Dogs are smart. We don't need to punish them every time they don't do a trick. Through positive reinforcement training, dogs can learn almost anything. From Dogmantics, dog trainer Emily Larlham shows a few tricks she taught her dog!

From Dogmantics, dog trainer Emily Larlham gives a us tips on how to get your doggy to stop barking. By first changing your dog's emotional response to the stimuli, then working from low levels of criteria to higher levels, then finally, adding full criteria you're dog will get comfortable around the bark-worthy source and remain calm.

In this video tutorial, Chris Pels will show how to extend the standard set of ASP.NET configuration settings with your own XML configuration elements. First, see how to create a configuration section handler which is required to interpret and process the information in custom XML configuration elements. During this learn how to use declarative model for defining the behavior of a configuration section handler. Next, see how to add a custom section handler and custom elements to an ASP.NET co...

At one time or another, every parent has thought about taking off the belt, but that's frowned upon in our current society, perhaps even illegal. Even using you hand could be too harsh for the child's sake, but there are ways to get your unruly tot under control. Toddlers are often headed for trouble, but you can steer them in the right direction without spanking.

Worried your canine might bite somebody? Afraid to take them on walks anymore because of what could happen if a child walks past you? Afraid of a lawsuit? These are the worries associated with overly aggressive dogs. But with proper training, an aggressive dog can be transformed into a well-behaved companion you'll love having at your side.

First in the training for a German Shepherd is that your dog should start the very first day you bring your German Shepherd puppy or adult home. In general, Dog obedience training benefits are to give proper mental and physical activities. Secondly, there should be existence of friendly relation (bond) between you and your dog. The third is to ensure that your dog's safety and happiness. Lastly correct many types of dog nuisance behaviors like digging, barking and chewing etc. Two levels of D...

Thinking it's time to give up the juice? If your need to drink has become a problem, quit. This lifestyle change requires planning and ferocious self-discipline, but everyone has it in them.

With information, diligence, and determination, hair pulling is a habit that can be broken. You Will Need

Before you select a guard dog, find out what qualities to look for and what to avoid. You Will Need

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Early intervention is important for children with autism, a developmental disorder that inhibits socialization. So be on the lookout for warning signs.

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.

Do you sometimes wish you were an only child? Yeah, so does your irritating little brother or sister.

This how-to video quickly outlines exercises to get your dog walking on a loose leash by your side. Put very basically, teach the dog what you want them to do! And secondly, stop reinforcing them when they pull! A clicker training method is used, but if you do not have one, you can always use a verbal marker like yes. However you will get much faster and reliable results by using the clicker. If you hold the clicker in the same hand as the leash, and keep the treats in the other hand, you wil...

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Okay, Mr. Thrifty, you reserved the least expensive hotel room that you could. But your inner Donald Trump doesn’t want to settle for low-frills. Go ahead, it never hurts to ask. Watch this video to learn how to get a hotel upgrade.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Check out how to demonstrate the Kaye effect using shampoo and lanyard with this tutorial. On dribbling shampoo from a small height above a pool of the same shampoo below, every now and then liquid lanyards of shampoo leap forth in a behavior referred to as the Kaye effect. Such behavior is characteristic of a viscoelastic fluid. This is a great science experiment to do with your kids. Watch this how to video and you will be able to create the Kaye effect at home.

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

Managing multiple applications on an iPhone is as simple as double-tapping the home button, long pressing the app you want to close, and tapping on the minus sign in the red circle. If you're using Mac OS X, the dock at the bottom of the home screen plays the role of the multitasking bar on the iPhone, just not as sleek or simple.

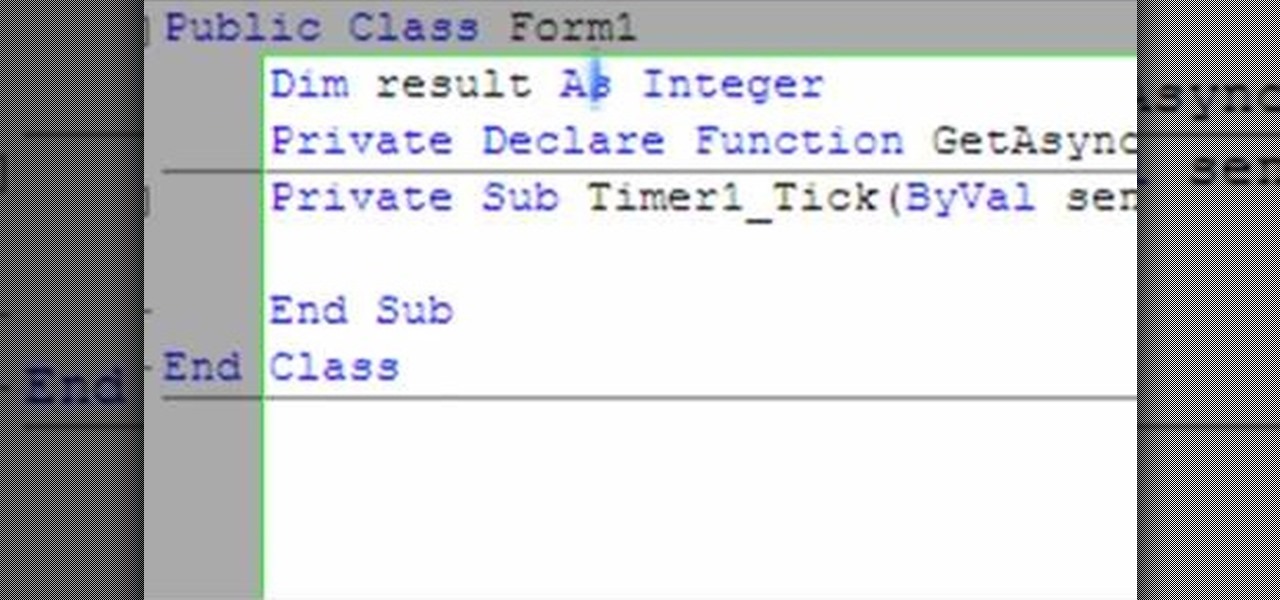
The following video shows how you can make a keylogger in Visual Basic 2008. Follow the steps below to create your own keylogger. First you will want to open a new application and name it according to your preferences. Then you want to click on the toolbar button and click textbox. In the textbox values, you will want to select the value of true for 'Multiline' option and the value of True for 'Read only'. On the toolbar, select the 'Behavior' tab and mark it as 'Window'. Go back on to the ma...

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Sooner or later, you're going to come across a person at work that you don't like—or someone that doesn't like you. This can result in uncomfortable tension, insulting gossip, and a disrespectful attitude, to name just a few of the negatives. But it doesn't have to be that way. The next time you're having a workplace conflict with a particularly challenging coworker, the best thing you can do is keep your mouth shut, and here's how to do it.

Despite all the tragic stories you hear on the news, you'll probably never be involved in a shooting. But you never know. Nobody thinks it’s going to happen to them – until it does. Be prepared to survive a shooting rampage, just in case.

These rabbit tricks are from the Santa Barbara Bunnies Urgently Needing Shelter Association. BUNSSB.org is training the bunnies to respond to a clicker using principles of Pavlov's dog. She shows his tricks and when you must click and give a treat to reinforce the trained behavior.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Pokémon GO updates will have new deterrents for cheaters, and these seem to use shame more than just prevention. The changes were mentioned by a Pokémon GO support account on Reddit. (There are other updates coming soon to Pokémon GO as well.)

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

An unfortunate byproduct of Samsung's One UI version of Android is redundancy, where you have the Google/AOSP way of doing things mixed with Samsung's methods at the same time.

Apple quietly pushed out iOS 12.3 public beta 3 on Tuesday, April 23, just over a day after developer beta 3 was released. Just like with the developer version, there aren't any major features or changes to get excited about, but if you were experiencing any minor bugs with the previous betas on your iPhone, this update could squash some of them.

Developers, get excited. The new iOS 12.3 dev beta 3 just dropped. While this beta doesn't introduce any major features or changes, it means Apple is continuing to address unseen bugs and potential vulnerabilities from the previous versions.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

In a twist in the tumultuous lawsuit between Uber and Waymo, Uber revealed today that they found a document on an employee device, allegedly stolen from Waymo.

You might not think a mixed reality headset could help kids eat their vegetables, but that's the exact premise behind Habit.at—the app that won the "Social Good" category at the 2016 HoloHacks competition in Los Angeles.

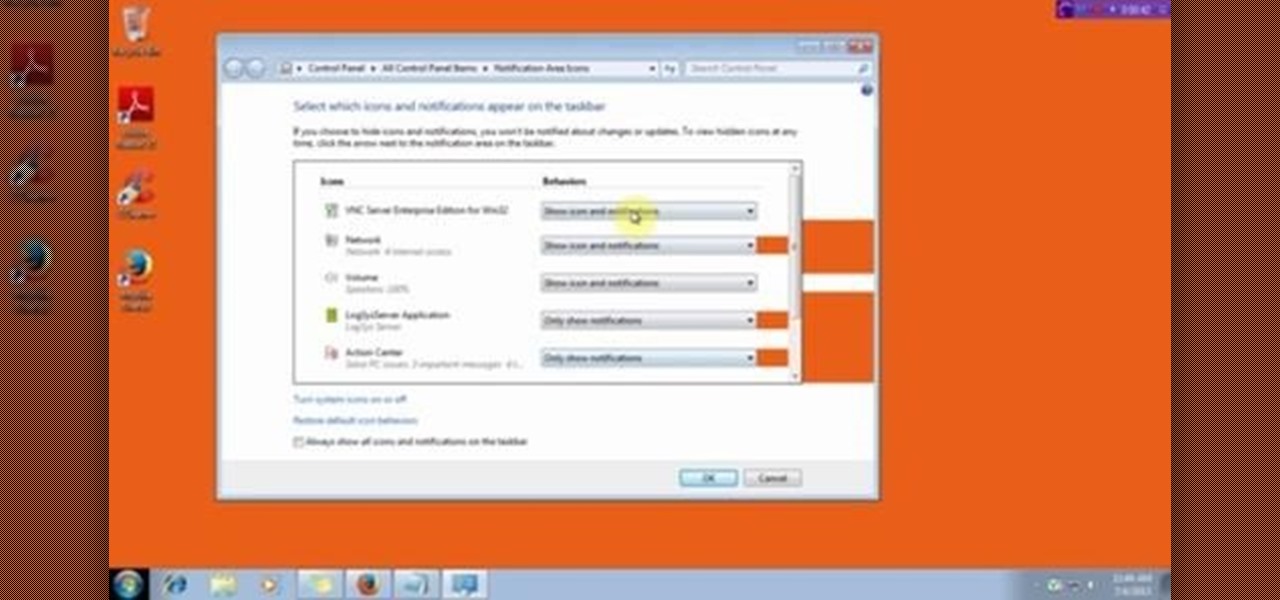
This video will show you how to customize the notification area on windows 7. Notification area is a small portion at bottom right corner of the screen. You could customize the notification area by adding new icons, removing icons and changing their behavior. Watch the video and follow the steps.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.