Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.
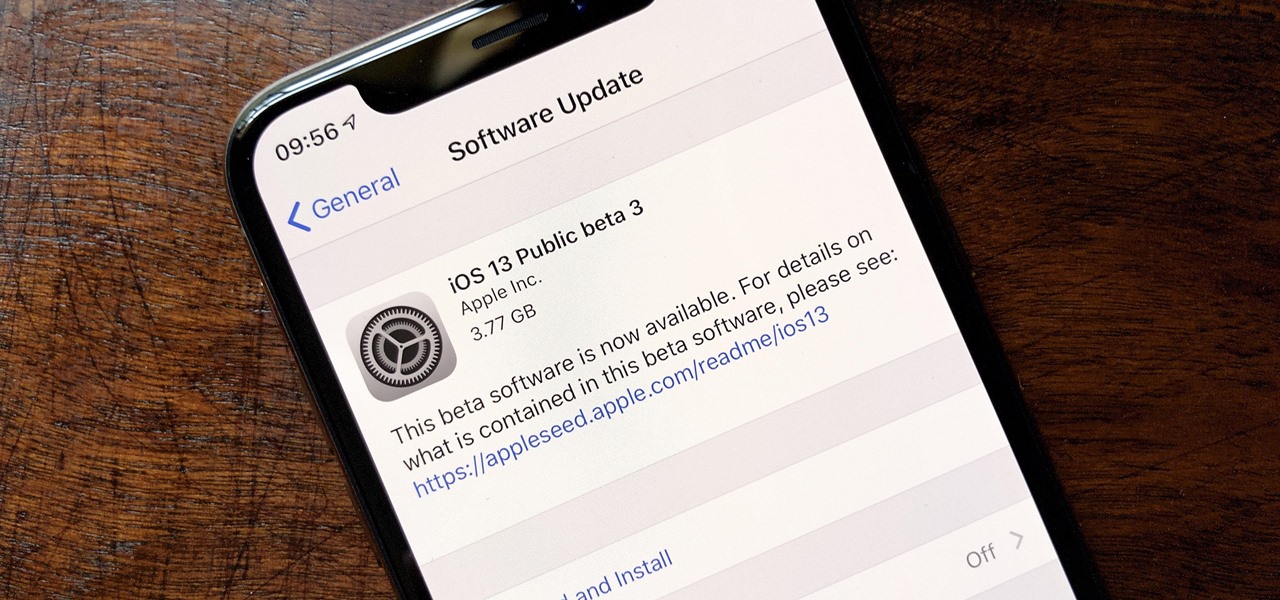
The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.
We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

Your iPhone's Messages app has some impressive new features and changes with iOS 17, and you've probably already noticed some of them just by using the updated app. But there are less apparent features, even hidden ones, that have likely eluded you that you're going to want to know about. There are even some new Messages features yet to be officially released.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Messages, and more.

Safari keeps getting better and better on the iPhone, and that's exactly what happened with the latest Safari 16 update for iOS.

The App Store has been around for almost 14 years now, and during that time, we must have seen over a million games come and go and stay and expand. But only a tiny fraction of those games have become blockbuster sensations because of the mighty App Store's reach on iPhone and iPad, and many of the first big hits are still alive today for you to relive the good ol' days of mobile gaming.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

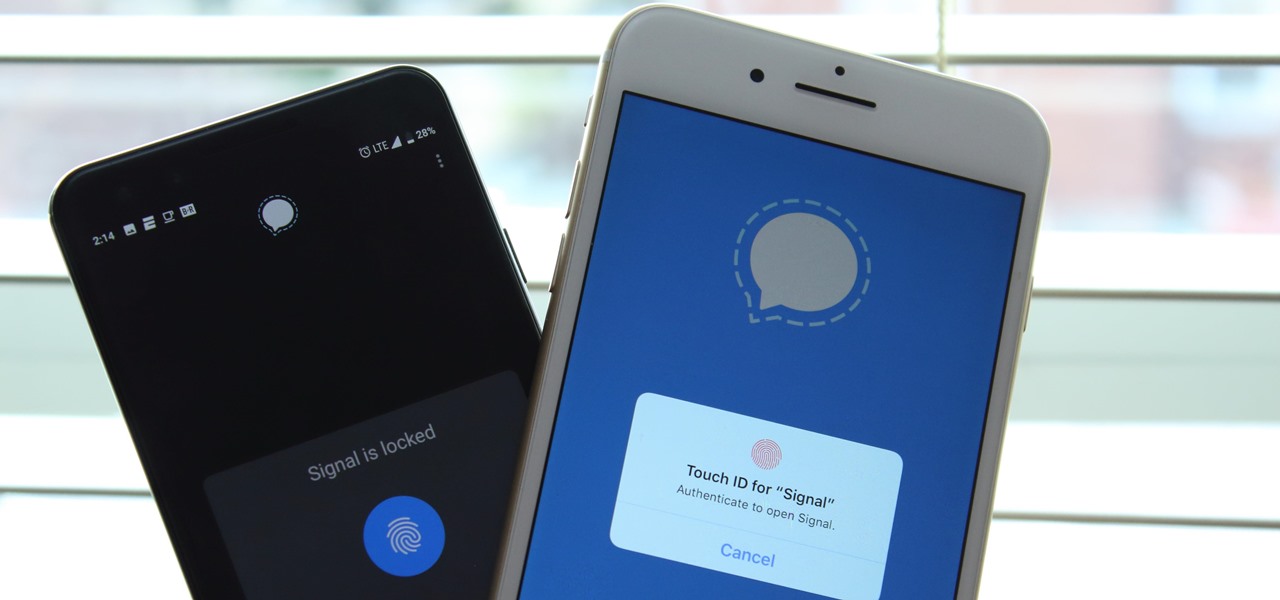
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Trying to determine whether your toe is broken or just badly bruised can be difficult. Here are a few telltale signs that’ll help you differentiate between the two. Of course, when in doubt, see your doctor. Know if your toe is broken.

To use your washing machine you will need washing powder and fabric softener. Load the washing into the machine making sure you've separated whites from colors. Choose a low heat for delicates and a high heat for badly stained clothes. Use your washing machine.

The BBC has sensationally censored a news story and a video showing Syrian rebels forcing a prisoner to become a suicide bomber, a war crime under the Geneva Conventions, presumably because it reflected badly on establishment media efforts to portray the FSA as glorious freedom fighters. » BBC Censors Video Showing Syrian Rebels Tricking Prisoner to Become Suicide Bomber Alex Jones' Infowars: There's a war on for your mind!.

Don't play dead and don't splash. Strike back. Hit its eyes and gills. This is National Geographic's excellent tutorial on how to survive a shark attack! It's excellent! Fight off a shark attack.

Watch this video tutorial for troubleshooting dishwasher problems. Check the following: are you over loading on detergent causing soapy residues? Have you stacked your dishes badly? Is the seal around the door old and worn? Do you have a dodgy pipe connection? Worst case scenerio is not good though, old machines corrode at the bottom and if this is your case then I guess it's time for a new one.

Help Someone Having a Panic Attack. We show the best measures to take to relieve someone suffering a panic attack. Come to the support of friends, family, and other members of the community. Help someone having a panic attack.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

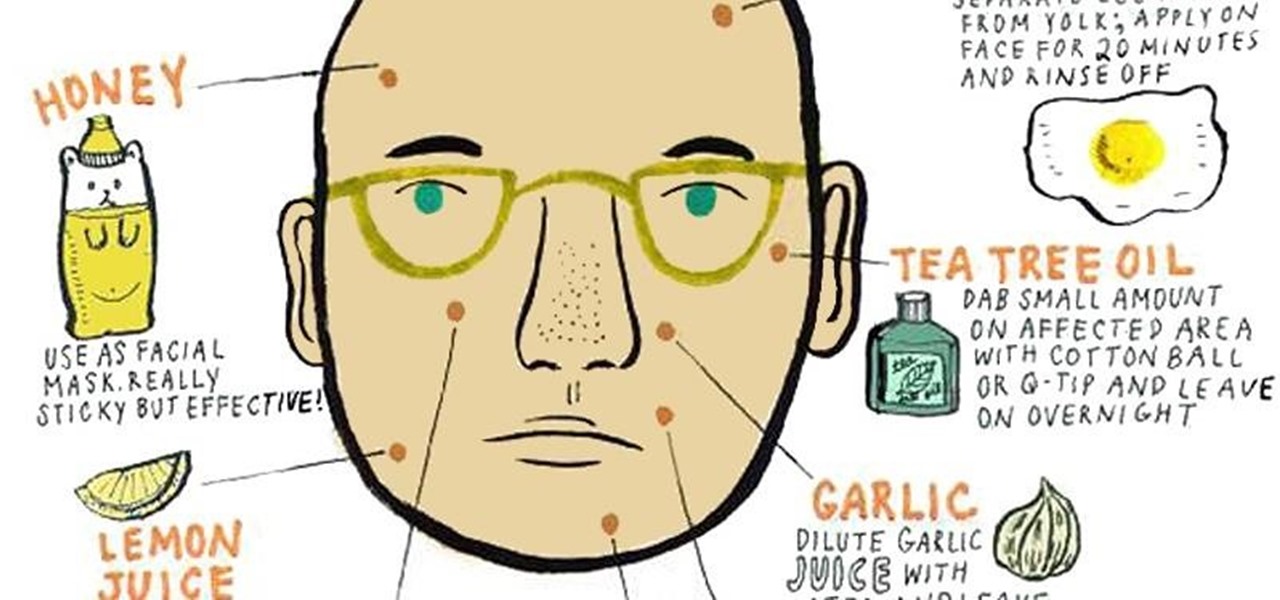
Acne medication can get expensive, but there are many common household items lying around your kitchen and bathroom that are perfect to use as a facial, face wash, or on-the-spot zit treatment to decrease the redness of acne and, more importantly, prevent future pimples from cropping up on your beautiful face.

The arm bar is a great self-defense maneuver to use when being attacked from behind. Learn to perform the arm bar for self-defense from a professional martial arts instructor in this free combat video. Defend against a back attack with the arm bar - Part 1 of 17.

In kung fu, use the twisting elbow lock to counter against the punch or grab attack. Perform this intricate defense move with tips from a professional kung fu instructor in this free martial arts video. Counter an attack with a Kung Fu twisting elbow twist - Part 1 of 10.

Misty May shows you how to handle being in the middle of all the action on offense and defense. Block and attack for middle hitters.

Israel’s Prime Minister Benjamin Netanyahu “is determined to attack Iran before the US elections,” Israel’s Channel 10 News claimed on Monday night, and Israel is now “closer than ever” to a strike designed to thwart Iran’s nuclear drive. Netanyahu 'determined to attack Iran' before US elections, claims Israel's Channel 10 | The Times of Israel.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

A Brief Summary on heart attack

Here is the 1958 Movie Trailer for "Attack of the 50 ft Woman"

In a recent address, Obama supports drone attacks against people 'on the list'. He talks about the people on the list being known of 'going to attack Americans', and who have a 'track record of terrorism'. Let me tell you, targeted strikes will, 90% of the time, have civilian casualties. There is no such thing as a clean strike. But I'll let you decide.

If you love playing those WarCraft and StarCraft strategy games on your PC, chances are you've also heard of a game called League of Legends.

To maximize your arm muscles, the "standing barbell curl" is the perfect exercise. To better maximize your muscles, keep tension on the arms throughout the move. This triceps muscle exercise from Men's Health is great for any man looking to get in shape.
Infowars has a great new article on the myths of 'limited war'. It's a great read. Here are some excerpts: