A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.
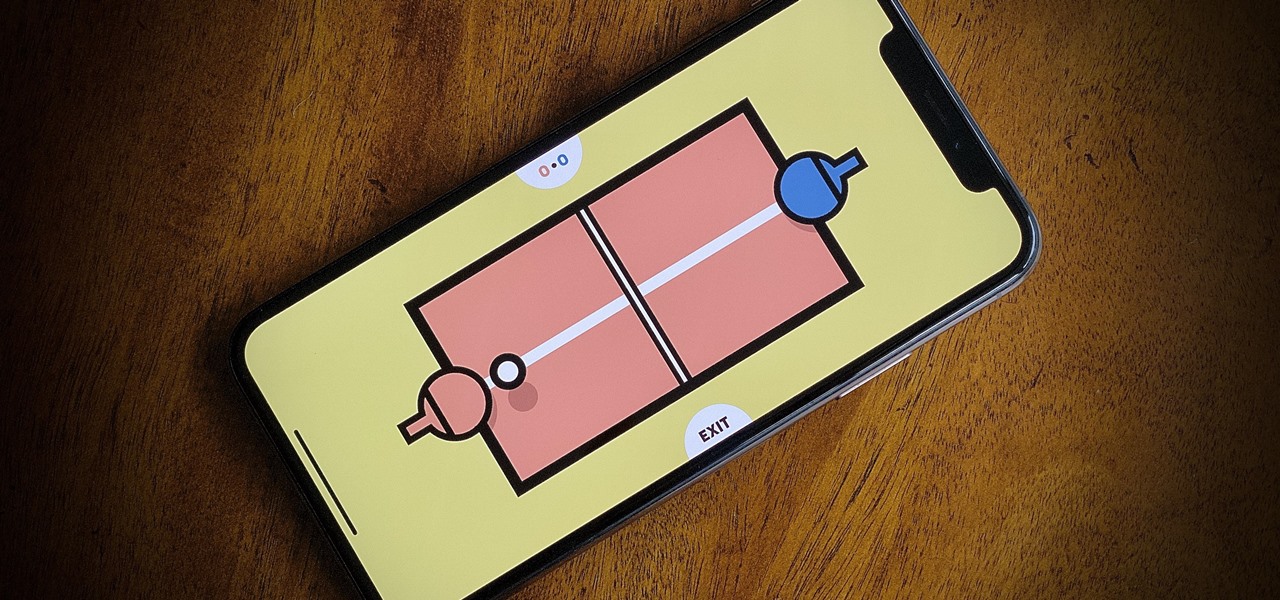
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.
Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.
When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy features you should know about, such as attendee attention tracking.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

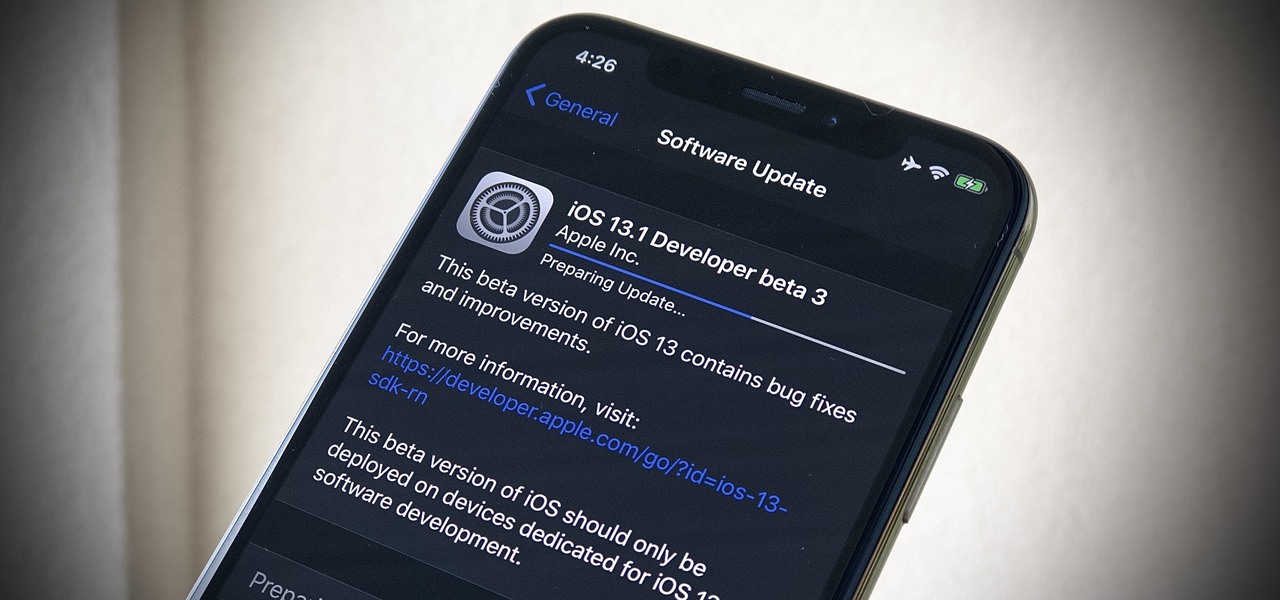
Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

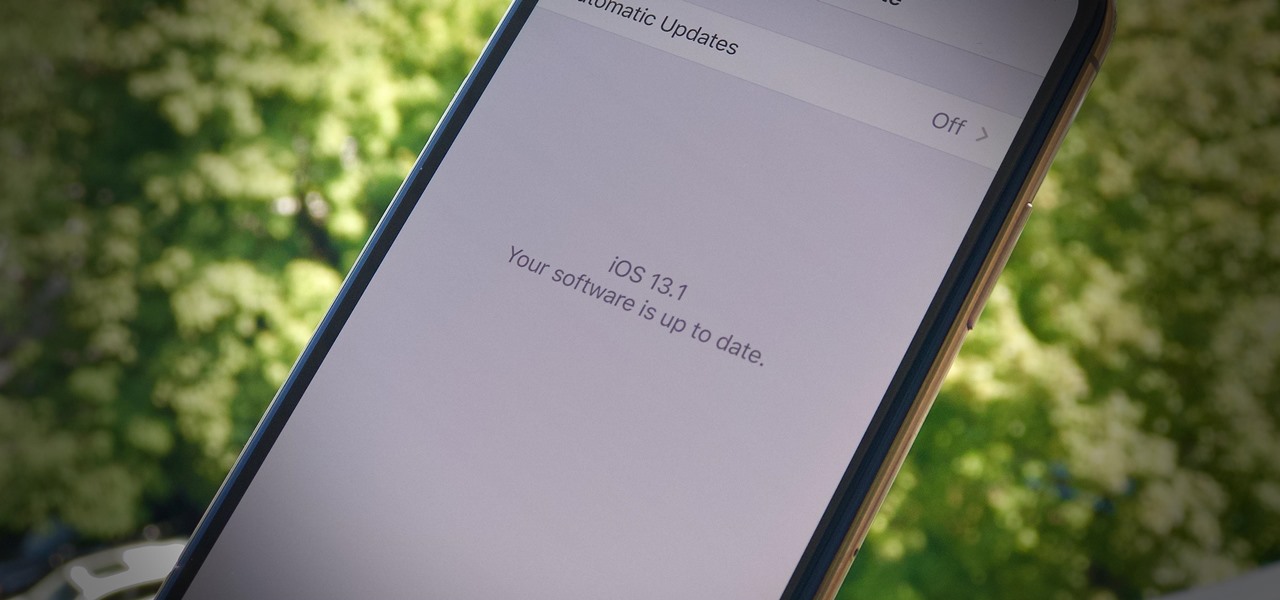
It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.

Apple's iOS 13 is nearly here. After four months of beta testing, the latest iPhone software update promises over 200 brand new features, like system-wide dark mode and an overhauled Reminders app. That said, it'll be shortlived, as Apple plans to release iOS 13.1 as a supplemental update just 11 days later. In fact, the company just seeded developers the fourth beta for iOS 13.1 today, Sept. 18.

Yesterday showed us our first look at the iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. But it wasn't all about hardware. Apple also released the iOS 13 Golden Master, making iOS 13.1 the main focus for us beta testers. Now, Apple just seeded the third public beta, following yesterday's release of 13.1 dev beta 3.

It's a big day for Apple. First, the company announced its new suite of phones: iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. Then, we get the iOS 13 Golden Master, the beta version of iOS 13 that will eventually release to the general public on Sept. 19. Now, it seems the company has dropped the third developer beta for iOS 13.1, set to release to all compatible iPhones on Sept. 30.

Apple has pulled quite the headscratcher in anticipation of its big iPhone unveiling next week. Its latest iPhone update, iOS 13.0, is just on the horizon, going through eight beta versions so far. And yet, before that software's official release, the company has started beta testing iOS 13.1, with no explanation why. And the second public beta for iOS 13.1 is now out, so let's see what's new.

When Apple takes the stage next week, we have no idea what version of iOS it will release. For months it seemed like a given that we would, of course, see iOS 13 seeded to our iPhones. Now, we aren't sure if Apple will tout iOS 13 or iOS 13.1, since the latter is now the focus of its beta testing. In fact, 13.1's second developer beta is now available to download and install.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

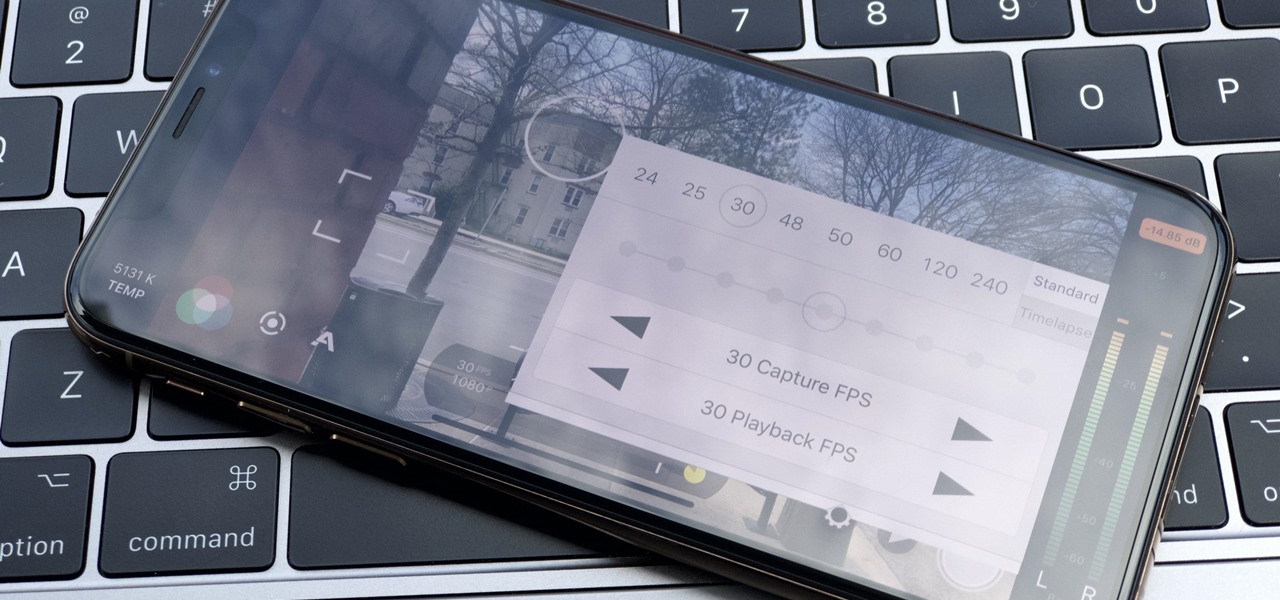
The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.