Ace Up My Sleeve: It's not a playing card though. Talk to Paola again and she'll give you the hookup with a cool weapon. Problem is, it doesn't work yet. You need to bring it to Leonardo da Vinci, who's just across town. Make your way to him and knock on his door for a lengthy cut scene.
New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

This is how to do the Manu Ginobili step back jumper! NBA hot shot show's us how to pull the step back jumpshot, one of his Signature Moves on Nike's series. First the long step and catch your balance. Then setup for the rim. Go behind the back and then see what you have in front of you.

Learn how to hold plank position while doing a cross kick under. Presented by Real Jock Gay Fitness Health & Life.

Greasy bacon is so delicious, but when it's too delicious it can be soggy, a heart attack just waiting to happy, or merely not as good as a less greasy, more crispy taste. But what if you don't have an oven or stove? How do you make crispy bacon without the mess? The microwave. Yes, believe it or not. Make crispy bacon in your microwave in just a few minutes without the greasy mess.

The narrator starts by asking the question, how do sumo wrestlers get so big. Most of his patients are seeking weight loss. Number one way to put on weigh is to sit breakfast. The reason behind this has got to do with you blood sugar levels. What sumos do is they wake up, skipping breakfast and that train for 5 hours. They then consume about 20,000 calories throughout the day and take naps in the afternoon. They then have a huge dinner. The sumo wrestler uses his metabolism to gain weigh. He ...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Is your girlfriend or boyfriend always right? No matter what you say, they will always be right? Well, in this tutorial learn how you can win in an argument fair and square with a few simple techniques.

Warts can be embarrassing – as well as contagious. Help minimize the chance you'll spread them to other parts of your body, or other people.

Your sewing machine needs bobbin thread to create overlock stitches, so keep your machine going by learning to fill your bobbin.

Prepare for adventure on the high seas by making your very own pirate costume. You Will Need

When protecting your garden, you can stay green with some environmentally sound solutions. You Will Need

Make your upholstered furniture look like new again by getting out spots and stains. Learn how to remove stains from upholstered furniture with this how to video.

Beat the snack attacks with this healthy banana and peanut butter favorite. You'll love how simple and quick this fruit smoothie is to prepare. This cooking how-to video is part of Healthy Appetite with Ellie Krieger show hosted by Ellie Krieger. Cooking healthy food can be quick, easy, but most of all, delicious. Nutritionist and author Ellie Krieger has created fast and simple healthy recipes for the real world. She'll show you how simple it can be to stay on the healthy track no matter how...

Women's self defense strikes are extremely valuable in a world where women are attacked everyday. Learn self defense strikes, kicks and punches with tips from a martial arts expert in this free self defense video series.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Whoop, there it is. McDonald's makes its food even faster by partnering with UberEats to bring orders to your doorstep in over 1,000 locations around the country.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

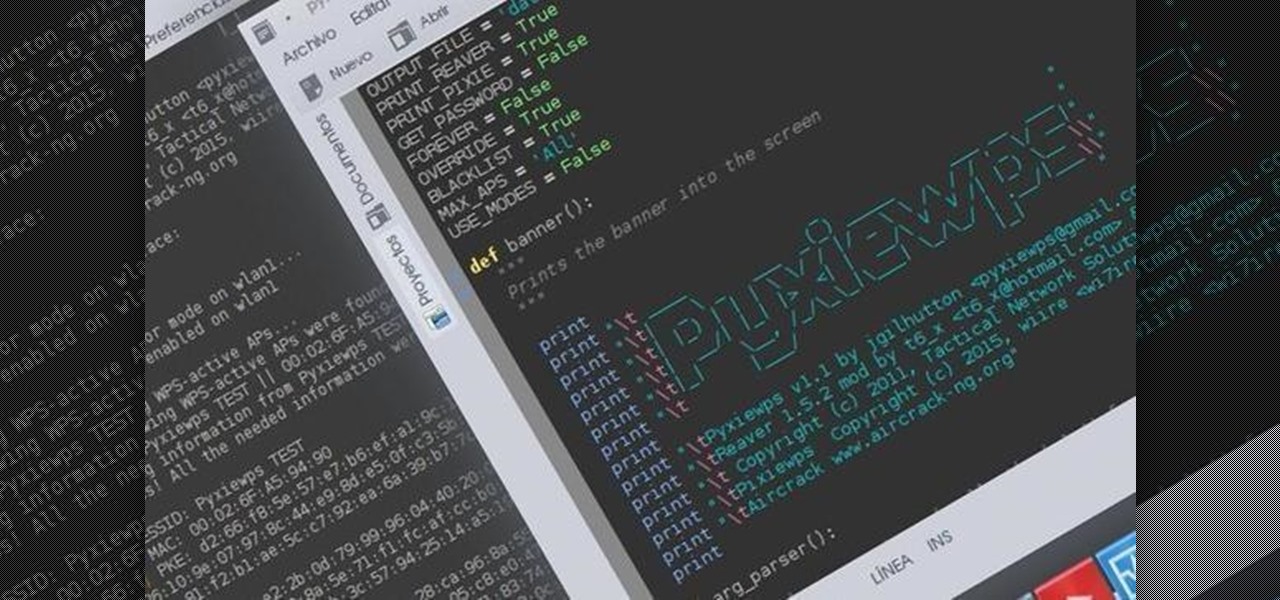
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!