Chef Sanjay shows you how to make biryani masala in his first 2008 video. The great thing about this recipe is that you can make a lot at once and save it to use as you need. He gives a good breakdown of how to use this Indian food base.

This video talks about cutting techniques. Bear in mind that you will need to have lots of coverage of the same scene if you plan to do editing, so you have multiple angle options. Israel Hyman, an Arizona-based videographer, shows you how to edit your footage in this tutorial.

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.
R4DS is a cartridge-based system that fits right into SLOT-! on a NIntedo DS. Here's how to install R4DS and be able to support ROMS, multimedia files, and homebrew games on your Nintendo DS.

This tutorial shows you how to used advanced tagging and filtering options based on keywords to organize your iMovie library even further.

Chef Michel Nischan combines eggplant slices, with zucchini squash, and a mixture of cheeses for a lasagna effect casserole. Take note as he uses low sodium and low carbohydrate based products for a healthier dish.

Tim Carter shows how to use a table saw and explains its benefits at a project site. Tim's table saw has wheels on it showing the portability of the table saw.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

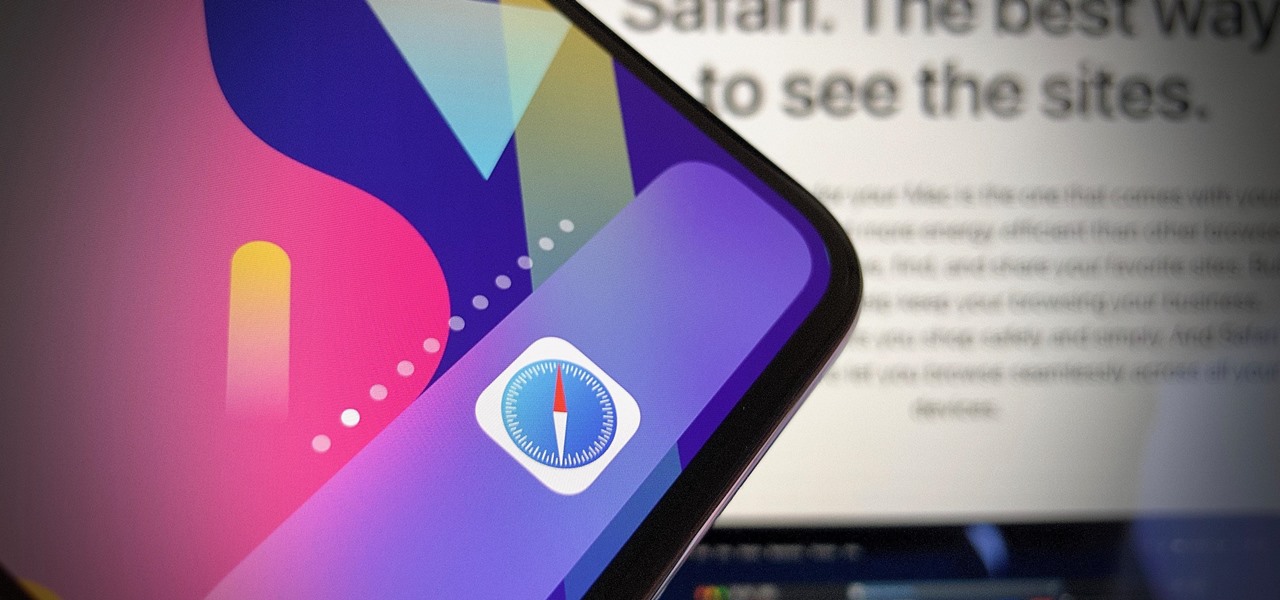
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

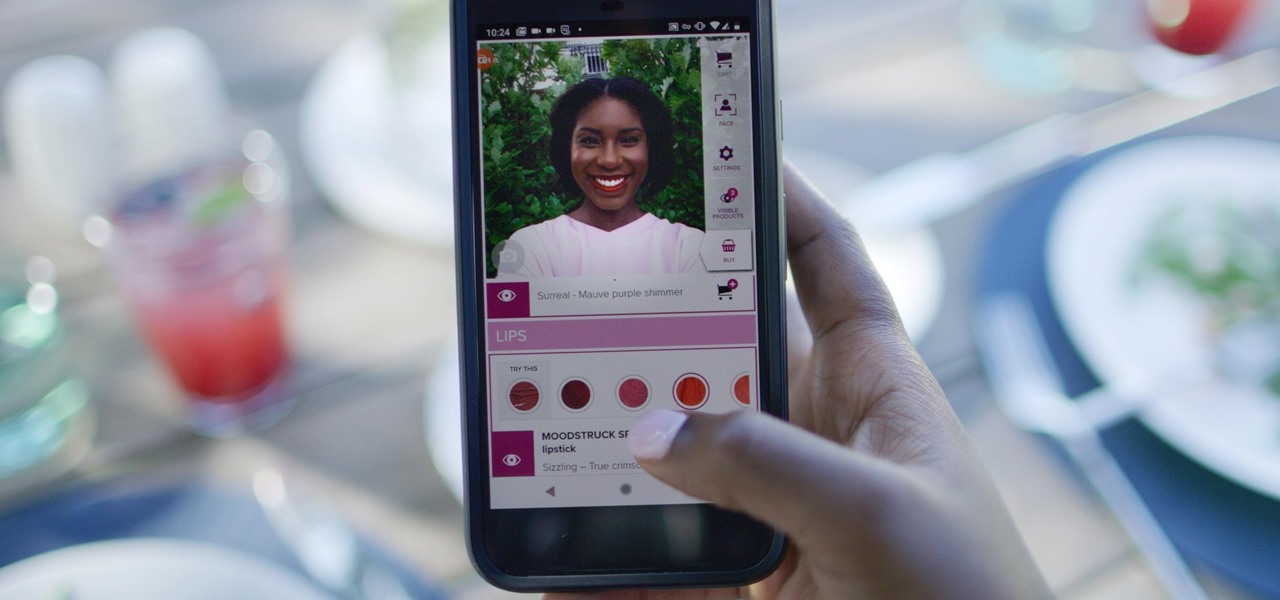
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

While the three new iPhones won't even be announced until Sept. 12 during Apple's fall event, case makers are already primed for the launch of the devices. Some case designs are already live on manufacturer websites, and you can even buy or preorder cases for the iPhone XR, iPhone XS, and iPhone XS Plus to have right now or on launch day.

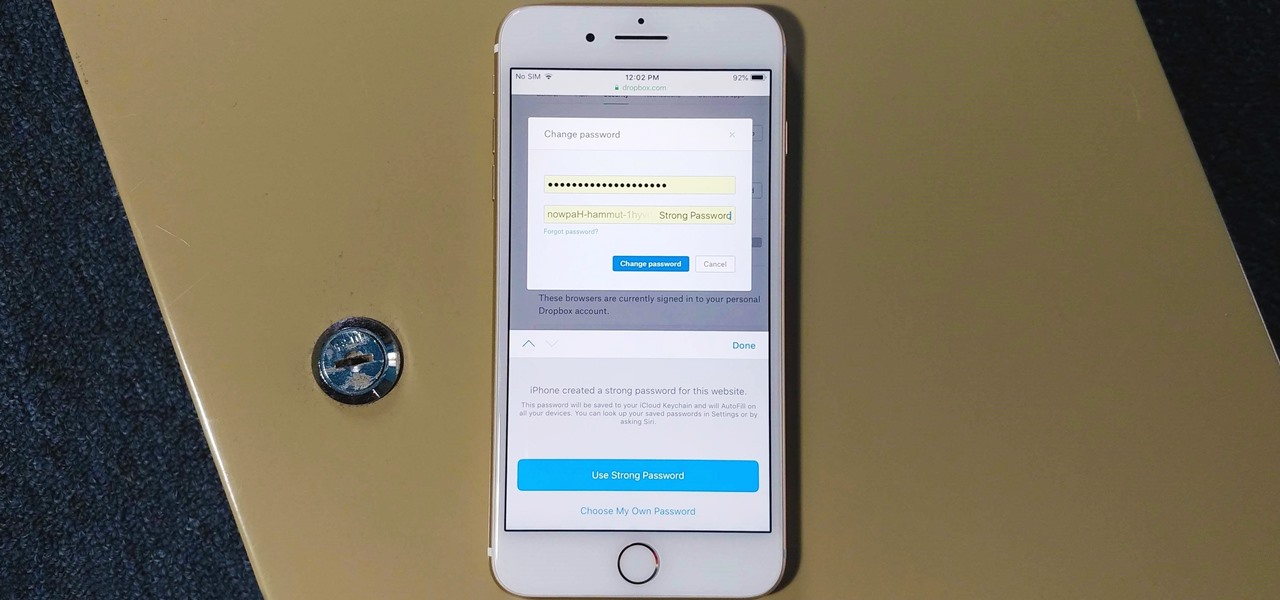
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Just a year after facing trade secret theft allegations from his former employer, ex-Meta Company employee Kevin Zhong and his new company are ready to ship the product that triggered the lawsuit.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

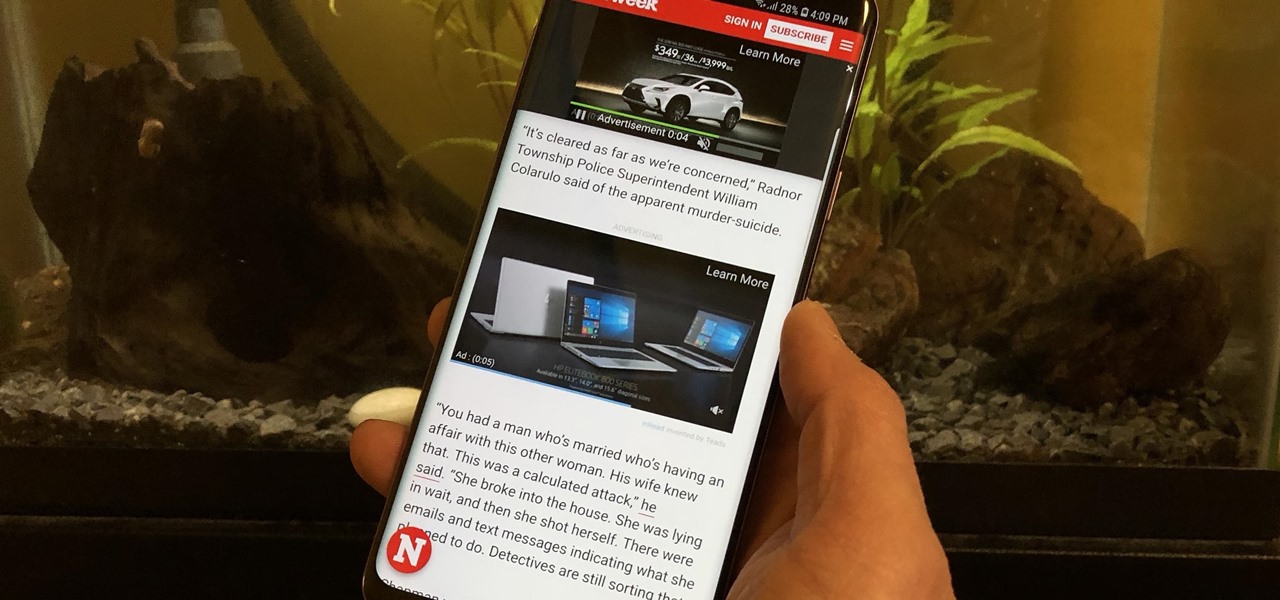
Ads can detract from your mobile browsing experience, especially if they appear out of nowhere as popups or large annoying banners that take up almost all of your screen. If those weren't bad enough, some ads appear as extremely loud videos that can even disrupt others around you. In fact, ads have gotten so obnoxious that even Google itself was forced to act.

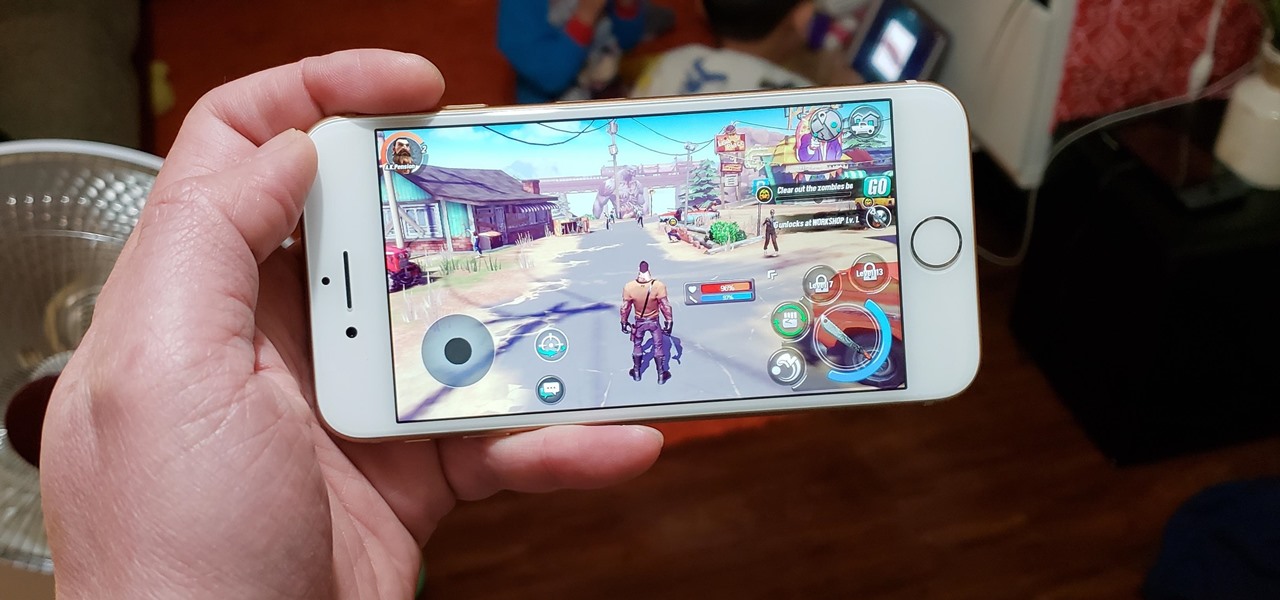
Mobile gamers are well aware of this, but zombie shooters have become pretty stagnant and unimaginative in recent years. Too many entries in this genre feature the same cookie-cutter gameplay, but thankfully, Gameloft aims to change this. The company has soft-launched Dead Rivals in a few countries, and with a little work, you can try the game yourself right now.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

|UPDATE: The event is now over and we've learned all there is to know about the new Galaxy S9 and S9+. But if you're still interested in watching Samsung's presentation, we've left the replay video embedded below.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

When it comes to paying with Apple Pay, showing your rewards number or coupon at a store, or paying for your coffee with a digital gift card, Apple Wallet is as convenient as it gets. But one issue you'll probably experience at least once on your iPhone is a persistent notification on your lock screen to view or use one of your passes — even if you're not somewhere you can actually use it.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

When iOS releases in the next few weeks, consumers on both iOS and Android operating systems can expect to see more AR ads in the mobile web browsers thanks to Vertebrae, an advertising platform for immersive media.

When it comes to playing videos from your personal media library, VLC is hard to beat. But let's say you want to play videos from an Android device by connecting it to your TV — what app should you use then? VLC is still the answer, particularly once you've enabled its TV-friendly UI.

All Galaxy S8 models apparently weren't created equal. According to numerous user reports, it appears that Snapdragon-powered Galaxy S8 variants are using an older flash storage standard than what Samsung was originally advertising.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

I don't know about you, but visions of pumpkin pie and cornbread stuffing and big, juicy turkeys are constantly dancing through my head right now. I'm sorry, healthy eating habits, but it's Thanksgiving week, and all I can do is think about food.

This little demonstration was a request to show how I die cut the Anna Griffin Flip card base die that was included in the Flip Card Kit. Step 1: Now Watch the Tutorial

This card tutorial make a very modern style of card that is out of the ordinary for me.. However this is an easy and quick card, ideal for Valentines Day or a Love card or even a Wedding Card Step 1: Items Used

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

This card is ideal for anyone that is getting married or has to make a card for the Big Day, easy to make but yet it looks so complicated. Step 1: Items Need to Make the Card

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Step by step directions for finding the surface area of a cylinder. In order to calculate the surface area of the cylinder you find the area of the two bases and add this to the lateral area.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

While its hardware may already be a little outdated compared to newer flagship phones, the OnePlus One is still a great value thanks to the dedicated community that continues to develop ROMs for it. Cyanogen 12 and Oxygen OS are the two most popular ones, but neither offers the type of unique experience you get with Xiaomi's MIUI (pronounced "Me You I").

Welcome back, my nascent hackers!