Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

'Loose Change' is cool secondary quest in Dragon Age 2 that varies depending on whether you chose to be a smuggler or a mercenary when you enter Kirkwall. This video will walk you thorough the mercenary version of the quest, allowing you to, in fact, tie up your loose ends.

If you're a God of Mount Olympis, you may want to leave town, because Kratos is still angry in God of War 3 for the PS3. Killing Gods and defiling women are just a couple of his his hobbies. The other is treasure hunting. And in this IGN Strategize video, you'll find the locations of all ten Godly Possessions in God of War III. The Godly Possessions are more than just conversation pieces. Each has a special power you'll be able to use after beating the game once. You'll also get a gold trophy...

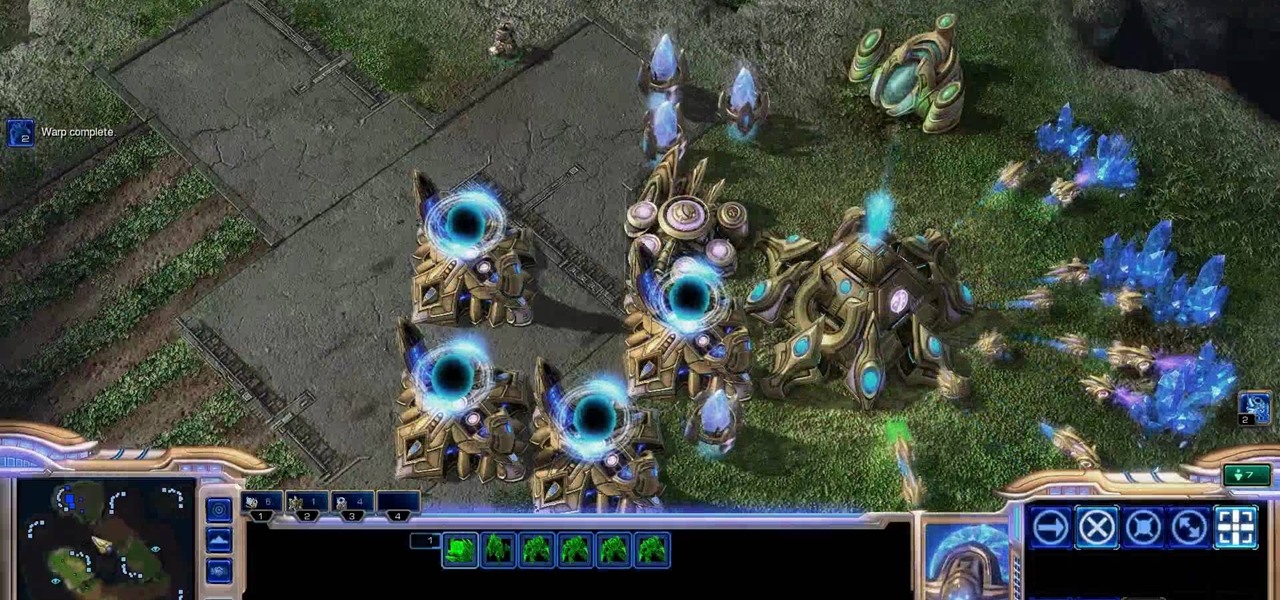
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to use the 4 Gate Protoss build, which is one of the best and most b...

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create a WoW-like camera and control scheme in the SC2 editor, allowing for WASD control of your uni...

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

The volleyball attack can excite the crowd and devastate the opposing team. The approach, jump and landing are the basic aspects of a successful volleyball attack. Learn how to attack in this volleyball video tutorial.

For a field hockey offense to score, their attacking must be better than the defense's tackling. Speed and accuracy are essential for an effective field hockey attack. Learn how to attack in field hockey in this video tutorial.

Watch this trainer wrestle with two full grown tigers, while showing tips and tricks to survive a real tiger attack in the wild. It's amazing how tame these obviously domestic tigers are, even when full-grown!

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

This debriefed game uses a queen/bishop castle attack. See hot to do it, or not do it. Just watch if you're a beginner, because who better to learn from than a beginner.

California is struck by earthquakes everyday, but the biggest ones, on average, appear every 150 years, just south of the San Gabriel Mountains. The last super-destructive earthquake in California was over 300 years ago, which could mean a long overdue Californian earthquake is on the horizon.

Kipkay is at it again with his pranks. In this video, he shares four fun and easy pranks that anyone can do to drive their friends (or victims) crazy! Their all very simple. They include a cell phone prank, a floss prank, and more!

Dispatch your enemies with a single sword strike. This cheater's guide will show you how to smite even the toughest of opponents with a single hit (and a few keystrokes in Cheat Engine 5.5).

In this how-to video, you will learn how to win at Chess in two moves. First, you will need a chessboard. Pawns go up twice at the start or once. They attack diagonally. Otherwise they just go up once. The castle, or rook, go up and down or side to side. The bishop goes diagonally in both directions. The knight moves in an L shape in any direction. The queen can go sideways, diagonally, forward, and backward. The king can move only once space at a time. Once the board is set up, you are ready...

The video explains how to hack the game Agony: The portal. First he clicked the start game and created new character by entering the name as test dummy and set the difficulty level as normal. The he clicked the start campaign. While entering the game he skipped the tutorial and directly he went into the game.

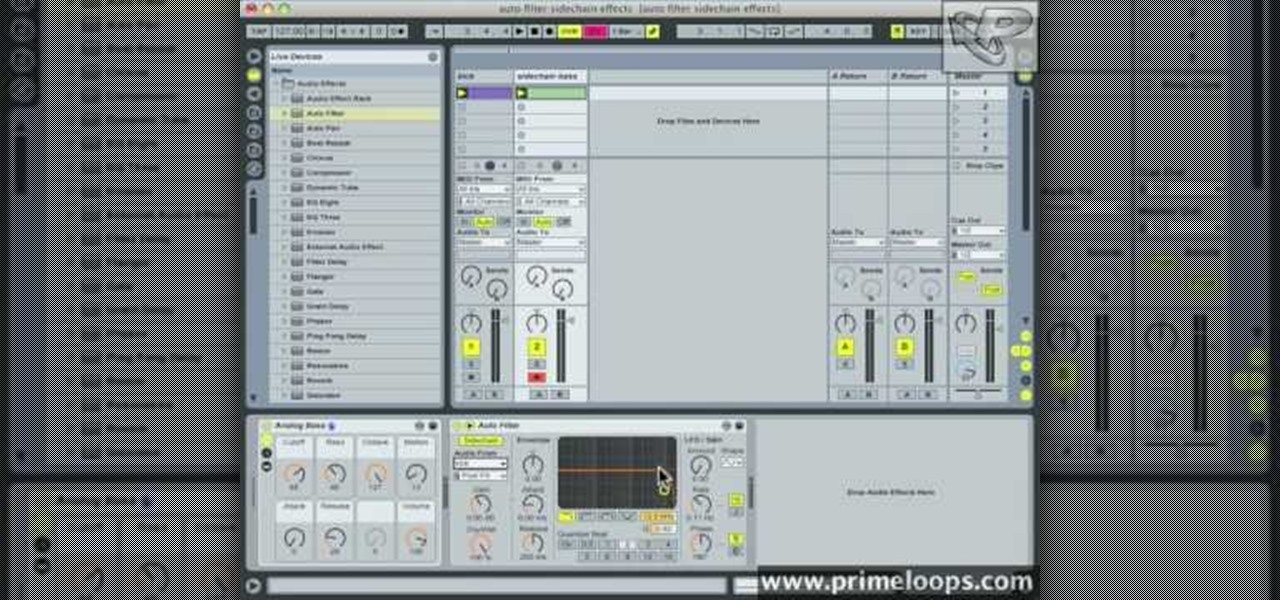
Open your program to a new live set. By using three keys (in Ableton Live), Command (Ctrl), Shift and t, you can create a short cut. Create two new midi tracks making one for (side chain) bass and one for (side chain) kick. To rename a track choose the two keys Command (Ctrl) and r. Next, you can load up the presets, located on the side bar list, one a bass, and, then a basic kick drum by opening up impulse, electronics and Tremor 1994. Now create a couple of patterns. To do this go an empty ...

Remember the Rocketeer? The rocket jet pack that he wore? Jet packs are the coolest sci-fi props that haven't been perfected in "real life" yet. Almost, but not quite. For now, film rocket belts or rocket packs will do. Like in the Bond flick "Thunderball" and in the Star Wars movies "Attack of the Clones" and "Return of the Jedi". It's even in "Fahrenheit 451" and "Minority Report". But your homemade DIY jet pack might be the best of all. Watch this video tutorial to learn how to build a jet...

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.