News: News Clips - June 10
3,000 soldiers to serve in Africa next year A brigade will deploy to Africa next year in a pilot program that assigns brigades on a rotational basis to regions around the globe, the Army announced in May.

3,000 soldiers to serve in Africa next year A brigade will deploy to Africa next year in a pilot program that assigns brigades on a rotational basis to regions around the globe, the Army announced in May.
Yesterday senior State Department official Alec Ross publicly announced that the Obama administration opposed CISPA, but refused to entertain the notion of the bill being vetoed.
A Pakistani lawyer who represents victims of U.S. drone strikes has been forced to cancel a trip to the United States after the U.S. government failed to grant him a visa. Shahzad Akbar was scheduled to speak later this month at an International Drone Summit in Washington, D.C. Akbar is co-founder of the Pakistani human rights organization, Foundation for Fundamental Rights. He filed the first case in Pakistan on behalf of family members of civilian victims.
Well I'm so surprised.

Besides Wikipedia and teachers (in that order), textbooks are the go-to source of information during our school years. Today, we take a look at what happens when the people writing these voluminous tomes get attacked by a sudden bout of ennui.

As you may or may not know, MegaUpload - one of the largest file sharing services has been taken down by the feds.

What Is Hypoglycemia Hypoglycemia is the medical term used to describe a state of lower level of blood glucose. It produces different symptoms and effects resulting from inadequate supply of glucose to the brain and it leads to impairment of brain function.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

Can you really make an explosive from salt, sugar and weed killer? Does glycerol and water actually recover text from burnt paper? Is it possible to develop film with a first aid kit and some orange juice? MacGyver says yes.
My friend has been through a lot. He's fallen down cliffs, been killed by lava and attacked by wild wolves. Let me explain about the "been killed by lava" bit:
to be honest with everyone, this is probably the first thing ive written about magic the gathering, but i figured i might as well start somewhere. in the game of magic the gathering there are countless different keywords, some being common, like trample, or rarely used or seen, like splice. what i wanted to do was take a closer look at some of the different keywords out there, and see just how they change the average game.
This are my tips for fifa 11. The following are purely my opinion and what has worked well for me, it is not my fault if the same things do not work for you.

As far as new artists go, 2010 more or less belonged to this 23-year-old Nashville native, who released her hit debut, "Animal," in January, then followed it up last month with a nine-track mini-album, "Cannibal."

National Geographic is holding their annual Photo Contest, in the categories of People, Places and Nature. If you're interested in participating, check out the guidelines now. Time is running out- all submissions must be in by November 30th.

As Theo Gray of Gray Matter demonstrates below, contrary to what the ads may say, diamonds CAN expire. Especially when attacked with a blow torch and liquid nitrogen. Gray says:

A recent Japanese study proposes a simpler, softer, more natural-feeling alternative to silicone breast implants: fat-derived stem cells. The cells are extracted from liposuctioned fat, and then injected into the patient to increase breast circumference. San Diego-based biotech company Cytori Therapeutics is currently waiting on FDA approval to start clinical trials.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

Dr. Elena Bodnar proposes a silly idea. Why not wear a bra that double as a gas mask? No point in being ill equipped (in the event of fires, terrorist attacks, dust storms or a swine flu outbreak). The instructions are simple: In the event of an emergency, remove bra.

Ever been warned that sitting too close to the TV might damage your eyesight? It won't. That probably won't stop this electronic View-Master from giving your poor mother a heart attack, however.

There are endless deep-fried recipes for disaster (re: heart attack), but this one takes the cake. Abel Gonzales Jr., the inventor of fried Coke and fried cookie dough, presents deep-fried butter, which tastes like a “a mix between a biscuit or a croissant that is just stuffed to the gills with butter on the inside.” Gonzales' creation took top prize at last year's Texas State Fair.

This weekend in a jungle estuary, the DEA and local Ecuadorian police seized a prototype narco sub that may be the most sophisticated one yet. Complete with air conditioning and periscope, this 100 foot creation would have carried a more cocaine tonnage than any previously captured narco sub. To give you a perspective on the resourcefulness of these outlaws, consider this. A U.S. Navy Virginia Class attack submarine will run around $2.8 billion. But a drug lord in Cartagena would make you one...

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

You might know the feeling: the sinking stomach that informs you something terrible has happened. You click on your trash bin. Nothing is there. Your hard drive has been wiped clean.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.
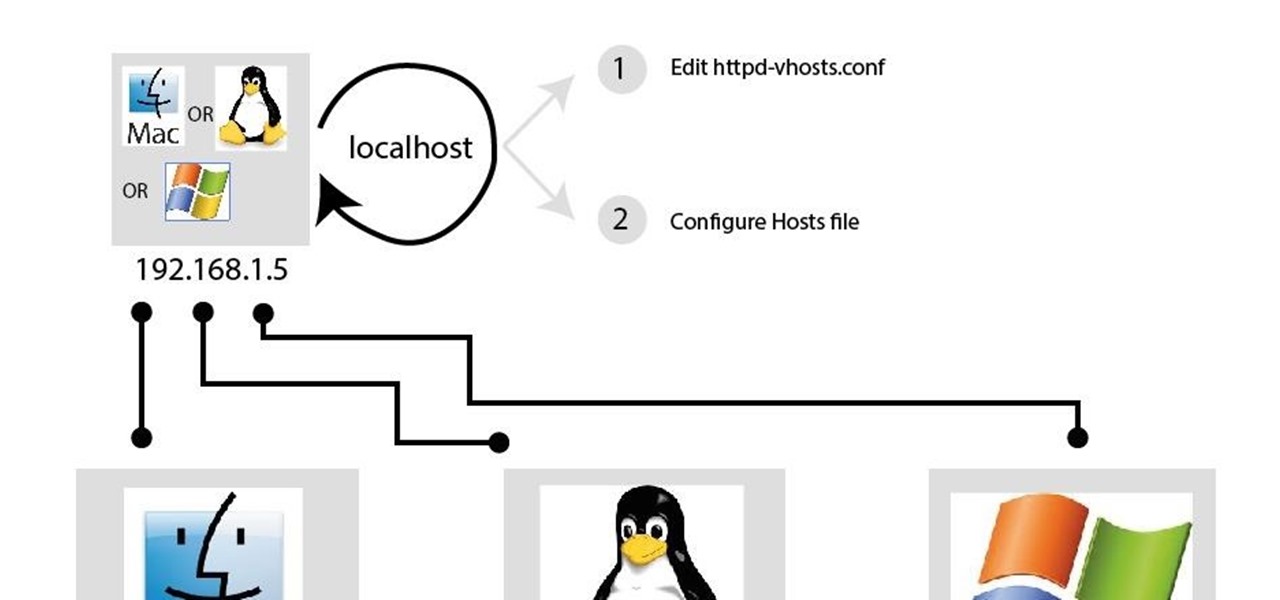
In my last article, I discussed: How to install xampp
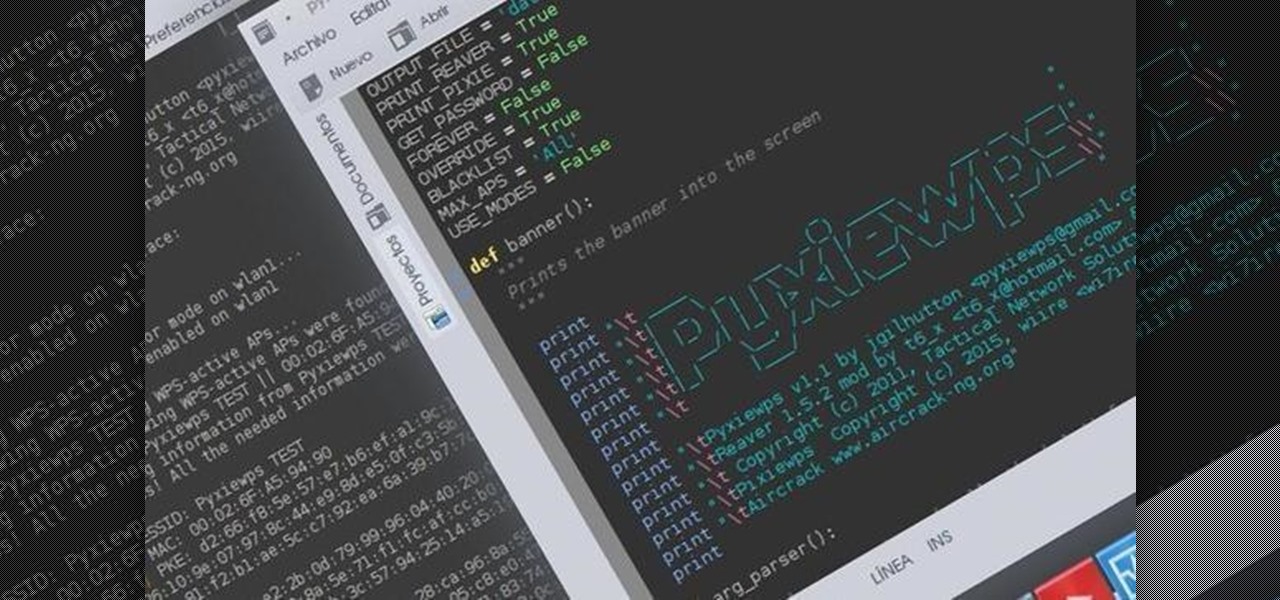
Helo my dear friends! A few days ago, I shared with this community my wrapper-script (a wrapper is a program that joins other programs that do the real job) to automatize the attacks on Pixie-Dust vulnerable routers. I was recieving complains from non-Kali users that had problems trying to launch the program, so I decided to make a good installer so anybody can use it in any DEB based distro.

Charlie Miller and Chris Valasek conducted an experiment earlier this month that ended up with a Jeep in a ditch, although the driver didn't drive it there. The two remotely hijacked the car, controlling it through a laptop and a cell phone. FCA says vehicles from the 2013 and 2014 model years with 8.4-inch touchscreen are affected. That includes Ram pickup trucks, the Dodge Durango, the Jeep Grand Cherokee and the Viper. Some 2015 Chrysler 200 sedans are also affected.

This is a followup from my recent series on XSS exploitation, giving a few extra attacks/tricks to try.

In the wake of a horrific attack on its Paris headquarters, satirical newspaper Charlie Hebdo has responded by upping its print run from a typical 60,000 to upwards of 3 million. This commemorative issue, Tout est pardonné ("All is forgiven"), has been met by such demand that the publisher is turning to alternative forms of media to reach as many viewers as possible.

Over the last few months I have been getting more and more into computers over the last few months, and I discovered my new favorite thing to do..... notepad stuff!

The Black Friday shopping battle is just around the corner. At the end of the day, will you emerge empty-handed or victorious with an armful of shopping bags bursting at the seams?
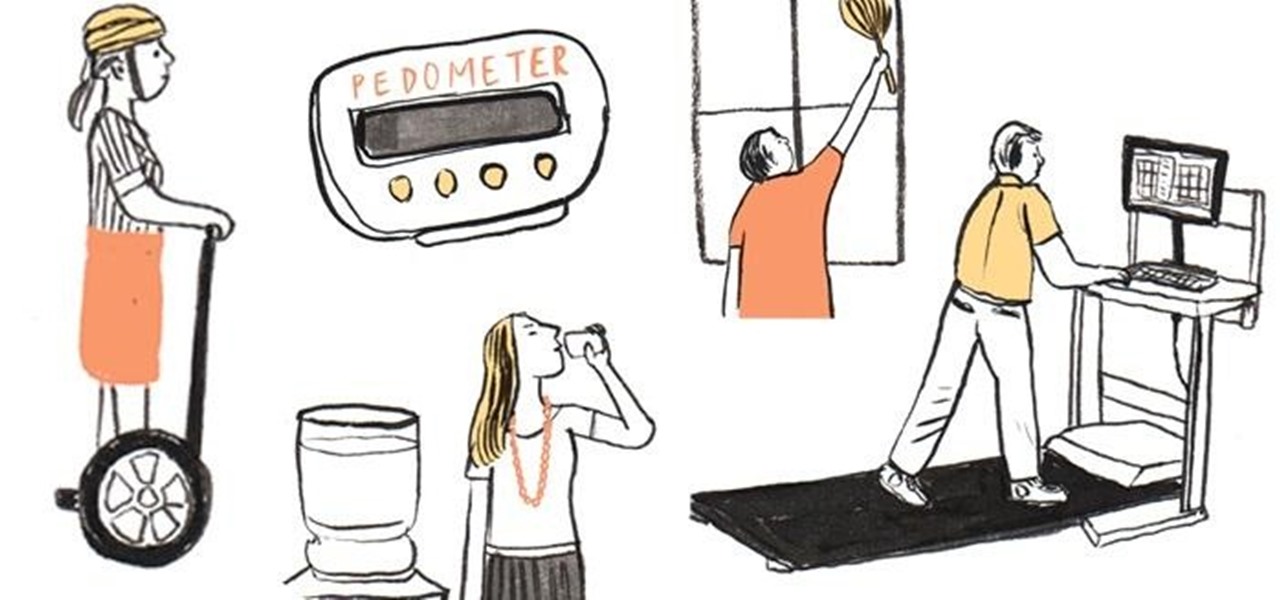
Are you sitting down as you read this? You might want to stand up for a little bit. In case you haven't heard, sitting for prolonged periods of time is really bad for your long-term health—so bad that chronic sitters are 54% more likely to die of a heart attack, even if they are non-smokers or regular exercisers.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Okay so it begins with someone either me or one of the jackass crew in the classic old person makeup that makes them look as nasty as possible. Then we get in an elevator with unsuspecting people and the "old person" pretends to be having a heart attack or something. finally, then we convince one of the strangers to give the nasty-ass old man mouth-to-mouth resucitation :) the person playing the old man make it gross as possible and throw in some tongue moves too.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...