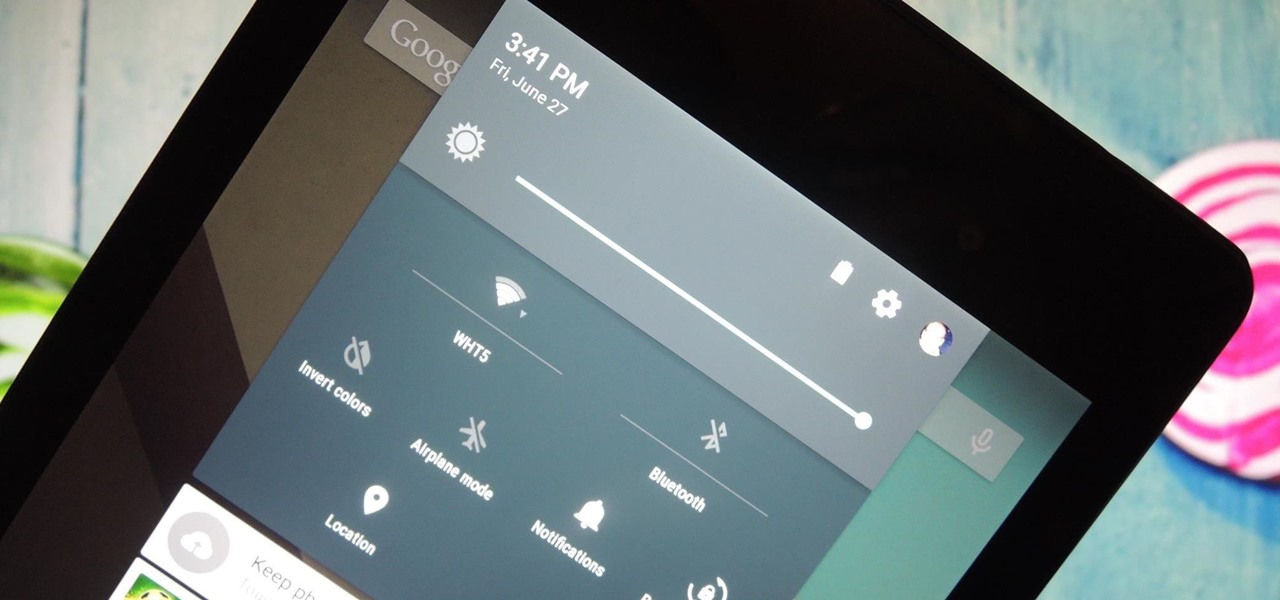
It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Rather than just use the stock Apple keyboard, iOS 8 now lets you use keyboards from TouchPal, Fleksy, SwiftKey, Swype, and more. I'll be showing you how to set up a third-party keyboard on your iPad, iPhone, or iPod touch, as well as giving you a firsthand look at TouchPal's keyboard for iOS 8.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:
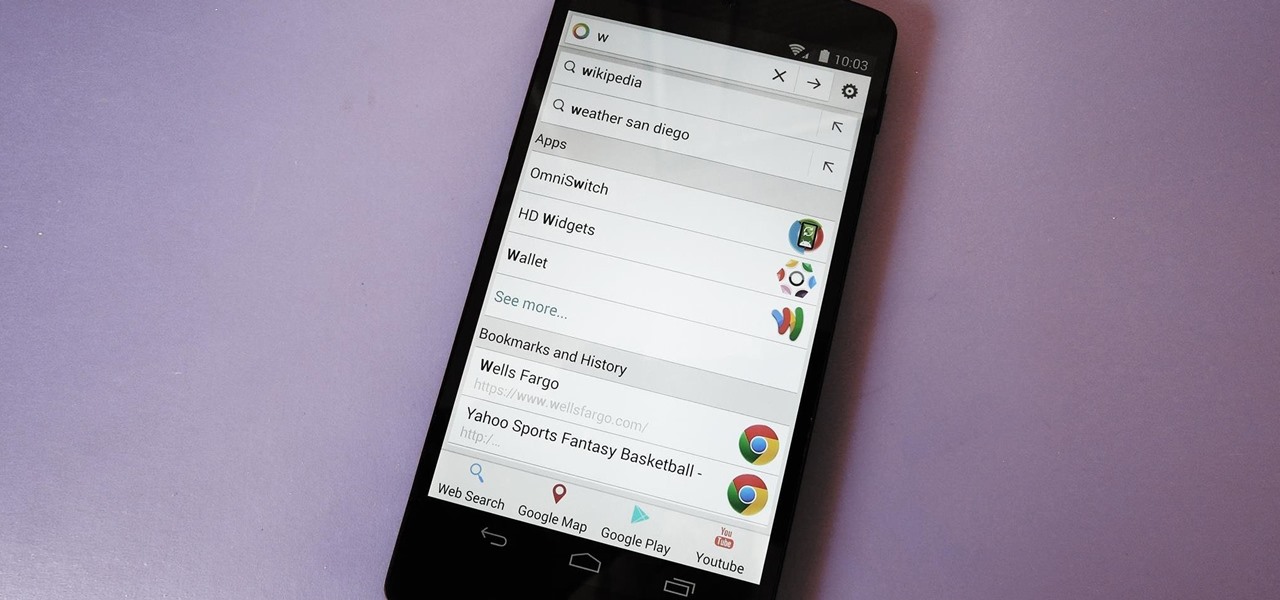
Prior to the release of Android 4.0, most devices had a dedicated search button. This functionality allowed you to search Google from your home screen and app-specific content from within any app. Eventually, though, this dedicated search button was ditched in favor of an icon in the action bar of apps, and a search bar on the home screen.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Loving parents can suffer bouts of insomnia when their children leave the house. Not just when they move out, but when hanging out with friends or during out-of-town weekends. Others may worry about their significant other who has to work late all week and their only option for getting home is that sketchy nighttime bus.

There really isn't any custom manufacturer skin, like Sense, that can match the clean look and fluidity that comes with stock Android. HTC knows this, and they, just like Samsung, include a Google Play Edition version in their flagship lineup.

This week, Google sidestepped their usual "Update Wednesday" strategy by dropping a huge update to their Maps app for both Android and iOS. We're accustomed to seeing new features and bug fixes to their stable of apps on Wednesdays, but today's Maps update was presumably big enough to get its own release day (it's Tuesday, folks).

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

It can be a pretty exasperating ordeal to hunt for one image on your tablet when you have hundreds and hundreds of photos in your gallery. Luckily, there are ways to make this a pain-free process on your Nexus 7, as well as make sure it's never a problem in the future.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

One of the best-selling video game consoles of all time is the Nintendo Entertainment System, better known by its acronym, NES. However, cartridge-based gaming consoles are a pain now when compared to the newer download-and-play alternatives.

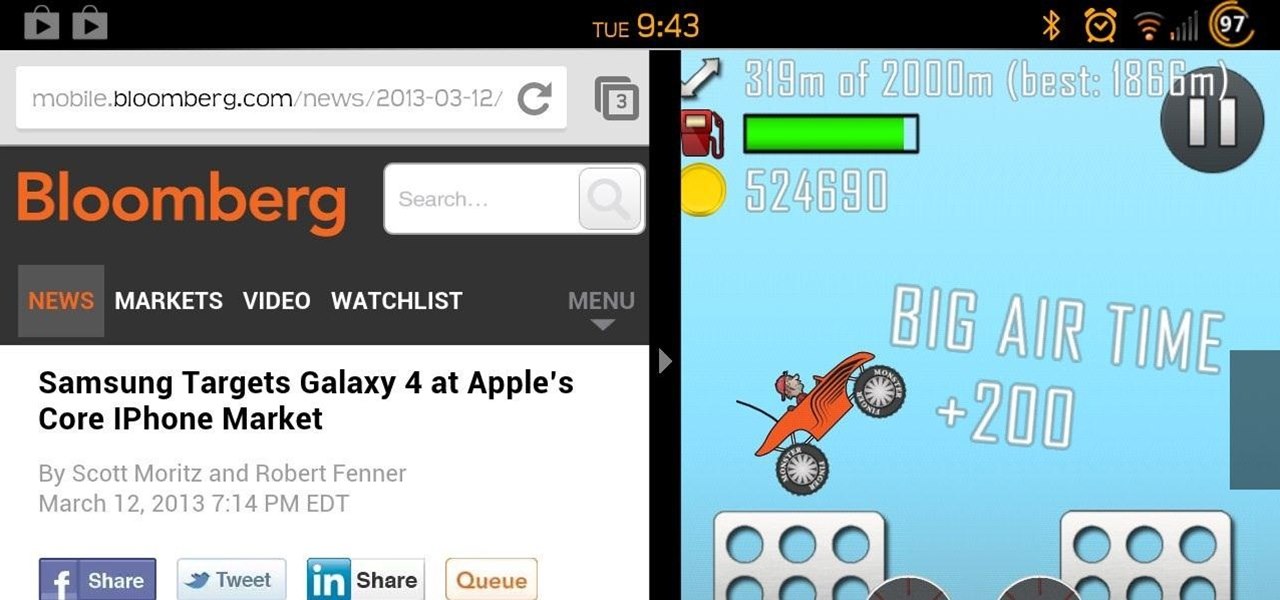
While many of the U.S. carriers have updated their Samsung Galaxy S3 devices to Android 4.1.2 already, one major absence from the upgrade is Samsung's Premium Suite. One of the coolest features from the Premium Suite is Multi-View, a function that lets you truly multitask by running two apps at the very same time—right next to each other. As you can see above in the left image, I have both Pandora and Spotify running. Why? Because why not?!? On the right, I have YouTube on top and Maps on the...

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Sometimes the hardest part about getting your minecart rolling is the beginning takeoff. Have you ever started a minecart on a hill, and then tried to jump into it as it started moving, only to fail and watch it slowly dwindle into the distance?

There are a number of different techniques for building underwater in Minecraft. The easiest is to fill a room with wood or leaves, then set them on fire. It'll burn down, leaving a pocket of air for you.

As I said before in my earlier post on how to make a two-tone doorbell, sound is more than just music. Note blocks can create a wide variety of notes and sounds, and those can be used for more than just making a stirring rendition of "Still Alive" from Portal.

In last Saturday's workshop, the tutorial was on the ABBA switch, so named because it fires redstone pulses in A-B-B-A order. While the turnout was low, it was a really productive workshop! We experimented with a lot of things and had a great time. Hopefully you'll consider joining us next time!

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

There's no shortage of ice cream recipes out there, but one ice cream shop in London has found a unique recipe to sell to its customers, and of course it's controversial—breast milk ice cream.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

In this video clip series, our expert will demonstrate the basic knowledge you need before adding an outlet in your home. Which tools you will need, how and where to drill, safety instructions and box installation instructions are included. Additionally, you will learn how to strip a wire and test for connectivity.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

Read palms for success in the hand. To focus mainly on business or workplace look to the mound of Jupiter, which should be prominent. Additionally, the first finger should be longer. A longer first finger is as long as the third finger. This shows someone who is ambitious, connected with work, and authority over others.

In these instructional video dance lessons, our expert will demonstrate intermediate-level Irish step dances, including treble shuffles, cuts, kicks, and hop moves, as well as combination clicks and stamps. Additionally, you will learn how to do the butterfly combo, complete with tips and suggestions for your own practice routines.