UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

Gotta catch 'em all, right? That's easier said than done, considering that Pokémon GO has region-specific characters that you may never get a chance to see. Sure, you can spoof your GPS location to make the augmented reality game think you're at a different spot on the map, but Niantic Labs seems to be catching on to this method, and some users have been soft-banned for a few hours after trying it.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Welcome to Minecraft World! Check out our tutorials, post to the Inspiration board, and come play on our free server! HELLO, FELLOW MINECRAFTERS. Pmaguire here, bringing you my favorite idea for a competition so far! I hope that you will come to love it as much as I do! Well, starting off, as the title states, this week's Redstone Competition will be PvP Arenas! Except, not just ones where you physically fight. You have to have traps, things that make it hard to fight, and various ideas using...

The AutoCorrect feature in Microsoft Word is a very nice feature to prevent from making spelling mistakes, but how about having this very useful Auto Correct feature in any application, not just Word or Outlook. PhraseExpress can do that, and it can even import your existing entries from Word for use in any program. Learn how to use the PhraseExpress software to export your Word AutoCorrect and AutoText entries for use on other computers and in any other application.

We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

How do you amp up your current cardio/strength training routine to make sure you burn extra calories and shed extra fat? By jumping. Though jumping sounds easy, after you try this routine and repeat it a few times we'd be surprised if you weren't completely winded and sweaty. Do these exercises after your usual routine to really kick things up:

LeBron is a threat, no matter what the defense throws at him. See how he uses the art of deception to find a way to score even when he's not shooting. First ask for the ball. Second make a move to draw the 2nd defender. Third pass the ball to the open man.

This will show you how to do the Lebron James Signature Move from Nike series on NBA superstars bball skills.

Projectors can be pretty pricey. 1080p projectors even worse. If that isn't reason enough for you to build your own, then what is? Systm shows you the complete, detailed process of building your own 1080p HD projector, so pay attention and take some notes!

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

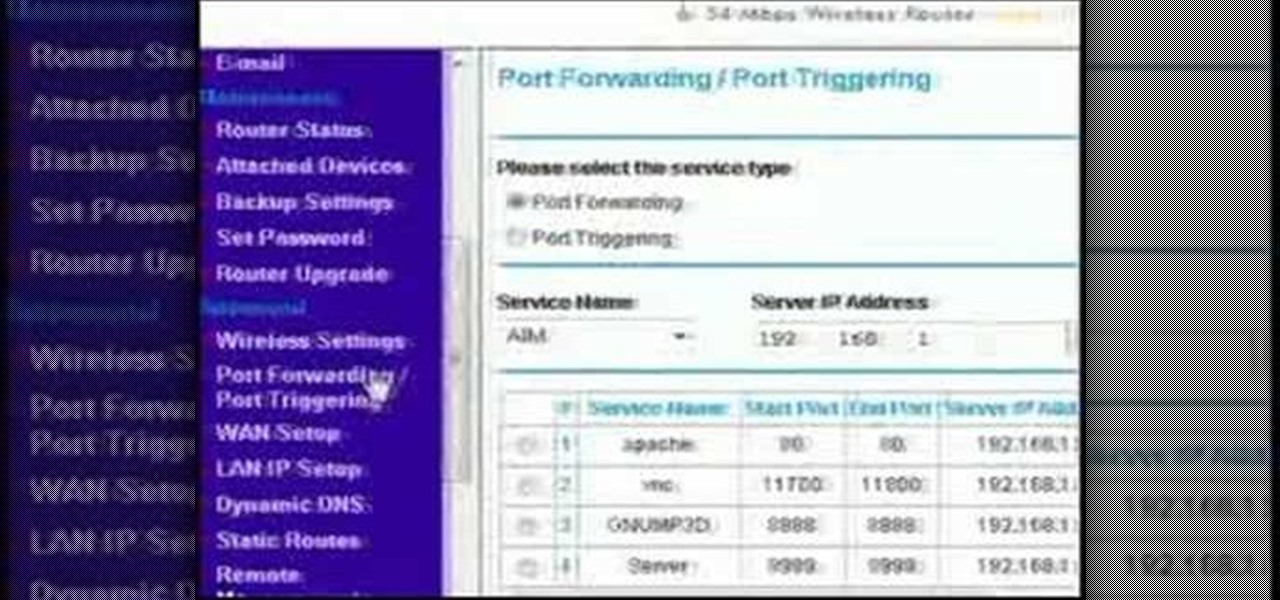
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

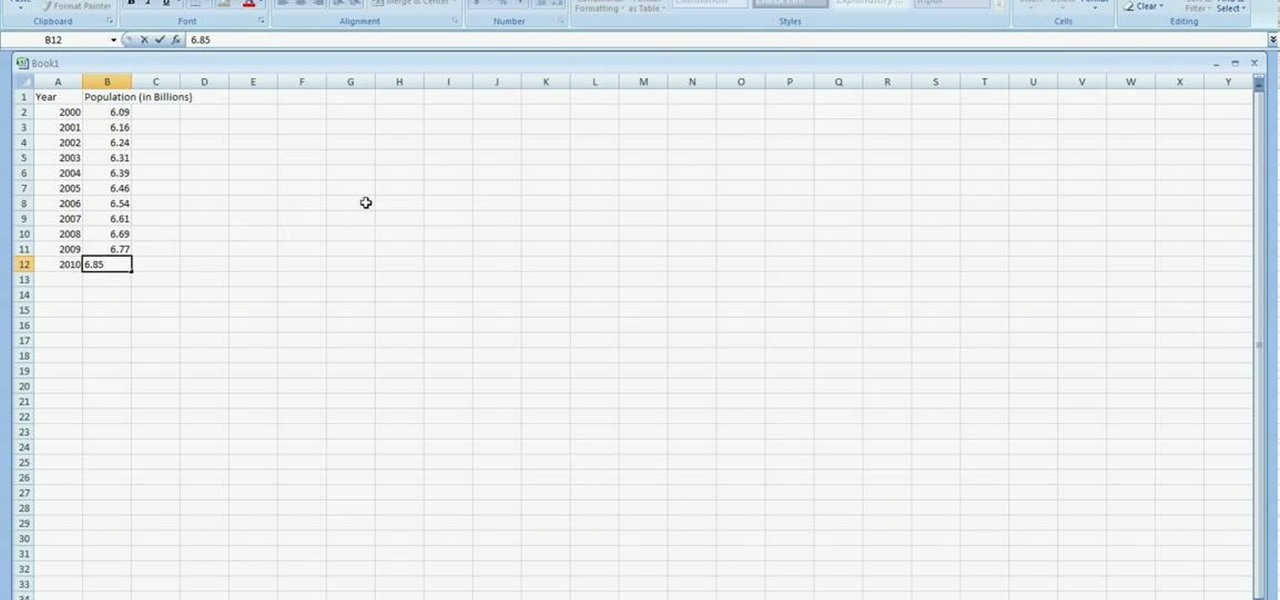
In excel a left click is made on box A1 and the X title is typed in as year. In A2 the year 2001 is typed and in A3 the year 2002. Both A2 and 3 boxes are highlighted and the bottom right hand corner is used to drag the work into a copied sequence down to A12. In B1 "population in billions" is typed. From the web site the data is copied and typed in as it appeared and the numbers are rounded off. A click is made on the "insert" tab and line is selected from the menu which appears. The upper l...

In this six-part video tutorial, learn how to create an access database. The following six parts go over the following:

You can block artists no matter where you are in Spotify's mobile app for Android or iOS, but it's not as easy when you want to hide songs from playing. Disliking tracks is possible here and there, but not everywhere, and that's a serious problem if you keep hearing songs you hate.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

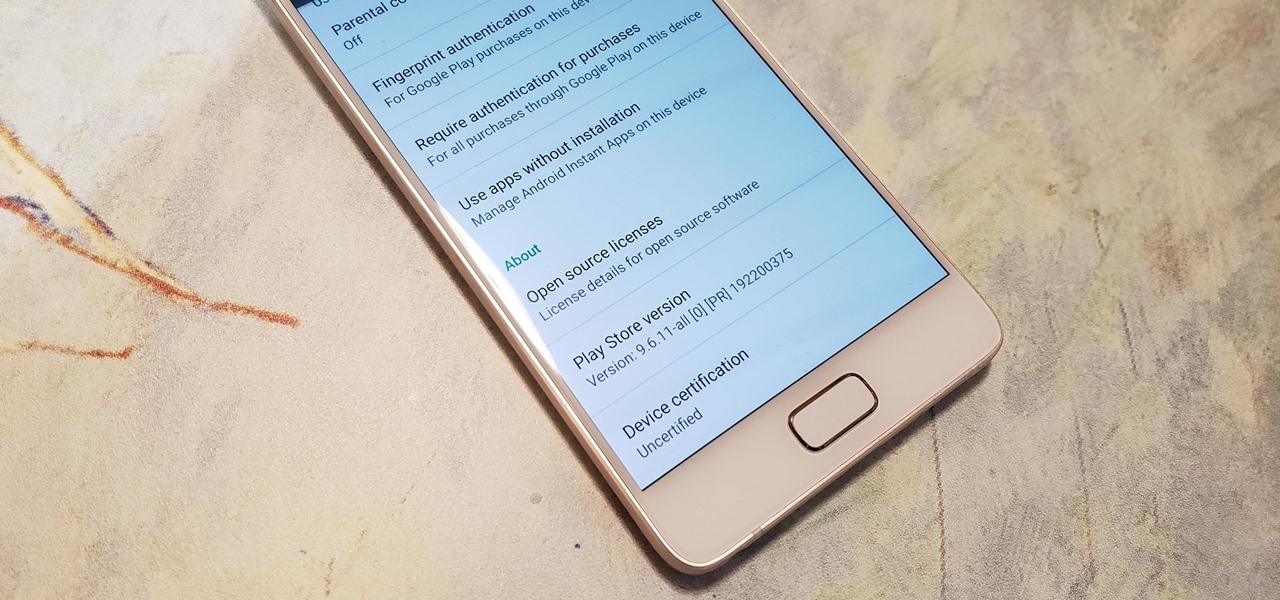
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

An advance in the race to stop birth defects caused by Zika-infected mothers has been made by a team of researchers from Rensselaer Polytechnic Institute in Troy, New York. They have identified the process Zika uses to gain entry into the placenta, and published their findings in the journal Biochemistry.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Multitasking has always been one of Android's strengths relative to other mobile operating systems. As the first cell phone OS with "true" multitasking, Android's been ahead of the game in this department for quite some time.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

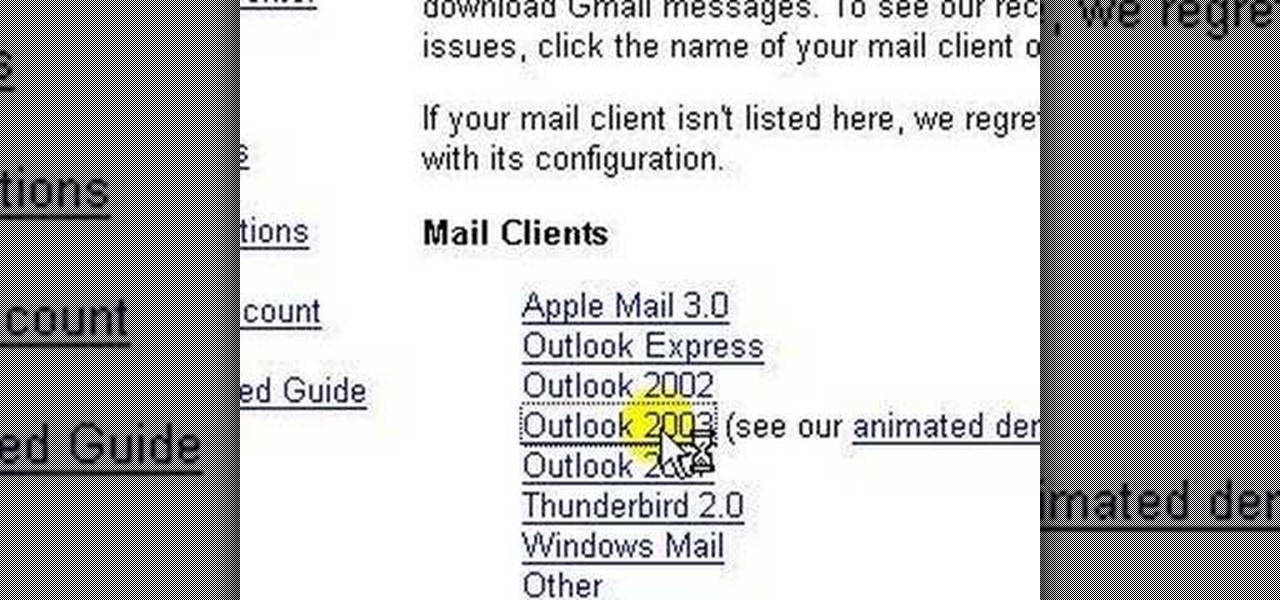
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

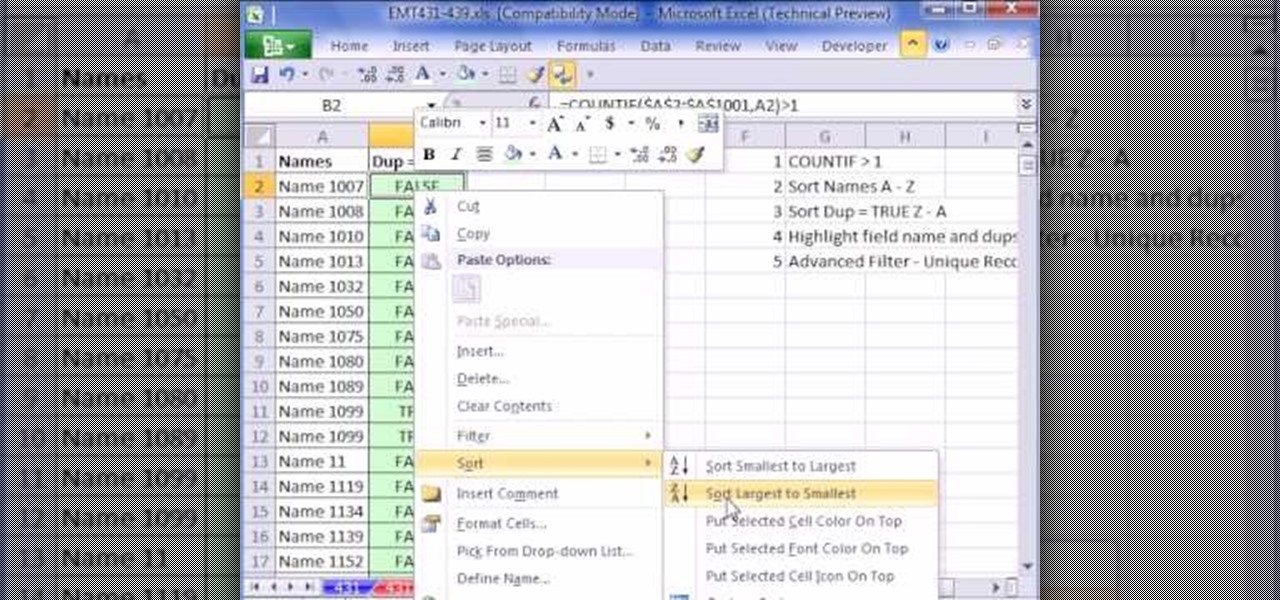
This video is about finding duplicate entries in excel sheet. The example excel sheet contains different names. There are around 1000 different names in the sample excel sheet. CountIf(range,criteria) formula has been used to do the comparison and return of results in True or False mode. Type =CountIf( now move your left arrow key, this will generate the formula like =CountIf(A2. Now press Ctrl+Shift+Down arrow, this will select all the available values in the column. Now press F4 to lock it ...

In this video Andrea Osterkorn demonstrates how to stage your home for sale. It is not a comfortable process to transform your home into a home for sale. The entry way should be inviting because first impressions are important. Closets should be cleaned out. Consider renting different furniture for the living area to make it more open and inviting, and move it around to create an impression of space. Add accessories and let natural light in. Try to depersonalize the room and remove clutter so...

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...