We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

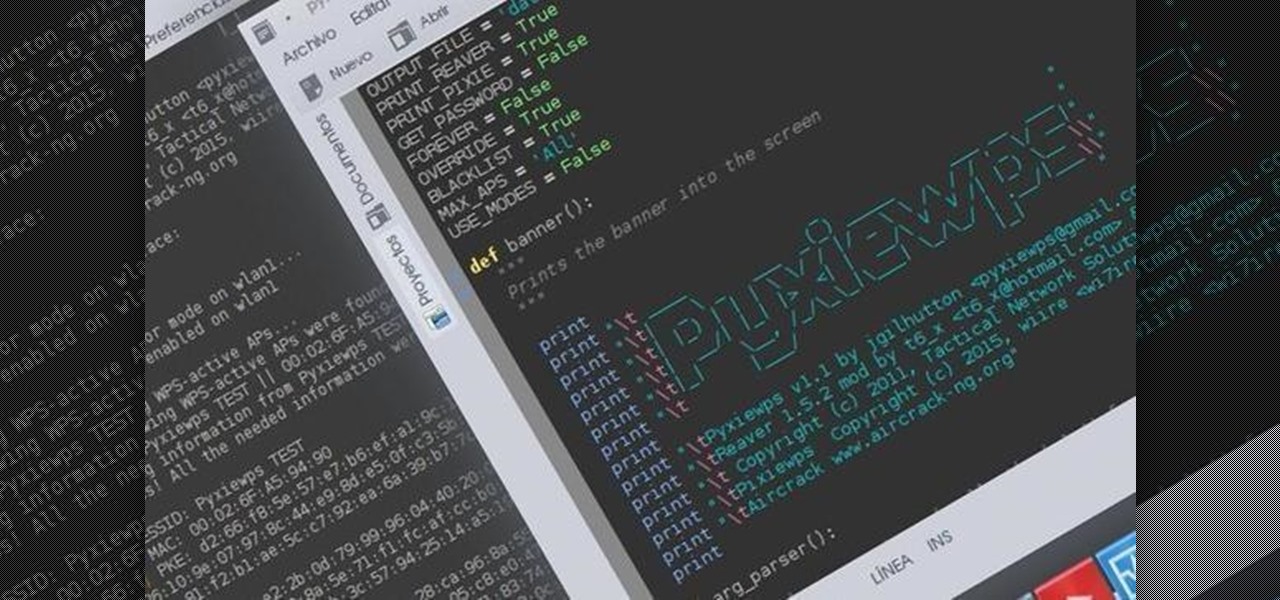
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

When you're experiencing an anxiety attack, there's almost nothing you can do to calm yourself down. At least, nothing that has worked for you yet. In this video, Chantilliscious offers up five of her tips for diversion tactics against anxiety. These are really simple tips, but when you're having an anxiety attack, the obvious is always elusive.

LEGOs are more than just a toy for young children— it's an emerging art form combining photography, stop-motion (i.e., brickfilms), and imitative models that portray today's pop culture as it is. It's something visual culture analysts are sure to be studying over the next decade, and Chris McVeigh, from Halifax, Nova Scotia, is sure to be studied for his LEGO mastery.

Is a Bridezilla driving you crazy? Whether the bride gone wild is your sister, daughter, or BFF, you can stop the insanity. Here are some tips offered on how to deal with an out-of-her-mind bride.

Learn sabre parry and defense moves in sabre fencing, including beat touch, missed attack, and more with expert fencing tips in this free sabre fencing video series.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

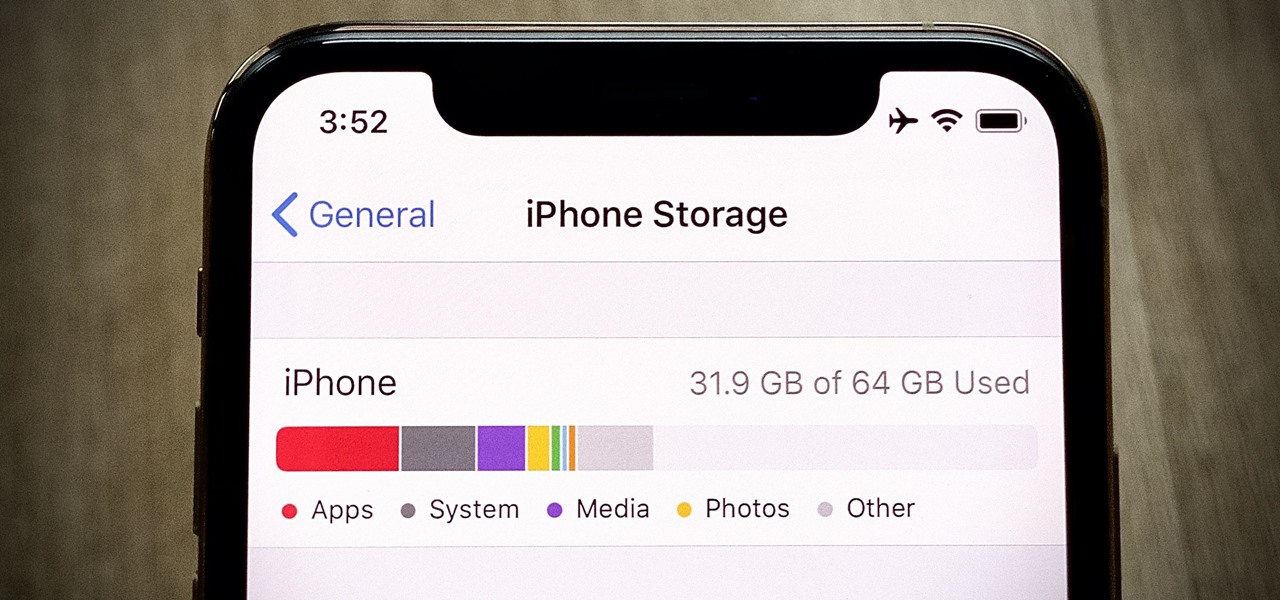
If you've ever run out of storage on your iPhone, you know how much work it can be to free up space. But all that work isn't necessary. Your iPhone can remove content automatically so you won't get any "storage full" warnings anymore — as long as you enable the option first.

Everyone seems to be talking about Elon Musk's new futuristic Tesla Cybertruck, the vehicle that either looks like a cool moon rover or an outlandish video game replica, depending on your tastes.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

To promote Battle of Azeroth, the latest expansion for the World of Warcraft franchise, Blizzard Entertainment has conjured a Shoppable AR Lens that is now available in Snapchat's app carousel.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

If you've ever wanted to hone your paintball skills, without spending a ton of money and making a huge mess, Show Me Virtual and Apple's ARKit have an app for you.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

Sending fleets of ships into battle as an ancient Nordic god? Sign me up.

It's safe to say that mobile developers are excited about the prospects of Apple's ARKit, with demos popping up seemingly on the hour on YouTube, Twitter, etc.

If there's one thing you'd never think to play music on, it's probably a coffee stirrer, right? But that didn't stop this guy from playing one of my favorite theme songs on one — "Darth Vader's Theme," aka "The Imperial March."

LARPing, or live action role-playing, can look a little silly because it requires a lot of imagination to suspend reality. But mixed reality technology like the Microsoft HoloLens can change all of that with voice commands and special effects.

I'll admit it: I ignore expiration dates. No matter if it's a sell-by date, "best if used before" date, or even a use-by date, I don't care. I just check for signs of food decay and keep on eating.

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

Turning your oven on in the summer is just asking to convert your house into a sauna. No matter how badly you want to bake cookies during a heat wave, having to deal with the boost in temperature is a deterrent at best.