After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.
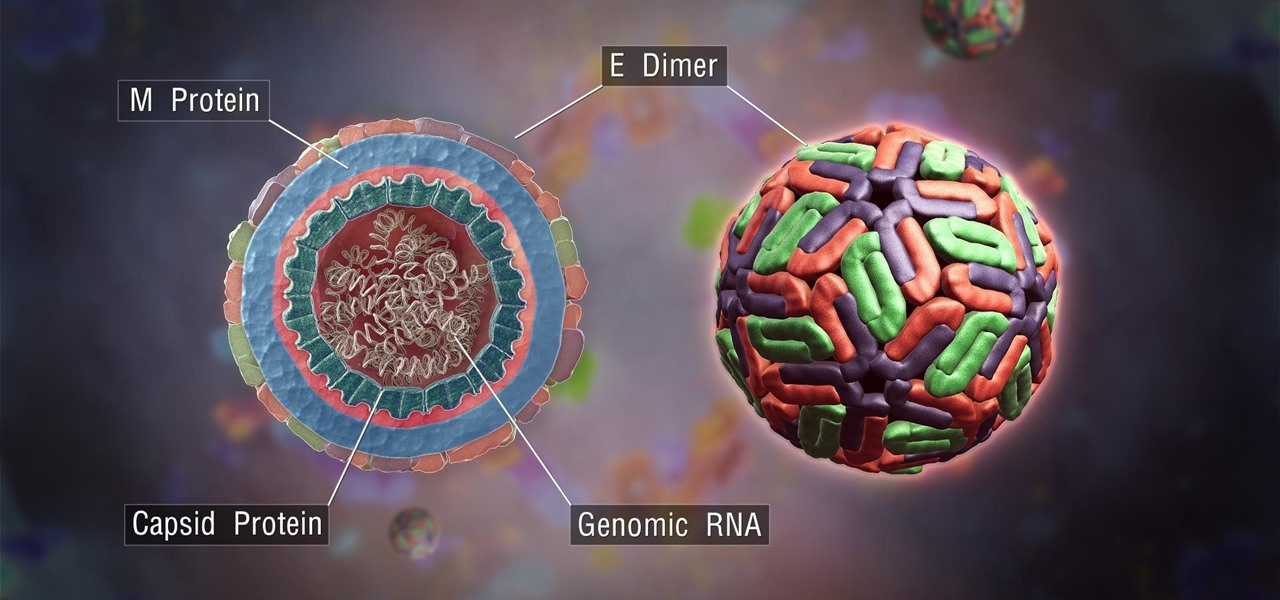
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

A report from app data firm Sensor Tower reveals that more than 13 million ARKit apps have been installed on iPhones and iPads within the first six months since the toolkit launched with iOS 11.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Each morning, we spend a significant portion of our time staring into the mirror. From choosing clothes and accessories to perfecting our hair, we try to make ourselves attractive. Yet catching others' attention doesn't have to rely on preening and primping. There's some truth to the maxim of beauty in confidence—all you need to make yourself more attractive is spray on your favorite scent.

Cats. Whether you love 'em or hate 'em, you've got to admit—they've got minds of their own. While this makes them incredibly entertaining at times, it can also cause tons of issues for their owners. Trying to "train" a cat is usually an exercise in futility.

Males fight for dominance in order to gain access to the limited supply of female eggs. This is why male birds expend energy on brightly colored plumage, but female birds do not.

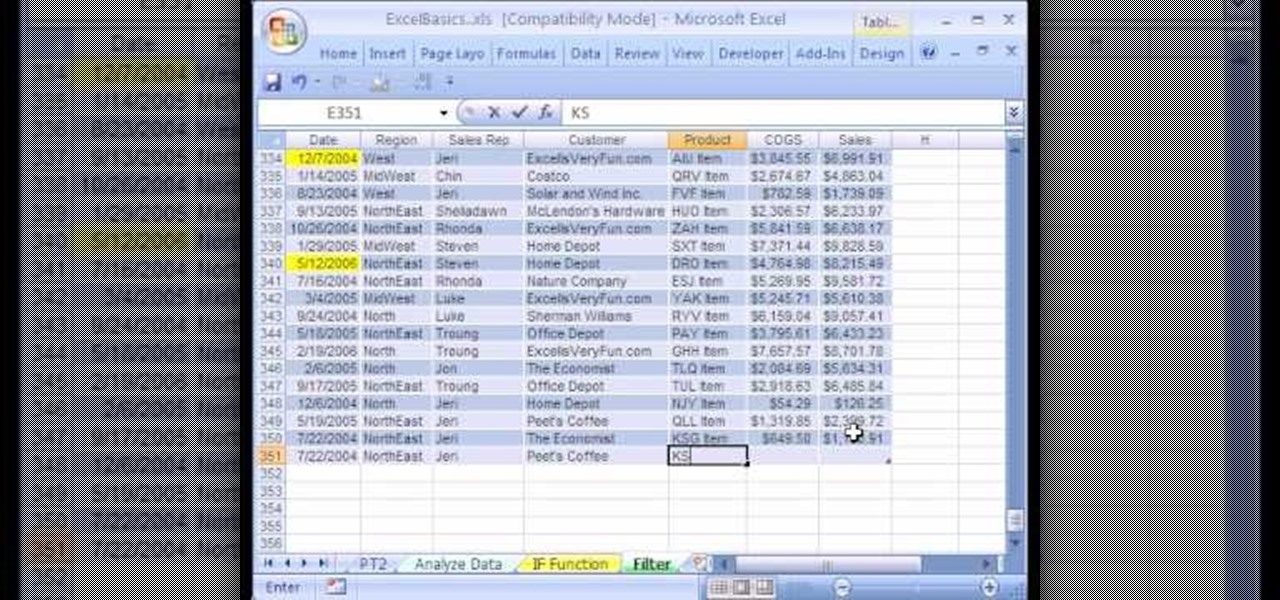
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

Master your tennis kick serve progressions. This tennis lesson video series lays out the 4 steps to tennis kick serve progressions. Be sure to click on all the video chapters to view the entire tutorial.

The ready position is the position you want to be in when you're waiting for your opponent to hit you the tennis ball. It's the foundation for tennis movement in general. From this position you can employ the various footwork patterns that let you move around the tennis court correctly. The ready position is very similar to an athletic stance in basketball. Your feet are a little bit wider than shoulder-width apart, your knees are slightly bent and the weight should be on the balls of your feet.

Footwork is probably the most important part of tennis. Unfortunately, it is also one of the most underrated areas of the sport. Learning to move around the tennis court correctly is EXTREMELY important. Correct footwork lets you use correct stroke mechanics when you hit. Correct footwork is what typically sets advanced tennis players apart from everyone else.

Bringing your back foot up after you hit the tennis ball puts you in position to recover back to the middle of the tennis court. The key, as we explain in this video, is to get your body facing the net after you hit (similar to the ready position). This will let you side shuffle back to the middle of the tennis court.

The fourth thing that every high-level tennis player does when hitting a backhand is follow through. Extend out in the direction you are hitting the ball, then smoothly bend the elbows and wrap the racket up over your shoulder.

This video explains how the amount of shoulder rotation you get during a windshield wiper forehand can differ from a classic forehand. After you hit the tennis ball, you typically have to rotate a little bit more than you otherwise would on the windshield wiper. There are a number of reasons for this, but in this video we keep our focus relatively narrow.

Every time you hit a tennis forehand you choose how you position your feet -- what stance you will use. You can hit a forehand with an open, neutral, or closed stance, but you should stay away from the closed stance if possible. This last stance makes it difficult to rotate your upper body through contact, making it difficult for you to use correct forehand mechanics.

You may think you know Microsoft's apps, but did you know that you could be using them as a power user and make yourself way more productive in the process? Thankfully, the easiest way to master them from home is on sale right now, as The Premium Microsoft Office & Data Apps Certification Bundle is on offer for just $39.99 — a huge 97% off the regular price of $1,782.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

This video describes how to make a talking robot mask using iPhone. For that you need Reading scale, Cutter scissor, Box to fix into head, Cutter Knife, Screw Driver, Glue, Cello tape, Aluminum Foil, Pen, 2 Bottle caps, used paper and an iPhone with mouth analysis software. First take together, now take that Box and have to two parts for make it convenient to wear into head by sticking both using Cello tape, now we have to make the mouth with size of "50mm by 75mm" which will fit with iPhone’...

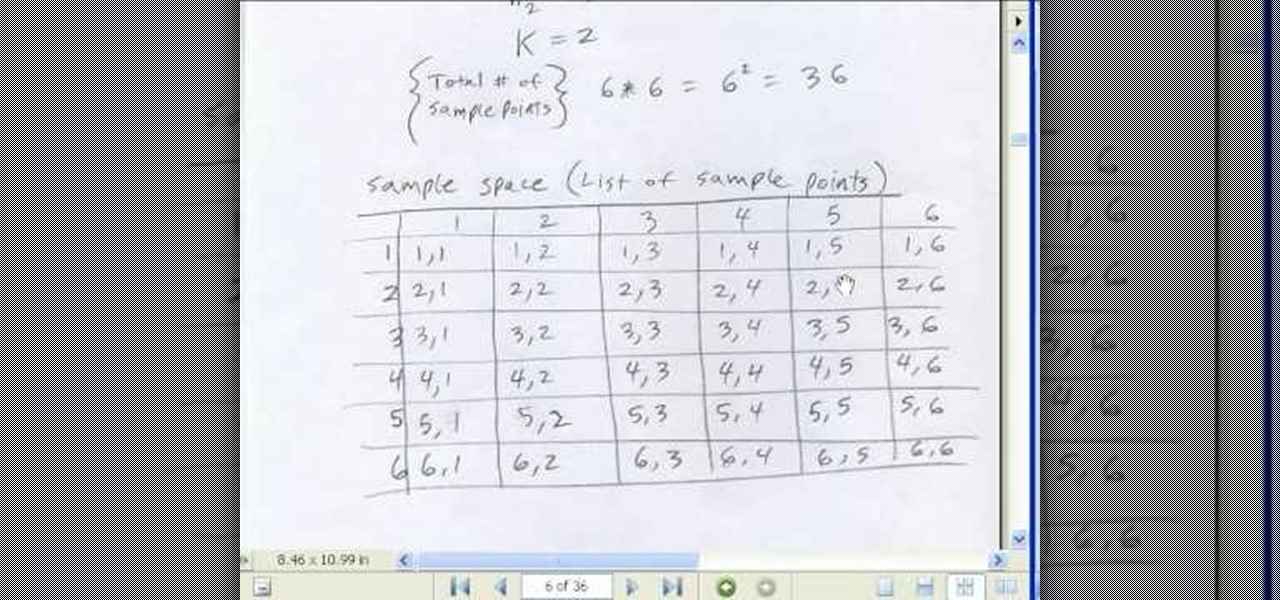
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 50th installment in his "Excel Statistics" series of free video lessons, you'll learn the basics of probability:

This week, Snapchat parent Snap came closer to fulfilling its smartglasses destiny by adding new 3D content capabilities to its third-generation Spectacles. At the same time, the now defunct Meta Company continued its fall from grace, as a judge ruled in favor of the plaintiff in the patent infringement case against the Meta 1 and Meta 2 headsets.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.