Besides being useful, mousetraps can be pretty loud, which makes them perfect for the prankster at heart. They can scare the crap out of your intended victim, but for some, giving them the heebie-jeebies can be more difficult than just a normal trap. They might not scare as easily with a short burst of sound. But they will if you add a few mods to that everyday mouse trap!
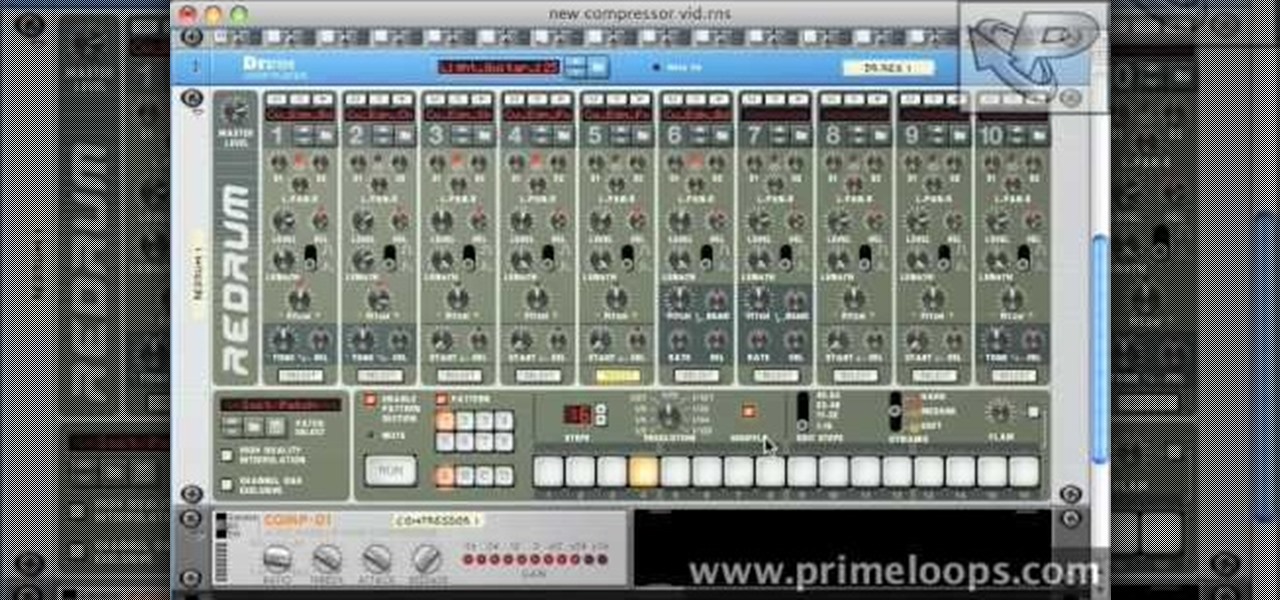
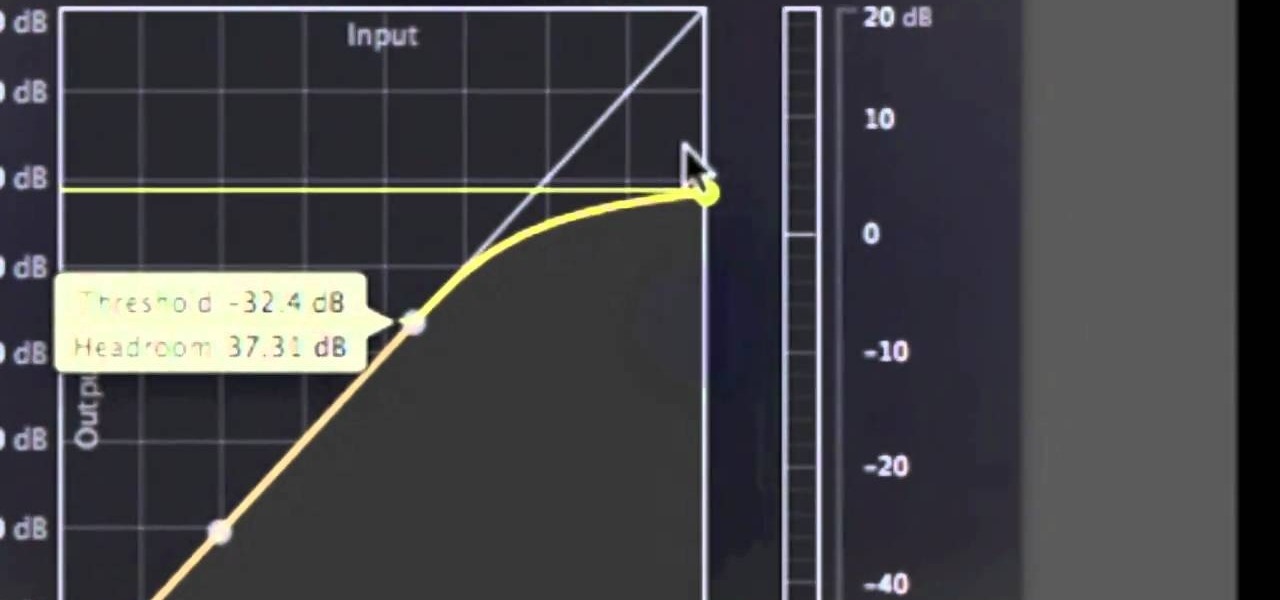
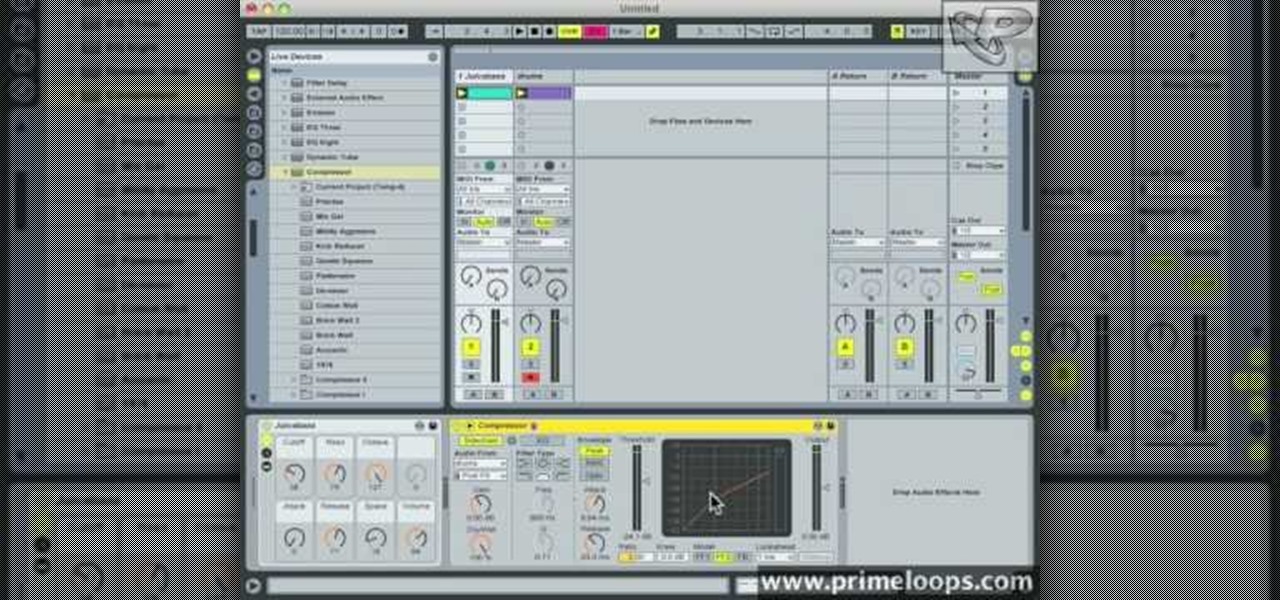
This tutorial video will show you what the purpose of compression is and how compression works through its parameters. Your instructor illustrates a drum beat and a plucked guitar line. Beginning with how to compress the drum beat, take (download) a drum sound pack without compression and to add compression using the software right click on the drum machine, choose create, and then choose combo on compressor. The virtual compressor has all the dials and adjusters found on any basic compressor...

If you can't beat Silitha in the Xbox 360 video game Darksiders, then perhaps you should check out this video on accomplishing just that. Silitha is a gigantic and ugly spider-like creature that dwarfs War. She can teleport around the arena and likes to appear directly above War and attempt to crush him beneath her. Silitha will appear around the edge of the room and taunt War. Get just about past the middle of the room towards her then use your Abyssal Chain to pull yourself directly at her ...
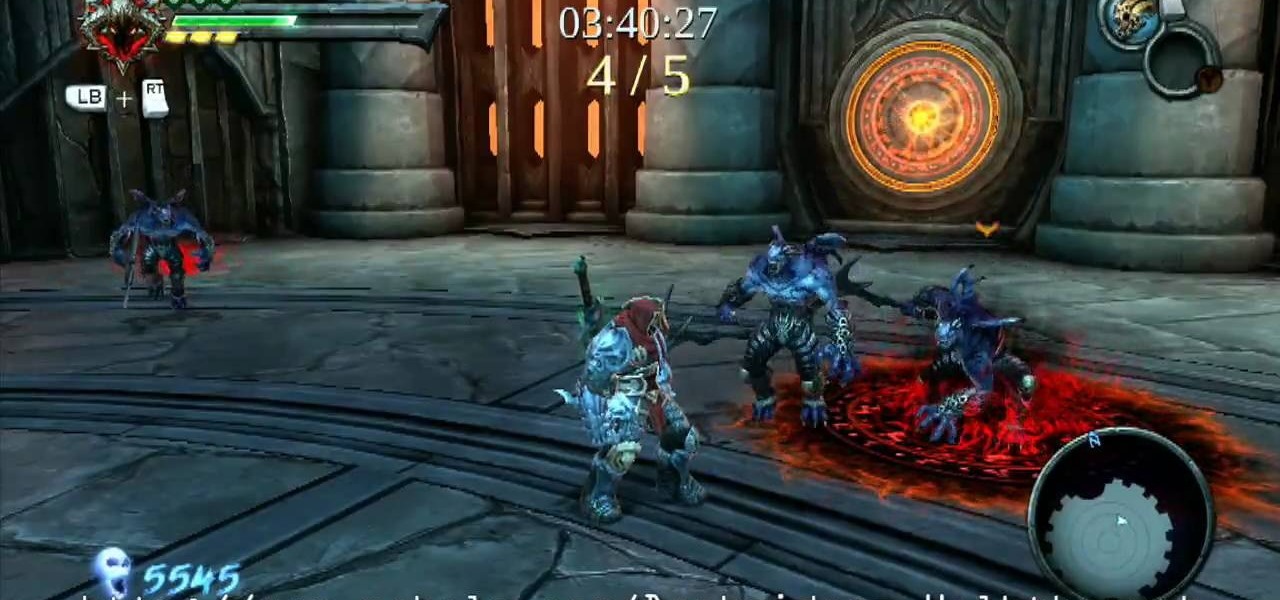
Get ready for one heck of a battle in the Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

Get ready for this Shadow Arena Challenge in the Choking Ground on the Xbox 360 game Darksiders. Meet the requirements of each portal to free the Tormented Gate so that you may proceed.

Luka will need to fend for himself in this level on the Xbox 360 game Bayonetta. In Chapter 15 - A Tower to Truth, stay close. In verse one, when you start you'll see two statues of Fearlesses (dog-like creatures). Attack these statues and they'll come alive and attack you. For more info, watch the whole gameplay.

Complete 10 verses in this level for the Xbox 360 game Bayonetta. In Chapter 12 - The Broken Sky, attack the tongue. In the verse 1 fight, there are a few minor enemies to kill. There is also a creature that looks like a wind-dragon, but you can't attack him. To end the fight, just head for the exit. Before you go through, look at the cage at the bottom of the stairs. Inside you'll find an Umbran Tear of Blood. For more info, watch the whole gameplay.

Wolves in Sheep's Clothing: So, yes, that means there are more than one wolf in sheep's clothing. Hit the map marker and this mission will immediately kick off. You need to check the nearby street in front of a large, regal building to find a certain somebody. The area is marked green on your map, so don't waste time anywhere else. Just turn on eagle vision and, once you've spotted the target, a cut scene will take over.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

Boys Will Be Boys: This is the very first problem for you to solve in the video game. You're dropped into your first mission, which requires you beat up a lot of dudes. Be sure to lock onto an enemy, which allows you to throw up your guard and block incoming attacks. You've got access to a counter move that's incredibly useful if you can get the timing down. Just hold up your guard and press the attack button as an enemy swings on you to put him down instantly. For more info, watch the whole ...

You'll find yourself in Kadessa and Deningrad in this installment of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are exploring Kadessa, they fight and defeat the Grand Jewel for possession over the Dragon Block Staff, the party leaves Kadessa just as the Divine Dragon is launching an attack upon Deningrad, the Winglies try to teleport the party to Deningrad but they are too late to stop the attack, the party rush to the castle and make s...

Africanized honeybees, also called killer bees, can be far more aggressive than other types. Here's how to survive when they're on the rampage.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the blood, diabetes, and high blood pressure.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

If there ever was a day to eat green candy, St. Patrick's Day would be it. But is there something better than the banality of green candy swarming the streets on St. Patty's Day? Yes—glowing green candy, and Instructables user BrittLiv wants us to show you how it's done.

The newest trend in couture? It's called 'trashion' - high fashion using trashy things. And we mean trashy! This tutorial shows you how to make a ball gown using trash bags, duct tape and newspapers. You'll also want a dressmaker's dummy to construct your dress around - or at least a model who's okay with standing still for a long period of time. Use the trash bags to form the dress, and then attack the newspapers over it layer by layer. You're ready for your debut!

It's called the AUDynamicProcessor, and it's very helpful when it comes to mastering your songs in GarageBand. In this video tutorial, you'll learn how to utilize and manipulate the sound dynamics of your songs in GarageBand using the AUDynamicProcessor filter, which effects the high and low ends of audio.

In this tutorial, we learn how to get the Phoenix achievement in Soul Calibur IV. To do this, you will need to win with all your equipment destroyed. Hit high and do low attacks to help you get the advantage. Don't fight and just stand there until all your equipment is gone. Go to the Tower of Lost Souls and do this on Floor 11 to help you get this achievement more easily. After the opponent knocks off your equipment, you will be able to start fighting and hurting the other person until they ...

In this video, we learn how to do Andres Iniesta's signature soccer move La Croqueta. First, while you are on the field and have the ball, you need to turn and control it. Pay attention to those around you and move around them. Move the ball from left to right around the people coming towards you. Attack the open space to free yourself up and get away from crowds of the opponents. Once you do this, you will be close to the goal. Finish off the shot by kicking the ball into the goal. From here...

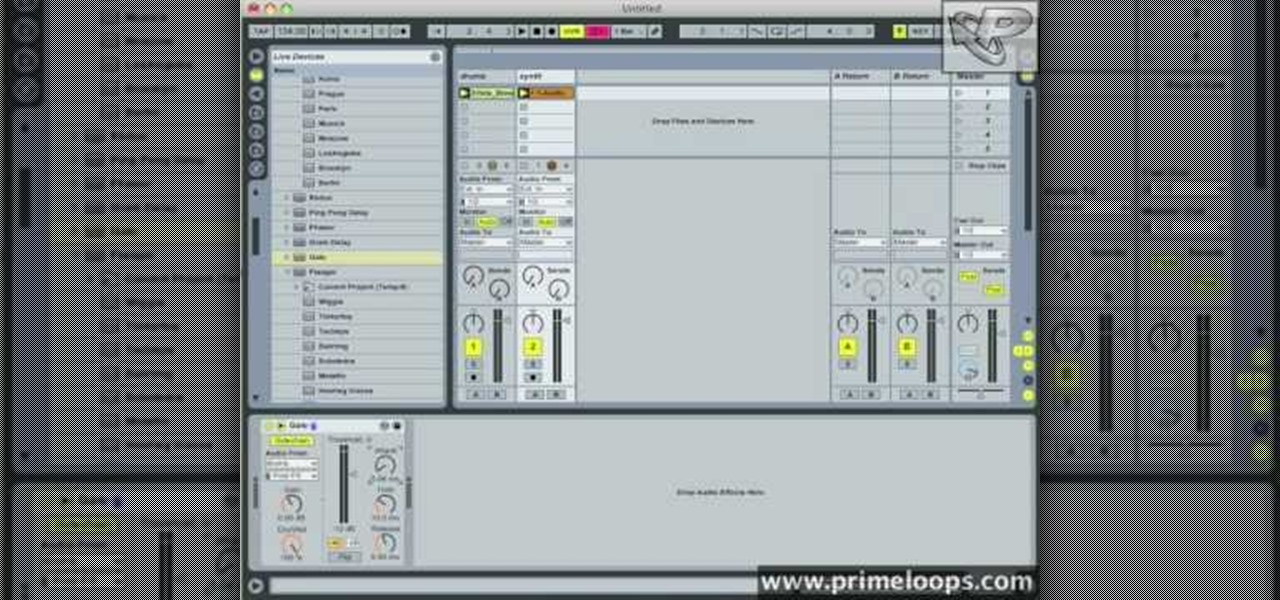
In this video, we learn how to use a sidechain gate on synths & drums in Ableton. First, drag a gate device onto your synth track. This will turn down the volume of the synthesizer device very quickly. Once you do this, you will have a sidechain view, turn it on by clicking the green button. Then, bring the attack down to 0 ms and bring your hold down to 3.9 ms. When this plays, you will hear an electronica type of beat. This is a simple way to make your synth lines more exciting. Save this w...

When in repose upon the toilet, the last thing most people want is for something to jump out at them. And that is exactly what will happen to them if you pull this prank. It turns out that the actual tape from a tape measure is a great little prank tool, and in this video you'll learn how to attach one to a roll of toilet paper so that when your victim attempts to wipe, they will be attacked by tape and scared... witless. Yes, witless.

Fries are such a killer food. They're beloved as the favorite "vegetable" of kids and adults everywhere, yet they are one of the absolute worst foods you can eat if you want to, you know, live past 40, containing high levels of saturated and trans fats that clog your arteries and lead to lots of gnarly diseases.

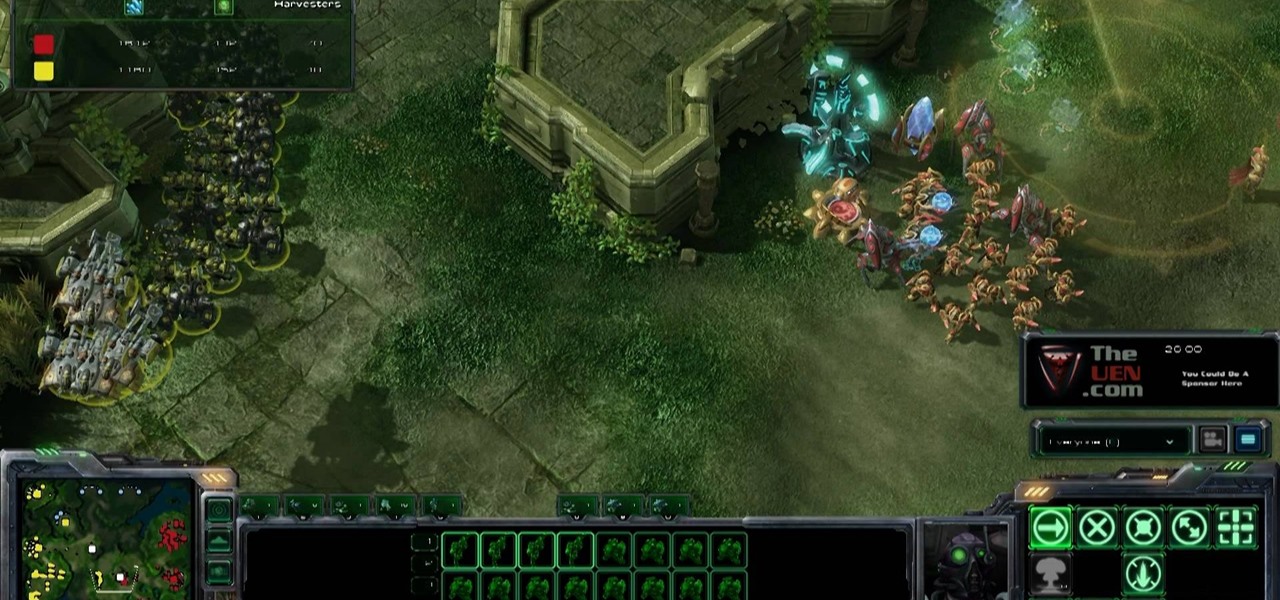
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to use the Protoss High Templar's Psionic Storm ability most effecti...

In this video, we learn how to defeat Aster Protoflorian in Final fantasy XIII. First, activate the aerosol to make yourself stronger. Now, switch over to medic anytime you get hurt from the monster. Take hits where you can and use your different tools to help attack him further. Slash and burn when you can, then use double doses. Libra him when you get a chance, then Libra him again and he will turn red. Now he will have different weaknesses, so watch out for these. The best way to defeat hi...

This video makes suggestions in how to choose colorful flowers and shrubs in your garden. Bowle’s Mauve is a purple flowering plant that will grow and bloom until fall. It will become bushy. Another colorful choice is the Rock Rose, a pinkish flower. The Blue Salvia has blue flowers. A Bank’s Rose, only bloom for a short time. It has yellow or white flowers. Aphids tend to attack it, but it is hearty.

No need to make a bad situation worse when running into an ex boyfriend or girlfriend. There is no need to be petty or spiteful when keeping to a nice yet vague conversation will ultimately leave you looking like a real class act.

This video is demonstrated completely through visual movement and accompanied with a brief written description. A young man speeds down the soccer field with a ball and scores a goal. His signature move leading up to the goal is broken down into very specific methods of movement, the first of which is a high speed attack as he races down the field. The next method to this signature move is the weight shift, in which the goal scorer shifts his weight, along with the ball, from foot to foot to ...

This video shows how to do audio side chain compression to improve your production audio mix. Side chain compression is an easy way to balance the base and the drums. Using a compressor, you can cause your base to drop in volume when the drums are hitting so that one is not over-powering the other. This video walks you through step by step instructions for configuring your compressor to balance based on threshold level, the attack time, and release time. This is an excellent source of audio p...