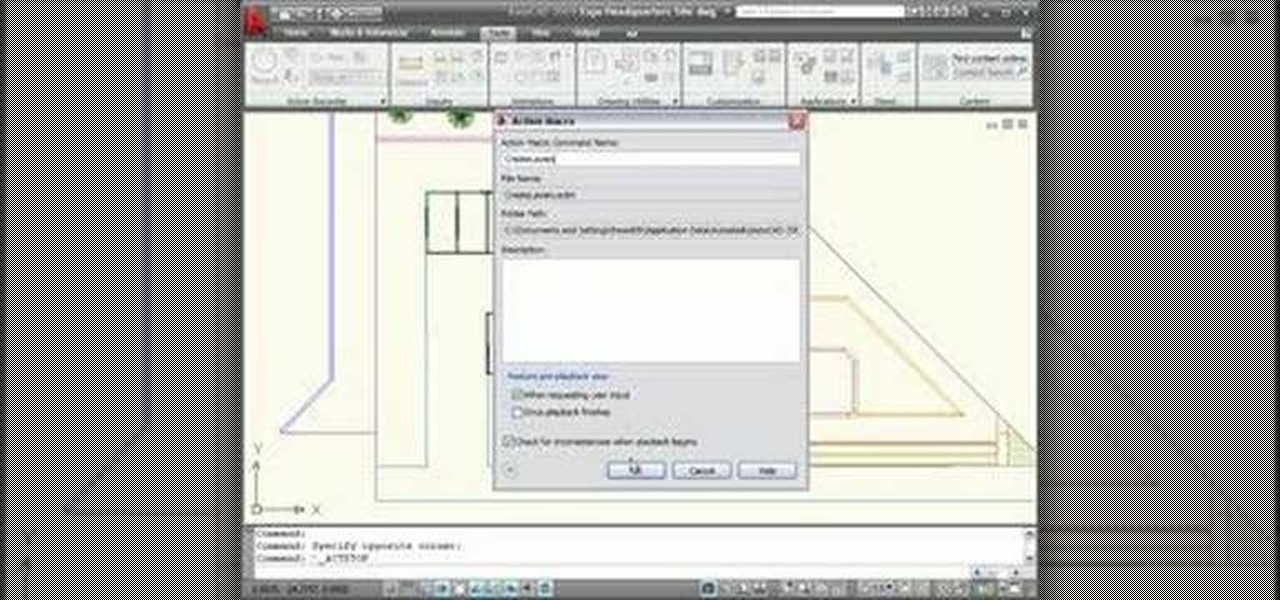
Heidi Hewett demos the Action Recorder feature in AutoCAD 2009. Recording actions with the Action Recorder can increase your productivity by automating repetitive tasks you have to perform on every AutoCAD 2009 drawing. You can record actions from the command line, toolbars, ribbon panels, and more. See how in this AutoCAD 2009 lesson.

Minecraft presents a vast, seemingly never ending landscape for exploration. How do you cover all of that ground? This video will show you how to build a train station, including a minecart call button and automating station. Watch this video to learn how to make a minecart train station in Minecraft beta.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Clash of Clans is one of the most successful games ever to come out for Android and iOS. It has been downloaded over 50 million times from Google Play alone, and shows no signs of decline.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

After playing Mario Kart Tour for a little while, you'll notice it's a bit different from previous games in the series. The biggest change is how they've deferred to new players by automating many of the controls. But what if you want the traditional experience? We've got you covered.

Getting on the phone for customer service can be extremely frustrating. First you've got to find the correct phone number for your region (good luck trying to get customer service from a sales department), then you have to listen to the annoying automated system to navigate your way to the department you want. More often than not, you'll be stuck with some elevator music while you wait to speak to an actual human.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.