
News: Review - The Other Guys (2010)
Describe this movie in one word? Hilarious! Could you watch this movie again? Without a doubt!


Describe this movie in one word? Hilarious! Could you watch this movie again? Without a doubt!

Tawkon has developed an app for the iPhone, Android, and Blackberry that measures the radiation levels at any given time. The demonstration below shows how the radiation levels go up for each phone when a "death grip" is applied. What's a death grip, you may ask? A death grip is a simple term used to denote a hand that has recently killed. What a troublesome thing to have.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

I took a class in the fall entitled Writing for Television at Bentley University in Boston. Much of what I learned has helped me through my first year of creative writing. One of the keys to writing television that we learned in the class was that a television show follows the traditional three act structure that any story follows, except for the fact that in a television episode, many questions are allowed to go unanswered.

If you look up the word SAWBUCK in the SCRABBLE Dictionary, you'd see that it was a sawhorse, but there's another definition that we're all probably more familiar with:

A microchip is a tiny computer chip which has an identification number programmed into it. The chip is the size of a grain of rice, and it is easily and safely implanted into the skin of an animal with a hypodermic needle. Once the animal is "chipped" he can be identified throughout his life by this unique number. Microchips are read by a scanning device which recognizes a unique identification number. Through registration of the animal with a national database, the owner can be contacted and...

Tired of seeing all of those ads in your browser? The flashing ones make for a terrible browsing experience, and those rollover ones are just downright annoying. If you don't want to be bothered by them again, you've got a few choices, depending on what web browser you're using.

Screw the airplane man. Ticket prices are too high. Competitive consumer choices are pretty much nonexistent. And need I go into the pain of being crammed into those tiny seats, elbow-to-elbow, thigh-to-thigh with a perfect stranger? Even your average Richie Rich winces at the astronomically high prices for a First Class seat.

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.

Shiny hair is good, shiny skin is bad. Keep your skin oil and shine free by following these four easy steps. Wash skin

Your victim has to be asleep. Place tacks upside down around the bed. Put super glue in the person’s shoes or slippers. Then set the clock 10mins before the alarm goes off. Carefully staple or glue the victim to the bed. Then be waiting outside the door with buckets of gross stuff. Then when the alarm goes off watch him/her go crazy. And when they come out toss the bucket of gross stuff on them.
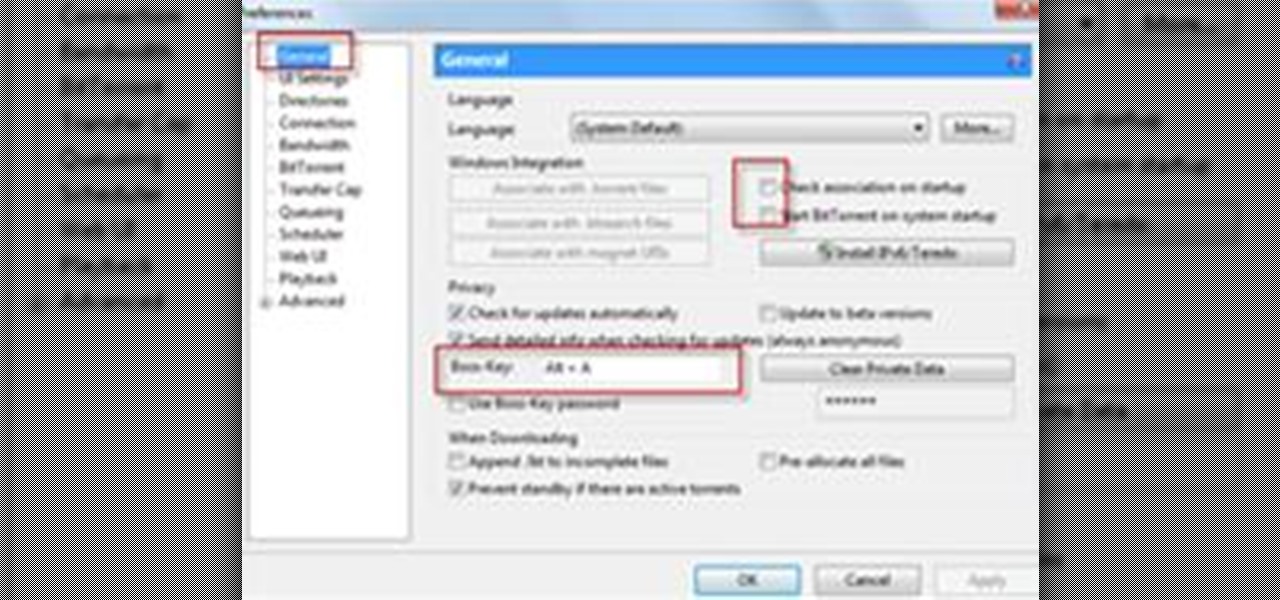
Completely Hide UTorrent and Bittorrent Software in Your PC While It Is Still Running!.

Especially today, with the internet making information so readily available, people of all ages, all around the world, are trying to learn magic tricks. Unfortunately, going about this the wrong way won't make you into a magician at all, but will instead make you into someone who simply knows how a few tricks work.

In each day of our life, we see inflammation. We see it during sore throats and abscess formations in our bodies, and even slight tooth pain is a form of inflammation. Sometimes it's good when it fights to protect us from invading organisms, but sometimes it becomes bad when it occurs in inappropriate ways, like acne.

We've all been there before: We're in a hurry to get somewhere (often in bad weather), so we get in the car, turn the key in the ignition and.....WHUH! WHUH! WHUH! The darned battery is dead! After a stream of choice expletives (that is, if you're anything like me....;o)), we open the trunk and take out the jumper cables - but what if we don't know how to use them? Even if we do, we can often forget such things in crisis situations when we're pressed for time.

So You're New to Counter Strike Source? So you're new to Counter Strike Source and you want to improve your gameplay? Great. You've come to the right place.

One retard, (preferably Steve-o) should glue his ass shut thinking he is doing a different prank, but its actually a prank inside a prank, he will be secretly fed laxative and chili. And he might even have to crap so bad he will rip his ass open?

Hey!!!! This should include all the Jackass cast : Johnny Knoxville, Steve-O, Bam Margera, Wee-Man, Chris Pontius, Preston Lacy, Dave England, Ehren McGhehey and Ryan Dunn

ok so my idea is you guys dress up like cowboys and indins and spreed out threw an arena during a wwe event and have pepperball guns and just start shooting eatchother but you dont do taht untell i blow th wisel and then thats when you start Warnings

Any talk about privacy is a complicated (usually) and touchy subject. In today's world, privacy is an ever eroding pleasure to be had. Numerous cases, like the monumental Kat'z vs United States, have been fought to hold on to this right.
The Power of One is one of those books that I really should have read years ago. I’ve certainly meant to read it for a long time so this was a satisfying title to cross off my list. It’s stunning that this was Bryce Courtenay’s first novel. I look forward to reading his others because if this is where he started, he’s a talented writer.

Today's fancy cars come with all sorts of options, from power mirrors to working seat belts. Some of us condemned to live in the reality of capitalist recession have no car, or perhaps a very modest one. But your modest car can still have some cutting edge technology wedged into the trunk and dashboard if you know what you want and where to look for parts. Today, we make a parking sensor using a sonic range finder, just like in the vehicles our owners drive!

No one likes it when random people wander into your home and mess things up, which is why it behooves you to hide your things from even the most prying eyes with builds like this totally invisible, 2x2, piston-operated door with no visible redstone either inside or outside. The story of Goldilocks and the Three Bears may have gone differently if they would have had one of these babies installed in their home: I did a tutorial for a piston-powered trapdoor and many people wanted to know how to...

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

If you know anything about search engine optimization and online marketing then you know that having as many links going into your site from good sources is very important. And if you’re not really experienced at building links or SEO in general then you might not know the best way to get good links for your site. So please read on and I’ll present to you what I feel is the best way to get good quality links for your site.
Here is my investigation on Teen Stress Base on FTA. QR/ER on Stress

In each day of our life, we see inflammation. We see it during sore throats and abscess formations in our bodies, and even slight tooth pain is a form of inflammation. Sometimes it's good when it fights to protect us from invading organisms, but sometimes it becomes bad when it occurs in inappropriate ways, like acne.

Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. Most locks are based on fairly similar concepts, so sharing methods across locks is possible.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

I'm pretty sure that it's a universal dream for everyone in the world to retire early. Who wants to to be stuck with the rest of the country and retire when you're almost 70 years old? You heard me right, 70! Most people can't go out and do the things they love to do by the time they're 70, unless they've been practicing good health and exercise their entire life.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Windows 8 Beta (Developer Preview) It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.

When you buy computer parts, it can be a tough decision where you want to put all of your hard earned dollars into. Not only that, but when you buy a top of the line component, 3 months later (at most), your hardware will likely be outdated. This puts consumers like us in a bit of a pickle when it comes to purchasing, especially on a tight budget.

When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. It's taking nothing and turning it into something. It's taking the bad and making it good. Above everything else, it's the art of manipulating the world and people around you—coercing that salesman into giving you a low...

Halloween is just a few days away, and since I've been churning out the creepy Bingo of the Days for everyone the past few weeks, it seems fitting to do a puzzle based on them.

The Netherlands are a hotbed of indie game development, which seems appropriate for such a brilliant and eccentric little nation. Two man Dutch indie developer Vlambeer have found themselves in the news more often than most companies of their size, thanks to two great games and a third on the way.

Apple's "Let's talk iPhone" event has just ended, and the information isn't anything that wasn't already anticipated. Much to everyone's hopes, the iPhone 5 was not the headliner of the event. Instead, Apple's new CEO Tim Cook unveiled the iPhone 4S to the 250-seat audience, a speedier version of the iPhone 4. Here's the details.