To steal a quote from Mean Girls, Halloween is the one night when a girl can dress like a total slut and no one can say anything about it—but why do girls get to have all the fun?

Old people are usually perceived as wise and enduring, whereas an old smartphone, like my iPhone 4, becomes the butt of a joke every time I take it out of my pocket. I mean, come on, it's not like I'm still rocking one of these... And if I was, I guarantee you wouldn't beat my score on Snake.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

I've been playing around with iOS 7 for a while now, and for the most part, I dig it. It's a nice update for a stale OS, and there are a lot of great new features. But like any good piece of tech, there are a few things to be disliked. Some of these are big issues, and some could be considered nitpicking, but given that I'm fairly used to the older iOS 6 version, they feel big to me. Paper cuts always hurt worse than gashes.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.
The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

I've never had a black eye, but I was in a car accident that turned my entire ear dark purple a few years ago. Believe me; it was enough to get more than a few funny looks.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

The airline is not your friend. It will do anything it can to gouge your dignity, time, and most of all, money. One of the biggest scams to get a few extra bucks out of you are those dreaded baggage fees. If the lines, security, "random" screenings, and unwanted fondling aren't bad enough, you have to pay them to check your bags (which, most of the time, is done poorly). Flying truly is the most inconvenient way to travel.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Video: . Optimize your Marketing with a Mobile Website

If you're a Steampunk (or costumer of any variety) and you don't know what Rub 'n Buff is, this tutorial will make your life so much easier. You have no idea.

Steampunking Nerf guns by painting them is a pretty common practice among Steampunks, but unfortunately, the really amazing-looking ones involve literally taking the gun apart, painting it, and then screwing it all back together.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go anywhere you want. But like most tablets, the Surface comes with a rather limited amount of storage space. The tablet comes in either 32 GB or 64 GB, but we all know that's not the actual amount of storage space you can...

In the first part of this two-part guide, I covered cutting, grooving, beveling, making holes, and stamping/tooling. I hope you enjoyed that part, because we're pushing the accelerator to the floor and moving ahead at full speed!

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

If you've run out of time for all of our more time-consuming Halloween costume ideas, here are some places on the web for free, downloadable paper masks. There must be at least 100 options among these links to satisfy your last-minute costume needs! Just download, print, and cut 'em out to the appropriate size, then either glue a stick/handle on or tie some elastic string on.

Watch the full gameplay for Castlevania: Lords of Shadow on the Xbox 360. Lords of Shadows is yet another video game in the popular Castlevania franchise, which has been around since the days of the NES. In this lengthy walkthrough, you'll see all the vampire killing action, set in the Middle Ages, with protagonist Gabriel Belmont. This is a handy video guide if you ever get stumped on a level.

This walkthrough will help your through the entire gameplay of Lost Planet 2 for the Xbox 360. Lost Planet 2 is the sequel to the third-person shooter Lost Planet: Extreme Conditions, and besides the Xbox 360, is also available for the PlayStation 3 and Windows. It takes place 10 years later, back on the planet E.D.N. III, which has more foliage compared to its previous white, frozen entity. To see how to defeat the game, watch this walkthrough, which provides you with all of the knowledge to...

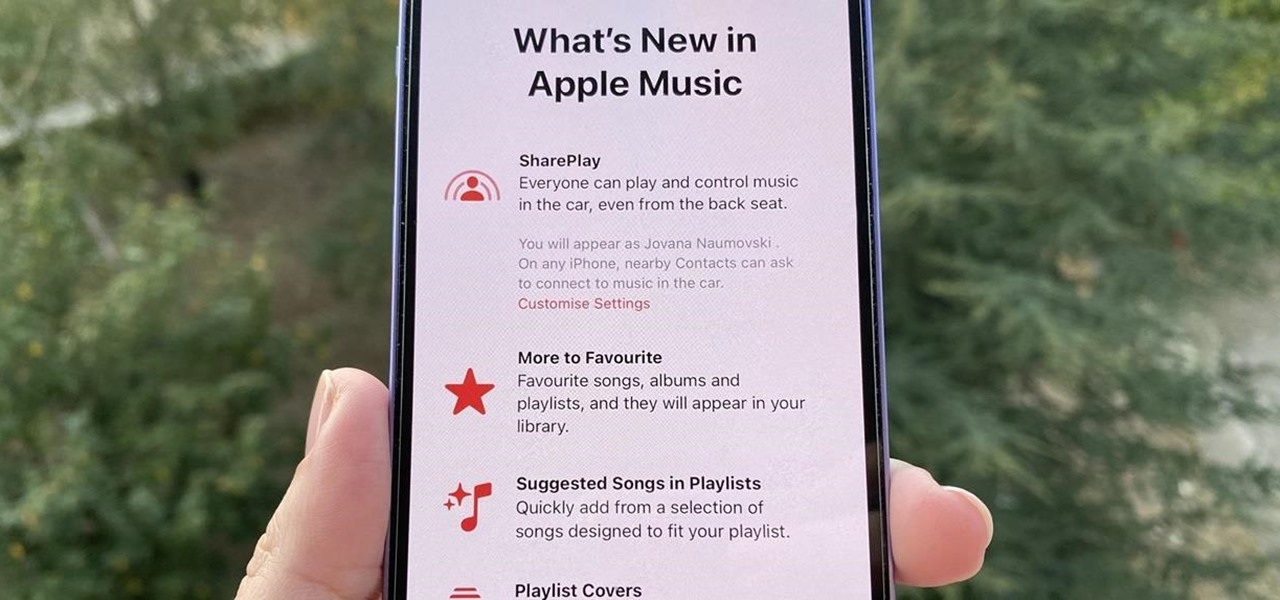
In case you missed it, Apple has added a lot of new features and enhancements to the Music app on your iPhone, changes that benefit both Apple Music subscribers and non-subscribers. Chances are, you haven't seen all the changes yet, especially since many of them weren't released when iOS 17 first came out, but we'll go over them all with you.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

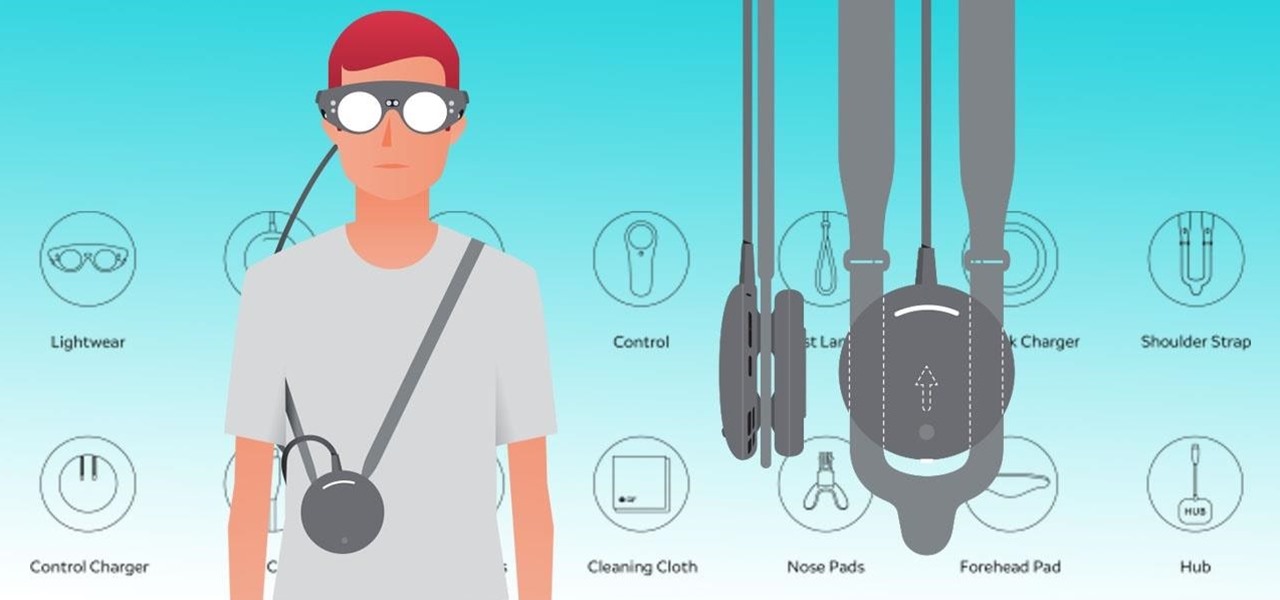
The long wait is over — the best augmented reality device on the planet is finally available.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.