
How To: Build a Sexy Floating Island
Hey guys, I was building my floating island earlier today (and having a quick look at the competition) and I came up with a couple of hints and tips that will really improve your islands.


Hey guys, I was building my floating island earlier today (and having a quick look at the competition) and I came up with a couple of hints and tips that will really improve your islands.
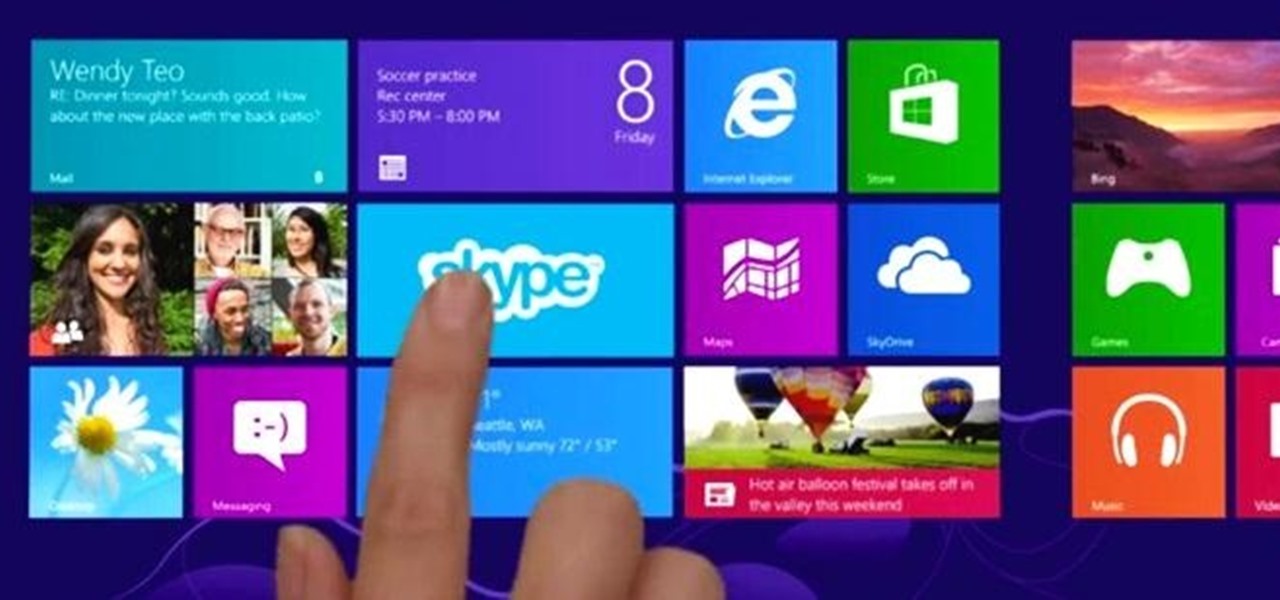
Windows 8 has been reimagined to take full advantage of touchscreen devices as the "future" of computing. A few years ago, touchscreen devices were super buggy and only played well with smartphones, but with the advent of the iPad and a ton of other tablets, touchscreen capabilities have spread to full-sized desktops and even televisions.

Before my time, people used to listen to music recorded on these things... I didn't really know what this thing was until my parents clarified and told me that they were called cassette tapes. These "cassette tapes" were utilized to store sound recordings on either side of the tape, which could usually hold between 30 to 45 minutes. I laughed at that information as I took out my iPhone 5 (roughly the same size), which can store roughly 40,000 minutes worth of music.

Small containers are useful for many things. They're good for storing snacks if you have children, as well as holding coins or odds and ends. But those regular store-bought containers are lame—who wants to keep their stuff in a Tupperware dish or old butter container?

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

This tutorial for Sony Vegas 7 helps you utilize keyframes and create even better masterpieces!

Learn how to utilize this ankle bounce exercise as a part of your ladder training workout, geared at improving your athletic ability.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create a Times Square billboard in Photoshop.
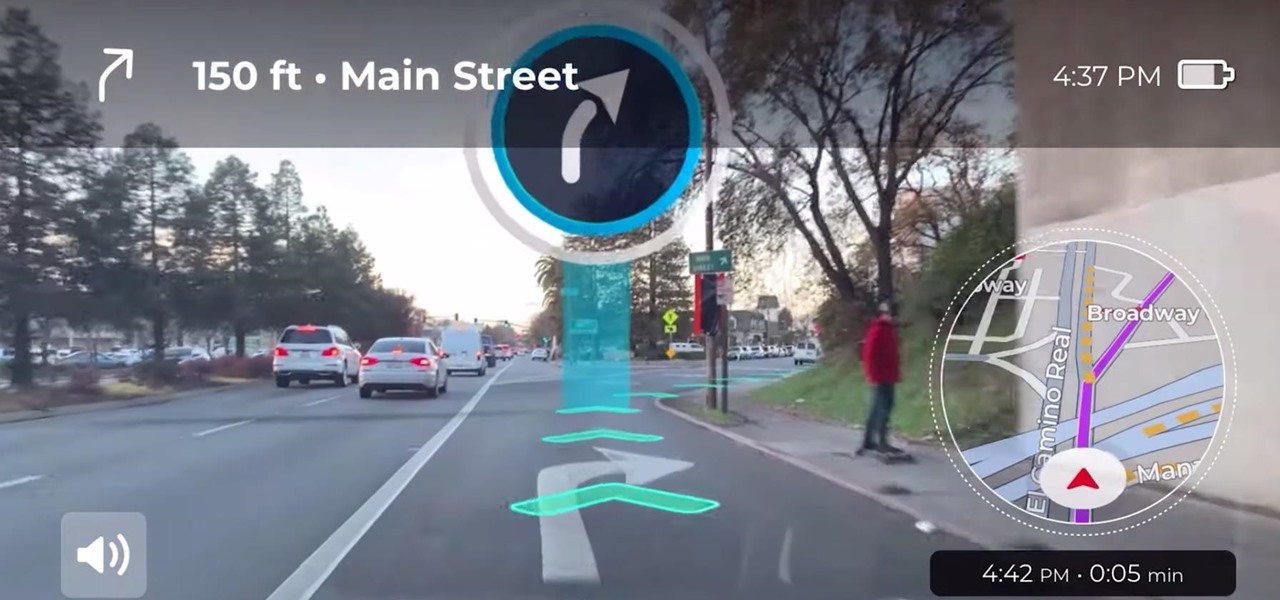
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Mobile augmented reality pioneer Blippar has now completed its fall from hopeful AR startup to the immersive computing history books.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.

Today it was revealed that Avis Budget Group will now support and maintain Waymo's driverless car fleet in Phoenix, the company's first public trial of self-driving cars. This is an unprecedented partnership in the autonomous vehicle field and conveys the steps driverless companies are taking to make their vehicles more accessible to the public.
The driverless competition is heating up as Detroit automakers attempt to woo tech talent away from some of Silicon Valley's biggest players.

Welcome back, my hacker novitiates!

Traditionally, incorporating loops and grooves can translate into hours of hard work just to get the loop to fit your song's tempo and timing. Help is on the way from the Propellerhead's ReCycle which gives you full creative control over utilizing your looped material. Join electronic recording artist David Alexander as he shows you how ReCycle has revolutionized using sampled loops. In this episode, David shows us how to Chop Up A Complex Loop.

Analog reel-to-reel tape is some of the most in-demand recording equipment today. Learn how to use a reel-to-reel tape machine in this free video series that will allow you to utilize this piece of musical recording equipment.

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

The basics of two-dimensional design utilizes design elements such as space, balance and line. Learn foundational design skills with this free art video series.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Native screen recording, one of the hottest features that Apple included in iOS 11 and later, is easily started from the optional Control Center toggle on your iPhone. From there, you can stop recording from the same place or from the red status bar or bubble. It's a very convenient addition to iOS, but there's one obvious downside — that red indicator, which can appear in your recordings.
BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!