There's 14 verses in this chapter in the Xbox 360 game Bayonetta. In Chapter 5 - The Lost Holy Grounds, combat Grace and Glory, Durga, and Alfheim. Near where you start you'll find the book "Crescent and Sunrise Valleys." Walk along the path and it will crumble as you go.

Defeat the Templars in Mission 8 on the Sony PSP and stop the attacks on the safe house. Altair doesn't really catch a break, although the Safe House assault squad comprises only six Templars. Slay them all. For more info, watch the whole gameplay.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

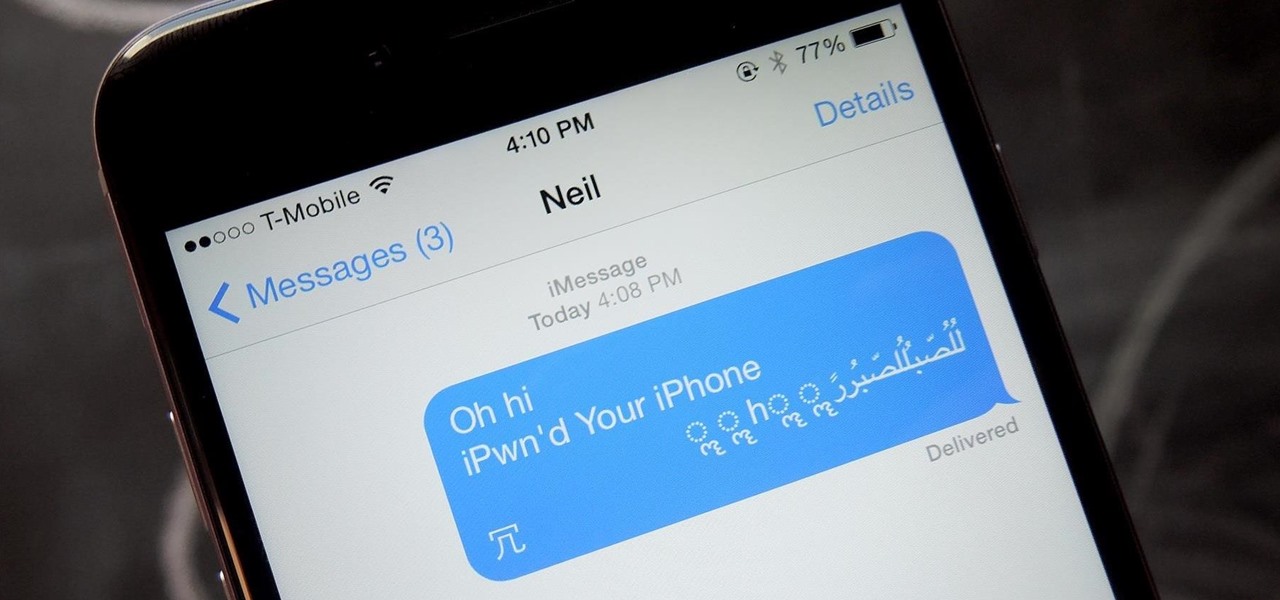
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

No one likes to think about the possibility of natural disasters, but we all know they could happen at any time. Some of us are a little more paranoid than others, but wouldn't it be nice to know that you'd be protected if anything really crazy ever happened? Like the zombie apocalypse?

Awww look, the piggies made a little train to pull other little piggies along. If only it would actually move, they might survive your attack. This video will show you how to beat level 3-6 of Angry Birds with three stars and stop the pigs dead in their tracks. Which they can't really make since they don't have feet... NEVER MIND!

This tutorial starts off by demonstrating the proper way to hold a boffer sword for greatest control. Once you've gotten that down, you're shown how you can go up against an opponent with a shield and still win, even if you only have a sword.

A shield isn't just for defensive maneuvers - you can also use a shield in several different ways to augment your weapon attacks. This tutorial shows you how you can use a shield effecitvely in boffer combat or at a fighter practice.

Combat is a fundamental part of many boffer larps, and you'll need to know how to fight well in order to have a successful PC for most games. This tutorial starts with the very basics of weapon grip, and shows you other important boffer combat techniques, like footwork and how to attack without leaving yourself open for a counterattack.

Heading to a potlock tomorrow but can't swallow the idea of slaving over the stove for hours in the kitchen making the perfect French onion soup and olive oil drizzled baguettes? Save yourself a panic attack as well as time by baking this apple crumble.

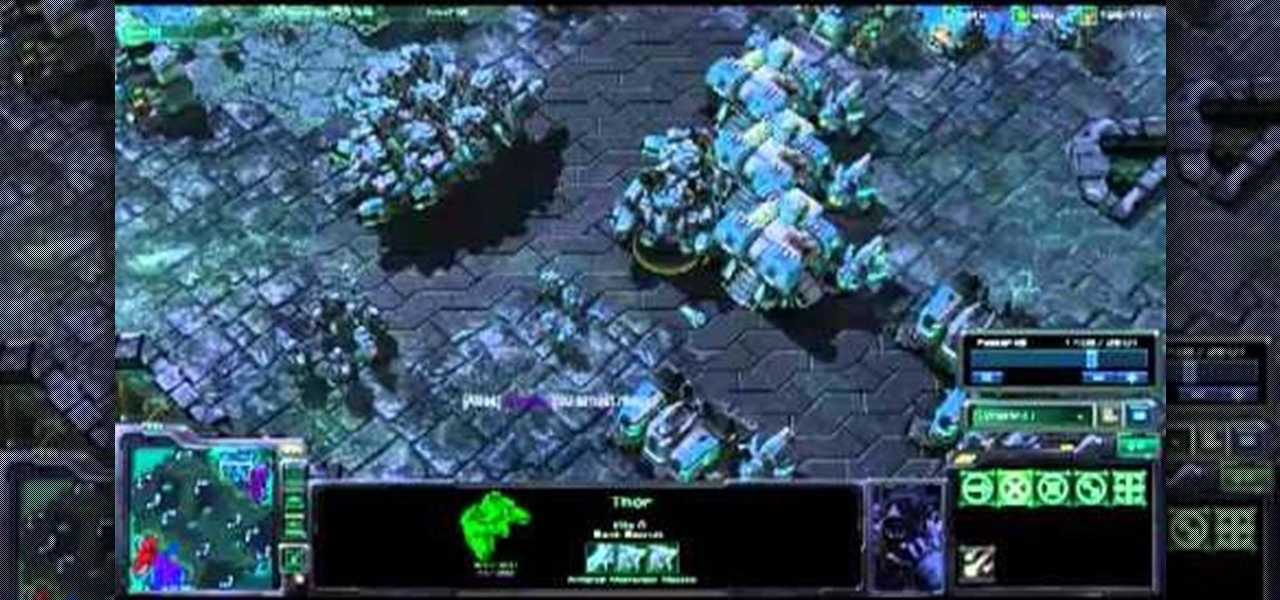
If you're playing as the Terran in StarCraft 2, then you need to know how to master the Thors, which are large and powerful Terran mechanical units (mech units) which are great for defense and late-game attack units. Watch and learn to see the best way to use your Thor army. They're especially good in StarCraft II: Wings of Liberty for sieging large groups of ground infantry units.

One achievement for you to earn in Starcraft 2: Wings of Liberty is the "My Precious" achievement, and you can get this in the Colonist mission of Save Haven. In order to obtain the achievement, you must successfully rescue two Colonist bases from the Protoss attack on HARD difficulty, i.e., destroy the Purifier while at least 2 Colony bases are left un-purified!

Is your kitchen out of control cluttered? Do you have paper work, utensils, and junk mail scattered in the one room in your house that should act as your sustenance sanctuary? In this episode of Real Women Scrap, the hub of every household is attacked as well as other ways to unclutter your kitchen.

L.A. Lakers superstar Kobe Bryant shares some tips with TIME Magazine's Sean Gregory on how he puts his best foot forward everytime he steps onto the court. Areas gone over in this video include: The proper grip & shooting form, attack the foot & sell the fake, the pull-up jumpshot, the art of the foul shot, playing to the opponent's weaknesses, getting in character, and stretching.

Are you using the Queen too much, or attacking with one piece at a time, or making mostly pawn moves, or that tricky Knight obsession, or "freeing" the Rook with a side pawn, or are you being a victim of a back row checkmate? Well, watch this video to to avoid these common chess mistakes.

This how-to video demonstrates Krav Maga Worldwide Sherman Oaks 3rd degree Dave Bluestein teaching defense against a basic choke from the front with a push. Follow along and improve your Krava Maga skills or just learn how to defend yourself from an attack. Watch this video martial arts tutorial and learn how to execute the Krav Maga choke with a push defense.

Worried about the MAC Defender that's been going around? Don't let your Mac get infected, watch this informative video to learn how to keep it virus free. If you are concerned with malware attacking your OS X Mac, you should watch this video.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

Most people can barely be bothered to carry their wallets all the time, let alone a survival kit. When they're all dead from a massive natural disaster or terrorist attack, you'll know you were right to watch this video and prepare an every day carry (EDC) kit that ensure you will have the tools you need to survive with you at all times.

Becoming better at boffer combat is not a matter of mastering fancy sword moves, it's about being able to force an opening in your opponent's defenses and taking advantage of it without leaving yourself open for a counter-attack. This tutorial shows you precisely how to create these situations and take the most advantage of them.

Working with friends is always fun in Shank, but if one person doesn't really know the strategy that you need to employ to wine a boss battle, well, you can just forget it every going any better than bad. But don't worry, in this video, you and your friends can work to succeed against the Bouncer boss in Co-Op mode! You will just need to employ a simple tactic of waiting for him to use his stomp attack, and then lining up a timed trigger pull from both of you to start a double attack against ...

You know you're in pain, but are you just feeling the aftershocks of that spaghetti dinner, or is it a heart attack?

Whether you're interested in trying out for the lacrosse team for your school or would like to brush up on basic positions and responsibilities, this video offers a great run through of the most basic elements of lacrosse. The four lacrosse positions will be covered: Midfielders, attack men, goalies, and defensemen.

The aim of CPR is to preserve life by maintaining an adequate supply of oxygen to the heart and brain. Effective CPR prolongs a person's chance of survival until either a defibrillator arrives and can be used to shock the heart back into its normal rhythm or advanced professional life support is available. This how-to video shows you how to use a portable CPR Ezy when someone you know is suffering from a heart attack. This medical device helps you perform CPR on a victim in a constant rhythm.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.

Shaun of the Dead's Nick Frost faces an ornery alligator and learns a few useful tricks in the process.

Learn to perform a Jiu Jitsu Banana Split leg submission. This is a submission for grappling not self defense. It attacks the groin by pulling the muscles apart.

A pinch harmonic is an overtone. This video is a demonstration of how to play a pinch harmonic on the electric guitar with a right hand technique. Distortion, attack, vibrato, pick selection and more are discussed in relation to this topic.