It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

The iOS 12.0 beta earned admiration for its superior performance to last year's controversially buggy iOS 11. That doesn't mean it was free from problems before the stable release went live. During the initial iOS 12.0 beta testing phase, there were plenty of bugs and glitches, many of which affected the apps we use every day. However, none of these issues persist anymore since iOS 12 stable went live.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

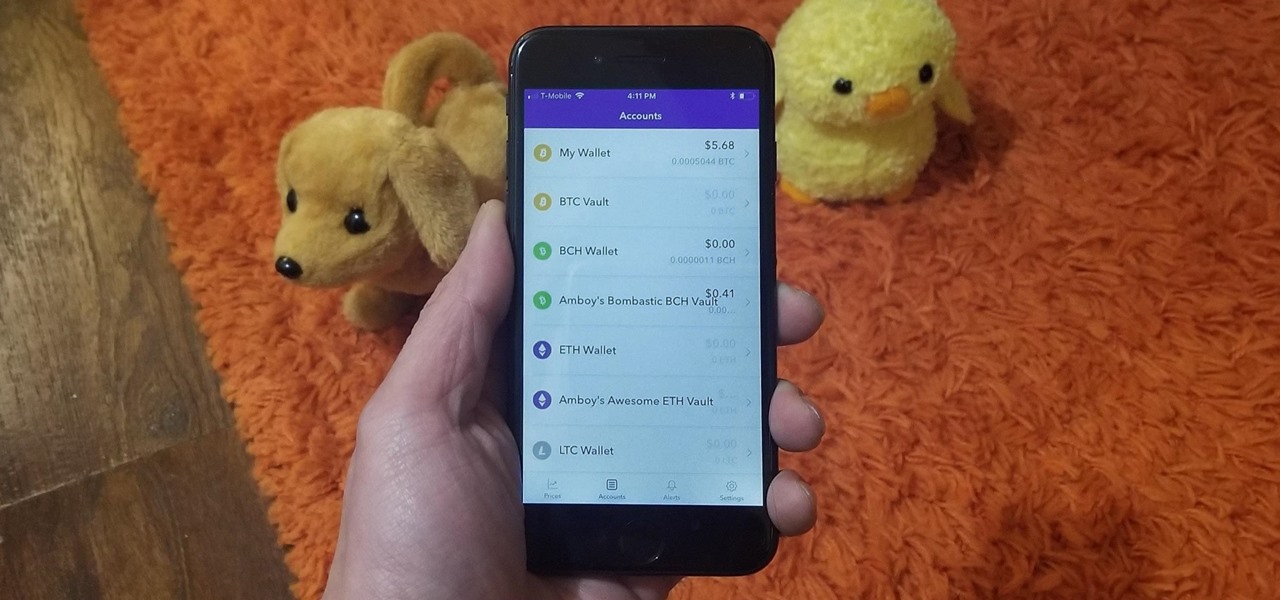
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

In Guardians of the Galaxy Vol. 2, Mantis resides in the shadow of an Ego who considers himself the actual heart of the universe. But when it comes Halloween costumes? Mantis will be the center of attention every time. The internet sure has noticed Mantis, and it's abuzz with debate over who she is. Is she just another iteration of the submissive Asian woman stereotype? Or is her character an empowering representation of empathy and the autism spectrum?

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

Apple gave the Messages app a massive makeover with iOS 10, with a slew of options that made iMessages on the iPhone a lot more fun. While not quite as comprehensive, iOS 11 builds upon that success and makes the app more user-friendly and all-inclusive.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

If the rumors are right, Microsoft has decided to cancel the second version of the HoloLens, and they will instead move onto version three of their mixed reality headset. In the latest report, Thurrott's Brad Sams states that the expected release date of this new Windows Holographic device wouldn't be until 2019, a long two years away for those of us putting full effort into HoloLens app development.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

Apple caught a lot of flak for removing the headphone jack in their iPhone 7 models, but they definitely got the last laugh when preorders with a delivery date of September 16 sold out within minutes. Headphone jack or not, the iPhone 7 and 7 Plus are still highly desirable products, and consumers have confirmed this by voting with their wallets.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

When there's a crappy stock app you want to hide, the easiest thing to do is just bury it in the back of a miscellaneous folder. But what if there's an app you want to hide on your home screen that you actually use? For instance, what if you don't want everybody in eyeshot to see what banks you use, or don't want anyone to know about your "dating" apps or porn shortcuts?

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Video: . Whether you are gardening, cooking, riding a motorcycle or just want to cover up on a bad hair day, doo rags are easy to make and fun to personalize to suit to your style. If you would rather just download the durag pattern click here.

Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're not home.

To steal a quote from Mean Girls, Halloween is the one night when a girl can dress like a total slut and no one can say anything about it—but why do girls get to have all the fun?

As you know, it's impossible to be a Steampunk without a pair of goggles. In fact, there are entire communities dedicated to judging other Steampunks based solely on their goggles. A Steampunk without goggles is like Samson without his hair, or a duck without a beak—totally powerless. As I'm sure you also know, the right pair of goggles can instantly render any outfit Steampunk, no matter what it looks like.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Written instructions on how to draft a basic skirt pattern with accompanying video. Take your correct measurements before you begin.