
How To: Turbo Ping Sweeping with Python
Why did I write this when they're tons of scanning tools available.


Why did I write this when they're tons of scanning tools available.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.
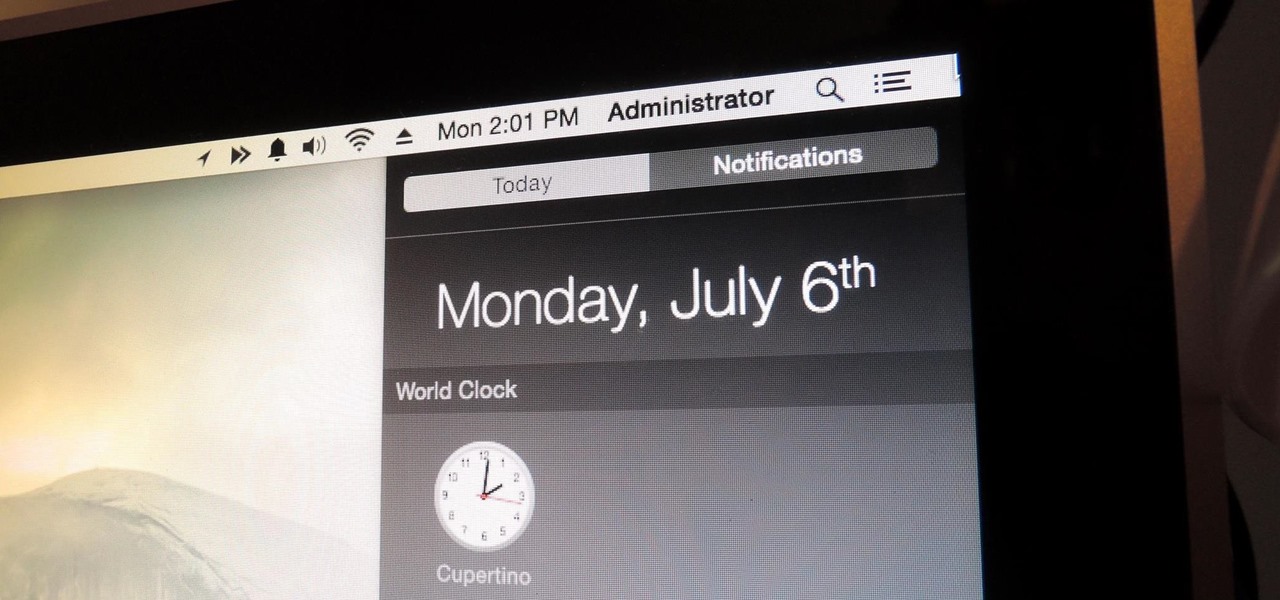
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

Willpower is a pretty significant word. It's the difference between sticking with a clean eating diet and diving face-first into a plate of brownies. It's what drags you out of bed on Monday mornings and into work rather than letting you stay snuggled under the covers asleep. And, most importantly, it's the kick in the butt we all require to both accomplish goals and make changes.

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

Welcome back, my greenhorn hackers!

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

Most Android devices allow you to simply replace a ZIP file in your /system/media folder if you want to change your boot animation. Unfortunately, though, this isn't the case for the Galaxy S5, as it's been buried deep in Samsung's TouchWiz skin.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

As I've explained before, black app backgrounds save you a bit of battery life on your Samsung Galaxy S5. This is because the AMOLED display on your S5 does not have to power pixels or a backlight for portions of the screen that are black.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Greetings, all ye happy miscreants! In my last article, I showed a certain technique for throwing a knife without spin. If you haven't read that article yet, do so now. This article will be useless to you if you have not read my article on proper throwing technique. Anyway, in this article, I will show you a cool trick you can do with my throwing technique.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

I'm one of those types of people who waits until the very last minute to find a Halloween costume, and thanks to last year's attempt at buying one at a local costume shop the day before Halloween, I will just settle for the things I have lying around in my house from now until eternity. It's like Black Friday chaos, only with more gropers.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Earlier this month, AT&T quietly introduced a new "Mobility Administrative Fee" which levies a $0.61 monthly charge to all postpaid contracts. While it's a seemingly small amount on an individual basis adding up to $7.32 per year, with its huge customer base, AT&T stands to make around half a billion from the tight-lipped move. AT&T has stated that the fee will "help cover certain expenses, such as interconnection and cell site rents and maintenance" that's consistent with other phone carrier...

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...
Admit, you're curious. You want to know just what does it take to make a virus for the Mac OS X operating system. Check out this video to learn how to write a harmless virus for computers running Mac OS X.

Watch this instructional knitting video to hang a cast on comb on a knitting machine. Watch this video a few times to master this little trick. You may want to reference some written knitting instructions in addition to following these visual guidelines.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to decrease the size of your knit piece. Use a single prong tool to unhook and tie off a single stitch on either side of the piece before completing each row to gradually decrease the width of the knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to crochet cast on. This is one way to cleverly weave your yarn onto the knitting machine and begin the piece of knit work. You may want to reference written instructions in addition to watching this knitting video.