A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Minecraft 1.8 has introduced Enderman to tons of blocky servers all over the world. If you're looking for ways to fight against Enderman or just avoid Enderman all together, take a look at this walkthrough on how to do both. Be sure to grab an Ender Pearl so that you can half their attack range!
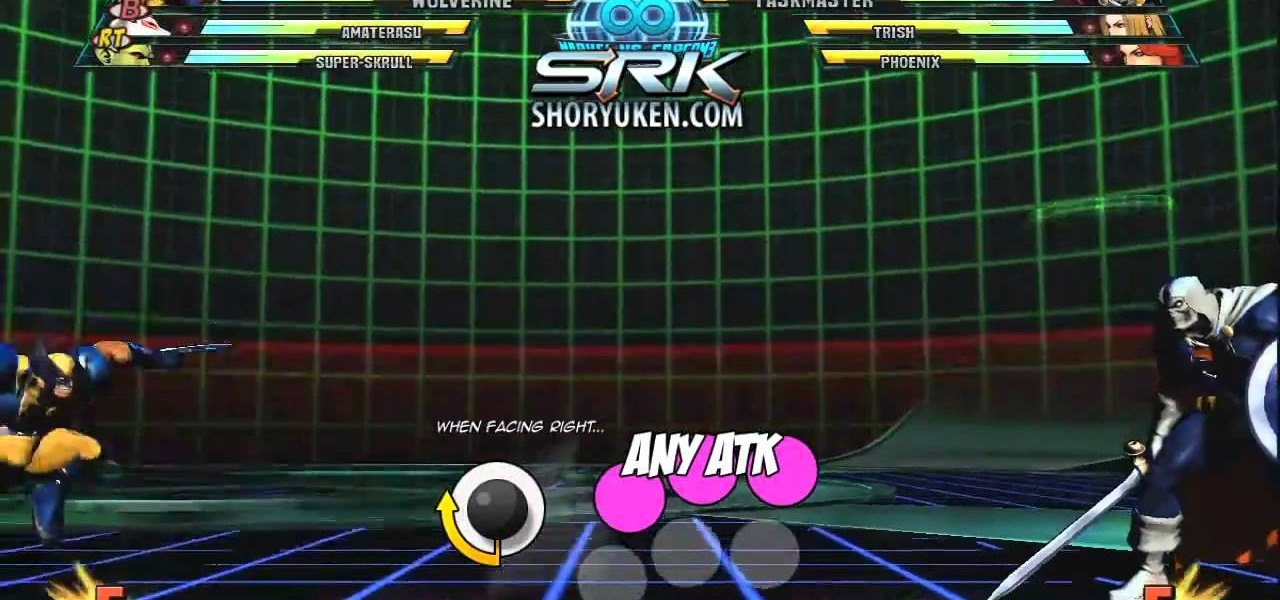
Wolverine in the most well-known X-Man and arguably the most famous face in Marvel comics. Of course he kicks ass in Marvel vs. Capcom 3! This video will teach you the basics of fighting with Wolverine, including his basic attacks, special moves, and some combos.

Okami was one of the best games of the last decade, perhaps Capcom's finest, and it's heroine Amaterasu makes a much-deserved appearance in Marvel vs. Capcom 3. She isn't quite as powerful as you'd expect the God of Everything to be, but she kicks serious butt and this video will teach you the basics of fighting with her, including tips on all her normal attacks and special moves.

Marvel vs. Capcom has been the flagship series for frenetic 2D fighting games for years, and Marvel vs. Capcom 3 hit store shelves in February. This video tutorial will teach you the basics of the game, including basic combos, hyper combos, team combos, special attacks, and more. Everything you need to start off your MvC3 career right.

Beyblade is a fun game from Japan that is very similar to Spinjas but much more complex. If you're new to the game or just ant some expert advice watch this video to learn about the four mains types of Beyblade (attack, defense, stamina, balance) and how they can each be used to play better Beyblade.

The SAW lead is the most recognizable sound in hardstyle and hardcore electronic music, sounding like a swarm of bees attacking with the precision of an honor guard. Watch this video to learn how to program a patch for a SAW (or sawtooth) lead on a MicroKorg.

Having a successful rushing attack is the key to good offense both in real football and virtual. If you play Madden NFL 11 and are having trouble running the ball, this video will give you all sorts of great tips and tricks to help you out getting your offense moving and scoring touchdowns.

If you recently purchased Castlevania: Harmony of Despair on your Xbox 360, this next tutorial will help save your life. In this strategy how to tutorial, you'll find out how to defeat the game's most difficult enemies, the stage bosses. Each one has unique powers and attacks, but they also have some different weaknesses as well. They're easy to follow and should be easy to follow. Good luck and enjoy!

Life on the frontier was hard, and it still is in the Zynga Facebook game FrontierVille. If your homestead has been attacked by foxes or wolves, this video will teach you how to beat them, clobbering their little furry butts clear of your homestead for good!

In this excellent informative yet entertaining video Sara from petside.com invites you to join here in the war to end flea and tick infestation. You'll learn why they love to attack your pet and how exactly to combat these pesky little parasite. So gear up for battle and make sure you end up on top and not defeated by these annoying little blood suckers.

Getting back to nature can be an incredibly rewarding experience – unless critters come along and ruin it! Here's how to keep your food from being plundered. To keep your food protected while camping out in the great outdoors, try bringing along a cooler, a cloth or nylon sack, a sock, some rope, and sealable, waterproof plastic bags. Keeping your provisions safe will decrease the risk of animal attack, and make your journey out into nature a fun experience.

Learn the proper method of striking a flint, how to hold the flint, and the angle of attack. Use a slow, downward scrape--make a spark even on a dull edge!

Here are 2 pins for arresting techniques in jiu itsu. One attacks the elbow the other the shoulder.

AntiPolygraph.org's George Maschke speaks with Nick Frost about how to fool a polygraph (lie detector) test in episode 5 of the tongue-in-cheek 2003 television series Danger: Incoming Attack. Note that the anal sphincter contraction, discussed as a polygraph countermeasure, while effective, is no longer recommended by AntiPolygraph.org, and alternative techniques such as mental countermeasures or tongue-biting are to be preferred.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Chinese search engine giant, Baidu, has just announced its own autonomous car platform which is intended to speed up the development of driverless vehicles.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

In this tutorial, we learn how to understand rheumatoid arthritis. This concentrates by attacking the joint spaces and causing a reaction. This doesn't happen for an exact reason, but it usually occurs in older individuals between 40-60 years old. This also occurs in young children rarely. The symptoms are when the joints become inflamed and painful. This happens around the knees, ankles, neck, and more. This attacks both sides of the body and the same body parts at once. Fatigue, fevers, mor...

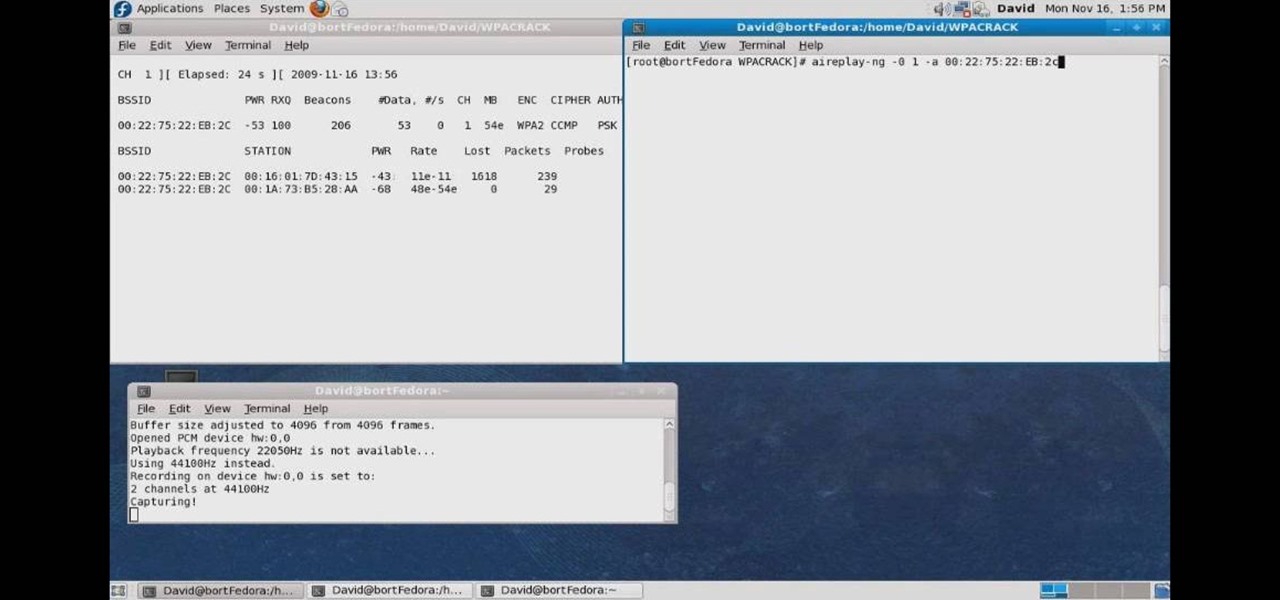
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...

Learn how to maintain your heart health at any age! Great advice for all women because the younger you are the better chance you have at protecting your heart and preventing heart disease. Starting at age 30 you should start getting cholesterol test just to keep yourself in check. Once you hit 40 you should start scheduling stress echo cardiograms which can indicate if there are problems with your heart. Once you reach 50 you really need to be aware of the signs and symptoms of a heart attack...

This how-to video explains the names behind the rubber guard (why they are called what they are) and a step by step method behind the basic rubber guard set up. There are many variations and attack positions, but this video covers the basics: mission control, zombie, New York, chill dog, and kung fu move into jiu claw. There are more advanced attacks and sweeps from anyone of those positions like: invisible collar, asylum, straight jacket, double bagger, reaper, gogoplata, locoplata, Croc, sw...

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

'Wayward Son' is a main story quest about halfway through Act 1 of Dragon Age 2, in which you are called upon to, big surprise, help a mother and son in need. This video series will give you a walkthrough of the entire quest, allowing you to complete it yourself and also making a compelling viewing experience in it's own right.

In order to play the game Risk, begin by setting up. Name a banker. Players choose a color. The number of players determines the number of armies. Remove the jokers from the country card packs. Shuffle the cards. Deal them face down. Players may not get an equal number.

This is a tutorial for controlling the Pine tip moth. Identifying and controlling the pine tip moth consists of studying the small plants of pine. The attacks on pine trees is caused by Nantucket pine tree moth found along the Rio Grande Valley as far north as Espanola, it has spread to South Arizona and California by importing grafts from Mexico. The moths are 3/8 inch long reddish brown to grey in color. They attack the main stem of the baby plant and the pines instead of growing vertical g...

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

Are you ready for the last boss fight in the Xbox 360 game Darksiders? Once you fight Abaddon in the Destroyer, you win, unless you lose. You'll now have to face Abaddon in his "normal" form. He is a powerful swordsman so you'll want to take the defensive route as he can block most of your basic attacks. Instead of attacking him, be patient and stand near him. You'll need to perform a Block Counter but simple tapping the Dash button (without hitting the directional stick) the moment before Ab...

Get ready for the boss fight of your lifetime in the Xbox 360 game Darksiders. In the boss fight in Twilight Cathedral, spar against Tiamat. When you reach the bat queen Tiamat she will take offf into the air immediately. Quickly dash to the Inert Bomb Growth around the edge of the arena closest to the flying and then throw it at Tiamat. Now you need to use your Crossblade and target a flaming urn then the bomb you stuck onto Tiamat to light the bomb on fire. Once you detonate the bomb on her...

Battle Temperantia is this episode of the Xbox 360 game Bayonetta. In Chapter 7 - The Cardinal Virtue of Temperance, prepare for a fight. This chapter consists of a boss fight. You'll start on a platform. Temperantia will punch the platform with his fists and they will stick in the platform. Attack the lighted area of his wrist. While you are attacking he will shoot at you with his other hand. He slowing sweeps his guns, so you can attack until his bullets get close to you, then jump as his l...