Getting two sticky-pistons to pull eachother, a piston-train, isn't anything new but the pistons and their timing in 1.3 are and there has been alot of QQ-ing on the Minecraft-forums about how bad they are and that Jeb should bring back the old pistons we all know. I, for one, not only welcome out new 1.3-pistons but have also made a small mini-game out of them. A two-player tug-o-war. The players stand on the diamond or emerald area and press a button to make the piston-train take one step t...

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway
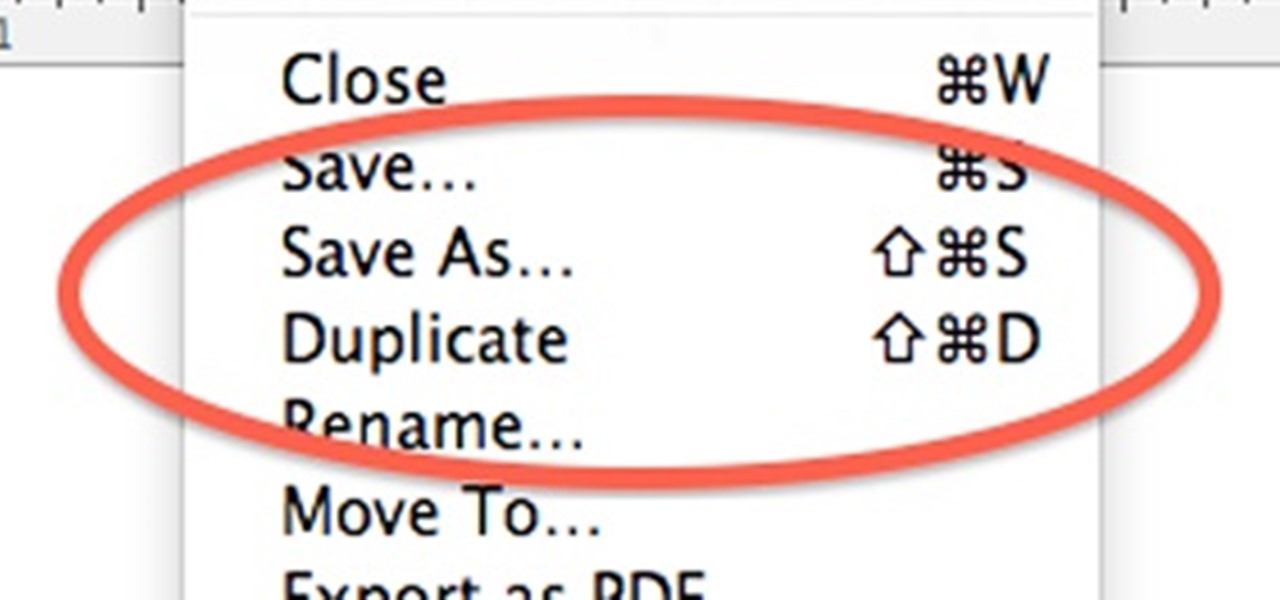
When OS X Lion (10.7) debuted last year, a lot of Apple users were dismayed that the "Save As" option had disappeared, replaced by the "Duplicate" function. Most felt that it just wasn't the same, so when Mountain Lion was released, the "Save As" option was brought back… sort of.

So, this idea was born from a necessity to save. My household uses tissues a lot. I have two small kids, so they are extremely useful. The problem with tissues is that they seem to disappear in no time. So, whenever we ran out in-between shopping visits, my family would just use toilet paper.

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

Magnetic knife strips are really handy. They allow for the removal of that huge knife block on your countertop, freeing up valuable counter space. They allow for easy access to your knives as you can mount them pretty much wherever you want. Plus, they look really cool, too!

In this handbag fashion video series, learn how to choose the best handbag from fashion expert and handbag designer Lindsay Colbus. Lindsay will teach you how to choose the best handbag for you and will give you examples of good and bad handbags. She will teach you how to match a handbag to your outfits, how to choose an evening handbag, how to choose a day handbag, how to choose a trendy handbag, how to choose a casual chic handbag, how to choose a clutch handbag, and how to choose a handbag...

This video shows you how to get all sorts of flash games and cartoons into your Sony PSP. The video quality is pretty bad, but if you listen you can figure it out.

Learn some tips on good piano playing vs. bad piano playing.

Most of us aren’t lucky enough to get clothes tailored for our bodies so to get your skirts just the right length you may need to change the hemline yourself. In one evening you can change a mediocre skirt into your favorite piece of clothing.

If you work with a computer, at some point in time your computer is going to freeze. Hopefully, you've been saving any important data or writing you've been doing because there are a few easy steps to take to get that computer running smoothly.

In these piano care videos, learn how to do some minor tuning on your own. Our expert will walk you through how to use some basic equipment to adjust the strings for any given key to bring it back in tune, including techniques for isolating bad notes, and how to properly use a tuning hammer. Enjoy!

A bad phonograph cartridge can damage your records. Learn how to change a DJ phono cartridge in this free record player maintenance lesson from an experienced disc jockey.

In this video series you'll learn basic brake fluid maintenance and how to change the brake fluid on your vehicle. Expert mechanic Jon Olson walks you through the process step-by-step, explaining how your braking system functions, how to fix a simple leak in your brake line and how to check your brake fluid and tell when it has gone bad. He also explains how to bleed your brakes in easy-to-follow steps, including using a bleeder wrench to loosen and tighten the bleed.

In this how-to video clip series on how to maintain healthy teeth and gums, learn how to practice good dental hygiene, including how to prevent gingivitis, plaque buildup and cavities, how to brush your teeth properly, whether to use an electric toothbrush, how to clean your tongue, how to prevent bad breath, how to floss correctly, and other tips and techniques for a healthy mouth.

In this video series, watch as expert kayaker James Sullivan teaches beginning kayaking tricks while playing in holes and waves. Learn how to find a good hole and identify a bad one, how to enter a hole from above and the side, how to move forward and backwards in a hole, how to get on a foam pile, how to find sweet spots, how to edge control in holes, how to enter a wave from above, how to avoid pearling, how to carve an edge, how to use the power stroke, and how to use forward and reverse r...

This video series will teach you how to train your cat, emphasizing positive reinforcement obedience techniques. Utilize clickers, water and meaningful alternatives to bad behavior to help your feline friend be a happy and non-destructive member of the family.

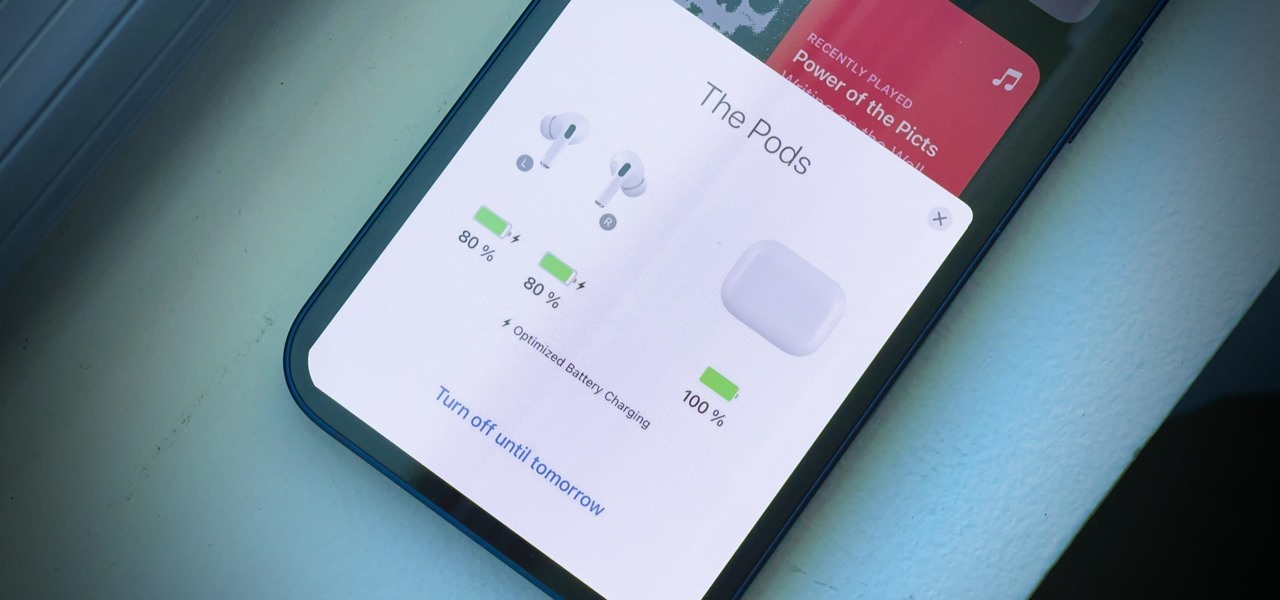
Your AirPods Pro can run up to 4.5 hours when 100% charged up. However, they're programmed to stop charging at 80%, and it won't kick back in until they think you'll need that extra 20%. That means they won't last as long in your ears before needing put back in the case. And you could end up with dead AirPods Pro if you're out, can't hit up a charger, and your case is out of juice.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

This week's Apple earnings offered a report of solid performance and guarded optimism about future iPhone sales, which may be impacted later this year by issues around the current coronavirus epidemic in China.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

While the long-awaited HoloLens 2 officially arrived this week, details leaked about another, arguably longer-awaited AR headset, the fabled wearable from Apple, and a previously undisclosed partner assisting the Cupertino-based company with the hardware.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

The streaming content vision from Magic Leap recently underwent a quiet but major update, courtesy of AT&T.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

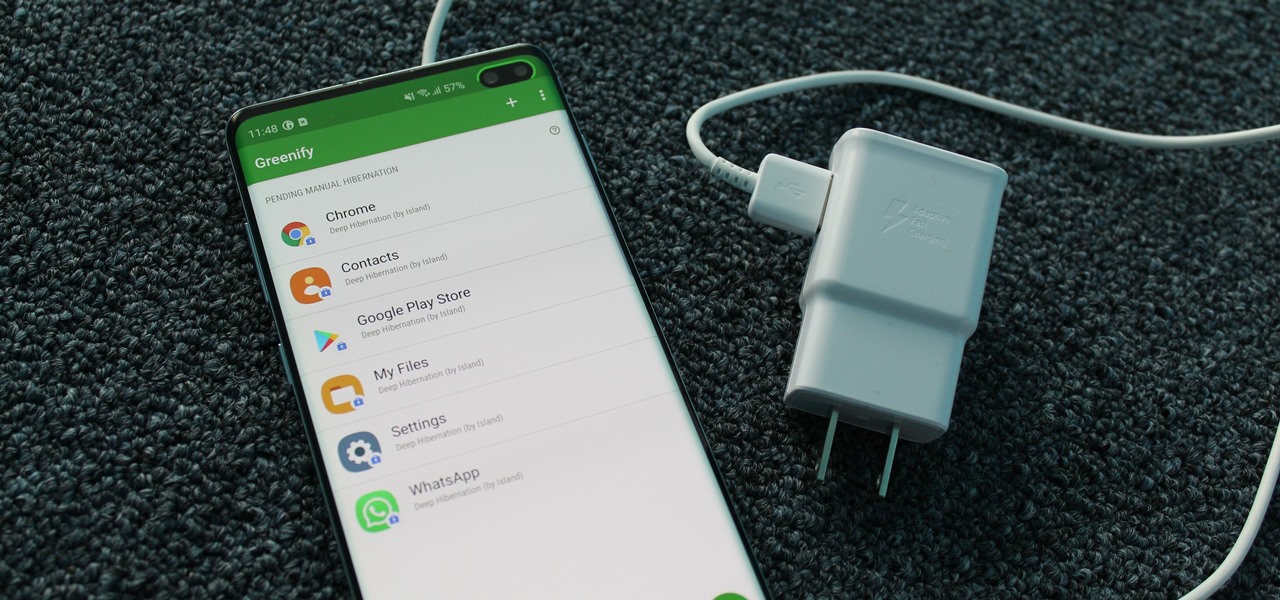
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need root to use it.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

New updates are always exciting, even more so when Google's behind the wheel. Yes, Android 10 "Q" is here, at least in beta form, ready for software testers to dive in and explore all the new changes. Among those changes, however, lie some issues. We won't sugarcoat it — there are some annoying things baked into Android 10.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.