
News: Daring Man Carves Thrifty Engagement Ring Out of Meteorite
When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.


When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

Reddit announced this morning, April 7th, that it has finally released an official mobile app. You can get it on Android and iOS.

This tutorial is quite an epic, so get a cuppa, kick off your slippers, sit back and relax as we go through a few great inking & blending techniques.
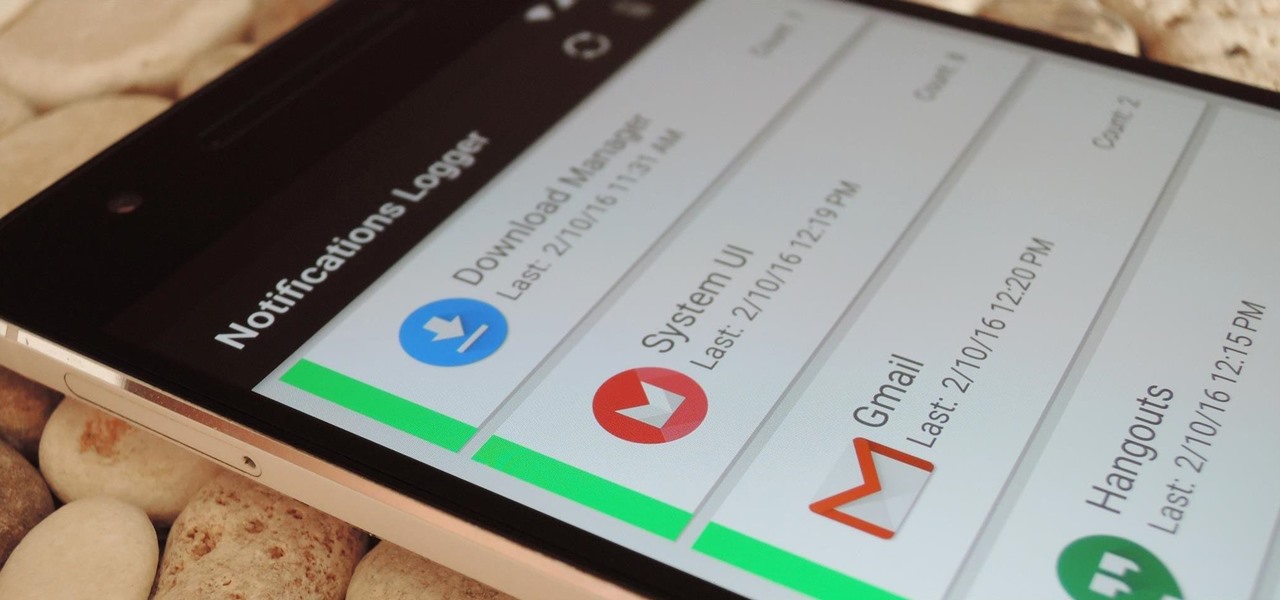
If you've ever prematurely dismissed all of your push notifications before you got a chance to read each one, you know how annoying it can be to dig through all of your apps to try and find the one with the missed notification.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Learn how to remove blackheads from nose and face, naturally at home! Video: .

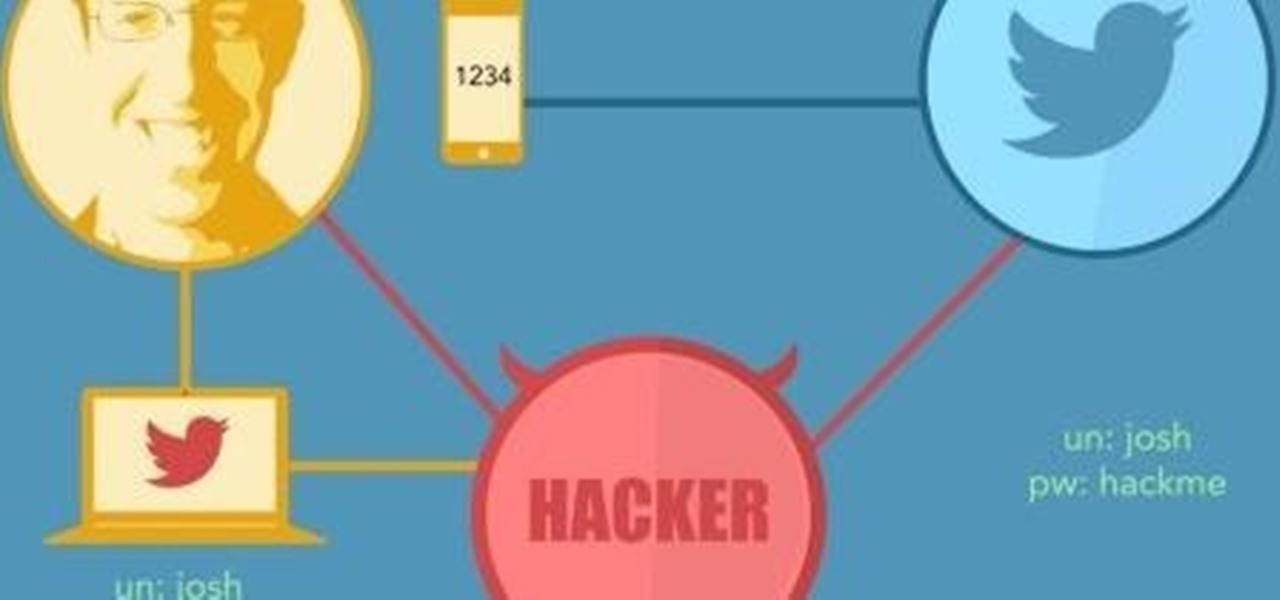
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."
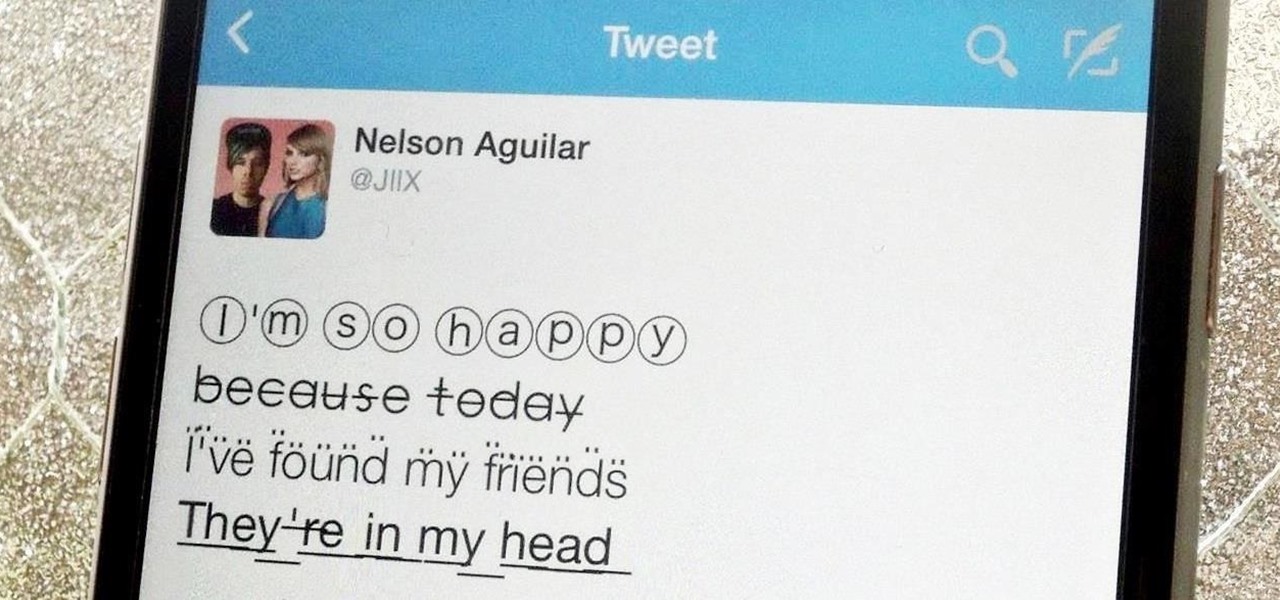
Aside from media, there's not a whole lot you can do in 140 characters to make your tweets stand out. You can use emojis, but they aren't exactly ground-breaking. However, now you can use Bedazzle, a Chrome extension from Gordon Zheng that'll allow you to add "rich text" to your tweets.

The bumper for bObsweep Pethair and Standard are installed the same way. It holds the sensors that allow Bob to see any obstacles in his path. If a repair of the wall detection sensors is needed, the steps for replacing the whole bumper are the same when working on either bObsweep model.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!
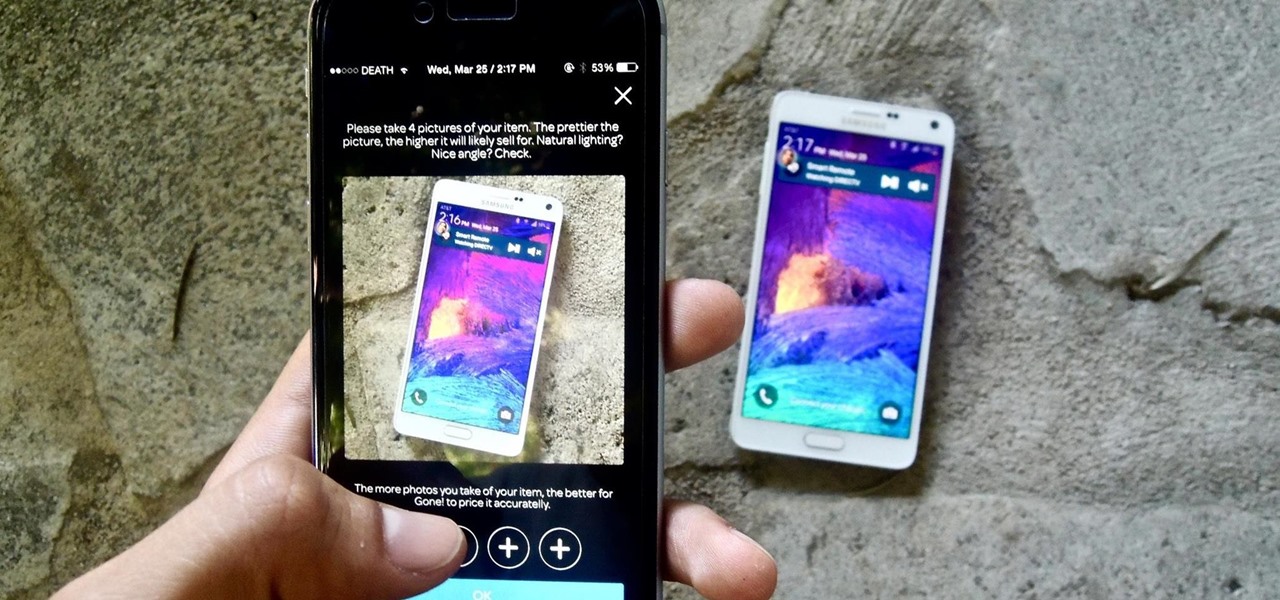
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

The next time you finish that last pickle spear, don't pour the leftover green juice down the drain. You can use your leftover pickle juice in cooking, in cocktails, and as a post-workout performance shot.

AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.

This post is brought to you by TOMCAT. Video: .
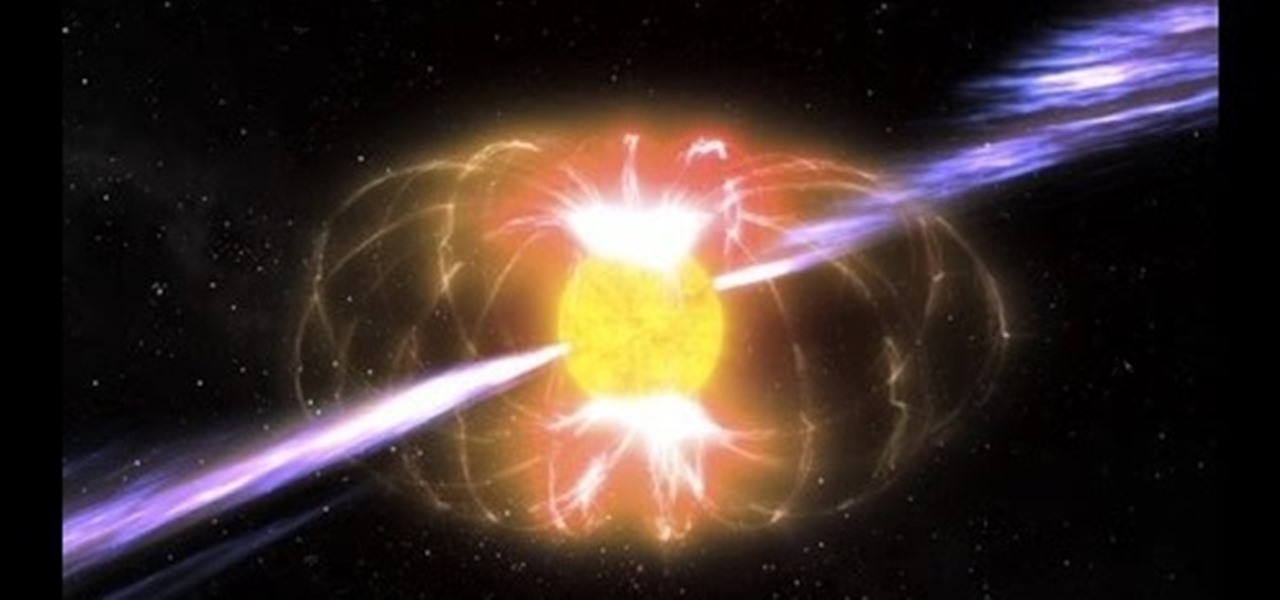
There is many different types of stars in the universe. Majority of them are red dwarf stars. However, there are plenty of stars like ordinary stars (like our sun), red giants, blue stars and etc. Furthermore, when you look in the night sky, we see a lot of small and bright stars. What people don't know is that there are stars that are not even completely understood by astronomers and scientists.

This post is brought to you by the Smithsonian Channel. Video: .

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.
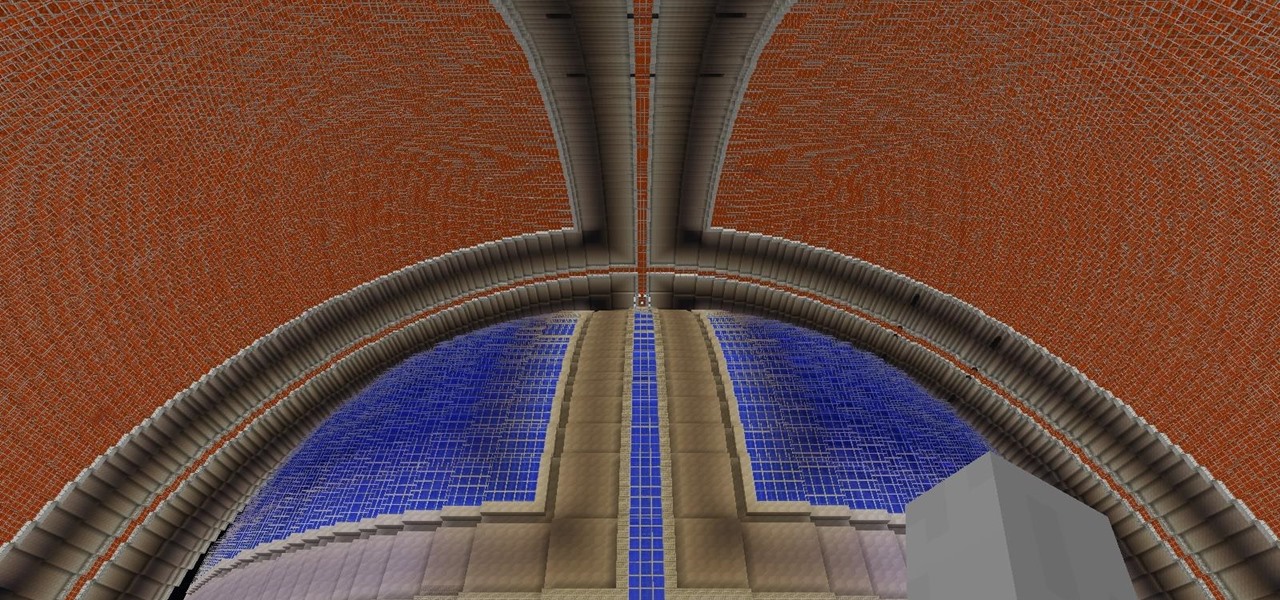
Still working on mega project builds. This one is going into my own PVP server which (will) contain 4 theme'd biomes inside of a 155m sphere - inside of a 255 meter containment sphere inside a 1000m+ void. The outer sphere acts as both artificial sunlight and a drop-death height of 50m. 4 more outer panels to go (water and lava) and it's ready for interior work and redstone - including command-block powered proximity traps that don't have any triggers marking them as well as hidden walls that...

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.
If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

I had such a hard time making black beans until I met the slow cooker. With this magic device I was able to make the deliciousness I was after. In this post I look to show you how to make black beans perfect every time

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Red Bull has a rich history of supporting athletes and artists achieve their goals, whether that's breaking a rebound record or getting back into painting. Ever wonder how to capture the inspiration that these star athletes and artists have?

This is for all you vegans out there who crave the taste of key lime pie more than Dexter. Traditionally key lime pie is not vegan, so in this inventive recipe I've made it vegan and you won't believe what makes it green!

Although mowing is key to keeping your lawn healthy and good looking, it isn't anything worth jumping up and down for when it comes time to doing it. As it turned out, the first time I mowed my lawn wasn't nearly as fun or exciting as Hank Hill made it out to be. Maybe it was the beer.

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

First of all I am glad that I was able to find this website and become part of it. So far I love it. Recently Playstation created a competition where a person has to show how online gaming is good. Pretty simple right? You can enter with an image or a video, however I do not think that an image can really show the fun of online gaming. I have created a video which does show some of the good parts of online gaming and I also tried to keep it fun. I would really appreciate if you would have a l...

The following video will demonstrate a simple process by which hard-boiled eggs can be scrambled prior to cooking, creating a deliciously blended center once finished.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.