You're better than a can of Reddi-wip, which is why you should always make fresh whipped cream at home. It's extremely easy to make, won't have all those nasty preservatives, is thicker and creamier in consistency (like cream should be), and tastes much richer.

The VLC Player app for Android has a really nice feature that allows you to adjust brightness and volume by sliding your finger up or down on the left or right side of your screen, respectively. It helps keep you immersed in the video while you're in full screen mode, since you don't have to mess around with any popups or overlays to perform these basic functions.

Many recipes call for self-rising flour as a staple ingredient. Oftentimes, we find ourselves passing these recipes by because we don't have it on hand, or because we don't use it enough to actually want to buy it.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

While there are tools online that let you turn photos into interesting emoji art, and mobile apps that let you create emoji mosaics, none do it better than an iPhone app by second verse, which makes it a super easy, highly customizable process.

This year's Nexus devices are already two of the best bang-for-your-buck smartphones on the market, but with a new sale price from several retailers across the net, they might just be an unbeatable deal.

Google's YouTube Red is an awesome service, particularly in the United States where it comes bundled with a subscription to Google Play Music. You don't have to worry about ever seeing ads again on any videos, you can continue playback after you exit the YouTube app or even when you turn your screen off, you can download videos for offline playback, and you'll have access to YouTube Music.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually released quite a few awesome Android apps.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Sony's Xperia smartphones are some of the most beautiful Android devices out there—but unfortunately, they're rarely promoted in the U.S. and are seldom available through major carriers (aside from the new Xperia Z5 devices), so not many Americans are aware of how awesome these devices really are.

If you consider yourself a regular coffee, tea, or hot chocolate drinker, you probably have a kitchen cabinet full of stained mugs that refuse to scrub clean. Thankfully, there is a better solution that doesn't involve continuing to fight those stains with a sponge, bleach, and elbow grease. The answer to your coffee or tea stain problems is Cafiza: an awesome espresso machine cleaning product that is popular amongst professional baristas... but also doubles as an extremely effective ceramic ...

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

This tutorial will show you how to fold an Awesome F15 Paper plane. Please keep in mind that this model can not fly.

The 2015 LA Auto Show showcases the best of the auto industry—well, at least according to car companies. Increases in horsepower, better fuel economy, and most importantly—the latest tech—is all on display during the 10-day event in Southern California. Once of my first missions at the show was to figure out who is putting the most care and thought into in-cabin electronics, mainly the ones that guide us around and play our music, affectionately known as "infotainment."

When an album sells a million copies, it gets certified as platinum and cements itself as one of its generation's biggest hits. When an album sells 10 million copies, it reaches diamond status and transcends generational gaps. But when an album sells well over 40 million copies, there's only one thing you can call it—Michael Jackson's Thriller.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

The new iPhone 6S and 6S Plus models have a really cool feature called 3D Touch that lets you perform app-specific Quick Actions from the home screen for apps that support it. The only downside is that this awesome new feature is not available on older iOS devices.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Apple revealed the new iPhone 6S and 6S Plus at their September 9th event, and there are two particularly awesome features built in just for selfie photogs. The first is 3D Touch, which gives you a quick shortcut to taking selfies just by pressing the screen in a certain way. The second feature is a front-facing flash to help illuminate your face in dark lighting.

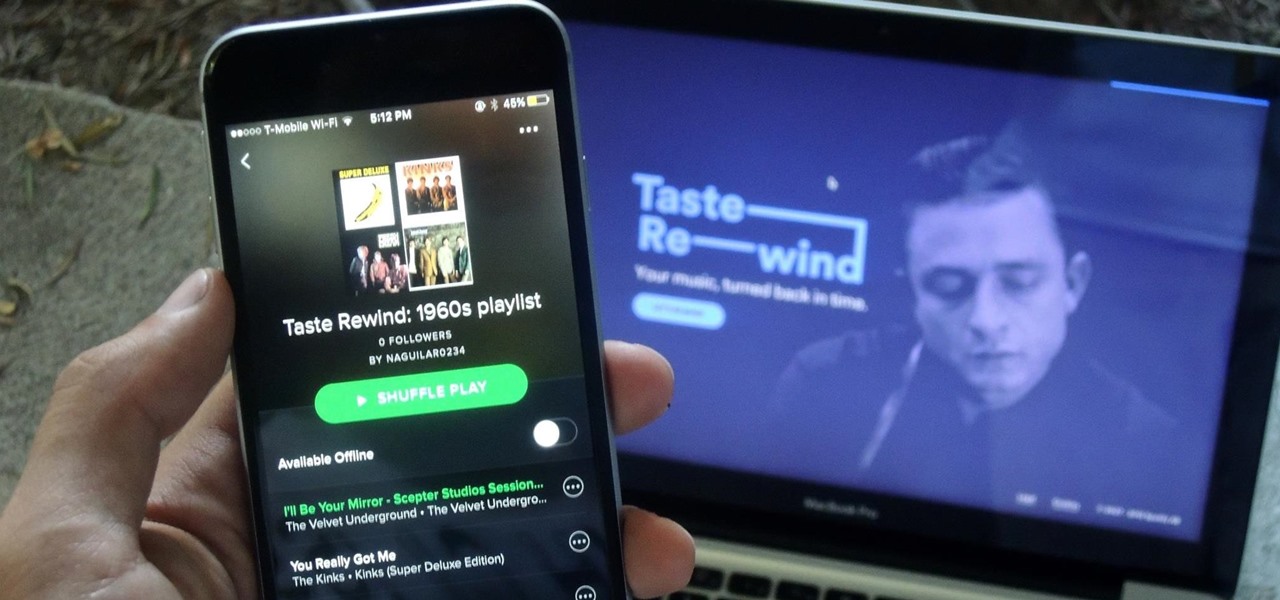
Spotify has a feature called Taste Rewind that claims to know what you would've listened to back in the '60s, '70s, '80s, '90s, and oughts ('00s), all based on your listening history and favorite artists. You can essentially time travel into the past and already have "favorites" songs to listen to! While I was skeptical at first, I tried the feature out for myself and was pleasantly surprised with the results. So if you want to create uniquely tailored playlists from the past five decades, st...

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

When I was a little kid, my parents often eschewed cakes for my birthday parties, and instead opted for ice cream sundaes and banana splits. It made perfect sense: ice cream is so easy, and you can get multiple flavors to ensure that everyone is happy.