Lemons and limes might be among the most useful fruits in the kitchen and even beyond. Their bright, tart flavor livens up just about any dish, while their mildly acidic nature makes them incredibly useful when you want to clean your house safely. We already knew lemons were great for keeping fruits and vegetables from turning brown, deodorizing garbage disposals, disinfecting cutting boards, and neutralizing odors. But just when we thought we knew all the ways that lemons can be used around ...

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Hard as it is to imagine, there are people out there who loathe garlic and onions. Some might have allergies or medical conditions like IBS, or are supertasters (i.e. people who carry a certain gene that makes them extremely sensitive to how certain foods taste). Others might just be picky eaters.

The new LG G3 is the latest Android flagship-level device to be released this year, and it's ready to give the Galaxy S5, HTC One M8, and the OnePlus One a run for their money. Sporting a gorgeous 5.5-inch QHD display, 3GB of RAM, and a huge 300mAH battery, the device looks great and has tons of power to boot.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

The camera situation on the all new HTC One is a little daunting. The M8 has not one, not two, but three camera lenses built in. First, there's the 5 megapixel selfie machine up front, then around back, there's the new Duo Camera with a refined UltraPixel sensor. HTC has done things differently here, and the UltraPixels and dual lenses means that the M8 doesn't necessarily take pictures like you'd expect—and that's not a bad thing. With a little guidance and some easy tricks, you can use all ...

The point of ice in your cocktail is to make it cold, right? Yes and no.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Becoming someone else for Halloween is a lot of fun, but it can take a ton of tools to accomplish. An elaborate costume can require you to slather yourself in all kinds of makeup, paints, and glues, and putting it on is only half the work. The real fun starts when the party's over, and you have to remove it all.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

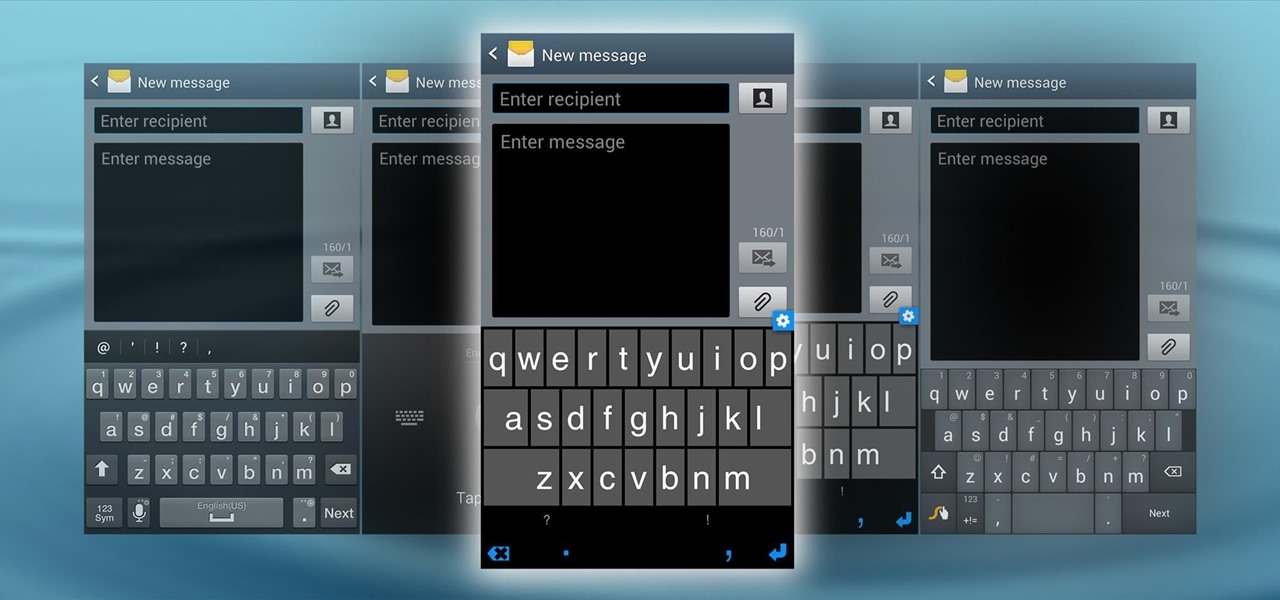
The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

What happens when you find your ball deflated and there's no pump or needle in sight? You could always cancel your plans of kicking around the soccer ball or starting that pickup football game in the park. Better yet, you could be terribly clever and find another way to get air into the ball. From a pen to a balloon to a gas station, there are ways to inflate it.

Why can't I see who is stalking my Facebook profile?

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

If you're a Steampunk (or costumer of any variety) and you don't know what Rub 'n Buff is, this tutorial will make your life so much easier. You have no idea.

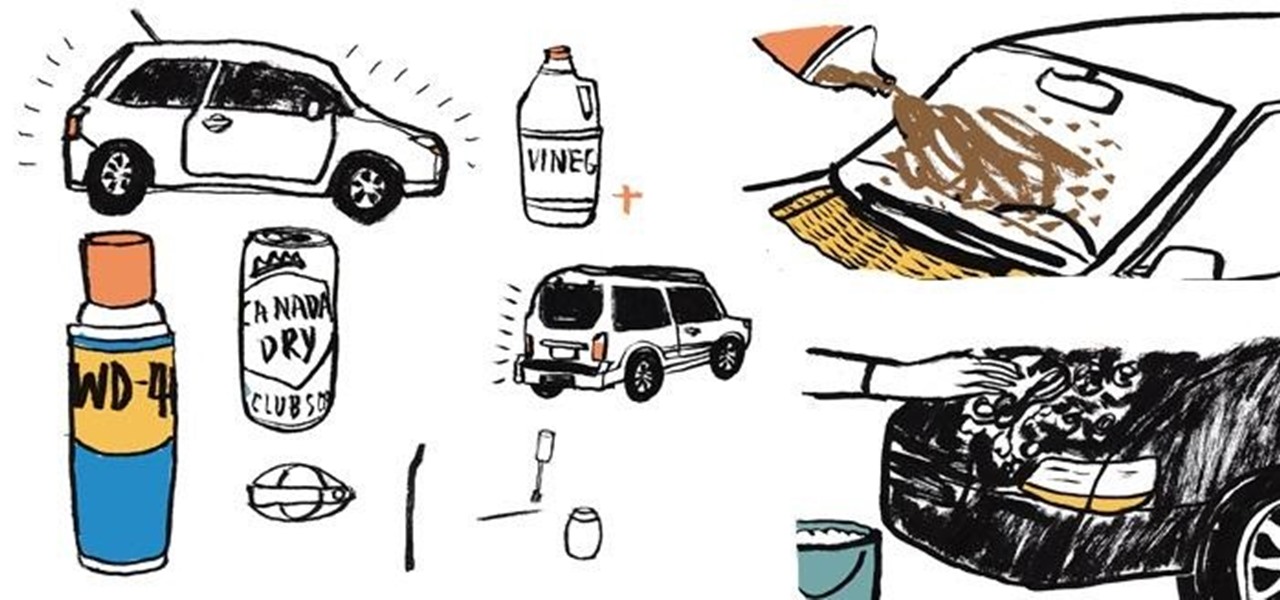
Ever see those cars so covered in dirt, dust, and grime that someone writes "Wash me" on it using their finger? Well, for those cars' sakes, as well as cases less extreme, a word of advice: procrastination is not a solution — it can only compound the problem. Self-cleaning cars are the stuff of the future, not the present, and your car needs attention now.

Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go anywhere you want. But like most tablets, the Surface comes with a rather limited amount of storage space. The tablet comes in either 32 GB or 64 GB, but we all know that's not the actual amount of storage space you can...

As you know, it's impossible to be a Steampunk without a pair of goggles. In fact, there are entire communities dedicated to judging other Steampunks based solely on their goggles. A Steampunk without goggles is like Samson without his hair, or a duck without a beak—totally powerless. As I'm sure you also know, the right pair of goggles can instantly render any outfit Steampunk, no matter what it looks like.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

I chose to make this a Steampunk iPad case, but you can change the details and make it look as modern as you'd like. As I said earlier, Steampunks probably shouldn't buy iPhones or iPads, but if you're going to get one, you may as well make it look cool, right? The iPad pictured below was borrowed from a friend of mine, though I should add that this design will easily work with tablet computers of any variety, Apple, Android, or otherwise.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

I'm constantly searching for a homemade pizza dough that tastes good but isn't too challenging to execute. In other words, a recipe that doesn't require any arcane "dough whispering" skills. However, my hunt may be coming to an end thanks to one celebrity chef's concept.

As we move toward the end of the year, the wheels of the augmented reality space continue to shift in major ways.

Quietly, while the rest of the world was engaged in pandemic and political concerns, a few weeks ago Facebook casually upgraded its Spark AR platform with what it calls Unified Effect Publishing.

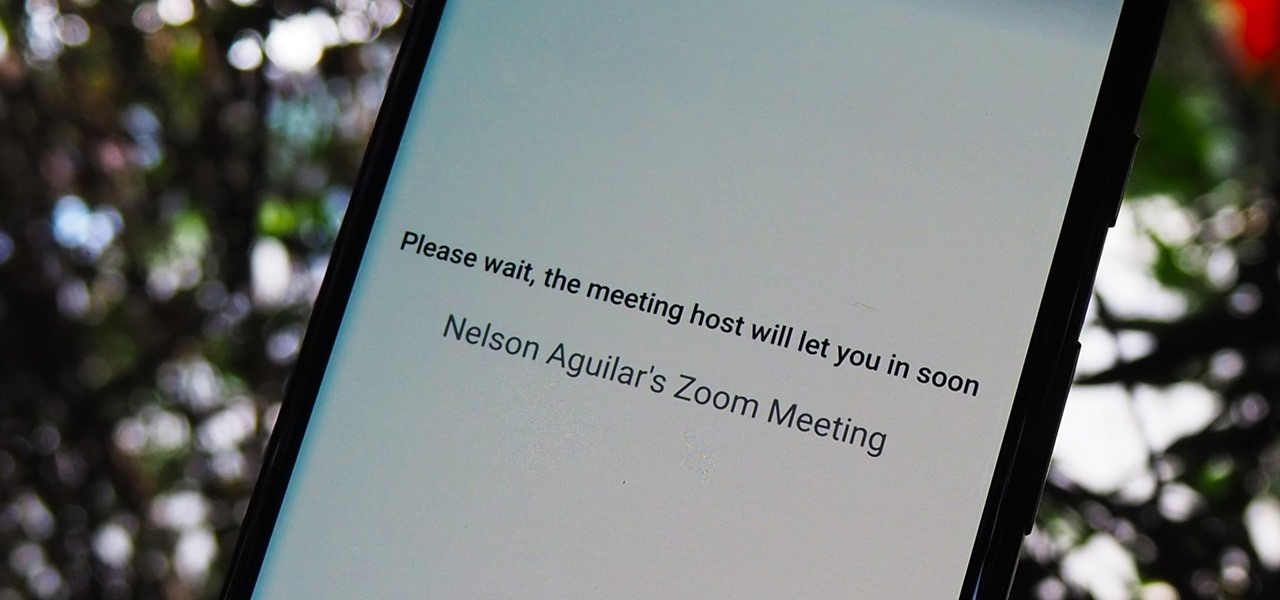
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.