If you've ever organized an event, you know how chaotic it can be. Event planners are essential, but even so, taking the time to make sure it's organized and everyone is getting what they want can be stressful. Especially when you have to account for what every person is eating at the event, what their toppings are, and how they'd like their meal cooked.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Whether you're hard of hearing, watching a foreign movie, or just like reading along when you're watching a TV show or film on your smartphone, Netflix includes captions and subtitles that you can use. Best of all, if you don't like the way the default captions and subtitles look (color, background, font, or size), Netflix has your back.

Reigns recently went on sale on the Google Play Store (sorry, iPhone users), and that inspired me to give it a go. I've wanted to try this one out for a while now, but the steep price tag kept me away. ($2.99 is a lot for me, okay?)

Facebook, you either love it or you hate it ... or maybe you're indifferent. The point is, Facebook is everywhere, and the debate is still raging over whether or not it's actually, well, good. That debate may not exist for the various personalities of Facebook much longer, however, as Facebook announced a new app geared directly towards improving how they broadcast their content to their audiences.

Researchers are putting driverless shuttles on campus next year at the University of Michigan and the rides are free for students and teachers.

Pokémon GO updates will have new deterrents for cheaters, and these seem to use shame more than just prevention. The changes were mentioned by a Pokémon GO support account on Reddit. (There are other updates coming soon to Pokémon GO as well.)

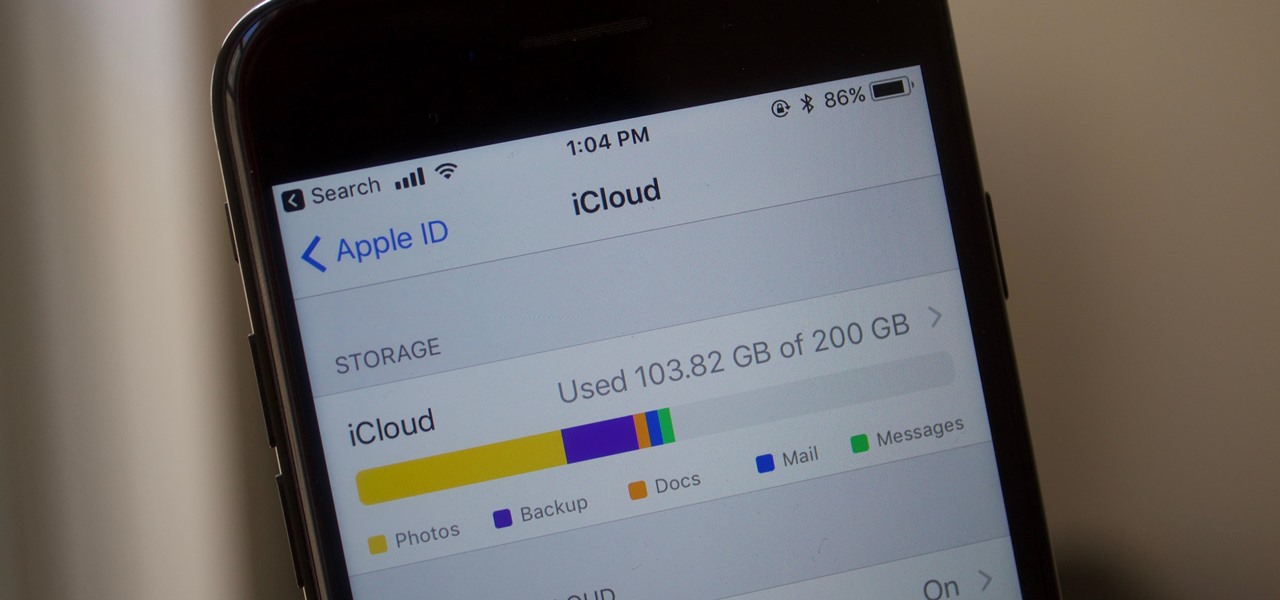
iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

If I told you to follow as many users as you could possibly follow, in order to get more Instagram followers, that may seem counterintuitive, right? If I told you I'm trying to brainwash/annoy you with how many times I could possibly say versions of the word "follow" in an opening sentence, that would seem weird, too.

Earlier this month, Edgybees was the first game developer out of the gate with an augmented reality racing game for DJI drones called Drone Prix AR. Now, as the month closes, they are crossing the finish line with the first gaming app for Epson Moverio BT-300 Drone Edition smartglasses.

In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

Online lives could be made easier now that Facebook, Instagram, and Messenger are testing merged app notifications. 'Could' being the operative word!

Over 90% of ride-or-die iPhone users will upgrade to the latest Apple smartphone, according to a recent survey. Really, though? Well, Morgan Stanley certainly seems to think so.

Updated 5/2/17: CultofMac reports analysts at Deutsche Bank are confirming the delays. The analysts believe the delays are due to "component shortages and technical challenges." This would corroborate the rumors listed below. We here at Gadget Hacks will bring you more on this story as it develops.

Apple made headlines last month when it announced it would acquire the popular application Workflow. Now, the company should be making waves again with the news that they will reimburse customers who purchased the app.

ASUS is gearing up to move its augmented and virtual reality departments into an independent startup named Glamorfy, according to a recent report from tech news site Fudzilla.

Starting today, you'll have the opportunity to save all your live Instagram videos to your phone at the end of each broadcast session. The latest update to the Instagram app now allows you to rewatch already-played broadcasts and gives you the ability to share them later on.

The Google Play Store is known for some pretty random promotions and offers, most of the time it's a free book or a discounted movie. But this time, an entire season for Game of Thrones is up for grabs. Yes, that's right, all of Season 5 of Game of Thrones is free to download, watch, or just stash in your library for later.

Google and Samsung have been leaving Apple in the dust when it comes to virtual reality gear. However, as the market grows and becomes more impossible to ignore within the tech world, Apple may be forced to play catch up. This could account for the new Apple patent that was granted today.

A new repository appeared in Microsoft's GitHub account a few months ago for a project called HoloJS. For those JavaScript developers out there that have been wanting to make HoloLens apps, this one's for you.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Facebook released a new app in November 2016 that aimed to compete directly with Snapchat, but it was only officially available in Brazil—and still is. The app, called "Flash," is so much like Snapchat that it's not even the slightest bit of a stretch to call it a clone.

Today in Los Angeles, Unity will be at the Loews Hollywood Hotel to host Unite '16, its annual developer conference. Unite is Unity's platform for showing the development community its upcoming direction and roadmap for augmented and virtual reality, game development, 3D technology, and more.

Microsoft began shipping the Development Edition of its much-anticipated HoloLens—the world's first untethered holographic computer—back in March. As the name implies, it was only available to developers (we got ours near the end of April), but Microsoft has recently opened up the program to anyone who wants one—not just developers.

Microsoft recently announced that they're producing HoloLens units fast enough to keep up with demand, which means you can acquire up to five dev kits right now—if you've got the $3,000 fee for each one.

Instagram is the world's biggest photo-sharing site, narrowly edging out competitors like Imgur and Flickr. But unlike the competition, Instagram doesn't make it easy for users to download a full-resolution copy of any of the images hosted on their servers, as the site's main intention is to keep folks coming back and using the social media aspect of it all.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

Vacuum sealers keep food fresher longer by first removing the air from plastic food preservation bags and heat sealing the bag to keep air out. They have rapidly become a popular way to keep your frozen food fresh.

If you've been debating on whether or not HTC's new virtual reality headset, the Vive, is worth the $800 price tag, then you'll be able to find out for yourself soon enough.

Hello there learners and readers! I figured I'd show you guys my problem and how I solved it, hoping that it would help people who are facing the same issue. Today, we'll be talking about the solution of

Taxi drivers and cab companies across the globe are in an uproar over Uber, and for good reason, too—you just can't compete with the low fares and ease of use that Uber brings to the table. The only downside is that the groundbreaking ride share service usually requires a smartphone—but that shouldn't be an issue anymore with one simple tip that I'll outline below.

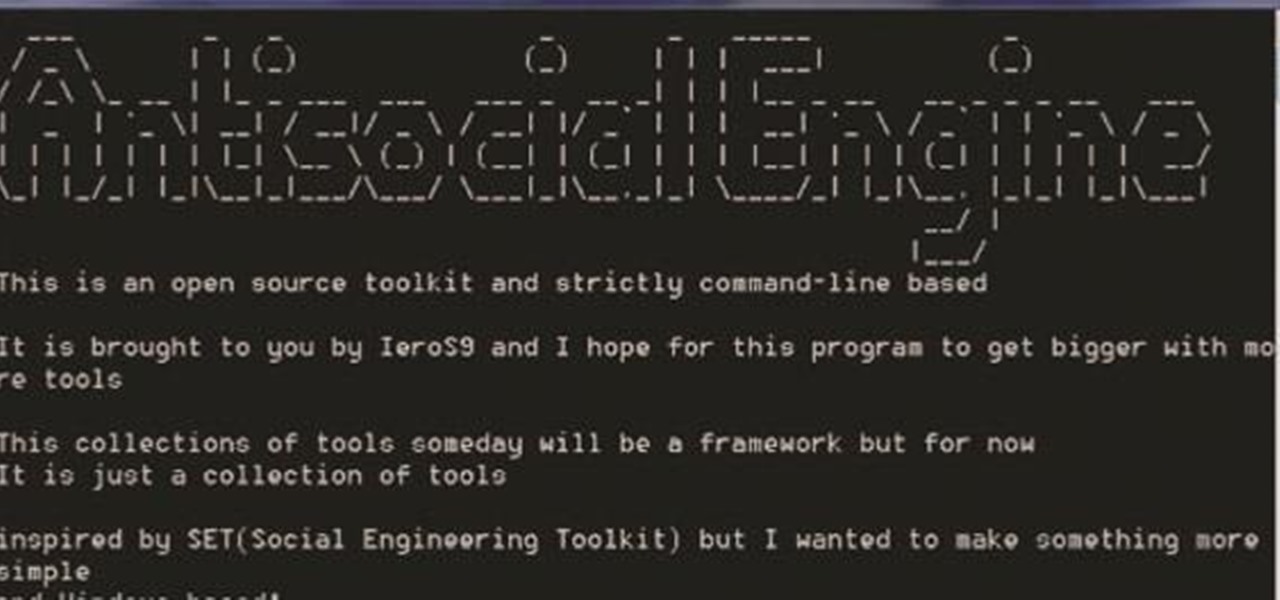
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

Well, here we are. We've come a long way, we really have. Watching this community grow has been amazing. Well, before I start babbling on about the community, let me get to the point...

Not that long ago, Google introduced a beta program for their Google Search app on Android. Much like any beta program, testers will get access to new features before they officially debut, but you might have to put up with the occasional bug as new functionality is introduced. If you'd like to sign up, it's quite simple, but I'll go over the process in detail below.

Windows 10 makes it a cinch to change the lock screen background: simply go to Setting -> Personalization -> Lock screen, then change the background to whatever you'd like. But, trying to change the login screen background—the screen where you enter your password—was a long, complicated, and possibly dangerous process. Luckily, developer Krutonium has published a tool that automates the entire process, and it's very easy to use.

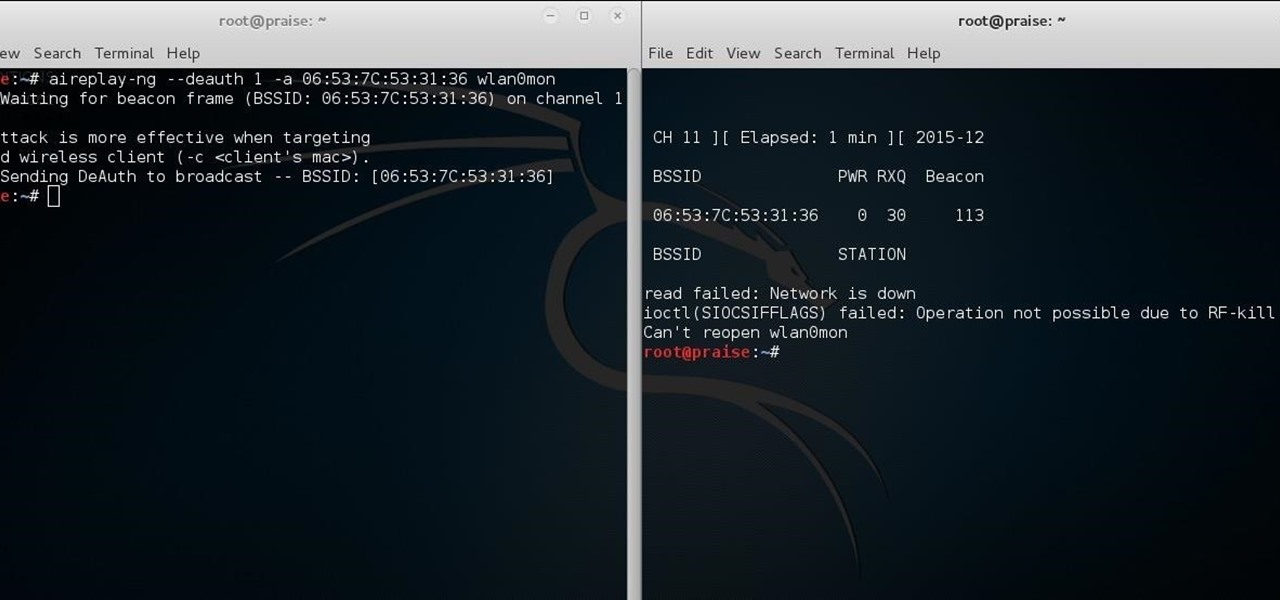
Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.

Serving as the primary tool of distribution for many websites, social media is how most of us catch up what's going on around the world. While there is a bunch of clickbait going around on Facebook and Twitter, there are plenty of genuinely interesting articles being shared.