Chi gyo ichi nyo is a familiar expression in the dojo. The word chi means knowledge. Gyo means doing, or action. Ichi nyo means inseparable. Action and knowledge are one! Acting without adequate knowledge or understanding is a constant source of frustration and problems. In our lives we are often busy and active without really understanding the basis of our actions and their full impact. Some people practice karate without really knowing why they are training. In class they do the techniques ...
I have been writing since I was a little boy. I remember watching South Park at age 9 and writing my own episodes. Aside from some curse words and sexual humor that you don't expect from a nine year old, there really was not much there. In middle school I used to write short stories, usually about myself and some of the things that had happened to me. To this day no one knows that a lot of the events I have written about are true. This is something that people have always asked about. I remem...

Get 4 of the guys to challenge eachother in a doubles tennis match, once they enter the court and start playing get someone to chain the doors closed so they can't escape. Over the horizon they will here and see an attach helicopter approaching armed with mounted tennis ball guns and probably Johnny at the trigger. Begin the Attack!! The ones trying to climb over the fence should be easy to pick off. (sc. justin stafford?)

My prank will be on steve-o and chris pontius. This prank is also like the taxi prank because it is a reverse prank. Steve-o and chris will think that the prank is they will be pretending to get attacked by a man in a realistic gorilla suit, like the gorilla suit from an episode from mtv's punked. The real prank will be that a Herd of full speed bulls will run out into the gorilla enclosures and we get to watch Tour guides Steve and Chris run for their lives! Also there will be a pit of water...
SQL injection is a common web application attack that focuses on the database backend. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. I plan to use WebGoat for a few future videos. This first WebGoat video will show the basics of installing WebGoat and doing two of its SQL injection lessons. Hack websites with SQL injection and WebGoat.

About a decade ago, Deus Ex came out to rave reviews. Except this guy Tom Chick hated it. And said so, in a pretty blunt manner.

Warfare strategies have become an inspiration to different marketing professionals, many of them drawing influence from Sun Tzu’s Art of War. This ancient Chinese text provided treaties on how to effectively manage resources, tactical positioning, and timing attacks. It also states that “..if you know your enemies and know yourself, you can win a hundred battles without a single loss”, a basic concept in which you have to always watch your competitor to anticipate his next move.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

What do you expect Israel do say when a suicide bomber from Sweden kills travelers on a bus at such a high point in tension between the US, Israel and Iran?

When building an attack in soccer, you and your teammates must think as one in order for the ball to connect smoothely from player to player. Get your football cronies on the same wavelength by practicing the one-touch passing move.

Just like late-night bar hookups, a wingman in soccer is indispensible for scoring a win. Robert Pires, a midfielder who has won the FIFA World Cup and UEFA European Championship with France, demonstrates in this video how to be a good winger.

Check out this instructional safety video to learn how survive a snake bite. Snakes are not uncommon in the continental United States. There is no region in the country where you'll be completely free from a venomous bite. When a snake bites out of hunger, it releases venom through glades in its teeth. But when a person disturbs a poisonous snake, it will attack with a dry bite, in which venom is not released. Watch this tutorial to learn all about surviving a snake bite. Survive a snake bite.

THC-Hydra is a remote dictionary attack tool from The Hacker?s Choice group. It?s a well made tool that supports a lot of protocols and options. The following protocols are supported: TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, RSH, RLOGIN, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, LDAP2, Cisco AAA. Audit remote password using THC-Hydra.

Buddy Mason demonstrates how to play the straight drive for the game cricket. You should play a straight drive to a full delivery on middle or off stump. You have to lean forward and keep the bat straight. The straight drive is one of the key attacking strokes in cricket, hitting the ball back down the wicket and hopefully to the boundary! Play the straight drive.

Unfortunately, toxic and belligerent people are not as avoidable as we would like for them to be. They show up in our work place, schools, neighborhoods—sometimes even within our own circle of friends and family members. The best we can do is minimize our interactions with them and plan for exit strategies to cut the conversation short. If an interaction is avoidable because the person is your boss or family member, then arm yourself with a few verbal defense moves to keep yourself from getti...
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.

Chicago cops, the FBI, Homeland Security, Secret Service and a large number of unnamed others have established a high-tech secret command center to surveil people exercising their First Amendment right in Chicago as the NATO war council unfolds this weekend.

After his fall from Asgard into space, the Asgardian Loki meets the Other, the leader of a warmongering alien race known as the Chitauri. In exchange for retrieving the Tesseract,2 a powerful energy source of unknown potential, the Other promises Loki a Chitauri army with which he can subjugate the Earth. Nick Fury, director of the espionage agency S.H.I.E.L.D., arrives at a remote research facility during an evacuation. Physicist Dr. Erik Selvig is leading a research team experimenting on th...

As a follow-up to an earlier post on surviving deadly animal attacks in the wild and another one on relieving a jellyfish sting, listed below are things you should do (and shouldn't do) if you are ever bitten or stung by potentially poisonous wild animals.
The United States asked Russia to send Iran a message that the upcoming round of nuclear talks is its last chance to avoid a military confrontation this year, Russian newspaper Kommersant reported Wednesday according to a diplomatic source.

Whether it's a shark in the ocean, a crocodile in the swamp or a swarm of angry bees, trekking through the wilderness always comes with its fair share of perils. To prepare for the worst case scenario, equip yourself with the right knowledge—then the worst that can happen to you is an awesome bar story when you tell your friends about your close encounter.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

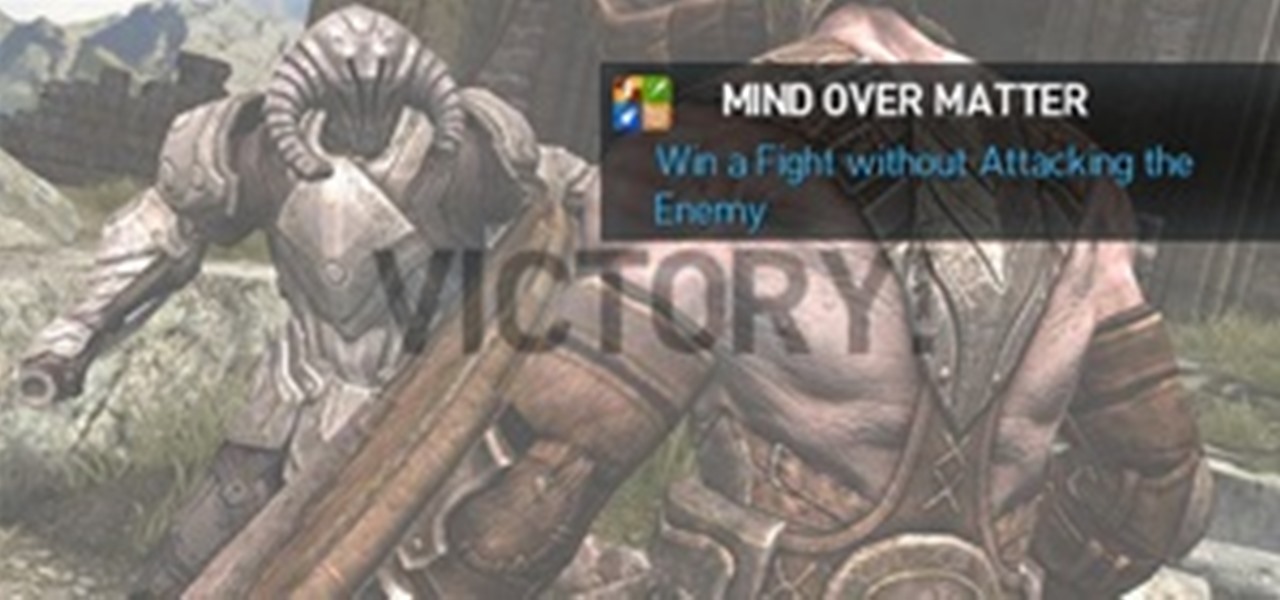
If you were to read the achievements list for Infinity Blade II, you'd come across a rather peculiar one called 'Mind Over Matter'. To get this one, you have to defeat an enemy without attacking him. Say what?

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Twisted Pixel Games' The Gunstringer is easily the most ridiculous game of the year. I mean, you play as an undead cowboy marionette, legendary director Lloyd Kaufman is in it, and at the end of the game, you shoot the developers. Oh, and the first boss in the game is an inflatable wavy tube man.

Further proving I need to start the College of Winterhold quest line already, here comes this achievement tutorial for 'The Eye of Magnus'. This is the last main quest for the College of Winterhold, and the coolest looking quest in the storyline. In true fantasy fashion, there's a really evil wizard looking to uproot all of reality, and you're tasked with taking him down for good. Here's a tip, though: shoot The Eye of Magnus with The Staff of Magnus so you're able to directly attack Ancano.

An unholy Sabbath Running from a unholy presence chasing me down

So, there you are, walking along a mountain range in the beautiful game The Elder Scrolls V: Skyrim, when all of a sudden a vampire attacks you. Oh no! Now you've caught Sanguinare Vampiris, otherwise known as the vampire disease. That's horrible for your goody-two-shoes character, since feasting on the blood of innocents isn't really your bag. That's where Achievement Hunters comes to your rescue! In this tutorial, Fragger and Jack show you how to initiate and complete the quest to become mo...

Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut down some of the games that offer web users a giant share of their online fun. World of Warcraft, League of Legends, EVE Online, and Bethesda Softworks have all been targeted by LulzSec's hacking efforts in the last week,...

The aging and maturity of video games as a medium has lead to some unfortunate consequences. One of these, perhaps drawn from the film industry, is the spate of remakes that has overtaken the game market over the last few years. It hasn't been as bad as the remakeorama trend in cinema, but developers have recognized the value in releasing the same thing they already made and making more money off it. Below, a roundup of some remakes of classic games released for XBLA recently, some fantastic,...

Those persistent alien beings from Space Invaders have finally abandoned the confines of their video game quarters, setting their crab-like eyes on the destruction of Earth. And it's up to one man to save the fate of human kind as we know it—Jeremiah Warren. Equipped with his trusty Atari CX-40 joystick, the lonesome savior battles the descending alien invaders, destroying them one by one with his laser cannon, right from his own bedroom window. See the battle below. The filming took about th...
Today my friend finished his house then got blown up by a creeper upon finishing it. He also found 3 wolves- two of which fell off a cliff.

From Boston.com's The Big Picture, what a real-life version of the Green Hornet's gas gun might look like. Taken in Afghanistan in February of this year, an Afghan army recruit is pictured shrouded in a cloud of shocking green smoke as he participates in a graduation parade after an oath ceremony at Ghazi military training center—an American effort to strengthen Afghan forces so they can fight against Taliban strongholds.

Blacksmith Sage Werbock —also known as the Great Nippulini, "pierced weight lifting extraordinaire"—welded together this Star Wars Imperial Walker sculpture with a bunch of old computer parts and scrap metal. Currently listed on Etsy for $450, the AT-AT is artfully assembled as follows:

Here are Jerry Brown, Meg Whitman and Arnold Schwarzenegger at the Women's Conference a couple weeks ago. The host of the "Today" show, Matt Lauer, asked both gubernatorial candidates if they were willing to get rid of their negative ads and make positive ones instead. Brown said yes but Meg Whitman said no and gets booed by the women in the audience.

Blood, guts, gore- it's precisely what Halloween's good for (plus Halloween candy… especially deep-fried Halloween candy). If your running out of time to behead yourself, then try Instructables member gnatquill's "nice effective quicky if you've left it too late for Halloween".

What could possibly make Halloween candy even better? Cakespy suggests deep frying it, Paula Deen style. First, gather your (already) fattening, deliciously classic Halloween treats: candy corn, mellowcreme pumpkins, Reese's Peanut Butter Cups, Twix, Kit-Kats, Whoppers. Second, roll 'em in batter, and third, drop your batch right into a vat of hot, sizzling oil.

From The LATimes: "Brown, the Democratic nominee, touted talking points — living within California's means, no new taxes without voter approval, returning control to the local level — that could come from a Republican playbook. Whitman, his GOP rival, unveiled her seventh attack ad against Brown, this time enlisting the words of former President Clinton during their contentious 1992 Democratic presidential primary battle. Tellingly, both candidates avoided mention of their political party.

alright this might be dangerous but fun. it would involve going some place where people get really offended. everyone has a car and some else gets to paint it how every they want. the goal is to get people from the street to attack the car. it would be like going to the south and writing NASCAR is for F**S on the other guys car. but in order to win this game who every can pull over and get the most amount of people to give you directions wins.