The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even read new ones.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

For some, there's nothing more thrilling than carrying an armful of bags while wandering the mall; for others, there's nothing more annoying. No matter what category of shopper you fit into, the truth is that you aren't always in control of what you buy.

HTC's Sense 6 has been out for over a month now with the One M8, and most of you have probably played around with its better known features, like the new Camera app and Harman Kardon audio.

Phantom phone vibrations. You might feel them in the pocket of your jeans, or when your handbag is on your shoulder—even when you're holding your phone in your hand. When you do, you immediately wake it up to see who texted or what app just had an update—but there are no alerts.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

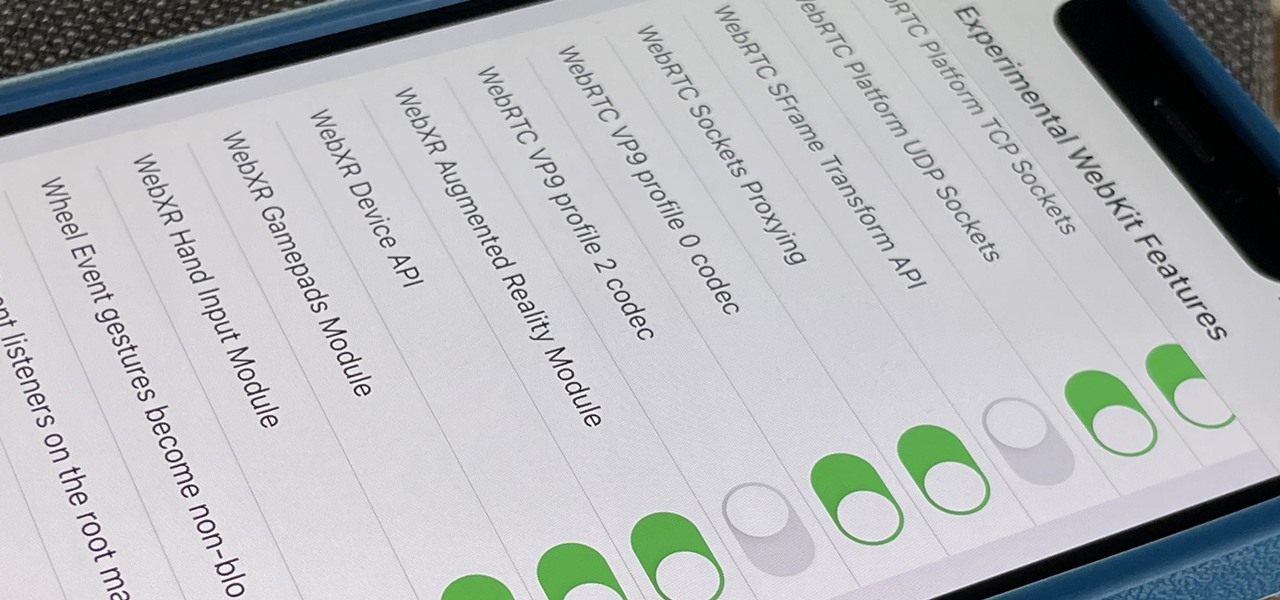
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

As you test out the new Quick Settings media controls in Android 11 and form an opinion, you'll notice one of the changes they made to the player besides the new location. For example, when you swipe away the mini version of these controls, the music keeps playing and the player still appears in the expanded view.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

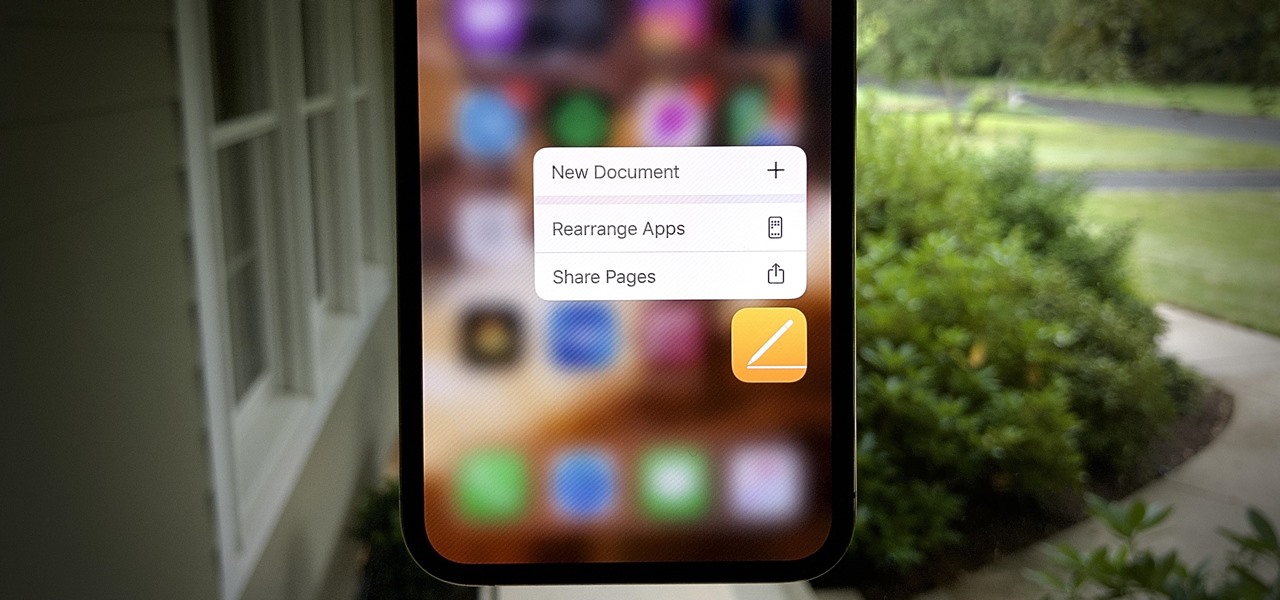
We're basically living in the future, so let's work like we are. For decades, we have, without question, opened a word processor like Pages, and clicked or tapped our way to starting a new document. What's wrong with that? It's unnecessary. We all have a digital assistant living in our iPhone, one that can start up a new Pages doc by verbal request.

The idea of squeezing your phone might have sounded a bit out there when it was new, but it's now a hallmark feature on Pixel devices. As useful as it is for summoning the Google Assistant, however, it certainly would be nice to be able pick and choose what action is triggered by squeezing the phone. Well, now you can.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all you'll need is ARKit!

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

A clean slate may be just what your Apple Watch needs. Whether you want to start fresh, wipe all your personal data, fix buggy issues, let someone borrow it, sell it, or get back in after you forgot your passcode, resetting the Watch back to factory settings is pretty simple, and you can do it with or without your iPhone.

In the Android community, there's a lot of discussion about how display notches should be used. For some, hiding the notch is more appealing, but others feel that hiding it wastes screen real estate. Well, Essential just provided another solution that should satisfy both sides.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

When you're trying to cut some calories or just eat more veggies, it's important to enjoy what you're eating. If all you're doing is telling yourself "no" and focusing on what you can't eat, you are pretty much destined to fail at your diet.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.