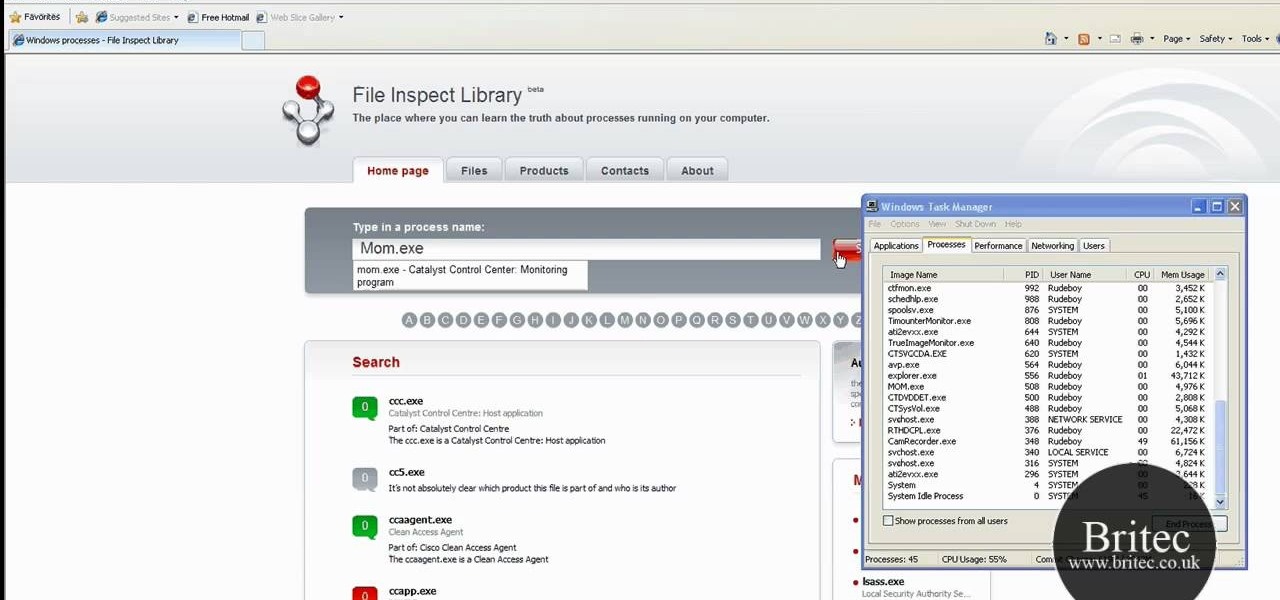
Need help figuring out what a suspicious process is up to on your Microsoft Windows PC? With FileInspect, it's easy to figure out whether a given process is benign or malicious. So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For complete details, including step-by-step instructions, watch this video guide.

Learn how to con a vending Pepsi machine and access a secret (but benign) debug menu with this hack how-to video. While this hack won't get you any free soda, you might, at the very least, impress your friends with it. For complete instructions for this simple, pushbutton hack, take a look at this instructional video!

Sepsis is not only a gross sounding word but also a deceptively dangerous and fatal infection. Which is why more than 40 hospitals nationwide are coming together to a new collaboration to help reduce sepsis mortality, named Improving Pediatric Sepsis Outcomes (IPSO).

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Upon reading the title for this article, I bet you secretly thought to yourself, "Yeah, I've got the perfect way to 'make' roast chicken: I go to the store, and I buy one!" Well, there's no question that there are some really tasty, convenient rotisserie chickens out there, already made and ready for eating or using in recipes.
Welcome back Hackers\Newbies!

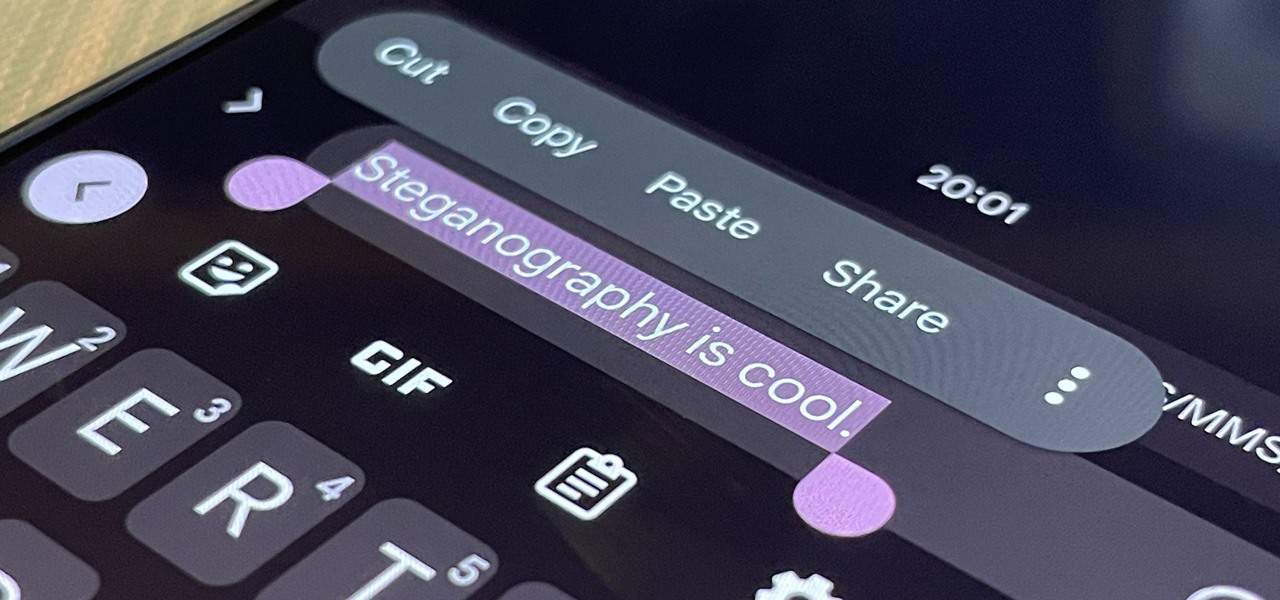
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Tin cans have resin linings that contain bisphenol-A (BPA), which has been linked in animal lab testings to a number of ailments that include reproductive problems, heart disease, and obesity. Tomatoes are high in acidity, which means that the content of canned tomatoes eats away at the resin lining, which causes BPA to leach into what you eat. Long story short: avoid canned tomatoes at all costs.

PopSci's Gray Matter explains how to "hack light", a simple project that calls for glow sticks, diagonal cutters and Drano. Here's the science behind it:

Is Daily Sunscreen Application Dangerous? Since birth, I've been lathered in the sunscreen anytime I venture into the sun. It's what comes with being the freckled spawn of two parents with (benign) skin cancer. Always a fan of the outdoors, my skin has seen lots of sun. You can tell, too. From the lifeguarding, surfing and soccer tournaments, I've definitely notched dozens of sunburns. To protect my skin daily, every morning I apply a moisturizer that includes an SPF 15 sunscreen.

We encourage everyone (especially breast owners) to please watch. Intently. The UK's Channel 4's fantastic program Embarrassing Bodies is serving up lifesaving health advice. This segment does not sacrifice any details (nipple shots, etc.) to accommodate conventional prudes or censorship. We do not intend to either.

In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing out the SCRABBLE board, or even listened to a rap about this word or that word. SCRABBLE is everywhere, even if you don't realize it.