Everyone loves ice cream, no matter what age they are. So why not try making a little homemade ice cream instead of hitting up Ben & Jerry's? You'll enjoy it, and most of all, you're kids will love it. With this recipe and an ice cream maker, you can create your own sundaes, shakes and ice cream cones at home.

Ever think you could lose weight from eating MORE food? Well, if you love to nosh, Volumetrics is the right diet plan for you. Volumetrics is based on the density of food, and how it will be absorbed into your body. If you think this might be right for you, give it a try! Good luck!

Sometimes it's hard to find the time to watch your diet. When you're in a rush, you'll eat whatever you can. Many people grab snacks without considering food quality. But there are healthy vending options.

The whole family loves pizza! Why not allow them to make and put their favorite toppings. Watch this how to video and learn how to make your own homemade pizzas that the whole family will enjoy.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

It's fall—so whether or not it's cold in your part of the world, it's time for apples and anything apple-related. (Please, don't get me started on pumpkin things. Seriously.)

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

Let's talk for a second about compound butter. No, scratch that, let's not. Because compound butters are too much work. You have to shape them and roll them and tie them and cut them... no thank you.

Summertime means lots of parties, picnics, and barbecues—and wherever a group of fun-loving adults can be found basking in the sun's rays, delicious cocktails are sure to flow freely.

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

A simply frosted or glazed cupcake is like a blank canvas for creative decorations. Intricate cupcakes are works of art, but piping frosting or rolling fondant can be tricky. Luckily, even the most craft-challenged person can use pre-made decorations to create party-worthy cupcakes. Use chocolates or candies to make designs or other decorations and you can have endless fun (and very little stress) creating eye-catching treats.

Do you ever walk into a nice boutique, a friend's house, or a fancy restaurant, and think, “I wish my house smelled like this”? Because I sure do.

Raw fruit "cakes" are all the rage these days, and this stacked watermelon cake is easy to put together and is perfect for people of all ages. It's also perfect for every diet, as it's low-calorie, low-fat, gluten-free, and full of "good" carbs.

This easy "recipe" requires just two ingredients: popcorn and caramel bits. Caramel bits are made for melting, and they take all the work out of making caramel-based anything. If you've ever made caramel before, the result is delicious, but it's often hot and sticky work—in most cases.

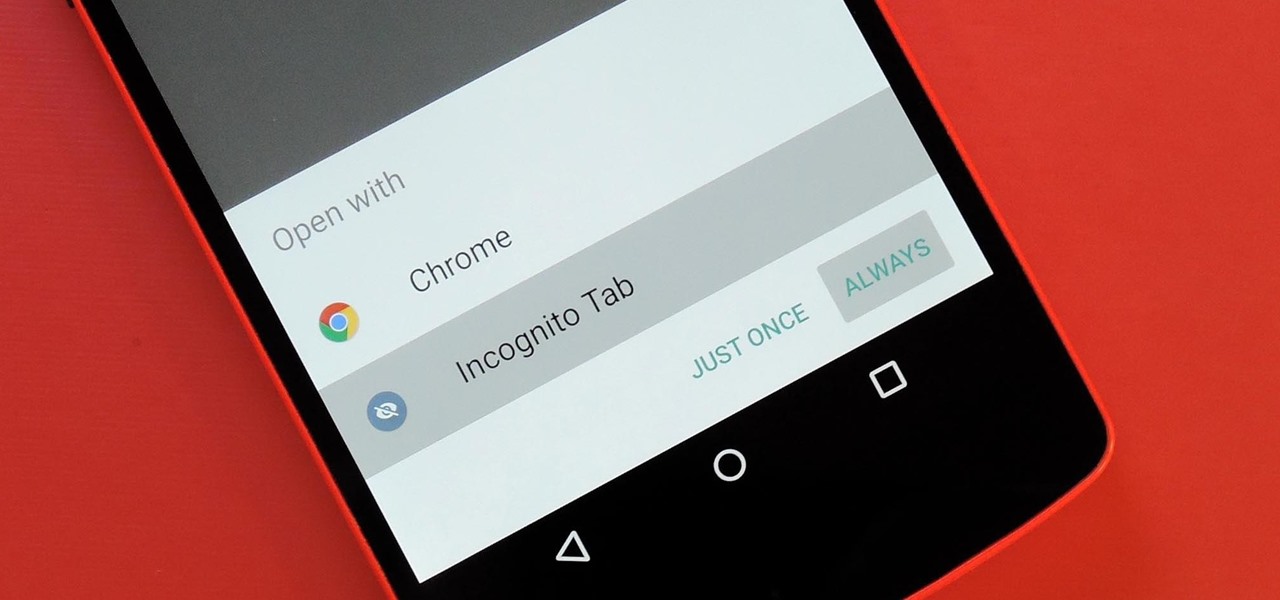
Chrome's Incognito Mode is a great feature for folks that don't want their browsing history tracked. When it's enabled, Incognito Mode makes sure that all cookies and cache that are saved while you're browsing are deleted as soon as you leave a webpage.

Most people who cook end up having at least three or four different kinds of spatulas in their drawers. I personally have at least five. However, if I had to do it all over again, I would purchase only one, and that would be a flexible fish spatula.

Doritos Locos Tacos were the brilliant concoction of a man named Todd Mills who never worked for Taco Bell, and never made any money from his creation. He originally pitched the idea to Frito-Lay, and when they said no, he took matters into his own hands by creating a Facebook page.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

There is no such thing as a pulled pork slider. In fact, there is no such thing as a pork slider. Or a chicken slider. Or turkey or fish. The term "slider" actually means a lot more than just a hot miniature sandwich, and if it's not beef, it automatically missed the first cut. Sorry, but that is not a slider above.

With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that's how they did it before the Internet...

In evolutionary times, we were far more likely to die from starvation than from diseases related to obesity. In those times, when food was available, it was best to stuff oneself.

Doorbells are a great idea. They let you know when someone who's not a burglar is trying to enter your house, apartment, or squat. They eliminate the need for lots of noisy yelling and startling door pounding.

Change things up and for your next dessert or for an after school snack, try serving banana pudding. Banana pudding is easy and combines the creamy fun of pudding with the fruity flavor of bananas. It’s a clever way to sneak in an extra serving of fruit.

Next time you have a backyard bash, serve up a tray of yummy pigs in a blanket. In this recipe, hot dogs are wrapped in light, flaky pastry dough and topped with an egg wash. o make this recipe, you will need:a package of hot dogs, though you can substitute sausage or less traditional types of hot dogs, like turkey or tofu, package puff pastry dough, egg yolk, optional. Homemade pigs in a blanket look delicious, and they are really a home run hit with everybody.

In this video tutorial, viewers learn how to make a paper fortune teller, also known as a cookie catcher. Begin by folding the paper into a right triangle and cutting off the bottom. With the squared paper, fold it horizontally both ways. Now fold the corners of the paper into the center. Flip the paper over and fold the corners of the paper into the center once again. Fold it horizontally in half. Now fold it diagonally and horizontally to make it more flexible. Finish the fortune teller by ...

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Yes, you can have your cake and eat it too. There are a lot of light or nutritional alternatives to a lot of the desserts that we commonly use or eat. Saving room for dessert is a must for adding any treat to the end of a healthy meal. Learn some tips for buying dessert foods in this nutrition how-to video.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.