Interested in using Cinebench to benchmark your Microsoft Windows or Apple Mac OS X computer? You've come to the right place. This home-computing how-to from the Greyscale Gorilla will teach you everything you'll need to know. For detailed, step-by-step instructions on how to download and run Cinebench on your own computer, watch this video.

Maximum PC posts a thorough guide on properly benchmarking your PC. For those not in the know, benchmarking is the process of "running a computer program, a set of programs, or other operations, in order to assess the relative performance of an object, normally by running a number of standard tests and trials against it." (Wikipedia)
Dragon Age 2 is the new benchmark in fantasy role-playing games, and like every Bioware title having enough money and XP is is crucial to your success. Enter this video, which will teach you how to use a glitch to get infinite money and XP! This has not been patched, doesn't mess up the game at all, and lets you play the game at whatever power level you want, essentially. It's brilliant.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

Check out Systm's calibration lesson to make your HDTV a great as it was intended. PCMag's HDTV expert, Robert Heron, teaches us top notch HDTV calibration tricks using tools anybody can afford!

This video gives tips on how to count calories in order to take responsibility for the food that you eat and your weight. Pick a daily calorie count for each day. Set a goal. That goal can be anywhere. You can set it at 1200 or 1800. It doesn’t matter. Weigh yourself regularly.

Screenshots are great, but sometimes they don't tell the whole story. You can show off that new app you got or that awesome new live wallpaper, but a screenshot isn't going to get the point across. What exactly am I trying to show you in the screenshot above? You probably have no idea, and that's the point. You can't see the action I'm trying to demonstrate, but in a video you can.

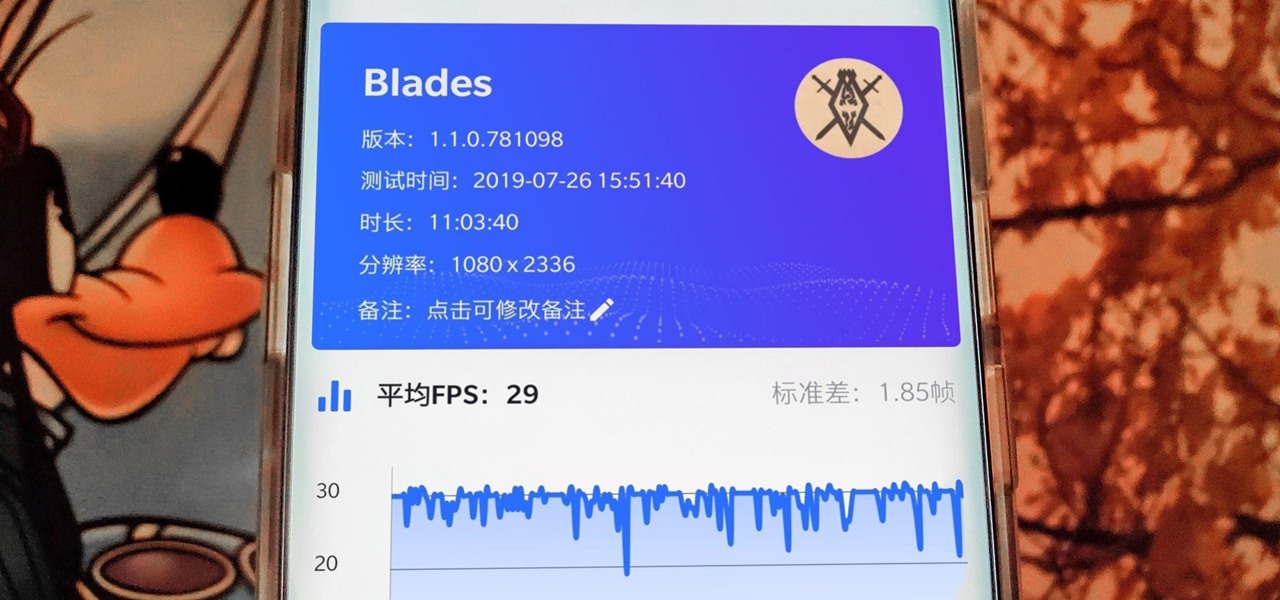
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Being able to use scissors is a good benchmark for measuring fine motor skill development in your child. These simple instructions will help you teach your children how to safely use scissors. NO HAIRCUTTING HINTS INCLUDED!

Google's new Pixel and Pixel XL smartphones are available for pre-order right now, but the general public won't start to get their hands on these devices for another week or two. Tech reporters got some hands-on time at Google's launch event on October 4th, but camera testing wasn't allowed, and the Wi-Fi coverage at the event was too flooded for real-world performance reviews.

There have been plenty of rumors and lots of speculation about the Galaxy S7 and S7 Edge, and now we're finally getting our first look at Samsung's newest flagships—in the form of two images.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

The HTC U isn't set to be revealed until mid-to-late-April, but that isn't stopping the leaks from creating hype. Weibo user Ann Bunny just leaked a spec sheet for the new HTC phone, which can be seen below. Keep in mind, though, all details are still just rumors at this point, but they're certainly juicy.

Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people's pockets.

Innotek, an LG subsidiary, announced today (link is in Korean) that it has developed a 15-watt wireless charging module that can recharge a battery three times faster than other wireless chargers available on the market.

Less than a week after debuting its AR Cloud platform in public with a multi-user installation of more than 100 participants, Ubiquity6 announced on Tuesday that it has closed a Series B round of funding totaling $27 million.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

A top executive from Baidu's telematics division believes the company will become the word leader in driverless by 2020, according to a report in today's South China Morning Post.

Tesla CEO and founder Elon Musk has repeatedly said this year all Tesla models made since October 2016 have the requisite hardware for "full self-driving" capabilities, yet the company has reportedly begun to add a second graphics processor (GPU) to its computer platform for Autopilot — without officially saying why.

The OnePlus 3T was released about five months after the OnePlus 3 with several noticeable upgrades. Firstly, it has a new processor, the Qualcomm Snapdragon 821, which is the same one that the Pixel and Pixel XL sport. Second is the 16 MP front-facing camera with a different sensor. And the next big change was a slightly larger 3,400 mAh capacity battery.

With a price that undercuts flagship devices like the iPhone 6s and Galaxy S7 by hundreds of dollars and a smaller size, new tests show that the iPhone SE incredibly packs just as much power as its bigger brother.

Last week, we told you about Microsoft's Alex Kipman and his nomination for the annual European Inventor Award, presented by the European Patent Office (EPO). And while that's big news in and of itself, it turns out we overlooked a very important detail buried in the EPO's video presentation. What was it? Only one of the most sought-after data points related to the HoloLens since its launch: how many have been sold.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

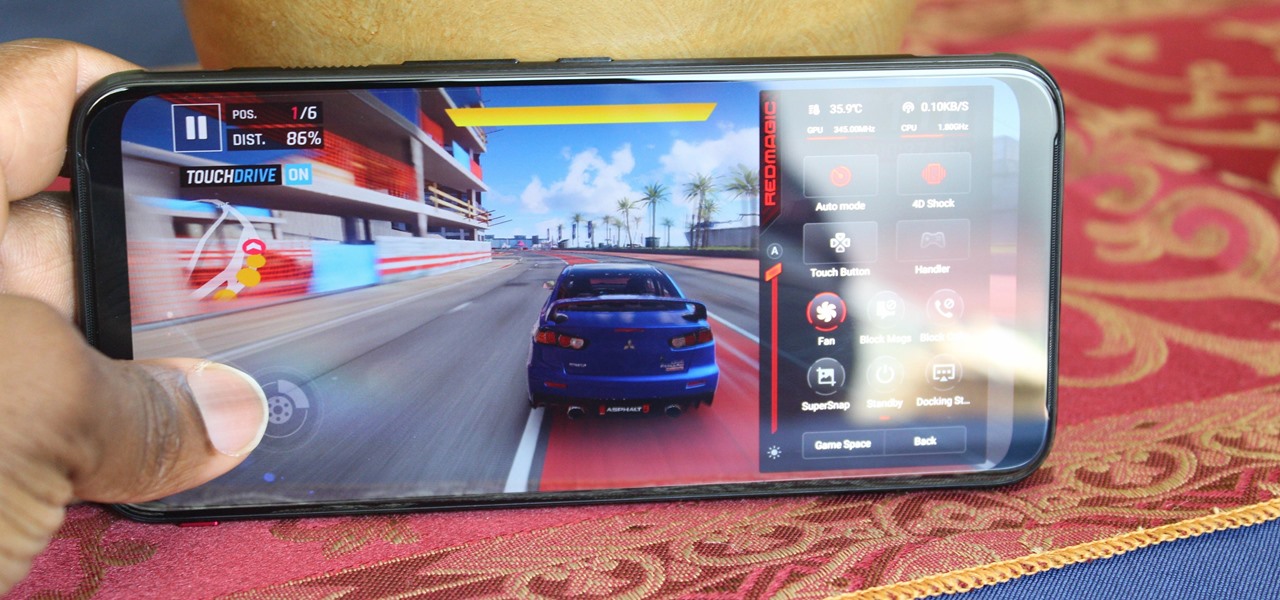
In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

Before, the only way to really tell how your iPhone's lithium-ion battery was performing was to use tools such as Geekbench and Battery Life, but now Apple has included some quick battery health checks right into iOS 11.

This year, two new OEMs are trying to enter the crowded smartphone space. The first was Essential, and now Razer has entered the market with the Razer Phone. Utilizing the team they acquired from Nextbit in January, Razer has created a powerhouse of a device designed for gamers. Coincidentally, Razer announced their new device a day before Apple's biggest revision to the iPhone was released.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

The 12.9-inch iPad Pro was released in stores on November 11, 2015, and a couple days later I went to an Apple Store and to check it out in person. I had mixed feelings about the tablet, but was intrigued overall—so much so that over the next few weeks, as I found myself hearing more and more about the device, a thought began to take hold in the back of my mind—I really want one. At the same time, I was hesitant about dropping roughly 10 Benjamins for a tablet!

What if, back in 2013, Google Glass had launched not as a Star Trek Borg-like eyepiece, but as a pair of seemingly normal shades, with the augmented reality lens and camera hidden within the frame?

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.