Learning how to play guitar, keyboards, bass, even singing, you have to train your ear. Being an intelligent musician and being able to convey ideas is INCREDIBLY important in any professional situation. Learning how to hear various intervals from a root note will open up new avenues of understanding, playing by ear and more! In this video you will get a lesson on intervals as well as some home work to practice with!

Get in shape and tone your body by getting in that pool for a swim! There's nothing better for your body than swimming and there are numerous techniques and avenues for the swimmer who wants to get in better shape. In this video, get expert tips and advice on how to get in shape with the help of swimming!

Crackled glass has made its appearance in lots of cultural avenues, including nail polish (remember the crackled nail polish trend popular a few years back?), glass designs, and now, cards.

With the economy looking more sour than Lindsay Lohan at her latest party, finding a job means exploring every avenue possible. This means thinking about doing job training to both expand what you know and to possibly work in a field you never considered before.

Are you sitting alone on a Friday night wondering why you haven't met Mr. Right yet? Well that may be your problem right there - you're just sitting and not actually putting yourself out there! If you're usually super busy at work and other commitments, then you're probably dreading the thought.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

After Uber noticed that if you walked to a more convenient pickup spot — instead of your exact location — that it would save you time and money, they decided to make a change to their system.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

Overweight kids often become overweight adults. New research suggests a couple reasons why and suggested that there may be ways to intercept that fate.

While the notch on Apple's newer iPhones started a wave of notches across the smartphone market, there are still plenty of users who don't like screen-obstructing zone up top, and you may be one of them. While it may soon disappear in future iPhone models, or at least get smaller, there are things you can do to hide the big notch you have right now.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

If you’re planning to hold a party this October, what better event to model your event after than Oktoberfest? The German beer festival began in Bavaria, Germany in 1810 to celebrate a royal marriage. Since then, it has been celebrated annually by millions of attendees these past decades and has spread throughout the world. Of course, Oktoberfest would not come to be without the beer.

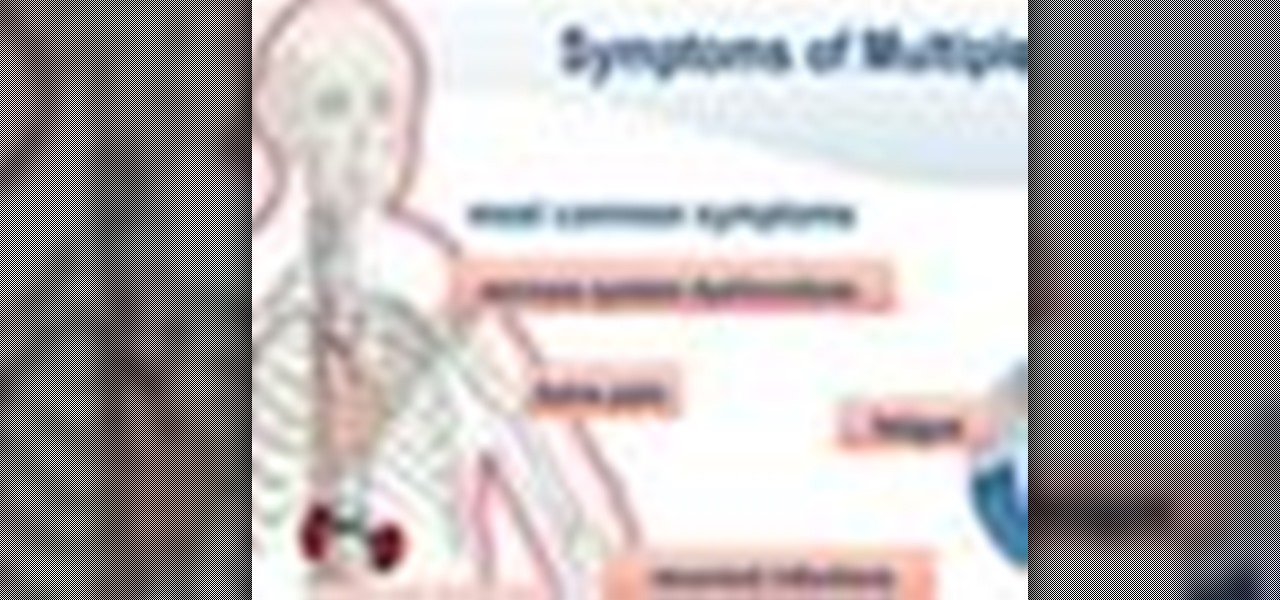
In order to treat and live with multiple Myeloma, you will need to first accept the diagnosis and what it means to your life. It is treatable, but it is not curable. They symptoms are: nervous system dysfunctions, fatigue, bone pain, recurrent infections, and kidney problems.

Self-storage may not be a new industry, but it is one that is rapidly reshaping its operations to suit a progressively more modernized customer base. In order to stay competitive with your self-storage facility, you'll need to keep an open mind, embrace current marketing trends, and most importantly, have a well-defined set of marketing goals. Your main focus should revolve around the following points:

Technology: The Less You Know the Better?

The HP Touchpad 64 GB is out in action with a robust processor and additional applications in the market. Using the best technology on earth, it is looking forward to give a tough fight to the Apple’s iPad 2. The 64 GB HP TouchPad sound more promising to its predecessors. The experts feel that the two device, HP TouchPad 64 and Apple’s iPad-2 is more or less the same. Let’s have a glance over the device by discussing the various features it encompasses.

Although there are many great camera apps with filters for the iPhone, Android users should not feel left out. Apps such as Vignette and Retro Camera offer an exciting array of filters to complement any photograph. I've tested out different filters from both apps, and uploaded the samples below.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.

Choose the Right Path Making a choice