Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to write and letter like an architect.

Zacuto Letus35 Elite Backfocus DOF Tutorial

See how to replace a backup sensor on a Toyota FJ Cruiser. This video shows you step by step replacement of this simple repair. Everyone who owns and FJ Cruiser knows how difficult it can be to judge distance when backing up. Little cars that sit below your line of site which are impossible to see make parallel parking hell. Luckily Toyota added a set of backup sensors to tell you when you’re getting close.

Snowboarding: Hit the Slopes With Style There was a time when simply riding a snowboard made you the extreme guy on the slopes. But now, with more people strapping on a board instead of skis, the stakes have been raised. Fortunately, we've lined up this video tutorial to keep you on the cutting edge. See how to perform a nollie on a snowboard.

Snowboarding: Hit the Slopes With Style There was a time when simply riding a snowboard made you the extreme guy on the slopes. But now, with more people strapping on a board instead of skis, the stakes have been raised. Fortunately, we've lined up this video tutorial to keep you on the cutting edge. See how to tailslide a rail on a snowboard.

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

Learn how to do power press single leg presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do long stride runs across a floor. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternating T push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do lean barbell single side rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do stability ball pike ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do flat bench push-ups and sculpt your body without weights. Presented by Real Jock Gay Fitness Health & Life.

This video lesson introduces a basic philosophy on chicken pickin' or country playing. For country guitar playing, you don't need to use much in the way of effects, just a tiny bit of reverb and compression. Country isn’t dependent on one set of scales, like rock or blues. To play country, you must play over the chords much like a bluegrass or jazz player. It is no coincidence that many country players are also jazz players and vice versa. Every chord has different lines, chord shapes, or rif...

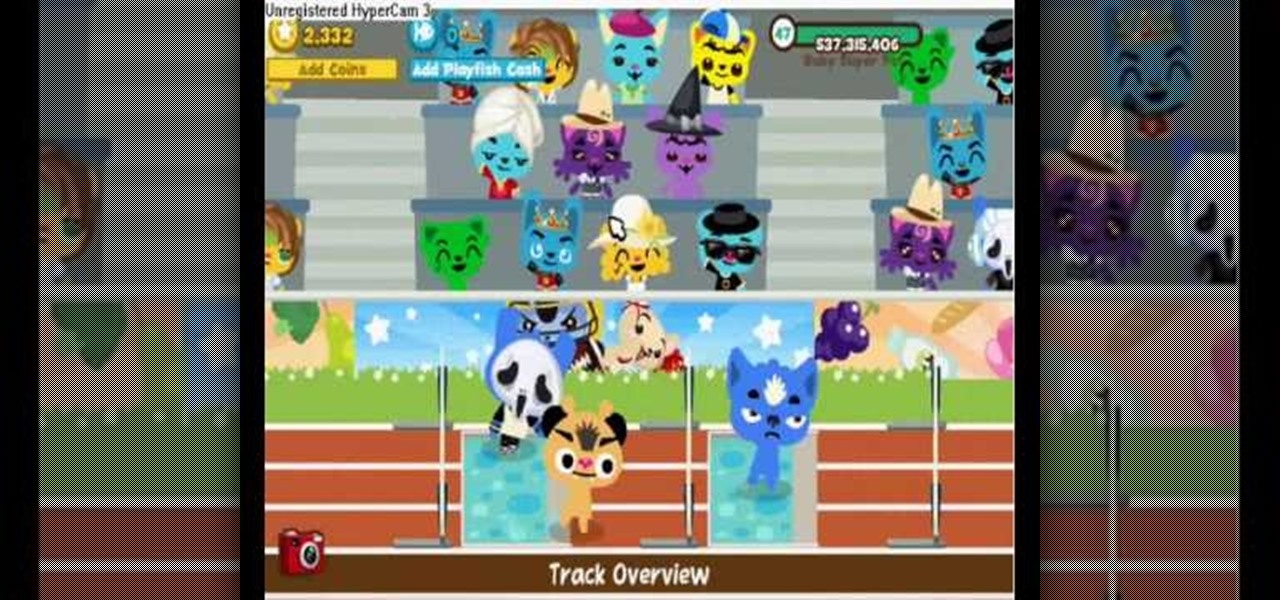
Want to earn coins and easy experience for your Pet Society pet without, you know, actually having to play the game? It's easy. This video guide show you everything you'll need to know to generate unlimited experience and digital cash money.

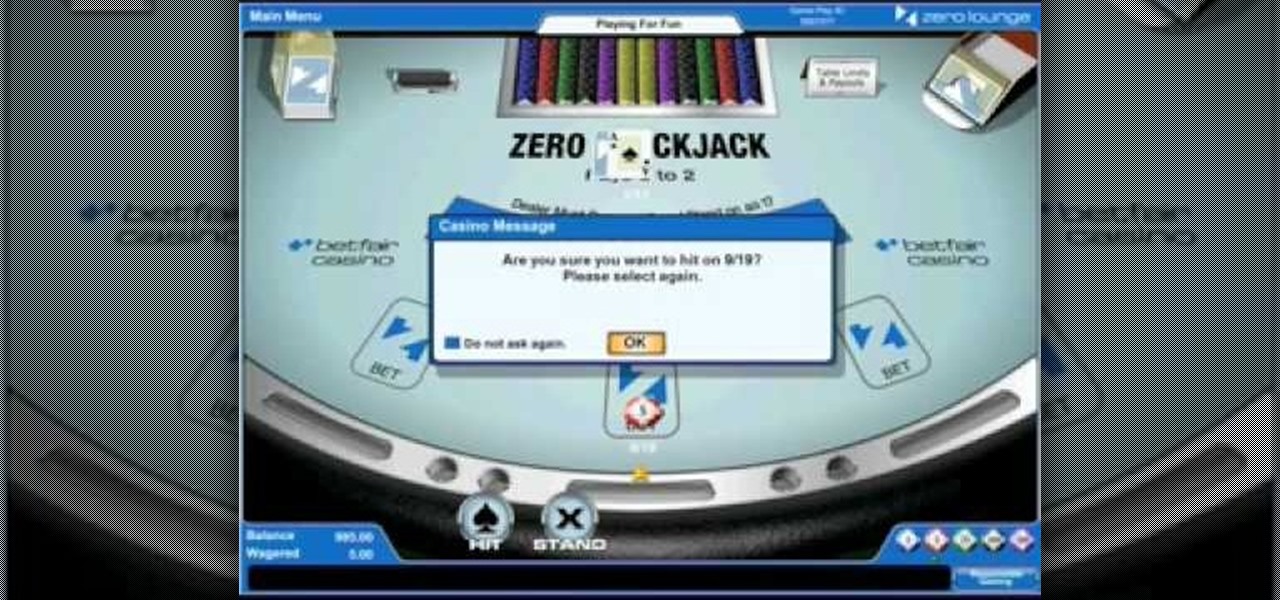
This is a simple blackjack tutorial using Betfair Zero Lounge for gameplay example.

In this video you will learn to speak and read the Aleph Bet - the Hebrew alphabet.

Jennisse shows how to do your nails ‘Fruit Style’, using acrylic glitter, in this tutorial. She begins by taking the natural shine away and bowing the nails down. A few coats of acid-free protein primer are then applied onto the nail beds. Next, some bright green acrylic glitter is taken onto a small brush and applied side to side, at the point where nail grows beyond the finger line. The nail is turned over to create a smile line. Then a thin coat of yellow glitter is added next, halfway beh...

You don't have to wait for the carnival to come around. You can make this special treat any time you like at home. It takes a little bit more time than at the fair but will be worth the look on party guests’ faces when they realize you've just made this counterintuitive dessert.

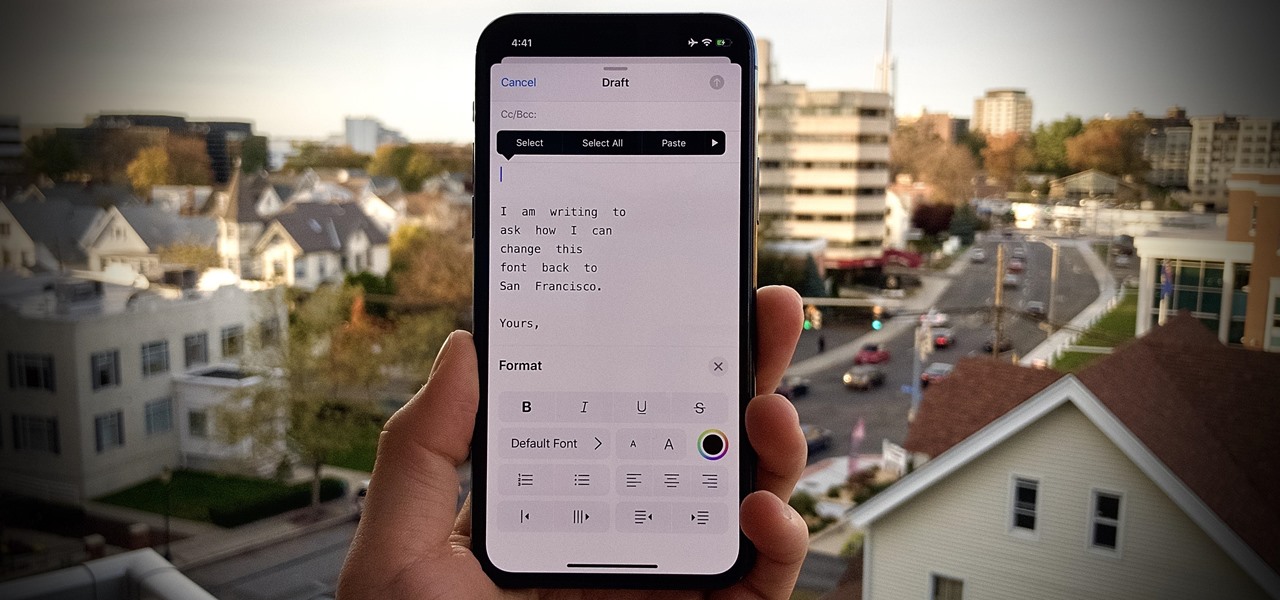
One of iOS 13's coolest features is the ability to download, install, and choose fonts in select apps like Pages and Mail. However, you might notice an issue when writing an email with a custom typeface: there's no option to return to the default font. What gives?

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

While Gucci is among the most recognizable brands in fashion, you would be excused for not realizing that the company makes sneakers as well.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

To promote Star Wars: The Last Jedi, Disney and Lucasfilm released virtual porgs into the wilds of Snapchat via a Sponsored Lens on Sunday.

There aren't many people who will believe that a prosthetic zipper face or gunshot wound to the eye (disgusting as they are) are real, but greyscale from Game of Thrones? That'll really unsettle people for awhile because it totally looks like an actual, honest-to-God infection that someone in 2017 could conceivably have. Which makes it very effective come Halloween, whether it's for a full-on Princess Shireen, Jorah Mormont, or Stone Man costume, or to just infect a completely different chara...

You can pinch yourself, but you're not dreaming. Sprint is actually offering a year of (mostly) free, unlimited service for anyone who switches to the carrier. The only stipulation is that you must bring your phone with you, and it has to be one of the 27 eligible devices.

Intense exercise can cause problems with our digestive tract. It even has a name — "Exercise-induced Gastrointestinal Syndrome." Simply put, strenuous exercise can damage the gut and let the bacteria that reside there potentially pass into the bloodstream.

New York City may not be the friendliest city, but with the apps Via and Curb now letting users ride-share in the city's yellow taxis, New Yorkers can expect to snuggle up close in the back of a cab next to complete strangers. That's right, get ready to feel the love.

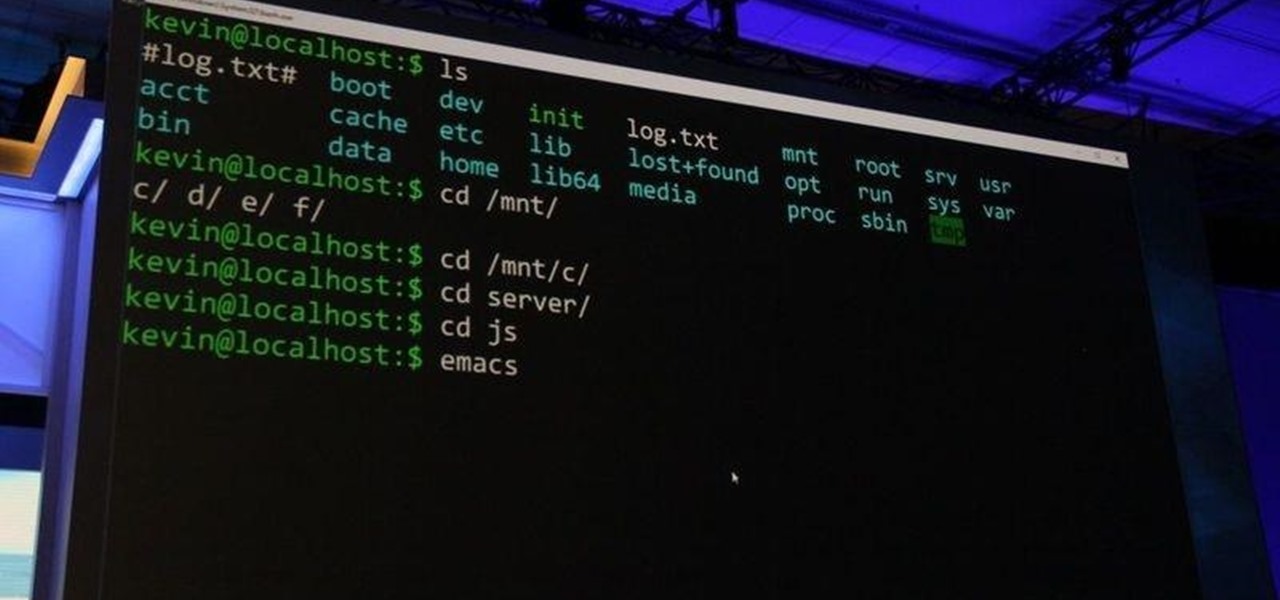
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.

With Android 5.0, Google introduced a new "Heads Up" notification system for incoming calls and messages. While the new incoming call interface seems to be a rousing success, the rest of the Heads Up system has been met with much less enthusiasm from users.

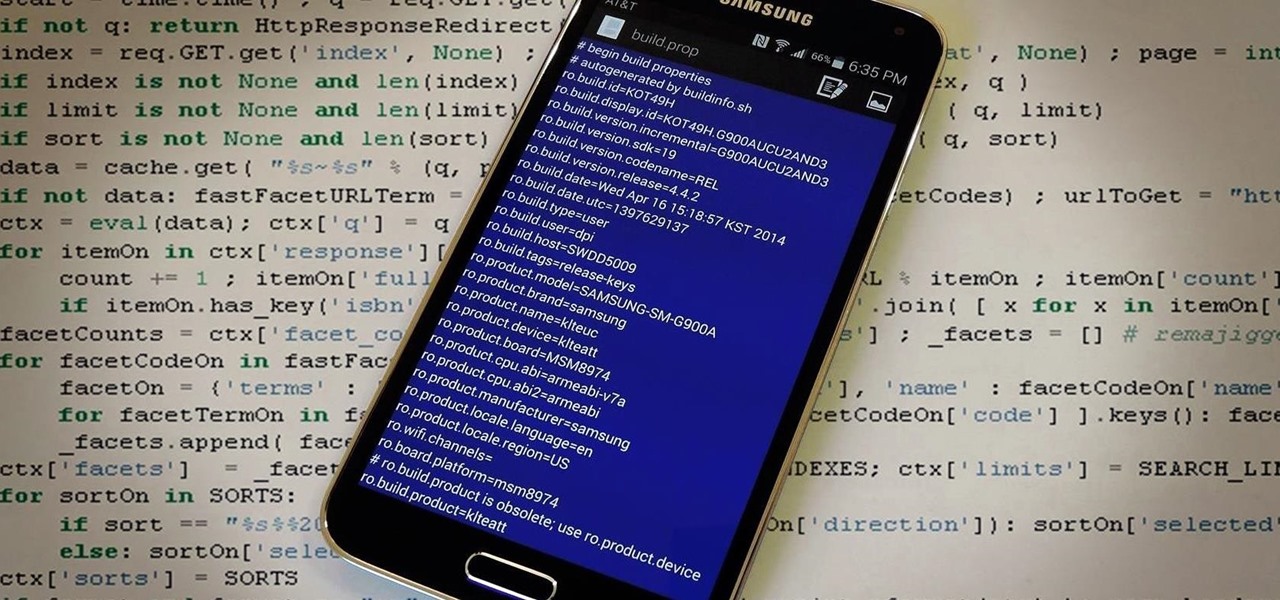
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

The video for Robin Thicke's "Blurred Lines" got its fair share of attention due to the three topless models who star in it. In the second version, they're covered up, but just barely. Both the song lyrics and the lack of clothing sparked plenty of debate, controversy and even parodies.

For some reason, there's only ever one person in a group of friends that has a cooler. Every time there is a hangout or BBQ, that friend is called and has to lug his expensive, huge plastic cooler around for everyone. Not really fair, is it?

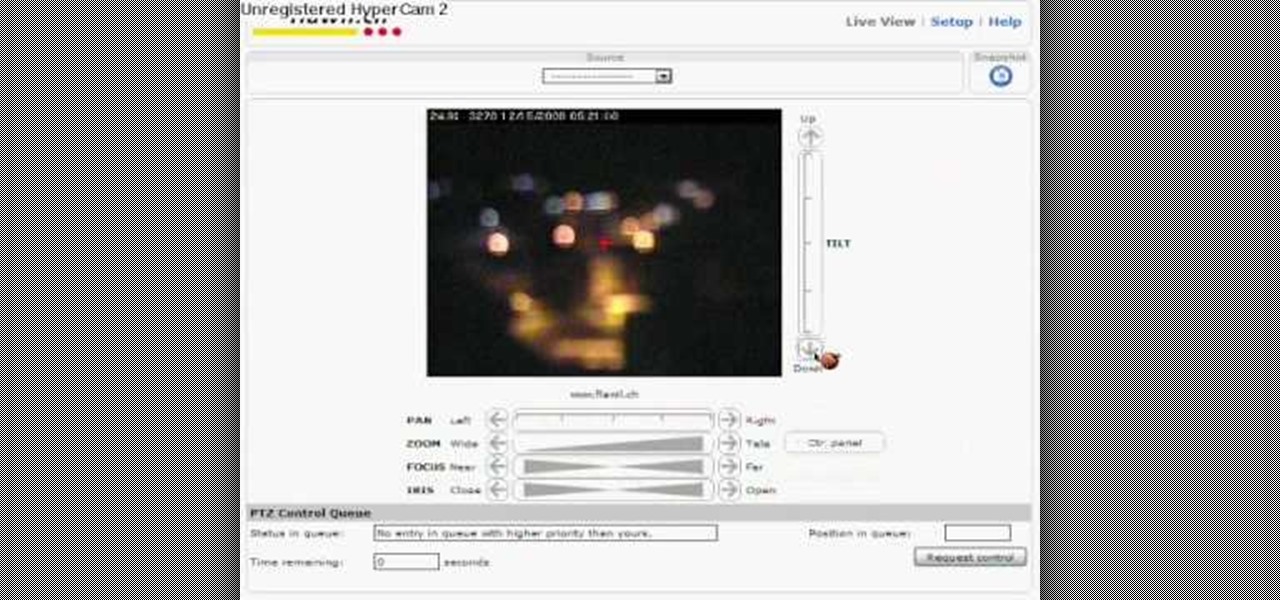
Okay, net sleuths — this one's for you. If you've ever wanted to spy on other people on their computers, this video will show you how to use Google to hack unprotected webcams. All you have to do is enter the following into Google's search bar:

Some Chinese dishes that sound healthy are surprisingly fat-laden. These tips will help you avoid diet land mines.