The HoloLens can do some pretty crazy things such as create a robot invasion in your walls, but it can also help you do simple stuff, like hanging frames, paintings, or anything else on those walls—after you repair them from the robot attack, of course.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

There has been a huge shift over recent years to alternative medicine as people get disillusioned with conventional medicine to overcome anxiety. Natural and herbal supplements are becoming popular as people re-engage with nature. The list of potential side effects from drugs and the rebound effects from withdrawing often make the thought of taking medication unpleasant. Often the promise of how effective the medication can be is exaggerated or it simply does not have the effect it should bec...

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

You're in the middle of cooking and a car alarm, cute kitten, or neighborhood brawl made you step away from the stove for a few minutes longer that you should have. It happens to almost every home cook. Most of the time, nothing dramatic happens, but every now and then, you end up with something like this:

So, what has Arnold Schwarzenegger been up to since his role as the Governator? Besides his resurgence in Hollywood and spooking gym members as Howard Kleiner, he's getting culinary on us.

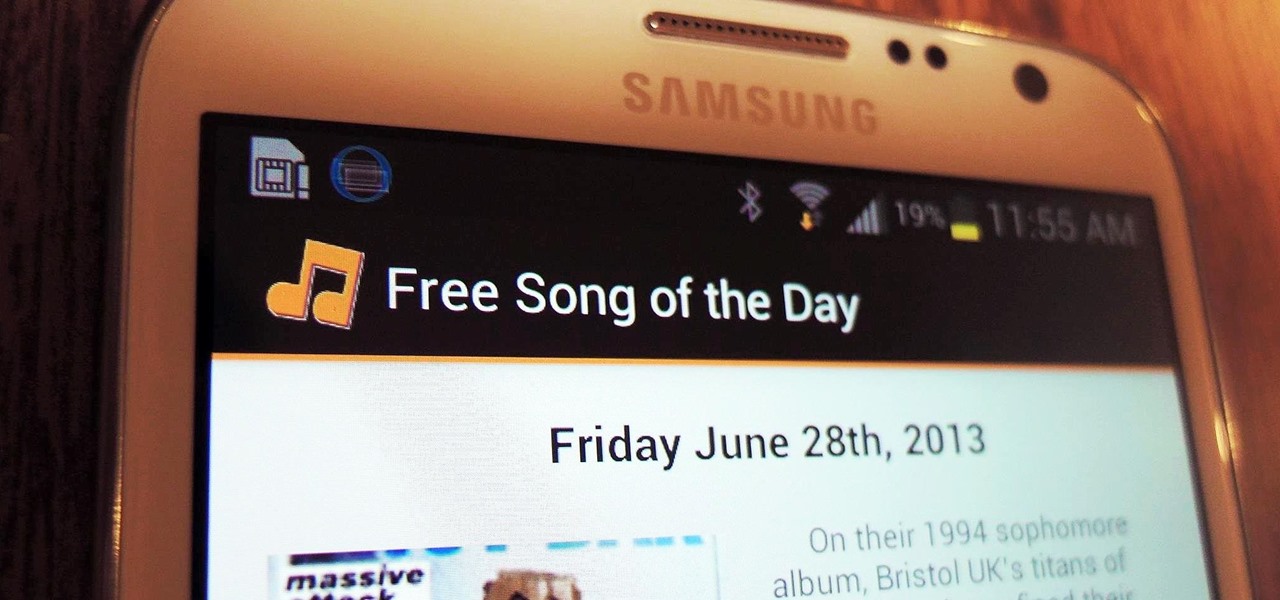
With millions of options to choose from in Google Play's expansive library of songs and albums, it can most definitely take a toll on the wallet after a while. As (slight) consolation, Google offers one free song a day, available for download straight from Google Play onto your Samsung Galaxy Note 2 or other Android device. Google's daily free song sure beats other services' free selections. Apple only offers one free single each week, and Amazon offers a decent selection of free songs from r...

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Tablets can be incredibly useful in many situations, and the kitchen is no exception. Whether you're following a recipe, using an app to convert cups to tablespoons, or getting your Gosling fix, there are a lot of reasons you might keep your tablet nearby while you're cooking.

When it comes to melee combat, two swords can definitely be better than one. Throw a stun gun on top of that and you've got a seriously terrifying weapon. That's exactly what YouTuber jonathanj9969 did with his homemade double-bladed stun sword.

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

Michael Faraday was awesome. He discovered electromagnetic induction, diamagnetism and electrolysis, and he invented the Bunsen burner (before it was the Bunsen burner). Because of his work, we can make suits that can withstand 1,000,000 volts of electricity and cases to protect our gadgets from nuclear attacks.

It can get pretty chaotic when you're gaming. When you're playing a fast-paced game like Black Ops, frustration, urgency, and confusion will lead to a sudden loss of control, i.e. a panic attack. There's an enemy at your six and you try to spin around, but it's too late—and that sudden rush of adrenaline will tear your controller to shreds. It's a step beyond mere button-mashing, because it's not really intentional—you just put a little more force on that thumbstick than needed. And now you'r...

Shane Benedict explains key techniques to an effective boof. Everybody wants to know how to boof. The boof is, without a doubt, the most essential weapon in your creeking arsenal. There are several key points to making this move effective; approach, stroke, and body placement are the three that we are going to focus on in this segment. We’ll allow Shane to explain…

So you've made it this far, and there's only one man that is standing in your way, and that's the masked butcher. If his exploding barrels, or grapple attacks, are causing you more than a little bit of an ache, don't worry, it's easy to beat him. In this video you will learn the strategy you will need to be victorious!

Learn how to make the MAPAJET (most accurate paper attack jet); loads of office fun! This video origami tutorial shows how to fold an accurate paper airplane.

This video demonstrates how to select your weapon in Gears. The video walks you through switching weapons and performing melee attacks with different weapons.

The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.