In this video you will learn how to complete the "Finish Him" achievement in GTA IV. In order to do that just follow these steps. First you will need to go in a crowded place. You will need to get 10 melee counters in 4 minutes. To complete a counter attack you will have to press the A button when the enemy tries to hit you. After you dodge the attack you will have to press the B button in order to punch him back. Just repeat this process for 10 times and you will successfully get the "Finish...

In these two videos, Matt discusses 1.d4 d5 2.e3 Bf5, preventing White's Stonewall setup by beating White to the d3-h7 diagonal. The only way White can play for an advantage is to play 3.c4 with the goal of an early attack on b7. Some of these positions can also be reached via the Slav Defense.
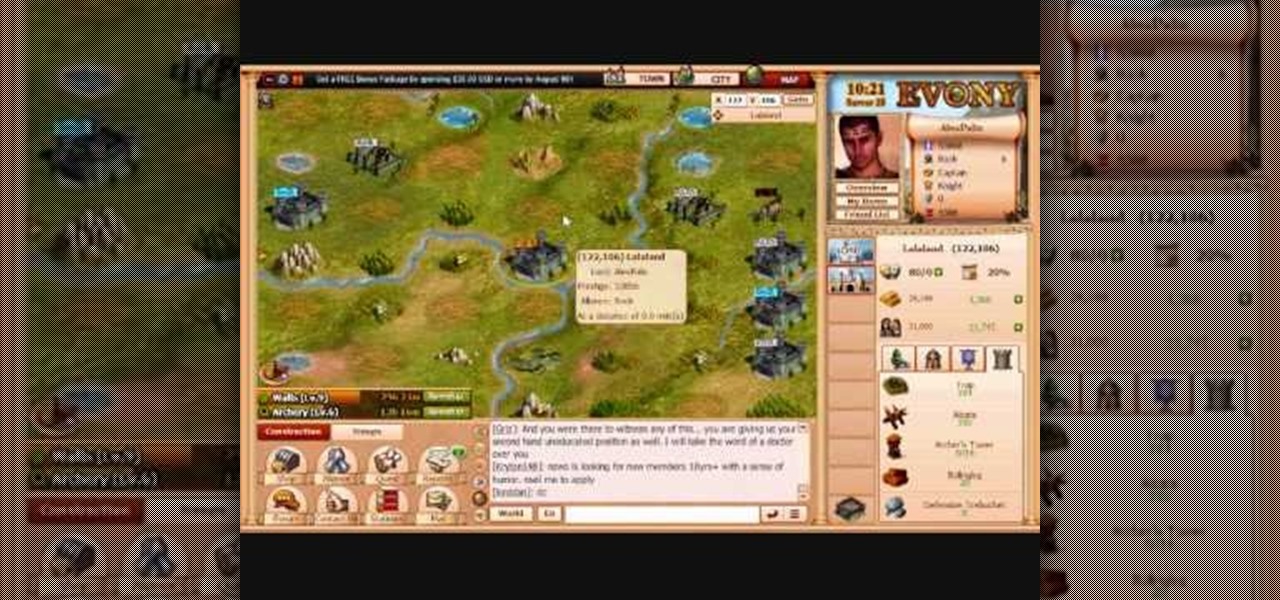
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Your job is to defeat Sapientia in this fight on the Xbox 360 game Bayonetta. In Chapter 13 - The Cardinal Virtue of Prudence, attack the red sphere over Sapientia's head. This fight starts with Bayonetta on the ocean, on a surfboard-like object. Sapientia will use two attacks. The first attack starts with his fin sticking out of the water, like a shark. He will then jump into the air and dive at you. Just keep moving in a straight line to avoid this attack. For the second attack the camera w...

Tired of being attacked by the goblin army in Terraria? Here's a sure-fire, or rather sure-lava, method for defeating them. Watch this video to learn how to design a lava trap that will make the goblin army vulnerable to your attacks.

Finding all of the rare trade objects in Assassin's Creed: Brotherhood can be infuriating, what with random item drops and quests to juggle. Watch this video for a guide to farming trade objects by killing bandits along a particular route.

Street Fighter IV : Blanka, the Brazilian Beast unleashes havoc upon the World Warriors once again. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

Street Fighter IV : Vega, the beautiful Spaniard delivers gruesome damage. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

So you like card games, huh? Don't we all. Well, have you ever heard of Heart Attack? I didn't think so.

This is a match that takes a look at rapidly changing from a queen side attack to a king side attack, and how that can sometimes catch your opponent off guard. The match also shows how creating complications can sometimes mask the most deadly, yet subtle threat.

Here is a match with a Reti Opening transposing to a King's Indian Attack. See how to do it, and see why to do it.

This is an introduction to the Veresov Attack 1.d4 Nf6 2.Nc3. It features a game in which Matt crushes a reasonably strong guest who only makes 2 very natural looking errors (...O-O and ...c4). Try it out for yourself.

In this series, Matt will examine the Stonewall Attack for White and display defenses which he thinks are challenging and/or interesting. Here's a prototypical Stonewall game where everything goes right for White.

This video demonstrate a system against the King's Indian Attack. Enjoy! And don't get too good, because if we ever play, I don't want to lose.

This is a trap in the Torre Attack (1.d4 2.Nf3 3.Bg5). It's a favorite in opening traps, so watch and learn. You'll need it someday.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Welcome back, my rookie hackers!

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

In this video tutorial, viewers learn how to checkmate an opponent in four moves in Chess. This task is very easy, simple and fast to do. Begin by moving your pawn to E4. Then on your next turn move the bishop to C4 to attack F7. Now move the queen to A5, which also attacks F7. Finish by moving the queen to F7. This is an automatic checkmate because the opponent will lose the king in either way. This video will benefit those viewers who enjoy playing board games such as Chess, and would like ...

The video describes an easy way to survive an attack from someone in the street. When the assailant grabs your, your first reaction should be to guard against their initial blow. Then, punch them in the groin, grab them around there neck in a sleeper hold type move using your arm to wrap around the back of their head and/or neck. Proceed to knee them hard either in the stomach or groin, and then simply push them off of you presumably giving you enough time to run and escape.

This video details how to survive a knife threat from behind. When threatened from behind with a knife, do not attempt to move the body first, this will result in the attacker maintaining the capability to thrust the knife into the body. When threatened, place arms out and low in a submissive position, this is to be followed by moving the left arm backward in a sweeping motion to push aside the arm which is holding the knife. Once the arm is moved, turn the body and bring the elbow up into an...

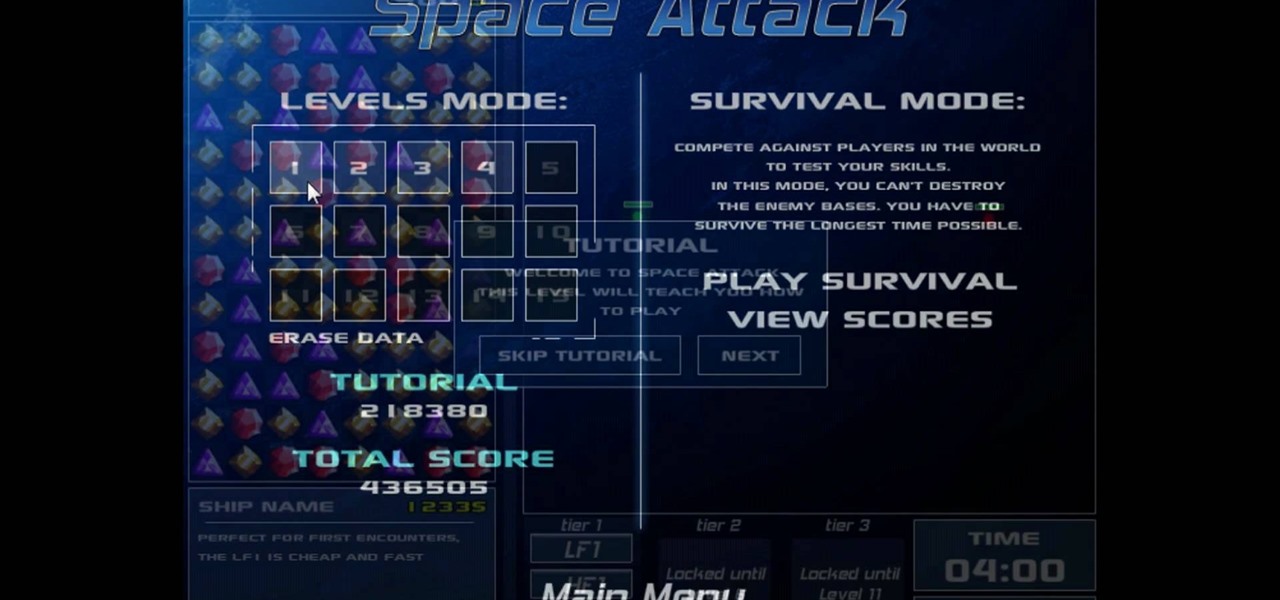
Trevor4Ever595 teaches you how to hack the game Space Attack using Cheat Engine. You start the game, select a level and pause it using P. Open up Cheat Engine, open the process list, select Firefox or whatever internet browser you are using. Then you will want to use the search box to search for the amount of money you have in the game. A lot of values will come up to the left of the search box. Go back to the game, earn more money and then search for that new amount. Cheat Engine will only r...

Machinima.com holds your hand through the 5th and final Prince of Persia Walkthru.

Street Fighter IV: Ryu, An old favorite returns, stronger than ever. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

Street Fighter IV: Quick, cunning, and flashy, Ken Masters brings his A game to the latest Street Fighter.

Street Fighter IV : Rufus may be portly, but his size obviously doesn't slow him down. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.