Achievement hunters, listen up! It's time to head into the Transformers' world with Transformers: War for Cybertron. This game takes place on the planet to both the Autobots and Decepticons and it gives you a first hand experience of what happened on that planet.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

This achievement is sure to make you "fly like an eagle." In the game Assassin's Creed II, you're introduced to a bunch of new weapons and skills that you can use to take down your victims. One of the coolest new additions is that of a flying machine or glider. This can be used to travel from once place to another and can even be used to attack nearby archers. Doing that can actually result in the achievement, Fly Swatter. So check out this tutorial on how they did it and how you can do it. E...

In this brief video tutorial, the host 'Uncle Todd' demonstrates how to 'attack a beat'. This video is intended for beginners. Watch as he shows you how to keep your tempo up as you time your drum strokes in a beat. You should practice my trying just your right foot and your right hand, and then alternating to to your left foot and your left hand. The host in this video uses an electric metronome to keep his tempo steady and accurate, something that he recommends you try at home. Don't forget...
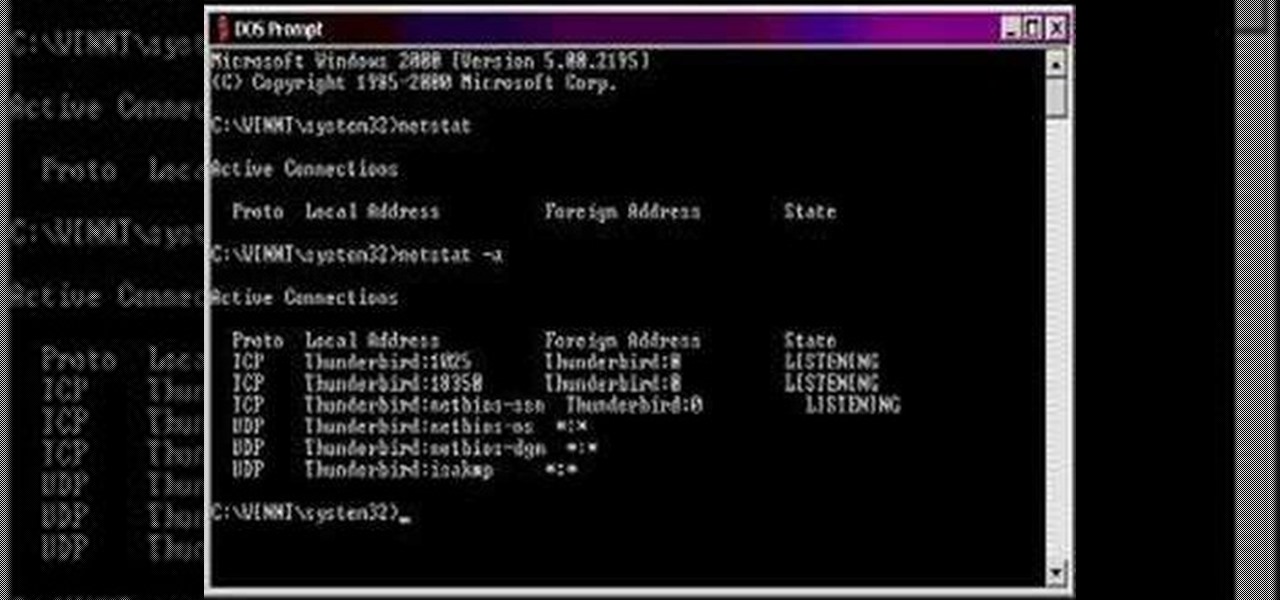
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

Rick Steinau with Ask the Exterminator demonstrates how to prevent yellow jackets from nesting in your home's walls. In mid to late summer yellow jacket populations increase. Yellow jackets can find spaces in the veneer or in cracks in bricks or siding. You can hear scratching noises in your walls as the wasps move. Observe wasp activity late in the day when they return to their nest for the night. Treat reachable holes with pesticide dust and a bellows. Leave the hole open to let the wasps f...

The moonwalk has been written in history and will go down as one of the most well-known dance crazes next to the Macarena and the jitterbug. In order to moonwalk like Michael Jackson, it's important to focus on the pivot and push of the feet and legs while sliding. Make your moonwalk smooth with the tips and tricks given in this free dance lesson.

This video shows tips on how to use insects to benefit your garden. This will teach you ways to reduce the insect load in gardens without the use of chemicals. Rose aphids can be controlled with lady beetles, for example. Although these techniques have been used for agricultural use, they will work in your home garden. Asian Lady Beetle, tend to stay put. They won’t migrate. They will attack Pecan Aphids. Trichograma, a wasp that is effective against larvae and eggs.

This video demonstrates the cross court backhand shot in a Racquetball match. It demonstrates the proper form and timing in an actual racquetball match. It provides helpful tips: for example, the cross court backhand shot should be employed strategically. The best time to consider using the cross court backhand shot is when you see your opponent leaning on the down line: i.e. use the cross court backhand, if it appears that your opponent has already committed to a line of attack. If it appear...

The Dahlia Guy is going to show you step by step how to plant dahlias. First, you want to bury your tubers at 2-4inches of depth and place a stick right next to the eye so you know exactly where the dahlia will be. Also, you want to place a timed release fertilizer in the hole and then cover it up with the dirt. Now, take a 16inch long stick and use that to space out the dahlias in your garden. Some tips to use are use name tags at the beginning of the of the planting and at the end of the di...

How To Set Intonation on a "Gibson Style" Fixed Bridge. A step by step video tutorial that will teach you how to change the strings on a fixed bridge guitar and also set the intonation. Andrew Wasson walks you through a series of instructions that include cutting the strings off your guitar, tightening the bolts on your tuners, polishing frets and fret board and more. He then goes on to show you how to put strings on your guitar, tune the guitar with a tuner, set the bridge saddle, and settin...

Let’s try to thread the needle, as in give a choke hole. First get your opponent down on the mat facing upwards and sit in the mountain position. Hold your opponent's left hand with yours around his head to block him/her. Get your right hand through your opponent's left hand (needle in the hole) and push your chest towards the ground. This will put pressure on your opponent. It will help in your attack as well as defense techniques.

In this tutorial, viewers will learn how to use the synthesizer functions of the Yamaha PSS-780 keyboard. Starting with the basic piano voice, the presenter shows how this can be modified to create a new sound. He shows how the attack rate of the sound can be modified with one setting, how the modulation button affects the tones of the sound, and how sounds can be further modified with the frequency control. The presenter concludes by noting that with practice the user will learn to create ot...

Want tour-like spin on your swing? There are several keys to imparting tour-like spin on your wedge shots, including proper set up, a correct angle of attack, and quality contact. Tim Mahoney, Director of Education for Troon Golf, explains these keys and how you can make them part of your game.

It's time to smash that iPhone, but wait… you don't really want to break your iPhone, do you? That's were a fake iPhone prop comes in, perfect for any homemade movie. Just make this, and switch it out with the real one during the anger attack. Watch this video tutorial to learn how to build a breakable iPhone movie prop. Also works with a fake smashable iPod.

This is a Cheat Engine guide on how to hack this flash game - P.O.D. Kongregate Acheatment shows you how to hack P.O.D. with Cheat Engine (09/23/09). This P.O.D. cheat will give you a level hack.

Cary Kolat demonstrates wrestling technique for collegiate defense. This covers defending single leg attack on the mat. Coach Kolat shows you how to practice funk roll same side as single leg move

Learn how to deal with a black bear or grizzly encounter with Shannon Davis and Ted the Bear. Black bears are distinguished from brown bears by lack of a prominent shoulder hump; a Roman profile or sloping nose and forehead instead of a dished forehead; and shorter, thicker claws for climbing versus longer, more slender claws for digging. Although brown bears are generally bigger, size is not a dependable indicator. Also, fetal position is often recommended as opposed to lying prone as shown.

You never know when you'll have to defend yourself against one of these bloodsuckers, so be prepared to bring a vampire to his knees. While you may not believe in vampires, there are those that do. In any case, prepare now for a hypothetical attack from the un-dead and you won't have to kick yourself later. You will need garlic, a cross, rice, grain, or seeds, holy water, a wooden stake, an axe, matches, and some water. Watch this video survival training tutorial and learn how to fight off a ...

Grandmaster Alexandra Kosteniuk teaches you how to... you guessed it, play a game of chess. This chess video tutorial will show you how to take the initiative in a chess game to win.

Trying to eat healthy and lose weight when you're a foodie is hard. Because when it comes down to it, most good food (we're thinking sweet, salty, fried, and crispy) is essentially a heart attack in a box. But every now and then you find a recipe that's both delicious and relatively healthy.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Have you ever had a cold sore that just won't seem to go away? In this video, we learn how to get rid of your cold sores for good! Since there is no complete cure for cold sores, you must start with prevention. Eat a healthy diet with lots of nutrients, which will restore your immune system to fight against cold sores before you get them. If you end up still getting one, don't bite it or irritate it. You can use natural remedies or over the counter products to help relieve these and get rid o...

Sometimes taking the route where you don't fight at all in Minecraft is the best plan of attack! If you're looking for a clever way to take down almost all types of creatures (well, except for spiders), check out this awesome video! You'll learn how to make a crafty water trap that'll keep them stuck until they drown to death, or burn up in the sun, and then it's a quick, simple matter of running down there and getting the loot that they drop.

In order to use ThermaPure heat system to eradicate bedbugs, you will need a professional, with the appropriate equipment, including surface temperature readers.

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to get medals fast on Evony (09/25/09). Swamps are NOT the best place to attack if you want medals. A level 2 would be the best.