
How To: Change character stats in Mugen
This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.


This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.

Shaun of the Dead's Nick Frost faces an ornery alligator and learns a few useful tricks in the process.

Learn to perform a Jiu Jitsu Banana Split leg submission. This is a submission for grappling not self defense. It attacks the groin by pulling the muscles apart.

A pinch harmonic is an overtone. This video is a demonstration of how to play a pinch harmonic on the electric guitar with a right hand technique. Distortion, attack, vibrato, pick selection and more are discussed in relation to this topic.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.
Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

How to replace a tap washer. Dripping Tap. Dripping Faucet. Replacing a tap / facuet washer is quite an easy process as long as you follow the 6 steps in my video. Basically all you need to do is this:

The Asylum Demon boss fight in Dark Souls showcases yet another demon with a giant weapon. You'll need to be able to dodge his jumps and mace attacks if you're planning on defeating him. This video walkthrough will show you how to quickly beat the boss.

A recent addition to Mortal Kombat 9 in the form of DLC has reintroduced several classical features of Scorpion, Sub-Zero, and Reptile including some of the more traditional fatalities. Take a look at this video from the Achievement Hunter team and watch for the commands necessary to perform each of these violent attacks.

Keep your Runescape account safe from hackers by following the instructions in this video. Don't get hacked by giving your password away or using unsafe websites. Watch this video and learn how to take precautions against hackers so you can enjoy Runescape worry free.

Are you working on a zombie movie and need to step your gore up? Or do you just want to scare your friends with an ultra-realistic halloween costume? Check out this video that shows you how to apply a prosthetic.

Are you interested in developing your artistic talents? Have you got great ideas for cartoons but not enough technical know-how to make them come to life? This video will show you to draw a cartoon cat that will jump right off the page.

Dragon Age 2 is the latest fantasy RPG from the folks at Bioware, and if you're watching this video you've probably either just gotten it or are thinking about it. Check out the vid for a walkthrough of the prologue quest, Destruction of Lothering.

As Desmond travels into the past, he discovers some strange layered memories hidden within Ezio's consciousness. And then as Ezio, you must journey to Roma and confront the forces of the Borgia Pope, who has brought your family under attack.
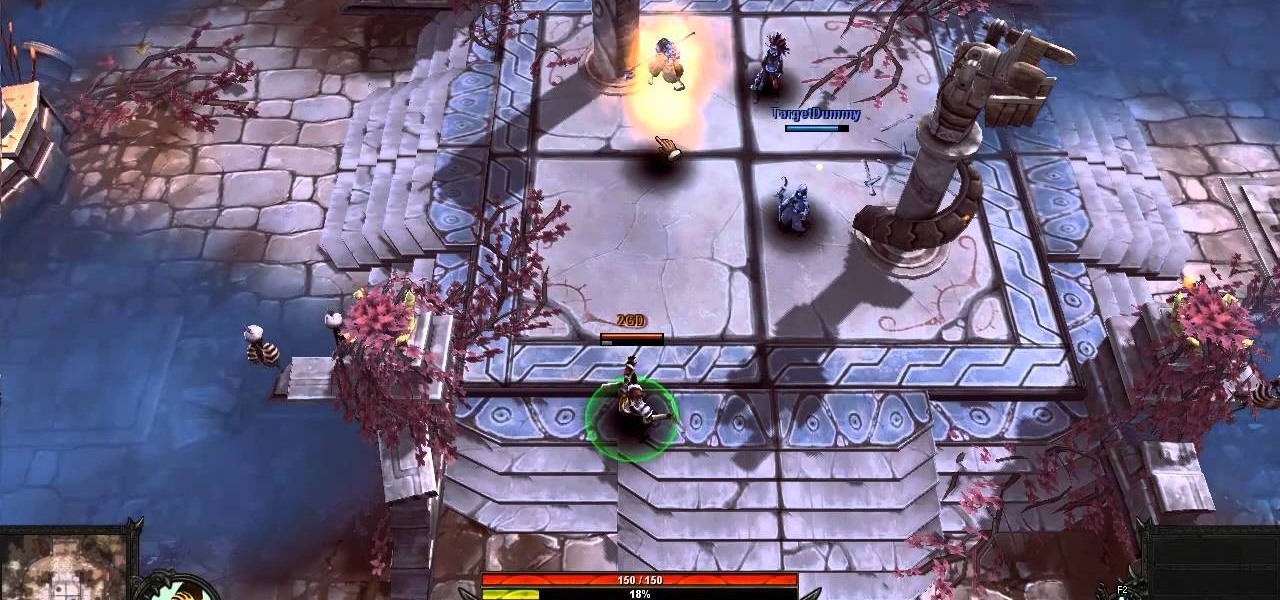
The boomerang wielding Nomad is good at both ranged stun attacks and crowd control, and can be adapted to fit a variety of play styles. Here's how to integrate Nomad into your own team matches when you play Bloodline Champions.

King Dedede is the final boss in Snow Land in Kirby's Epic Yarn. He's one of the tougher bosses to defeat, since grabbing the buttons to defeat him can be challenging. Fortunately, his hammer attack is fairly easy for Kirby to dodge!

Halo Reach is newest edition to come out from the "Halo" series, featuring really cool advanced CGI and super fast attack vehicles called ghosts. These cars look almost like gigantic beetles, with a pod-like midsection and two wings on the side.

Want to be the best spear fighter you can be? This tutorial show you two basic shots you can make when wielding a foam spear on the fields of battle at your next boffer larp. You're also shown how you can thwart a javelin shot with a spear.

If you or someone you love is undergoing heart surgery in the near future, it's important that you have a solid grasp of the potential complications such that you can do everything in your power to avoid them. In this brief medical-minded tutorial from ICYou, you'll learn about a few of the most common complications including bleeding, infection, damage to blood vessels, heart damage, heart attacks or strokes.
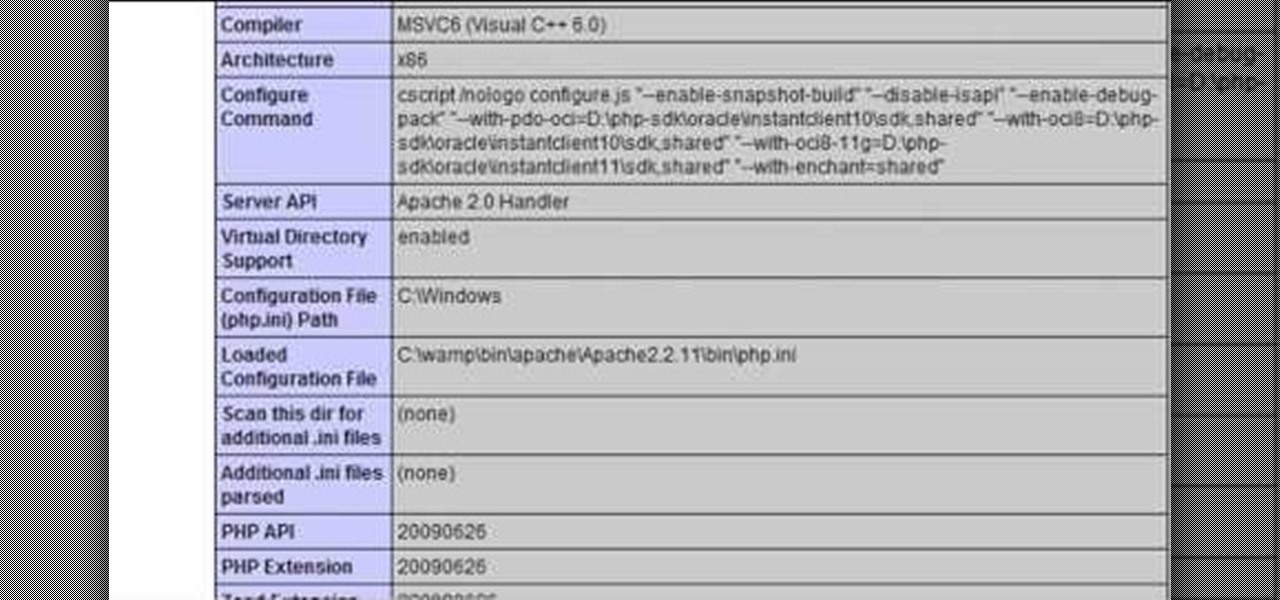
In this clip, you'll learn about how to prevent SQL injection when writing code in PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

In this God of War 3 tutorial, discover what it takes to complete the Knockout Challenge. It's easy to complete and requires you to do two things:
Computers are vulnerable to all kinds of viruses, hacks and other attacks that can do serious damage and cost you money. Make sure your version of Windows is the real deal and protect it from counterfeiters by making it genuine. This video will show you how to make Windows XP genuine.

Grab some paper, pennies, and paper clips, and create this stealth weapon in the comfort of your own bedroom. Scaled to actual size, this craftable katana can be used to fend off paper-based attacks, or displayed for decoration. Add as many, or as few, foldable components to customize your sword size.

Spidering enables you to maintain a position of power, where you can pass, shoot or move quickly. Spidering is the position where one hand is sculling, and both legs are doing eggbeaters. This is a standard water polo position for both attack and defense.

Shooting in water polo is a basic skill for attackers. Water polo shot requires good height out of the water, arm position, shoulder rotation, and head stall. Shot strategy is important to building your water polo game. Concentrate on improving your rotation to follow through and speed up the shot. This is an attack focused water polo drill.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.
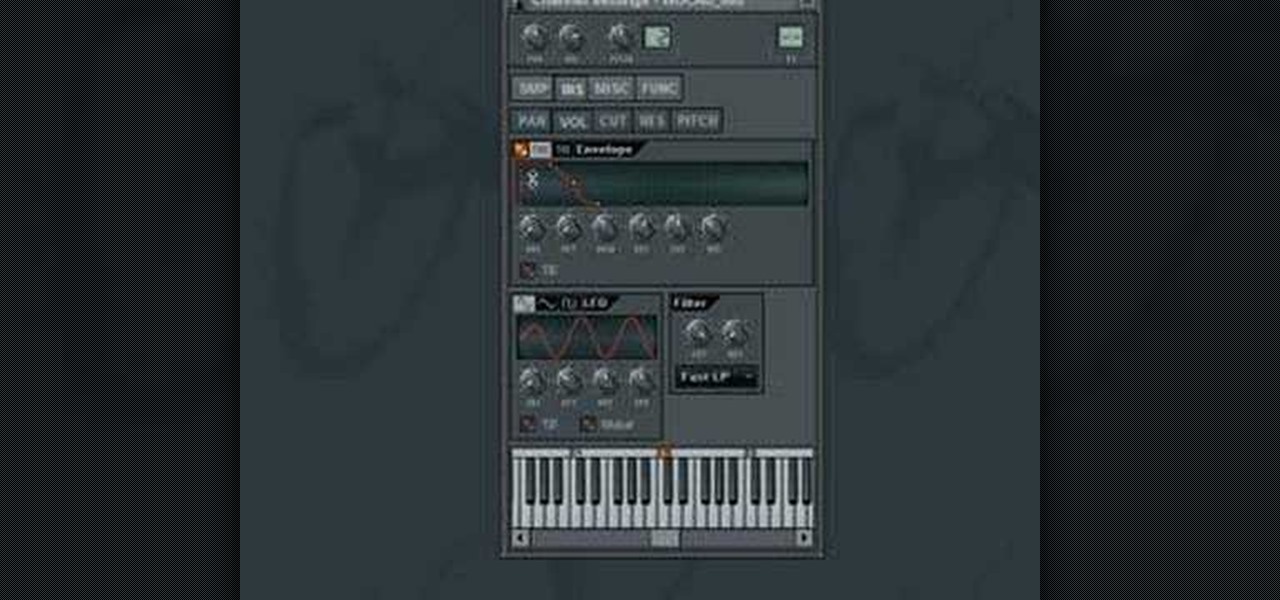
The famous ADSR Envelope (Attack, Decay, Sustain and Release)... It's seen in almost every virtual instrument or software synthesizer from Albino to Halion to SampleTank to Z3ta but do you know what it does?

This is the set up I use for the straight jacket submission when someone defends the gogoplata. This submission attacks the shoulders depending on how flexible you are. There are a couple of ways to set this up.
This tutorial shows you how to path Artificial Intelligence monsters in Unreal Engine 3 for Gears of War. This allows them to move around and get them to attack players.

It's Jaws! No it's just face paint, but watch this video to learn the tricks and tips to apply face paint and look like a shark!

Today's word is "thwart". This is a verb which means to prevent from accomplishing a purpose or a plan. For example, you can say "The police thwarted three terrorist attacks at LAX last month."

After a series of quarte disengage attacks, Bijan takes several counter-ripostes before finishing with a fleche. (For those striving for perfection--He's too close when I'm coming forward/hand is too far back in his sixte parry & he's not fully stretched in the fleche--Aside from these things, I think Bijan has admirable form but I'm his coach & biased...)
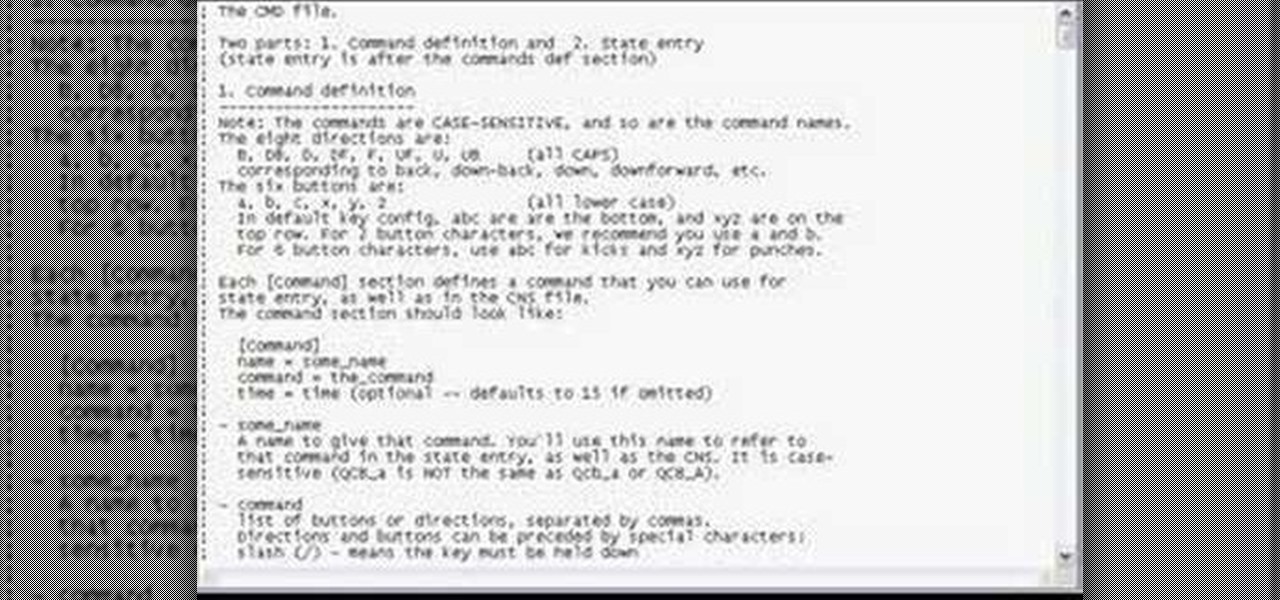
This is a tutorial on how to access characters command list in Mugen - the custom PC game engine - to see how to perform special attacks and basic moves.