With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

I'm one of those types of people who waits until the very last minute to find a Halloween costume, and thanks to last year's attempt at buying one at a local costume shop the day before Halloween, I will just settle for the things I have lying around in my house from now until eternity. It's like Black Friday chaos, only with more gropers.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

If I could only eat one food for the rest of my life, it would definitely be potatoes. In fact, when I recently saw The Martian, I didn't feel that badly for Matt Damon. I mean, sure... he was stranded on a hostile planet, millions of miles from home. But he got to eat potatoes all the time! Pretty fair trade, if you ask me.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Elaine gave Whatley.

Disney Plus shows WandaVision and Falcon and the Winter Soldier are both streaming hits, but the two series could not be more different in terms of giving fans a taste of the Marvel Cinematic Universe.

The Apple ecosystem might be strong, but so is the pull from devices outside Cupertino's walls. If you've ever felt curious about what life could be like with a Samsung Galaxy smartphone, be that an S21 or a Note20, you don't need to make the switch to know. In fact, you can give it a go right on your iPhone.

Are you one of those people that waits until the last minute to come up with a costume for Halloween? Unless you're a makeup artist, have a ton of money, or are ultra-crafty, coming up with a good Halloween costume is always a low-priority task. That is, until it's Halloween and you're having a panic attack.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

With the list of available mobile apps for moviegoers constantly expanding and improving, seeing a film at your local theater has never been better. With the right apps for your iPhone or Android phone, you can research movies, find out if showings are sold out, reserve seats, save money on tickets and concessions, preorder popcorn and soda, and even find dull bathroom-worthy scenes.

With all the time most of us spend on our phones each day, wouldn't it be great if we could get rewarded for our addiction? Well, we can, thanks to various iPhone apps out there that can help us make a quick buck, earn cash back, donate freebies to charity, get complimentary cryptocurrency or stock, and receive other types of rewards.

RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

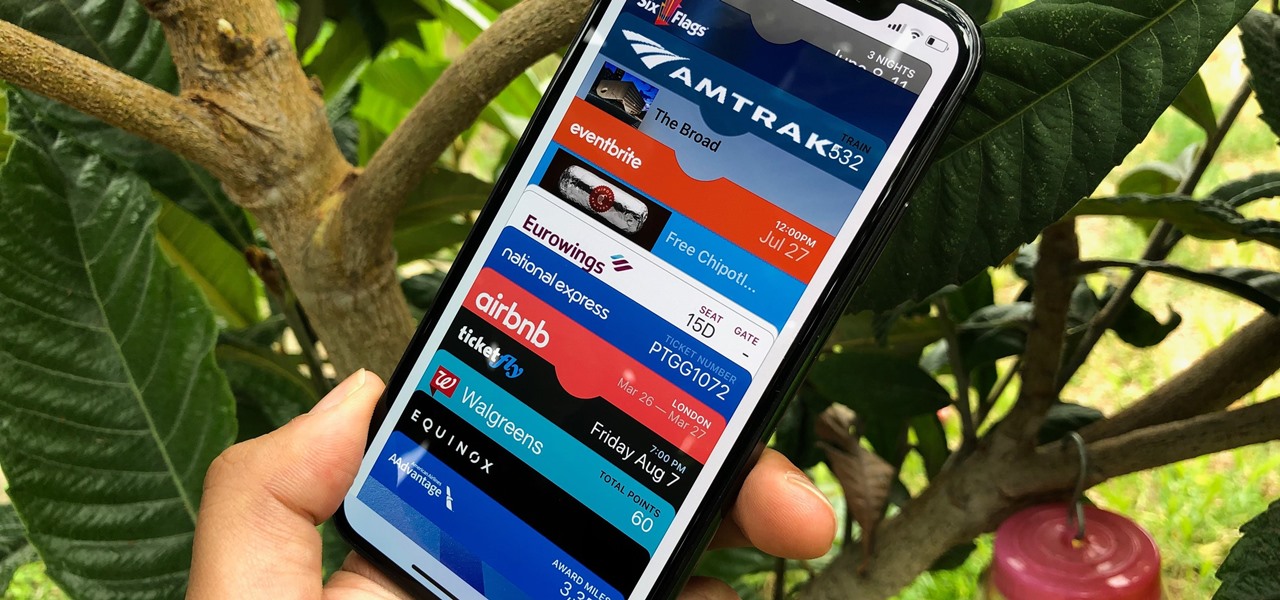
The Wallet app on your iPhone can be used to store and access event tickets, loyalty cards, boarding passes, gym memberships, airline miles, gift cards, coupons, and more — all in one centralized place. Before doing so, though, you must add your passes to Wallet, and there is more than one way to do it. However, not every pass can be added using all of the available methods.

Don't be fooled by the fancy monocle: this servo-powered serpent is as American as Apple Computers. So American, in fact, that his creators at Carnegie Mellon decided to christen him Uncle Sam. Boasting more points of articulation than a GI Joe, Sam's hobbies include crawlin' in the dirt and climbin' trees.

Mike from the SubStream's "Film Lab" have some tips regarding a few in-camera trick shots, specifically... the dolly zoom.

Would you think that you could draw a cartoon duck just by writing the word duck? Or Uncle Sam from the letters US? Well, grab a pen and a piece of paper and get ready to draw. All you need is a pad of paper, pencil, marker, colored chalks or colored pencils, and an eraser. To make a cartoon duck, first, write the word “DUCK” in all capital letters. Draw a face in the “C” by putting in an eye and an eyebrow. Connect it to the “K,” and close up the bottom and top of the “K.” Connect the “C” to...

Back when I was a Windows user, I know I'm not the only one who has experienced password loss—that moment where you just can't remember your password. Sometimes it happens to the best of us. So, how can we get into the system without paying a local geek or geeksquad to do it? First, we have to look into how Windows stores their passwords.

Can you pull 33x your body weight? Sam Noyoun can. Uphill no less.

Here are 7 clips from the movie "Charlie St. Cloud" Charlie (Zac Efron) teaches Sam (Chris Massoglia) how to hold a baseball. .

When Windows stores a password, it is done so by hashing the password in an LM hash and putting it in the Windows SAM file. In the scary moment that you lose your password, but don't want to pay some geek to have full root access to your computer, you need to recover it using Ophcrack. Ophcrack doesn't remove the password, or bypass it, it cracks the password hash using rainbow tables.

Purple Hyacinth Look that Purple Hyacinth will soon bloom

hi i'm sam hinson and i have another idea for u guys. it's called seat belt death trape and well you put super glue in the buckle and have hem drive down a big hill and set the breaks up o that it seems as though it is broken. o the person is now traped in the car but at the last min one of the guys uses a controler to make he brakes work. this idea ame from sam hinson and richard barnum we hope to one day work with the jackass guys and get paid to come up with awsome ass stunts and funny ass...

Mike from thesubstream's "Film Lab" have some tips regarding a few in-camera trick shots, specifically... the dolly zoom.

Beautiful Eerie Cinematography and Fantastic Editing. This film by Sam Spreckley an artist out of Scotland. His experimental film shown above is quite abstract yet moving none the less.

Think white kids can't dance? Meet Jeff. This 17 year old from New Jersey can move.

Sam Veale shows you how to tie a knot in a rope using only one hand and his Brylcreem powers Tie a knot with one hand.

Want to get better at seeing in the dark? This video by Sam Noyoun will give you ten steps to improve your natural night vision. This method is used in the military to help soldiers at night time. Improve you night vision naturally.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Love old-school games like Pac-Man and Space Invaders, but don't have the extra space for an arcade machine? Get the best of both worlds (and save some cash) with this DIY Arcade Coffee Table built by Sam Wang. He started with just an ordinary IKEA table and drawers, then cut out a space for an LCD monitor. The controls (including joysticks!) are mounted on the drawers so that when they close, it just looks like a normal coffee table. Once everything was in place, he added a glass table top, ...

The Netherlands are a hotbed of indie game development, which seems appropriate for such a brilliant and eccentric little nation. Two man Dutch indie developer Vlambeer have found themselves in the news more often than most companies of their size, thanks to two great games and a third on the way.