Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

This is why you're fat. Coincidentally, this is also why you're happy when you nom on artery clogging junk fare. We don't recommend you whip up this recipe on a regular basis unless you're hopin' and wishin' for a heart attack this Christmas, but this would make a sweet treat every once in a while.

Of course, in a Star Wars story, one cannot hope to board a major ship and take it any major distance without being attacked by Rebel or Imperial forces, depending on your side. Star Wars: The Force Unleashed 2 is no exception, and in this video you'll learn how to deal by beating level 7: The Battle for the Salvation.

In this video, we learn how to install brakes, shifters, and grips. You will need: Allen keys, grease, a knife, and a grip to do this. First, attack the brakes onto the handles, then the shifter and the bolts. Make sure to grease the bolts before you place them onto the handles. Do this on both sides of the bike. Make sure you have everything on the correct sides, then slide the grip in. Customize the grip so it's the right length and cut it with the knife to do this. Once finished, connect a...

In Minecraft, the key to survival is building proper shelter for yourself to survive the nightly attacks by the creatures that roam the land. But whose to say that you can't spruce the place up a little bit? Notch has included a feature in the game that allows you create paintings using a few sticks and a piece of wool. In this video you will learn how to craft the paintings and also how to put them up and some of the random paintings that you can get.

During Halloween, party planning can get really hectic. Between baking and cooking party food to picking up plates and utensils at the store to putting up black and orange streamers, there's more than enough stuff to do to give you a panic attack.

We once read a Twitter profile that said, "Love food. Hate exercise. Will die of heart attack." While that's funny and all, we doubt any of you guys and gals would want to drop dead on your 40th birthday. While we're totally for the occasional splurge, it's definitely a good idea to begin eating healthy now.

A big part of pizza's allure is its perfectly crispy crust and oodles of heart attack-inducing oil sitting on the cheese. Personally, we can't even consume a pizza we get from Pizza Hut or Domino's without taking a napkin and blotting off the oil.

Bed bug management requires many levels of attack. Prevention is very important. You should never pick up discarded items on the street. Don't buy used or refurbished mattresses or furniture. Toss out vacuum bags.

Kameron Kay teaches us how to make a floating flower crystal toe ring in this tutorial. You will need: stretch cord, large crimp bead, flat nosed pliers, flat backed crystal flower, glue, and small scissors to make this. First, cut out your chord to the exact size that you need. After this, use glue to attack the ring into the middle of the string. Place a crimp bead on the bottom to help the bead stay in place, then glue these together as well. Next, tie this together and attach an end to th...

In this tutorial, we learn how to work a spinner bait. This has a head as the weight, then the hook underneath the head and skirt. On the other side of the safety pin, there is who flat blades for murky waters. These help with sun reflection. This is a very versatile type of bait that helps you fish in murky waters. Bass will attack it as soon as they see it, helping you catch more fish. There is a lot of equipment on this, so it takes the bass a little while to get a hold of it. To ensure yo...

Are you having a hard time defeating the character Tiamat? Well, this tutorial is just what you need! In this video, you'll find out how to defeat this ugly, Predator looking beast.

if you're looking for a little bit more of a challenge in the game Darksiders, then check out this tutorial. In the video, you'll be finding out how to find all ten pieces to the Abyssal Armor. This armor is much different than War's original armor and is much stronger and gives life on all attacks. It doesn't need to be collected to win the game, but it helps make your character stronger.

Achievement hunters, listen up! It's time to head into the Transformers' world with Transformers: War for Cybertron. This game takes place on the planet to both the Autobots and Decepticons and it gives you a first hand experience of what happened on that planet.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

This achievement is sure to make you "fly like an eagle." In the game Assassin's Creed II, you're introduced to a bunch of new weapons and skills that you can use to take down your victims. One of the coolest new additions is that of a flying machine or glider. This can be used to travel from once place to another and can even be used to attack nearby archers. Doing that can actually result in the achievement, Fly Swatter. So check out this tutorial on how they did it and how you can do it. E...

In this brief video tutorial, the host 'Uncle Todd' demonstrates how to 'attack a beat'. This video is intended for beginners. Watch as he shows you how to keep your tempo up as you time your drum strokes in a beat. You should practice my trying just your right foot and your right hand, and then alternating to to your left foot and your left hand. The host in this video uses an electric metronome to keep his tempo steady and accurate, something that he recommends you try at home. Don't forget...

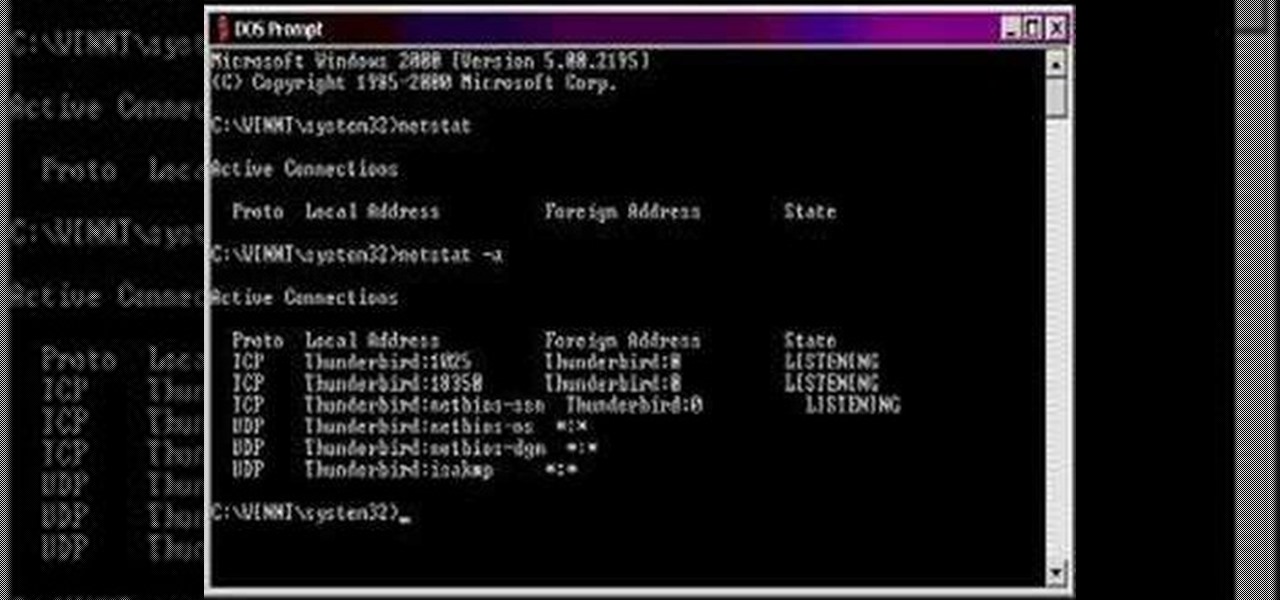
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

Rick Steinau with Ask the Exterminator demonstrates how to prevent yellow jackets from nesting in your home's walls. In mid to late summer yellow jacket populations increase. Yellow jackets can find spaces in the veneer or in cracks in bricks or siding. You can hear scratching noises in your walls as the wasps move. Observe wasp activity late in the day when they return to their nest for the night. Treat reachable holes with pesticide dust and a bellows. Leave the hole open to let the wasps f...

The moonwalk has been written in history and will go down as one of the most well-known dance crazes next to the Macarena and the jitterbug. In order to moonwalk like Michael Jackson, it's important to focus on the pivot and push of the feet and legs while sliding. Make your moonwalk smooth with the tips and tricks given in this free dance lesson.

This video shows tips on how to use insects to benefit your garden. This will teach you ways to reduce the insect load in gardens without the use of chemicals. Rose aphids can be controlled with lady beetles, for example. Although these techniques have been used for agricultural use, they will work in your home garden. Asian Lady Beetle, tend to stay put. They won’t migrate. They will attack Pecan Aphids. Trichograma, a wasp that is effective against larvae and eggs.

This video demonstrates the cross court backhand shot in a Racquetball match. It demonstrates the proper form and timing in an actual racquetball match. It provides helpful tips: for example, the cross court backhand shot should be employed strategically. The best time to consider using the cross court backhand shot is when you see your opponent leaning on the down line: i.e. use the cross court backhand, if it appears that your opponent has already committed to a line of attack. If it appear...

The Dahlia Guy is going to show you step by step how to plant dahlias. First, you want to bury your tubers at 2-4inches of depth and place a stick right next to the eye so you know exactly where the dahlia will be. Also, you want to place a timed release fertilizer in the hole and then cover it up with the dirt. Now, take a 16inch long stick and use that to space out the dahlias in your garden. Some tips to use are use name tags at the beginning of the of the planting and at the end of the di...

How To Set Intonation on a "Gibson Style" Fixed Bridge. A step by step video tutorial that will teach you how to change the strings on a fixed bridge guitar and also set the intonation. Andrew Wasson walks you through a series of instructions that include cutting the strings off your guitar, tightening the bolts on your tuners, polishing frets and fret board and more. He then goes on to show you how to put strings on your guitar, tune the guitar with a tuner, set the bridge saddle, and settin...

Let’s try to thread the needle, as in give a choke hole. First get your opponent down on the mat facing upwards and sit in the mountain position. Hold your opponent's left hand with yours around his head to block him/her. Get your right hand through your opponent's left hand (needle in the hole) and push your chest towards the ground. This will put pressure on your opponent. It will help in your attack as well as defense techniques.

In this tutorial, viewers will learn how to use the synthesizer functions of the Yamaha PSS-780 keyboard. Starting with the basic piano voice, the presenter shows how this can be modified to create a new sound. He shows how the attack rate of the sound can be modified with one setting, how the modulation button affects the tones of the sound, and how sounds can be further modified with the frequency control. The presenter concludes by noting that with practice the user will learn to create ot...

Want tour-like spin on your swing? There are several keys to imparting tour-like spin on your wedge shots, including proper set up, a correct angle of attack, and quality contact. Tim Mahoney, Director of Education for Troon Golf, explains these keys and how you can make them part of your game.

It's time to smash that iPhone, but wait… you don't really want to break your iPhone, do you? That's were a fake iPhone prop comes in, perfect for any homemade movie. Just make this, and switch it out with the real one during the anger attack. Watch this video tutorial to learn how to build a breakable iPhone movie prop. Also works with a fake smashable iPod.

This is a Cheat Engine guide on how to hack this flash game - P.O.D. Kongregate Acheatment shows you how to hack P.O.D. with Cheat Engine (09/23/09). This P.O.D. cheat will give you a level hack.

Cary Kolat demonstrates wrestling technique for collegiate defense. This covers defending single leg attack on the mat. Coach Kolat shows you how to practice funk roll same side as single leg move

Learn how to deal with a black bear or grizzly encounter with Shannon Davis and Ted the Bear. Black bears are distinguished from brown bears by lack of a prominent shoulder hump; a Roman profile or sloping nose and forehead instead of a dished forehead; and shorter, thicker claws for climbing versus longer, more slender claws for digging. Although brown bears are generally bigger, size is not a dependable indicator. Also, fetal position is often recommended as opposed to lying prone as shown.

You never know when you'll have to defend yourself against one of these bloodsuckers, so be prepared to bring a vampire to his knees. While you may not believe in vampires, there are those that do. In any case, prepare now for a hypothetical attack from the un-dead and you won't have to kick yourself later. You will need garlic, a cross, rice, grain, or seeds, holy water, a wooden stake, an axe, matches, and some water. Watch this video survival training tutorial and learn how to fight off a ...

Grandmaster Alexandra Kosteniuk teaches you how to... you guessed it, play a game of chess. This chess video tutorial will show you how to take the initiative in a chess game to win.

Trying to eat healthy and lose weight when you're a foodie is hard. Because when it comes down to it, most good food (we're thinking sweet, salty, fried, and crispy) is essentially a heart attack in a box. But every now and then you find a recipe that's both delicious and relatively healthy.

Balisong knives, or butterfly knives, are folding pocket knifes with two handles that can counter rotate. People love performing tricks with them because of the balisong butterfly knife's flipping ability. Since knives aren't toys, make your balisong butterfly knife out of Legos. You still might hurt yourself, but not as badly as with the real thing. Learn how to build a Lego balisong butterfly knife by watching this video tutorial.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.