With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

With all the talk about returning to the moon via SpaceX, NASA, and international agencies, some have forgotten some of the magic surrounding the original Apollo 11 mission.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.
Just because augmented reality is the technology of the future doesn't mean it can't reach into the past of computing.

Public software testers can now run the fourth iOS 12.1.3 beta. Apple seeded this update to testers on Thursday, Jan. 10. Just like with beta 3, public beta 4 includes two resolved issues — a VoiceOver fix for ECG and Irregular Heart Rate notifications, as well as audio improvements for iPad Pros.

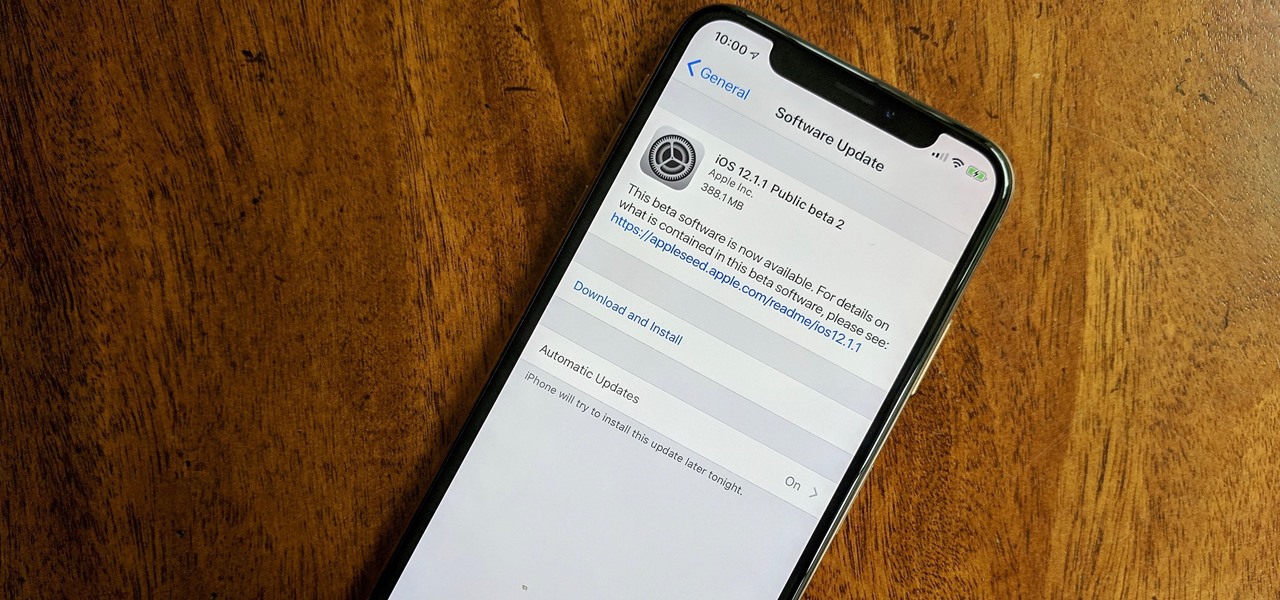
Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

Last month, Leap Motion's vice president of design and global creative director, Keiichi Matsuda (a member of the NR30), suddenly left the company. Just days later, a story leaked that revealed that Leap Motion had twice failed to lock in a potential deal with Apple.

Registered iOS developers received their first taste of 12.1.1 dev beta 2 on Wednesday, Nov. 7, and public beta testers received the iOS 12.1.1 public beta 2 shortly thereafter.

Developers opened their iPhones on Wednesday, Nov. 7, to find an update to the iOS 12.1.1 beta. Apple seeded developers the first 12.1.1 beta on Halloween, marking one week between it and the second beta. It's a quick update turnaround but in line with trends as Apple typically waits at least a week in between beta releases.

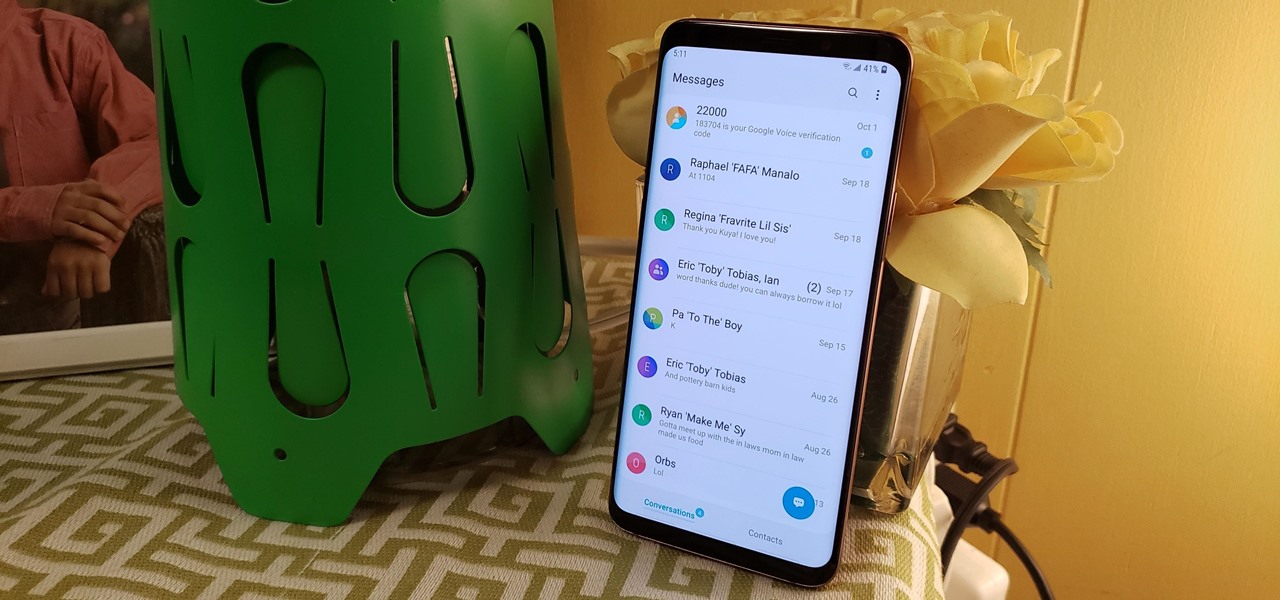
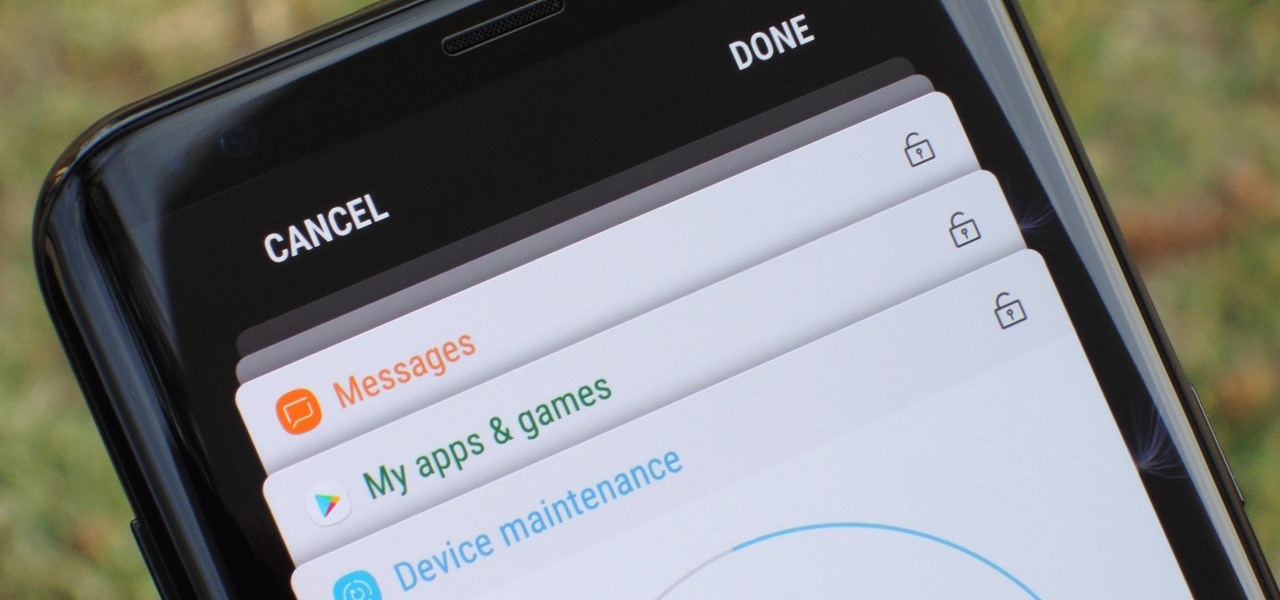
Samsung's Android Pie update — known as One UI — is bringing major changes to the Galaxy S8, Galaxy S9, and Galaxy Note 9. The main interface has received a visual overhaul, and this is no more evident than it is with notifications.

Samsung's version of Android Pie has landed on Galaxy handsets like the Note 9, S9, and S8, though we've known what to expect thanks to leaked beta versions of the software a few months back. The newly dubbed One UI has plenty of new features and improvements, but some of the first you might notice are the visual improvements to the default messaging app.

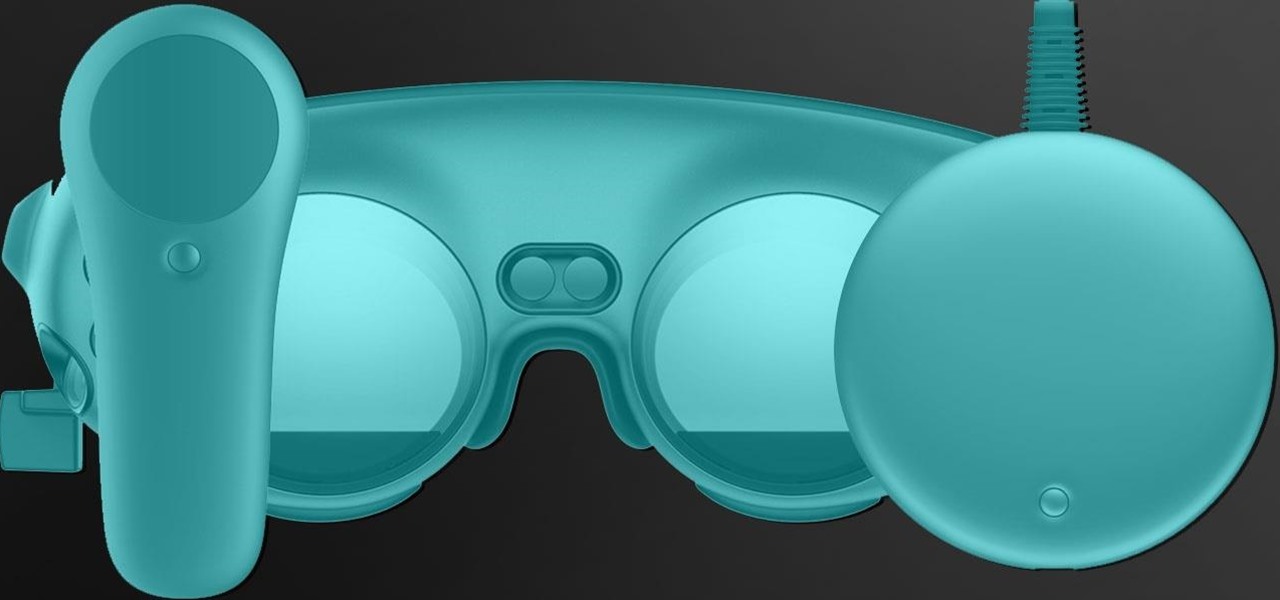
Last week, Magic Leap gave us an additional peek at its Lumin OS and more tutorials that show how its device works with virtual content. But details about the hardware wasn't included in the array of new information.

Outside of a few headlining features, Apple focused on polishing things up in iOS 12. Instead of revamping functionality left and right and running the risk of releasing a buggy mess like iOS 11, this year's feature additions are smaller. Case in point, you can now show favicons in Safari — nothing groundbreaking, but a nice touch.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

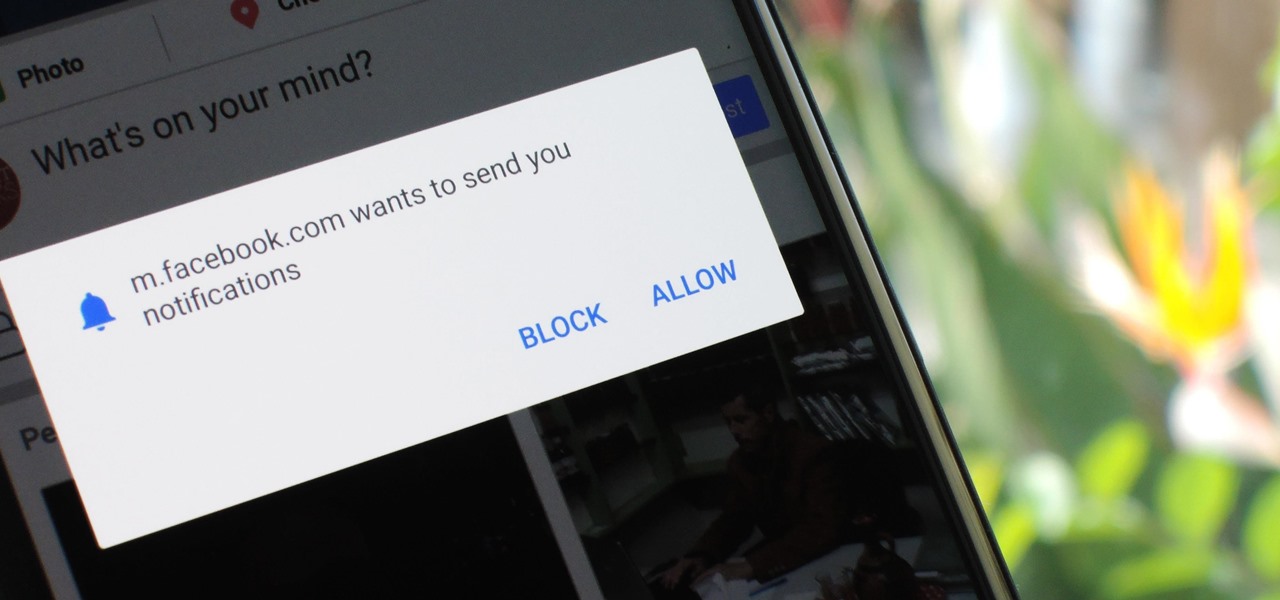
As the go-to browser for millions worldwide, Chrome makes web surfing a breeze with its simple interface and Google integration. But many websites are starting to ask if they can send you notifications, and this can interrupt your browsing. Thankfully, you can completely disable these prompts if you prefer.

The Galaxy S9 is truly a sight to behold. With a class-leading display, the best camera ever put into a smartphone, and Samsung's cutting edge design, it might just be the best piece of hardware on the market. Having said that, some of the most useful additions are actually in the software.

A Swedish digital artist has developed an app for the iPhone X that creates mind-bending 3D illusions that correlate to the user's point of view.

While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.

Soon, kids young and old aspiring to imitate Iron Man will only need to learn how to duplicate Tony Stark's snarky wit, because Hasbro will now supply the augmented reality helmet.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

Facebook may have shamelessly copied Snapchat and its camera effects for faces (as well as its World Lenses), but it might beat its social media competitor to virtual body augmentation.

Apple released iOS 11.3 beta on Jan. 24 and the public stable release on March 29, and it didn't take us long to find plenty of cool new stuff. Aside from new Animoji, Health Records, and some upcoming changes related to the recent battery fiasco, most of the new features are about polish. One such feature we've found should make iPhone X users a little happier.

Last week, we told you about one of the first pairs of augmented reality smartglasses to get Amazon Alexa functionality, and now we're finally getting a look at how it works.

Did you forget to get a Christmas gift for that niece or nephew who you see once a year? If you're lucky, the Walmart near you may have a Merge Cube in stock. When paired with the 57° North game for the Merge Cube, the mysterious-looking cube offers the possibility of extended sessions of virtual adventure in the palm of your hand. Available for $2.99 through the App Store or Google Play, 57° North is a choose-your-own-adventure game that takes place in augmented reality.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Apple is no stranger to lawsuits. They were in a decade-long battle with Samsung that finally came to an end last month, and they've been duking it out in the courtroom with Qualcomm since last year. The more recent case has seen both companies file suits and counter-suits, but now, Qualcomm is claiming that Apple's new iPhone X infringes on patents from a long-deceased mobile operating system.

With smartglasses designed for navigating drones and an AR drone racing game to its credit, Epson has just added another credit to its pioneering efforts in the AR-meets-drones space with the launch of a drone simulator app.

There was a time when building a website required coding knowledge. Eventually, software came along that made the process easier, and then services like Squarespace made it dead simple for even a technical novice to design a website.

People love emojis, it's a scientific fact. So an app that places poops, smileys, and ghosts into social media videos should, in theory, be the most popular app ever. That's likely the reasoning behind the new Holocam app, which is available for $0.99 in the iOS App Store. Sure, Snapchat and Instagram offer users editing tools to stick static text, emojis, and drawings on top of photos and videos. However, Holocam ups the ante by placing fully three-dimensional emoji, text, and drawings, as w...

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

The fifth developer beta for iOS 11.1 was released on Oct. 24, and the official iOS 11.1 update was pushed out to iPhones everywhere on Oct. 31. However, that isn't stopping Apple from seeding developers with the iOS 11.2 beta already.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

The augmented reality feature in Pokémon GO is one of the key components that draw people in to the popular Android and iPhone game. Indeed, there's nothing quite like the sight of a Pokémon standing around in an otherwise uninteresting parking lot.

Augmented and virtual reality motion tracking leader Leap Motion, Inc. announced that it has secured $50 million in Series C funding to fund expansion into new territories and industries.

The Galaxy S8's Always On Display is a fantastic feature that gives you a brief overview without having to wake up your phone. But AOD now has a virtual home button, which kinda ruins the sleek look and can even cause screen burn-in.

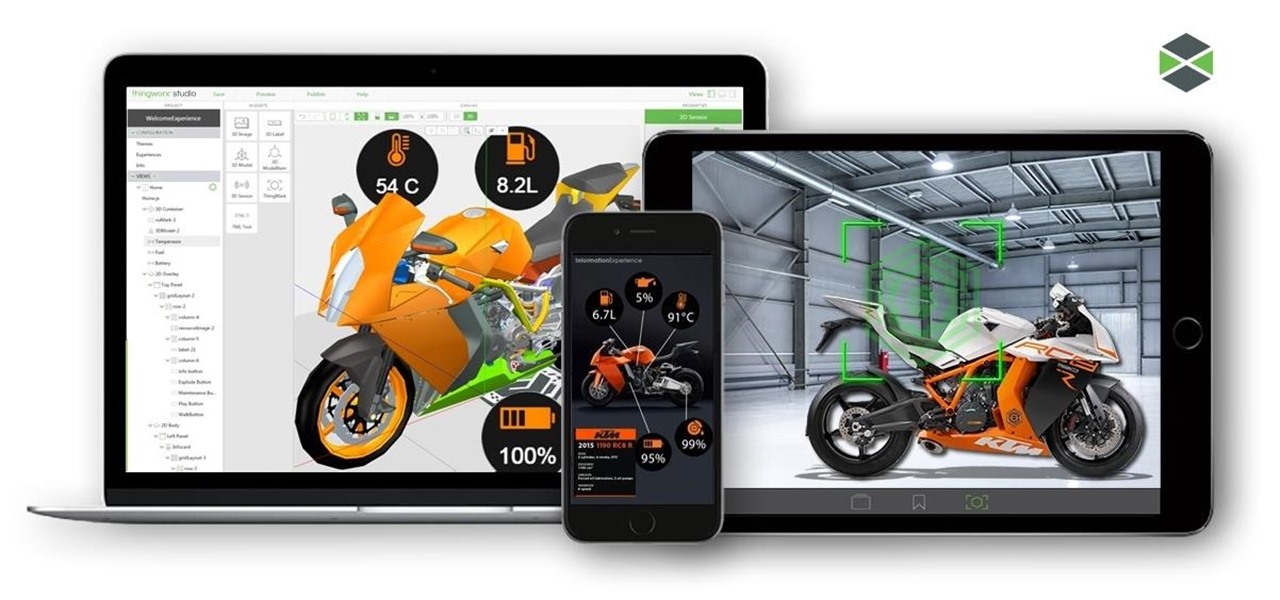
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

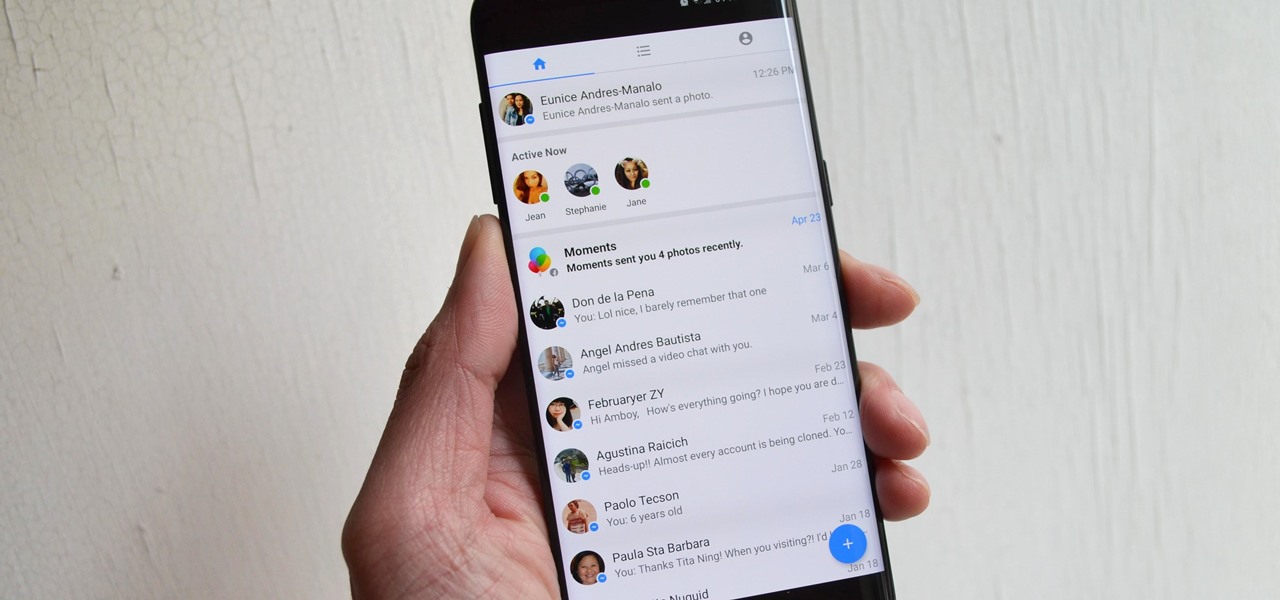
In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

Cortana, a strong competitor to Apple's Siri and the Google Assistant, has just been updated for beta testers on Android. The update introduces some sleek redesigns of both the look and features of the app, developing anticipation for the official update.