
Behavior Search Results


How To: Potty train and housebreak a dog
In this tutorial, we learn how to potty train and housebreak a dog. There are a lot of techniques out there, but you will want to do in the most fast and effective manor. Some pet owners want to paper train their puppies. This may work, but it will take longer to get your puppy to associate going to the bathroom with paper. Don't let your dog pee in the house in the beginning, or this will let your dog think it's okay for them to do this all the time. Focus on all the aspects of dog training ...

How To: Solve the Hanayama Cast Chain metal puzzle
Watch and learn how to solve the Hanayama Cast Chain metal puzzle in this video tutorial. The Hanayama Cast Chain is a 6 out of 6 for difficulty.

News: The First Beta for iOS 15 Is Now Available to Download on iPhone
Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

How To: Tactical Nmap for Beginner Network Reconnaissance
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.
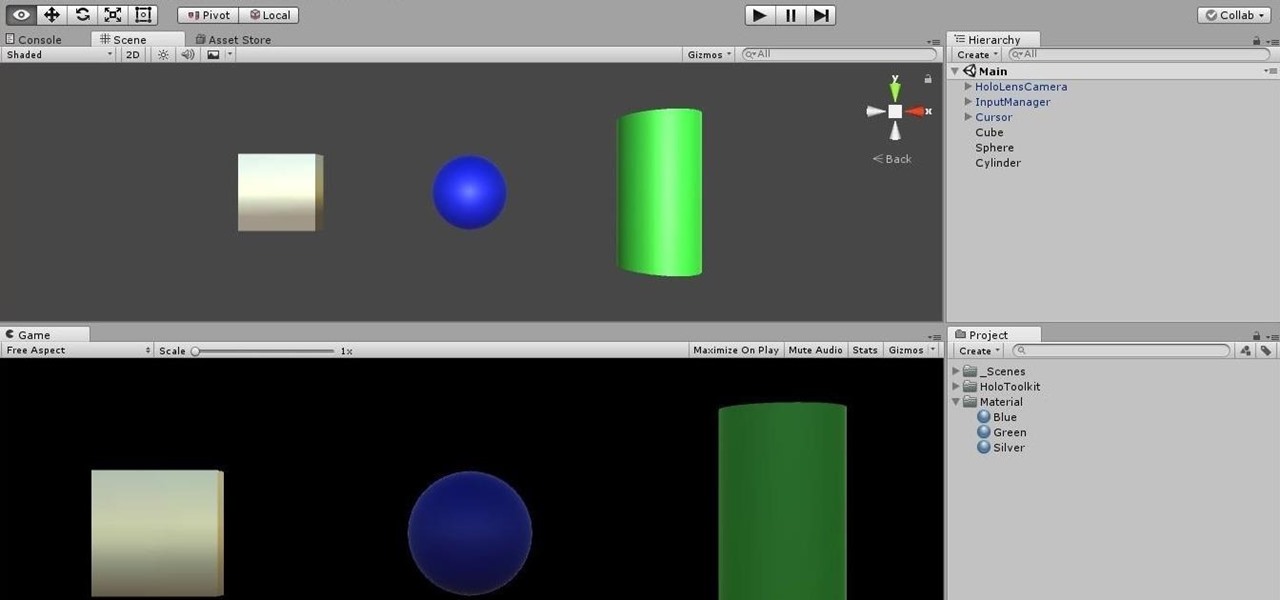
HoloLens Dev 101: How to Use Coroutines to Add Effects to Holograms
Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.
Canvas Fingerprinting: How to Stop the Web's Sneakiest Tracking Tool in Your Browser
Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

News: Apple's iOS 14 Public Beta 7 for iPhone Includes New Dark Mode Wallpaper Options, Tweaks to App Library & More
Apple just released iOS 14 public beta 7 for iPhone today, Thursday, Sept. 3, and features new dark mode wallpaper options. Choose from any of the rainbow wallpaper's color backgrounds, and iOS will automatically shift the background to black when you enable dark mode.

News: Apple's iOS 14 Developer Beta 7 for iPhone Includes New Wallpaper Options
Apple just released iOS 14 developer beta 7 for iPhone today, Thursday, Sept. 3. The new update (18A5369b) features new wallpaper options. Now, you can choose any color background for the rainbow wallpaper, and iOS will turn the background black when you enable dark mode.
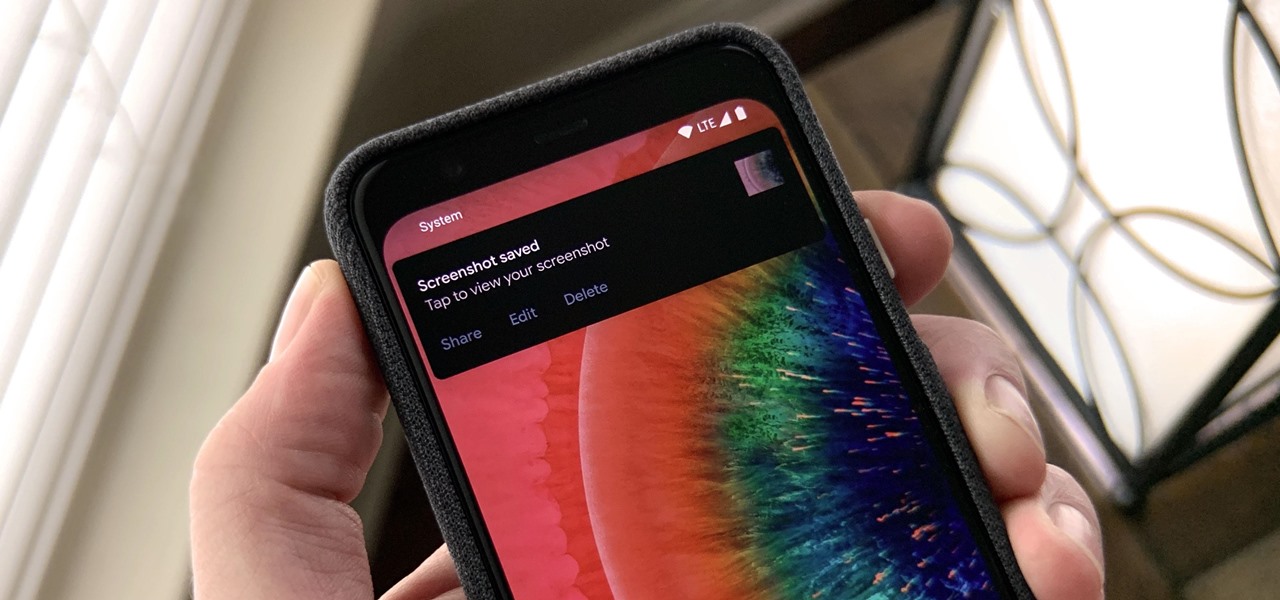
How To: Disable Those Pesky 'Screenshot Saved' Notifications on Your Android Phone
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.
How To: Get the Pixel Launcher with an Integrated Google Now Page on Any Phone — No Root Needed
Google has an exclusive launcher for its Pixel devices, and it's pretty slick. But even though we've found ways to get this home screen app on other phones, certain features simply wouldn't work unless you were rooted. That's finally changed.

News: Your Android Apps Are Secretly Getting Chatty with Your Data
As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.
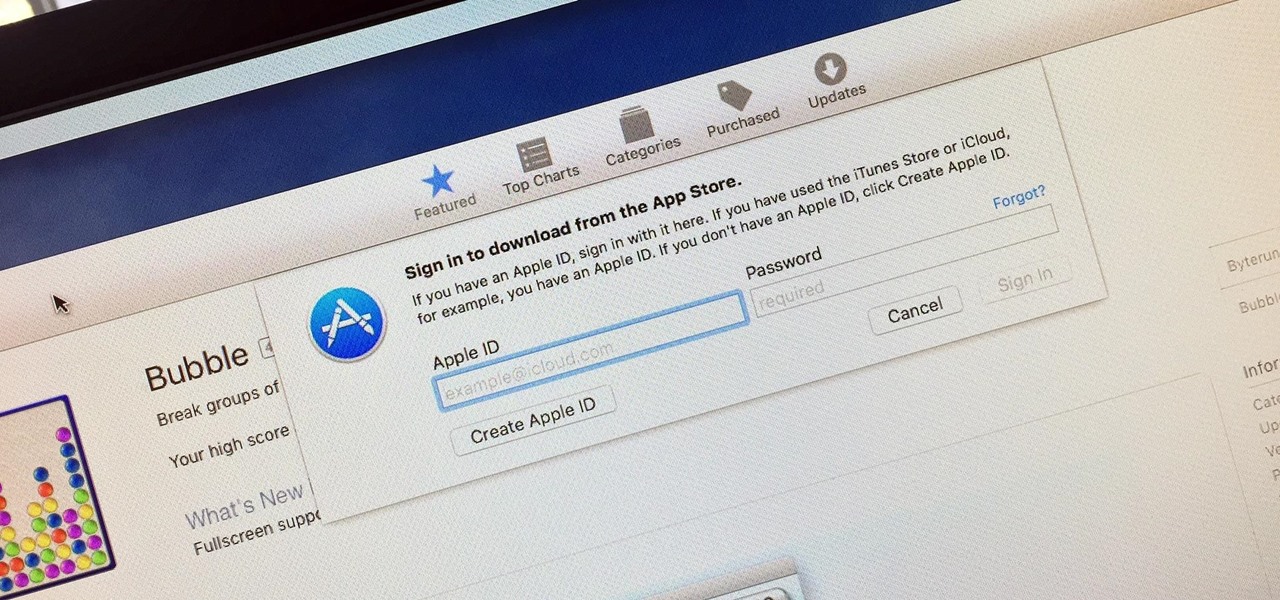
How To: Disable Password Prompts When Downloading Free Apps in the Mac App Store
Whether you want to edit photos, compress files, play games, or DJ your next party, there's a free Mac app that can help you out. But things can get annoying real fast if you download a lot of free apps from the Mac App Store, since you have to type in your Apple ID password each time.

How To: Wait... Photographing Your Meals Actually Improves Them?
Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

How To: Translate Languages on the Fly with This Floating Translator for Your Samsung Galaxy S3
Parlez-vous français? While we all wish we were fluent in multiple languages like Jason Bourne, most of us are probably one-trick ponies. When traveling abroad, or even when taking language courses, having a translator handy is extremely important.

How To: Insult someone with the perfect insult
Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

How To: Handle a bridezilla
Is a Bridezilla driving you crazy? Whether the bride gone wild is your sister, daughter, or BFF, you can stop the insanity. Here are some tips offered on how to deal with an out-of-her-mind bride.
How To: Use an ESP8266 Beacon Spammer to Track Smartphone Users
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

How To: Exploit Java Remote Method Invocation to Get Root
In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

How To: Security-Oriented C Tutorial 0xFC - A Simple XOR Encryptor
Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

How To: Extend Battery Power on Your Windows 10 Laptop or Surface
Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

How To: Recognize the Tricks of a Salesman (And Overcome Them)
Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

News: Apple Just Released iOS 13 Public Beta 2, Includes FaceTime Attention Correction, Cursor Sizing Options & More
The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just released iOS 13 public beta 2 and all the goodies that come with it.

News: Apple's iOS 13 Developer Beta 3 Available for iPhone, Packed with New Features & Changes
On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's just a few of the new features.
News: Apple Releases iOS 13 Developer Beta 2 with Config Profile OTAs, Plus Controls & New Effect for Portrait Lighting
There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

News: iOS 13 Developer Beta 1 Available for iPhone with a Lot of Kinks to Work Out
The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

How To: Check Your MacOS Computer for Malware & Keyloggers
While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

How To: Steal Ubuntu & MacOS Sudo Passwords Without Any Cracking
With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

How To: 5 Reasons You Should Use Be Using Norton Mobile Security on Your Android Device
When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

How To: 5 Ways You're Making Yourself Dumber
No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

How To: 5 Reasons You Should Stop Sleeping In
Are you someone who always struggles to wake up in the morning, no matter how much you've slept? For most, the thought of getting out of bed any earlier sounds horrific. Yet dragging yourself out of bed and towards the coffee maker a few hours earlier each day can have benefits you've never realized. Here are six reasons that make a compelling case for ending our bad habit of sleeping a little too long.

How To: Zuitte Offers 50+ Must-Have Tools for Entrepreneurs
The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

How To: The Paranoid Mac Owner's Guide to Defeating Remote Snooping & Evil Maid Attacks
If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.
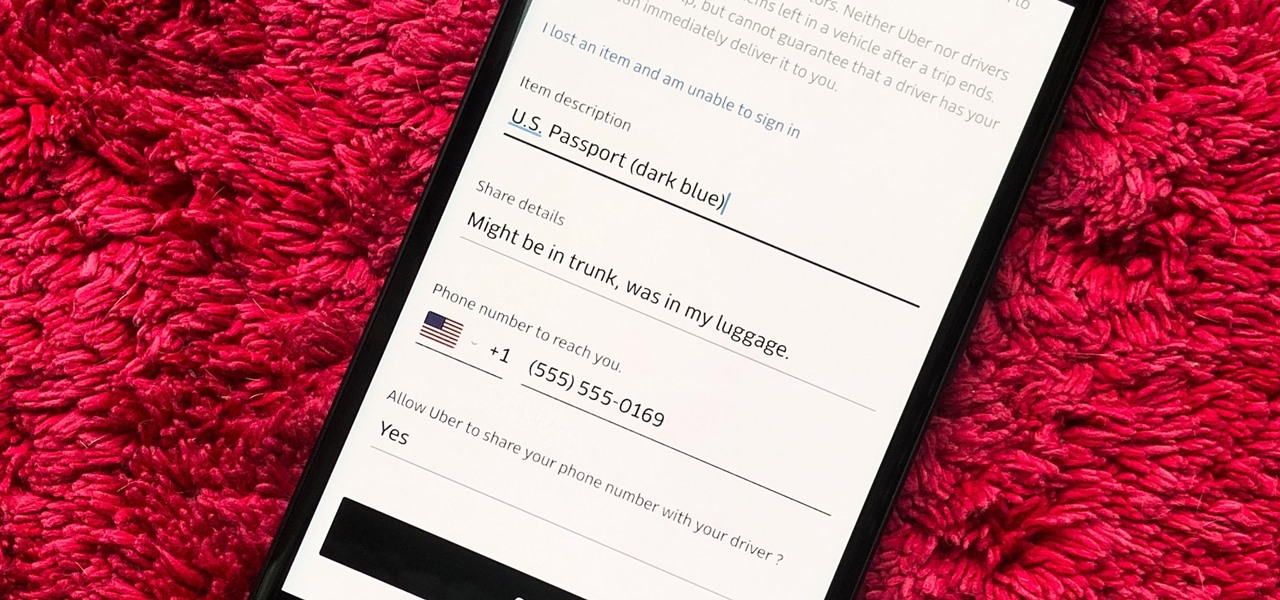
How To: Get Your Lost Item Back from an Uber Driver (& What to Do if They Don't Respond)
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

News: Jurassic World Augmented Reality Game Wants to Be Pokémon GO for Real Dinosaurs
Following in the augmented reality footsteps of Pokémon GO, Universal Studios has decided to give us an AR version of Jurassic World.
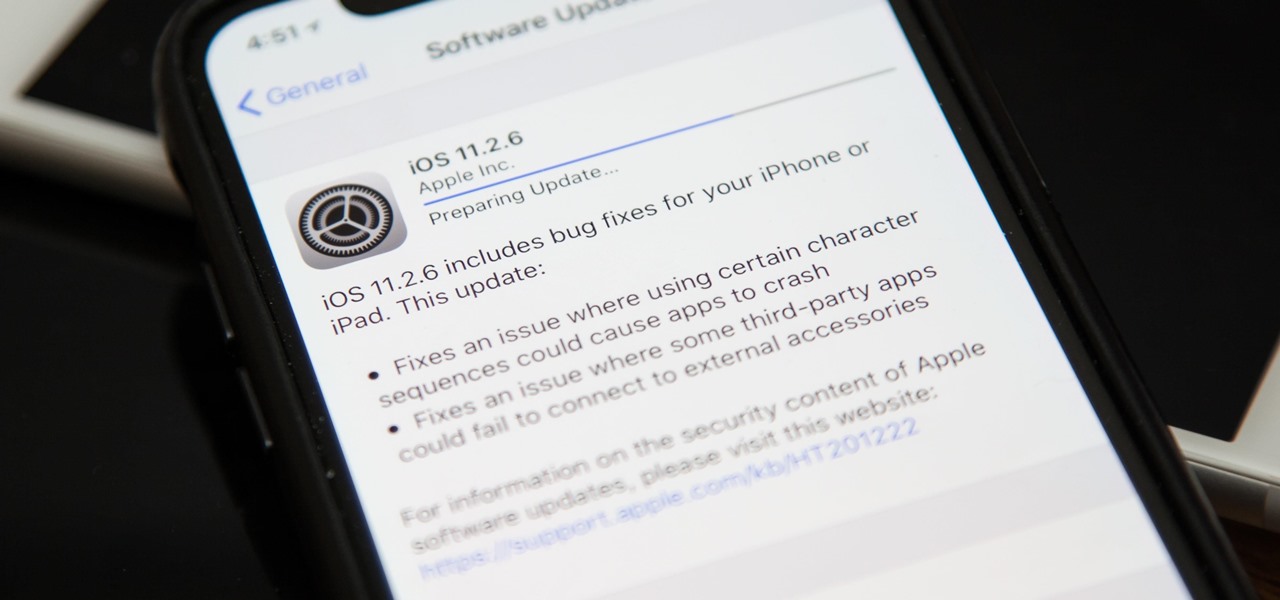
News: iOS 11.2.6 Released for iPhones with Patch for 'Telugu' Character Bug
Apple released the official iOS 11.2.6 update Monday for iPhones, which comes just under four weeks after Apple pushed iOS 11.2.5 to users. This latest update was released off Apple's normal release schedule to quickly patch the "Telugu" character bug that causes erratic behavior when viewed in apps.

How To: The Next Big Thing in Smartphone Cameras Is Machine Learning — & It's Already Here
As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

News: Zappar Extends AR Services to EVRYTHNG IoT Platform
A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.
News: Safari to Block Third-Party Tracking & Autoplay
Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

News: How Governments Around the World Are Undermining Citizens' Privacy & Security to Stockpile Cyberweapons
In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

