
How To: Create an iPhone ringtone in GarageBand '09
Check out this informative video tutorial from Apple on how to create an iPhone ringtone in GarageBand '09.


Check out this informative video tutorial from Apple on how to create an iPhone ringtone in GarageBand '09.
Check out this informative video tutorial from Apple on how to create a podcast in GarageBand '09.

If you have ever wondered about the functionality of slating during a film shoot, what a shooting script or line script is and how to keep a shot log, then this may be the perfect video tutorial for you, in two parts.

Watch to learn how to count from zero to one hundred in French. Includes written-out words. Part 1 of 10 - How to Say the numbers from 0 to 100 in French.

This video will teach you how to write and pronounce various Chinese numbers.

This video will teach you how you can write and pronounce the Chinese word for "courage", yong qi.

This video will show you how you can write and pronounce the Chinese word for "Landscape", shan shui.

This video will show you how you can write and pronounce the Chinese word for "nature", or "made from heavenly nature", "Tian ran".

This video will teach you how you can write and pronounce the Chinese word for "spring", chun.

This video will show you how you can write and pronounce the Chinese phrase "Get well", or "an kang".

This video will show you how you can write and pronounce the Chinese word for Autumn, qiu.

This video will teach you how you can write and pronounce the Chinese word for winter, dong.

This Chinese video will teach you how to write the Chinese word for patience, nai xin.

This Chinese language video will teach you how to say and write the different Chinese characters used for location.

Watch to learn how to correctly use Stampin Write markers.

The samurai were half warrior half artist. Learn the first character of the word "aikido" and some Japanese samurai history in so you too can write the name of the Japanese samurai martial art form.

To create a simple game in flash select the first frame and open the action bar where you will write "stop[];". Next you will make a start or begin button. Convert this button to a button. Then you can open the action bar and write "on(release) {gotoAndPlay(2)}". Afterward use F7 to insert a blank key frame and turn on onion skin. Next draw a path starting from the (onion skin) Begin button, make sure to draw the outer lines too, then color the area outside your path. Convert the colored area...
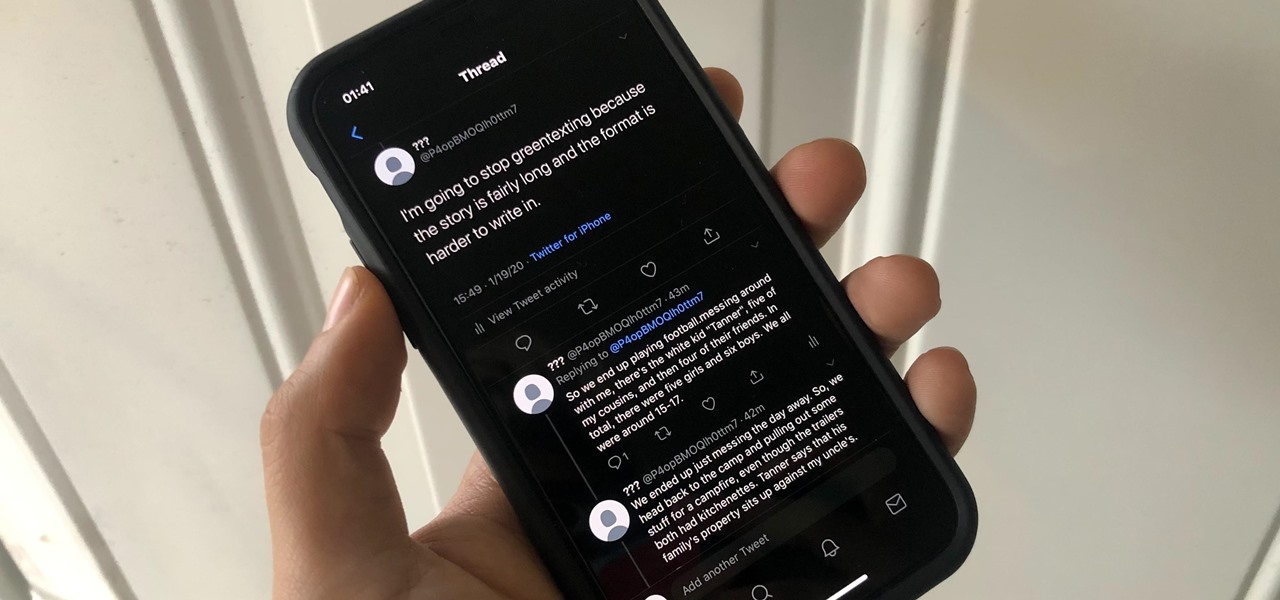
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.
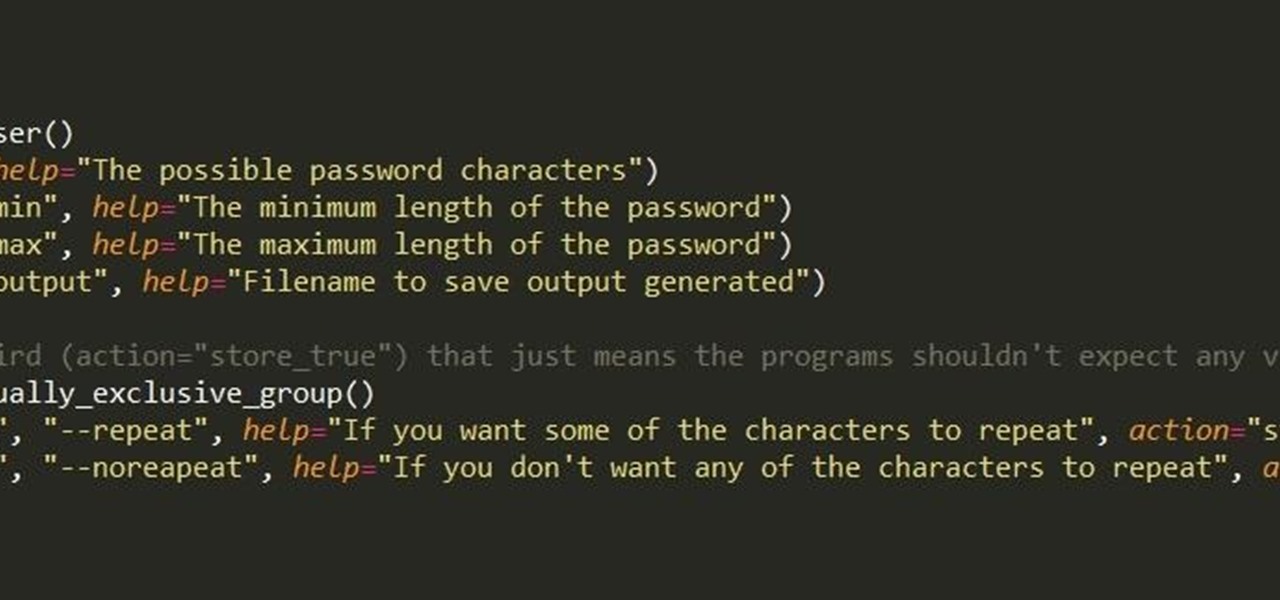
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

After you have registered to this site,sign in then to start missions. Basic Missions

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.