
How To: Make Your Remote Screenshot Captor(Python)
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.


Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!
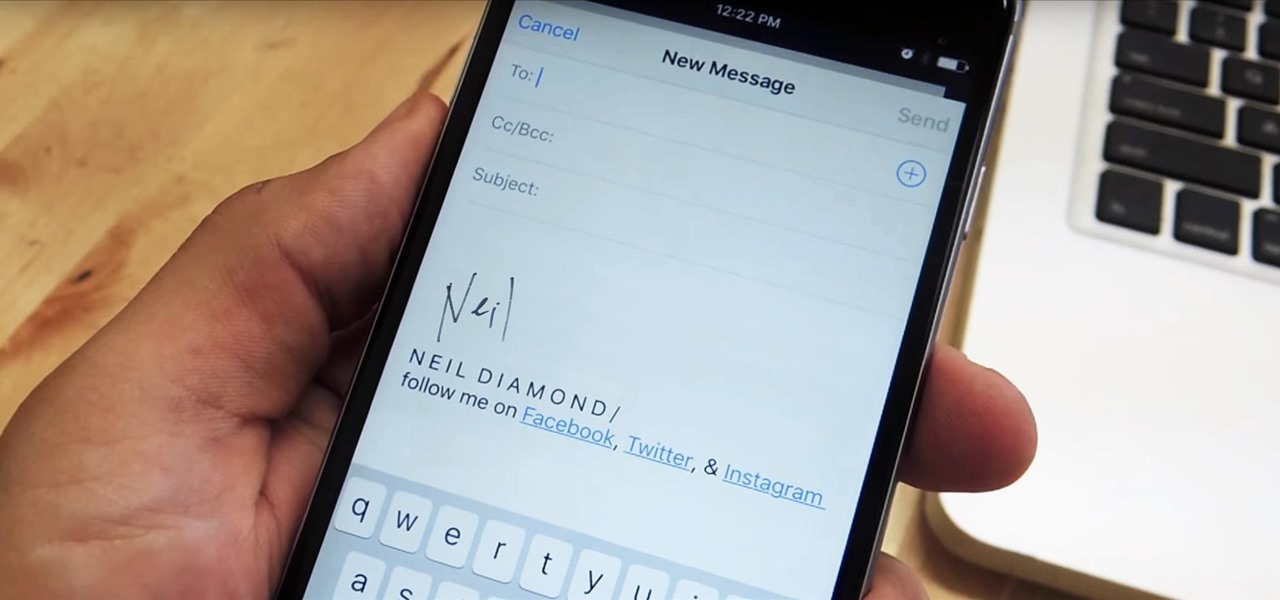
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.
The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Whenever you simplify a square root or a cube root you are writing them in the simplest form. This video teaches a factoring method.

We've all been there: facing a lengthy, complex word that ignores the phonics we were taught in elementary school, unsure of not only its pronunciation, but also its meaning. These words, from autochthonous to esquamulose, are both terrifying and impressive. After all, if someone knows how to use them—and even say them—they must be quite smart. Yet before you begin stuffing every email and presentation with verbose prose, you might want to reconsider what others perceive to be intelligent.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.
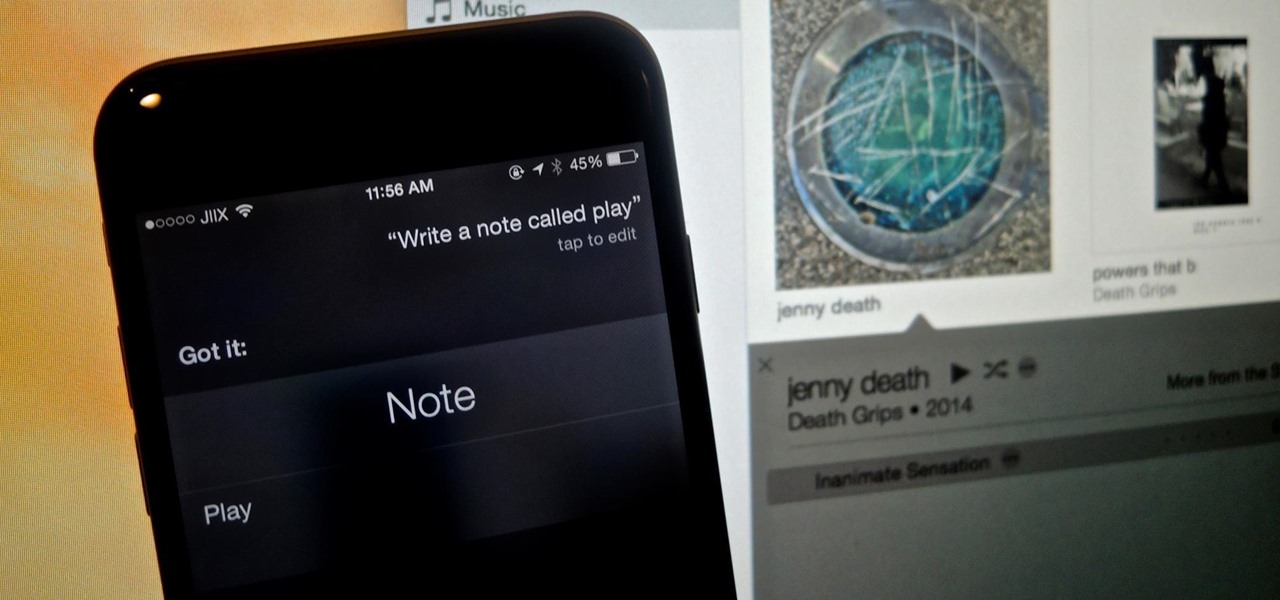
While Apple's Continuity feature has certainly impressed me, I can't help but feel like it could be used to create a better connection between my iPhone and Mac. Sure, Handoff allows me to pick up where I left off in certain applications between the two devices, and it lets me pick up calls and send text messages on my Mac, but I want even more functionality.

Android is all about customization: "Be together. Not the same," as Google's latest ads for the platform put it. Changing your device's boot animation, for instance, is one of the many great ways you can add a touch of personal flair.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

I honestly believe that everyone on earth owns the same blue cooler—you know the one. Cooler technology hasn't changed since the '50s, and frankly, it's time to mix things up, with a built-in blender perhaps? With the Coolest Cooler, it's actually possible!
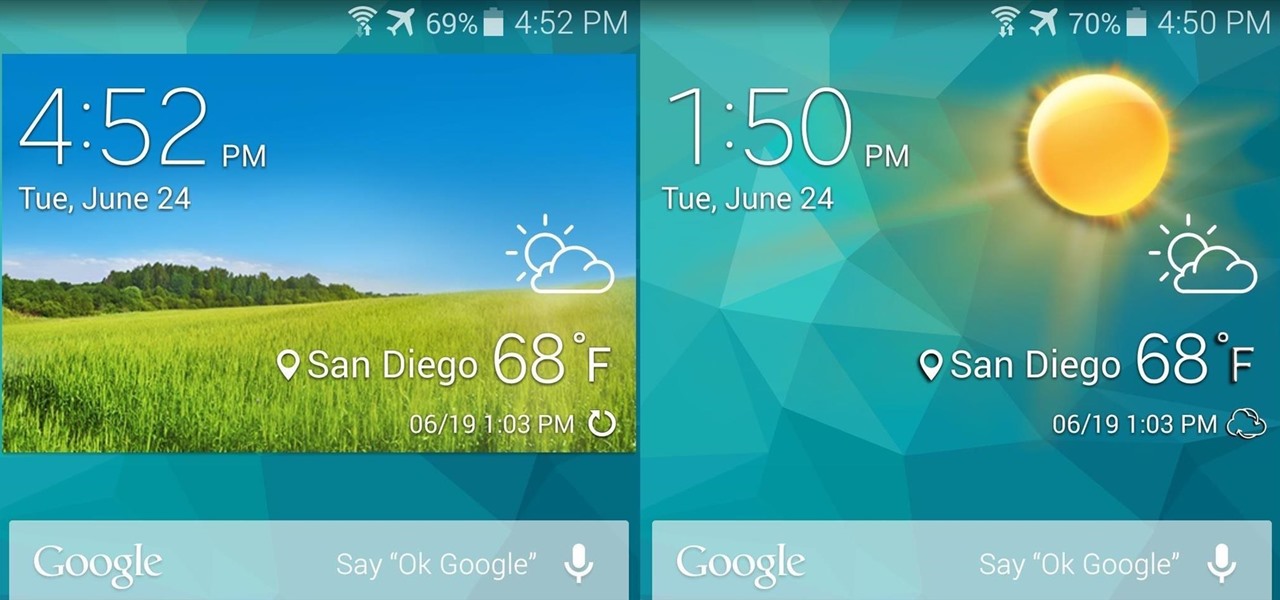
The weather widget on the main home screen of a fresh-out-of-the-box Galaxy S5 is meant to show off the screen. Super-high contrast and crisp definition on the individual blades of grass in the background let you know that the phone you're holding has one helluva display.

We recently gave you a peek at what Amazon's first smartphone will look like, and its 3D technology. With six (six!) cameras and no-touch motion control, the product is intriguing to say the least. Now, Amazon's put out a teaser video, and it's got Amazon Phone written all over it.

Hello Everyone Today in this post I will teach you how to get a banner for your terminal.(Video Available at the End of the Post) To get a banner first we need "figlet" and then we have to configure it. Its Easy ..

Here's an in-depth video on how to make a functional gauntlet with simple hand tools. You can make it with metal like the video shows, or even just cardboard if it's for a costume. You can download the template and written instructions for this gauntlet over at my website for five bucks. Otherwise, you can just watch the video to follow along—or to inspire your own version.

Need a good way to hold your iPhone up? There are a ton of smartphone stands out on the market, but they can be pricey or just downright ugly—and potentially phone damaging. But like the Une Bobine above, they do have their perks, like movability at almost any angle. But to alleviate pressure off of the connection port, Sharon Vaknin from CNET developed her own flexible iPhone stand—from an old desk lamp and suction cup.

Is "Last Resort" Steampunk? Well, no. I mean, how could it be?

This week on the Steampunk Research and Development Podcast, our guest is Joey Marsocci, better known to the world as Dr. Grymm. He's a full-time, professional Steampunk maker, and is the owner and operator of Dr. Grymm Laboratories. He's written several books and has worked as a designer at companies such as Hasbro and Disney. In fact, he worked with Disney to design the 20,000 Leagues Under the Sea attractions for both Paris and Tokyo Disney parks.

Video: . HOPEWELL, Va. (WTVR) -- A Hopewell circuit court judge has ordered that a Marine veteran detained over anti-government Facebook posts be released from a psychiatric hospital.

Even in the MP3 world, vinyl is still king among music lovers. Unfortunately, making your own record is nowhere near as simple as burning a compact disc or throwing some files onto an MP3 player. One clever inventor isn't letting that stop him though, putting together his own homemade vinyl cutter out of old parts. The end result—CD records!

Spices are a necessary ingredient in any kitchen. It doesn't matter how good of chef you are—without proper spices, your food will always fall flat.

Check out this instructional piano video that shows you how to write songs on the piano. Charlie and Siggi Mertens offer some tips to songwriting in this piano tutorial. Follow along and improve your song writing skills and compose some interesting melodies on the piano.

Need to figure out if your cd has been written on or not? Here is a quick way to be able to tell the difference between a blank cd and a cd that has been written on. Obtain the techniques to be able to tell between a dvd and an audio cd that have been written on.

Despite what we all argued in school, math does come up in daily life. When those dreaded fractions are staring you in the face remember these steps and you will be multiplying in no time. Practice always helps.
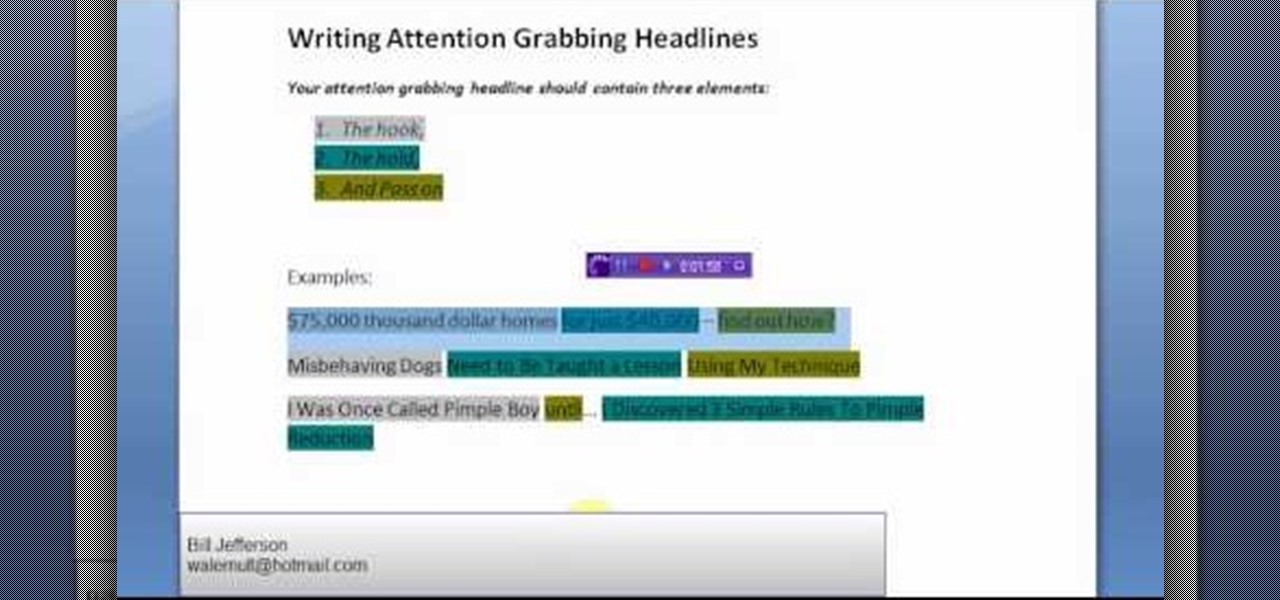
Not selling that much online these days? Maybe it's because your headlines just are reaching out to people the way they should. Good marketing means good writing in the web industry.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

Recording the tortured sounds of a guitar running through three pedals and a dirty amps worth of distortion has been the heart of rock n' roll since Jimi Hendrix at least. In this video you'll learn everything you need to know to record distorted guitar sounds yourself. It discusses mics, amps, settings, and positioning, then moves on to computer-side stuff like amp sims, EQ, double tracking, and compression. If you play rock guitar, want to record it, or both, this is a must-watch.

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

Magic. Does it really exist? Can you really put a hex on somebody… or a love spell? Can you really cast supernatural spells? Believing is up to you, but anyone can be bewitching with the help of a little black — and white — magic.
Word 2008 for Mac is jam-packed with tons of cool and useful features and tools that you can use to make a great looking document. Starting with the pre-made templates is the best way to go, and from there, customize it the best you can, anyway you can. The Microsoft Office for Mac team shows you all the great features in this how-to video.

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...

As a doctor, sometimes it will be necessary to perform a neurological examination of your patient to rule out any neurological disorders. Your objective is to identify abnormalities in the nervous system, to differentiate peripheral from central nervous system lesions, and to establish internal consistency. This is a great video less that outlines the complete neurological exam procedure. It's great for medical students or doctors, and even nursing students can learn a thing or two.