The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

In a world where augmented reality is becoming the hero of the movie marketing, Universal Studios has decided to use the technology to reinvent the traditional movie trailer, a time-tested tactic of film promotion, in support of the forthcoming Robert Zemeckis film, Welcome to Marwen.

Location-based AR game Ghostbusters World is creeping closer to launch, and developer FourThirtyThree has released some new gameplay footage and a trailer to capture the interest of the living.

Less than four months after Snapchat introduced its Snappables platform, Facebook has met the challenge with its own AR gaming feature that surpasses the originator.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-launched Survival City in the Philippines for further development. With a simple hack, you can try the game yourself right now.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Soon, Pokémon GO allies attacking a raid boss at a gym will be able to do so together in augmented reality.

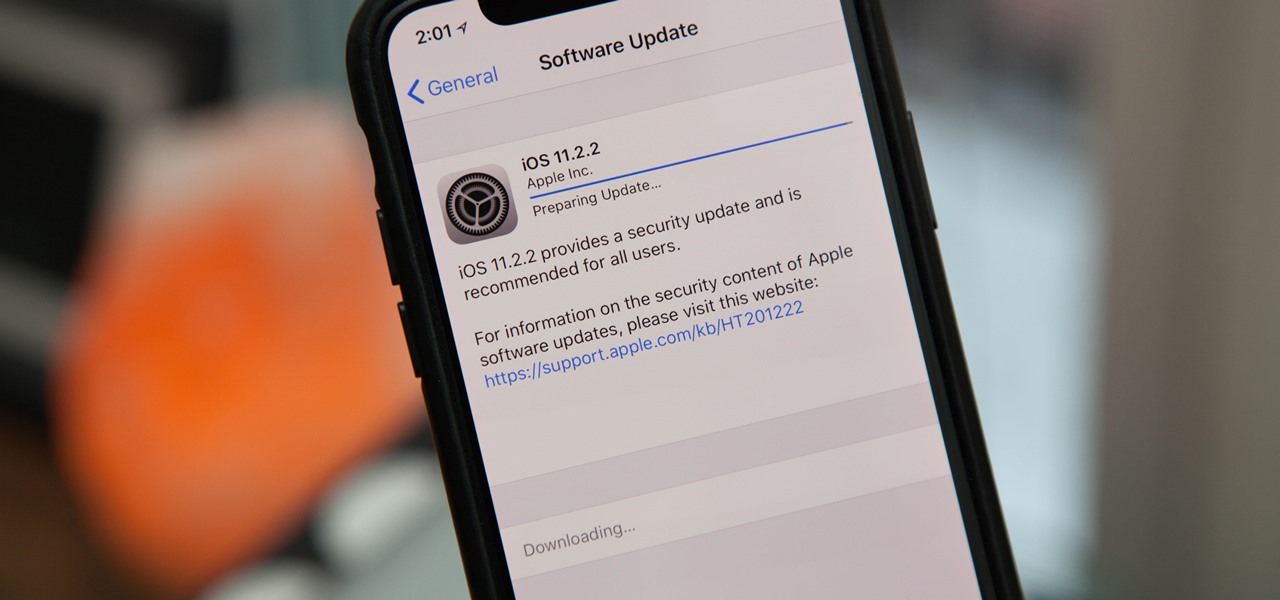
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Until Star Wars Jedi Challenges arrives in November, a forthcoming ARKit revision of HoloGrid: Monster Battle from Tippett Studios and Happy Giant, might be the closest most Star Wars fans can get to playing the HoloChess game from the movie.

Google largely helped to pioneer the concept of a steering wheel- and pedal-free self-driving experience when it began testing its Firefly pod-like vehicles a few years ago.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

You know the drill. It's time to d-d-d-duel! This time you're a part of the Shadow Games in a way you've never been before, thanks to Micorsoft's HoloLens.

Disasters can happen at any moment, and when they do, it's often hard to find the right information to help you get to safety as quickly as possible.

As a side scrolling game, performing various jumps in Super Mario Run on your iPhone or Android is as vital as eggs in a breakfast buffet.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

The Sharknado franchise is, somehow, releasing a fifth movie "Sharknado 5: Global Swarming" (groan) next month. In anticipation of the film's release, the company has decided to create an augmented reality mobile game called, prepare yourself, "Sharknado: ShARkmented Reality".

The Stories feature on Instagram has a pretty great editing program, and it's one that I think is extremely undervalued. Instagram Stories goes beyond just its Snapchat-like features, but also allows you to create more creative and original content to post on your actual profile page.

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

Based in the DC Universe, Injustice: Gods Among Us was a runaway success on the iOS App Store, generating enough downloads to rival its console-based iteration in terms of popularity. But now, the sequel to this long-running game, Injustice 2, is finally out in the wild, as it was soft-launched in the Philippines this past February.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).